Managing Risk, Business Continuity
Published 2 November 2020
1. Introduction: Managing the risks
Managing the risk of terrorism is only one part of a manager’s responsibility when preparing contingency plans. Such plans may be in response to an incident or event, either within or near their premises, which may inadvertently impact staff safety, public safety or disrupt normal operations. It is important that this is one person’s function and responsibility. The governing body or board is ultimately responsible and must be committed to managing the risks and understand the consequences of ineffective management.
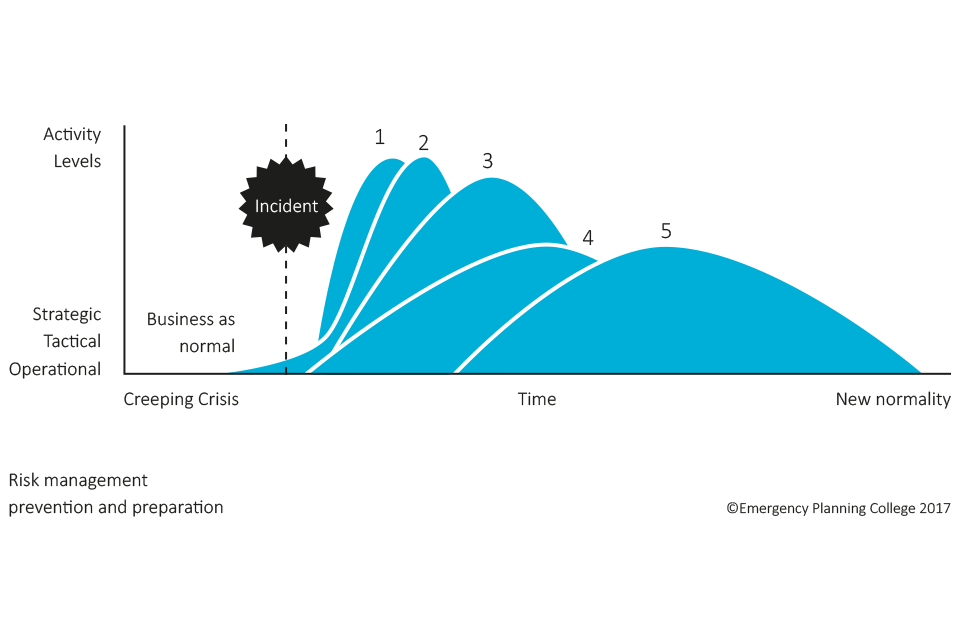
Robust risk management processes will anticipate and assess risks to the organisation. The risks should be mitigated through preventative measures such as ‘target hardening’, the training of personnel and an effective use of information security systems. Having worked on preventing the risk materialising, the organisation must still be ready to respond and recover from a business interruption, regardless of its cause. There are a number of phases in a response, which are summarised in diagram 1.
1.1 Incident response
Incident response deals with the immediate impact of an incident. It is a relatively short term phase that focuses on escalation and activation, ensuring people and the environment are supported and made safe wherever possible.
1.2 Incident Management (IM)
IM refers to how the organisation will manage the consequences of the business interruption at the scene through command, control, coordination and communication. (IM covers who is in charge, how to keep stakeholders informed, escalation processes, coordination of resources, etc.)
1.3 Crisis Management
Crisis management is about your arrangements to manage strategic, complex and unprecedented events. It is rarely standalone and will require integration with other disciplines. Note that an incident may require a crisis management response without the need for a business continuity plan activation. This may be, for example, in the event of major negative media attention about the business. In contrast there may be a ‘creeping/rising tide crisis’ where a disruption such an attack on an IT system emerges and, if not managed effectively, turns into a crisis. The incident response arrangements must therefore be flexible enough to manage both an operational disruption which may need to be escalated, and a crisis situation which requires strategic leadership.
1.4 Business Continuity & Resilience (BC)
These are the arrangements you should develop in order to maintain critical and urgent business activities to a pre-determined level i.e. what work your business must continue to do to survive the disruption from a terrorist attack. Consider a range of impacts that could disrupt your business, including the unavailability of your building (through loss of utilities or evacuation), people (colleagues and suppliers) and equipment (machinery and IT). Then plan how you would continue critical parts of your business during disruption.
Business continuity planning is essential in ensuring that your organisation can cope with an incident or attack and return to ‘business as usual’ as soon as possible. An attack on a crucial contractor or supplier can also impact on your ‘business as usual’, so will need to be included in your business continuity plan. This is particularly relevant for smaller operations that may not have the resources to withstand even a few days financial loss. Make sure you include a consideration of sub-contractors to your principal contractors.
International Standards ISO 22301 Societal Business Management Security Systems and Guidance provides further information on the subject of business continuity plans, along with the Business Continuity Institute (BCI) GPG (Good Practice Guidelines).
Free practical advice is available from your local authority or from the Business Emergency Resilience Group, a Prince of Wales initiative or via the BCI website.
Other useful resources:
You may also wish to complete the Business Continuity & Resilience Checklist
For advice and training on resilience go to the Emergency Planning College Website
Go to the Business Emergency Resilience Group website
Go to the Cabinet Office website
Go to the Government Emergencies, Preparation, Response and Recovery webpage
Go to the Government Emergency Planning webpage
1.5 Business Recovery
A Business Recovery Plan usually takes place over a long duration, with wider stakeholder engagement and detailing the priorities for rebuild, recovery and restoration. It should detail how and in what order you will return to the new normality following a disruption.
Response and recovery usually overlap – there is a transitional phase. After each activation of resilience arrangements, a formal debrief should be conducted in order to continuously improve.
Response activity over time
- Emergency Services: Response safeguarding life, protecting environment and company assets
- Incident management: Command, control, coordination, communication
- Crisis management: Strategic, complex and unprecedented reputation stakeholder confidence
- Business continuity: Maintaining critical activities
- Recovery: Focussed on rebuilding, restoring and rehabitation
2. Reputation
Failing to prepare for serious incidents may impact on your reputation and goodwill. Being resilience minded and better prepared reassures your customers and staff. Effective resilience could potentially deter or mitigate an attack.
3. Neighbours and partners
Do you know who your neighbours are and the nature of their business? Could an incident at their premises affect your operation? There is limited value in safeguarding your own premises in isolation.
A number of organisations have adopted good practice to enhance the protective security measures in and around their premises. This document identifies and complements such good practice.
This guide recognises that crowded places differ in many ways, including size, location, staff numbers, layout, footfall and operation and that some of the advice included in this document may have already been introduced at some locations.
4. Managing the risk
With regard to protective security & resilience, the best way to manage the hazards and risks to your business is to start by understanding and identifying the threats, vulnerabilities and the resulting business impact.
This will help you to decide:
- what protective security & resilience improvements you need to make
- what type of security and contingency plans you need to develop
For some crowded places, simple good practice, coupled with staff vigilance and well exercised contingency arrangements may be all that is needed. If however, you assess that you may be vulnerable to attack, you should apply appropriate protective security measures to reduce the risk to as low as reasonably practicable.
The following diagram illustrates a typical risk management cycle:

4.1 Step One: Identify the risk
Understanding the terrorist’s intentions and capabilities, what they might do and how they might do it, is crucial to assessing risk. This guidance outlines in other chapters the threat and some of the current terrorist attack methodologies.
Ask yourself the following questions:
- What can be learnt from the government and media about the current security climate locally, globally, or about recent terrorist activities?
- Is there anything about the location of your premises, its visitors, sponsors, contractors, occupiers and staff, your activities, or within the wider community that may attract a terrorist attack?
- Is there an association with high profile individuals or organisations who may attract a terrorist attack?
- Do you have procedures in place and available for deployment on those occasions when VIPs attend your crowded place? How often are the procedures reviewed? Are there resources and funding to support this as required?
- Does your location mean you could suffer collateral damage from an attack or incident at a ‘high risk’ neighbouring site?
- What can your local police tell you about crime and other problems in your area?
- Are there any aspects of your business or activities, or those of your staff, that terrorists might wish to exploit to aid an attack; e.g. building floor plans, publically available documents, technical expertise or poor security culture such as unauthorised access to restricted areas?
- Do you communicate information about the threat and building response levels to your staff?
- Do you train and advise your staff to take a level of personal responsibility given the environment and threat of terrorism we face in society in general?
- Do your contracts with other companies restrict what information they can publish online about you such as information or images of your site; e.g. floor plans, security features, patrolling detail etc.
- Does anything identify vital installations or services critical to the continuation of business in your premises?
Read more about Digital Built Assets and Environments
4.2 Step Two: Decide what you need to protect and identify your vulnerabilities
Now that you have determined the risks, you can identify what you need to protect. Your priorities for protection should fall under the following categories:
- people (e.g. staff, visitors, customers, contractors, general public)
- physical assets (e.g. buildings, contents, equipment, plans and sensitive materials)
- information (e.g. electronic and paper data)
- processes and policies (e.g. supply chains, critical procedures) – the actual operational process and essential services required to support it.
For each, you need to consider:
- what is the vulnerability?
- why is it vulnerable?
- what are they vulnerable to?
You know what is important to you and your business. It may be something tangible, for example, the data suite where all your transactions are recorded, the IT system or a piece of equipment that is essential to keep your business running. You should already have plans in place for dealing with fire and crime, procedures for assessing the integrity of those you employ, protection from IT viruses, and measures to secure parts of the premises.
4.3 Step Three: Identify measures to reduce or mitigate the risk
Having identified what you need to protect and why, you need to understand what measures your site has in place already, how effective they are and where the vulnerabilities are. The measures you use should be proportionate and cost effective; measures should work together to produce an integrated system.
An integrated approach to security/resilience is essential. This involves thinking about physical security, cyber security, personnel security (i.e. good recruitment and employment practices) and personal security. There is little point investing in costly security measures if they can be easily undermined by a disaffected member of staff, supplier or contractor by a poor recruitment and or procurement process. This guidance identifies and signposts measures which can be implemented to assist in mitigating the risks.
Remember, TERRORISM IS A CRIME. Many of the security precautions typically used to deter criminals are also effective against terrorists. So before you invest in additional security measures, review what you already have in place. You may already have a good safety and security culture on which you can build.
If you need additional security measures, then make them cost-effective by careful planning wherever possible.
Introduce new equipment or procedures in conjunction with building work. In multi-occupancy buildings, try to agree communal security arrangements.
Even if organisations or businesses surrounding your location are not concerned about terrorist attacks, they will be concerned about general crime; your security measures will help protect against crime as well as terrorism.
Staff may be unaware of existing security measures, or may have developed habits to circumvent them, such as short-cuts through fire exits. Simply reinstating good basic security practices and regularly reviewing them will bring benefits at negligible cost.
Go to the CPNI Operational Requirements webpage
4.4 Step four: Create security plans
Security Planning
Following a risk assessment, it is recognised that for the majority of crowded place sites and venues, the responsibility for the implementation of protective security measures will sit with a security manager or an assigned individual. They must have sufficient authority to direct the action taken in response to the risk.
They must be involved in the planning of the perimeter security, access control, glazing, contingency plans etc., so that the terrorist dimension is taken into account. The security manager must similarly be consulted over any new building or renovation work, so that counter terrorism specifications, such as glazing and physical barriers can be considered and factored in as appropriate.
The security manager at most crowded places should already have responsibility for most, if not all of the following key areas:
- The production of the security plan based on the risk assessment.
- The formulation and maintenance of a search plan.
- The formulation and maintenance of plans dealing with for example bomb threats, suspect packages and evacuation.
- Liaising with the police, other emergency services and local authorities.
- Arranging staff training, exercises, rehearsal, testing and exercising. Include their deputies and conduct briefings and debriefings.
- Conducting regular reviews of the plans.
4.5 Creating your security plans
Effective security plans are those that are simple, clear and flexible. The security planner should call upon staff with particular business area knowledge to help, such as an IT specialist, Procurement or HR manager (to consider countering the insider threat for example).
Plans should be:
- Protective i.e. the site search plan should counter the threat of a placed Improvised Explosive Device (IED), security patrols, deployment of CCTV, staff training etc.
- Responsive i.e. the actions which staff should take if they identify a person acting suspiciously, discover a suspicious item, receive a bomb threat, are the recipient of malware, or if there is a need to evacuate or invacuate. A communication and media strategy should also form part of this response.
The planning should include:
| Policy | Be clear and document what you want to achieve. |
|---|---|
| Operational | Put processes in place to make the policy work. |
| Physical | The “hardware” that supports any operational process. |
| Education, training and awareness | Make sure those with a role to play in the security welfare of the site are properly educated and equipped to act confidently and effectively. |
| Validation | Agree and implement appropriate measures to validate plans and arrangements. These may include exercises, tests or other techniques to establish the suitability, sufficiency and effectiveness of your arrangements. |
| Partnership | Working with those who can or are needed to make security work. |
| Review and monitor | Conduct regular reviews or following any change in circumstances such as a change in threat, circumstances, environment, post an incident or changes in. |
| Communication and media |
Identify how you will communicate with staff, visitors, suppliers and contractors. |
4.6 Action plans
To help progress security planning, it is good practice to create an action plan.
The action plan should set out:
- the activity to be undertaken
- a brief rationale for the activity
- the name of the person responsible for completing the action
- a start date, review date and realistic completion date
- a scale to measure the actions progress, i.e. red, amber or green
The action plan will form an important part of your security audit.
4.7 Step Five: Review your security measures; train staff, rehearse, exercise and test security plans
You should regularly review and exercise your plans to ensure that they remain accurate, workable and up to date. Additionally if there is an attack elsewhere, or there is a change in threat or circumstance including to suppliers, contractors or stakeholders, consider reviewing your plans. Through training, make sure your staff understand their personal responsibilities, they accept the need for security measures and that security is seen as part of everyone’s responsibility; security is not merely something for security experts or professionals. Make it easy for people to raise concerns or report observations. Rehearsals and exercises should wherever possible, be conducted in conjunction with all partners, emergency services and local authorities.
Managing risk and security planning are on-going processes. Part of the validation process is to exercise your plans and use any learning to further refine and ensure plans are workable, achieving the required outcomes.
The aim of your exercises should be to:
- ensure that plans work (verification)
- develop staff and third party competencies and enable them to understand and practice carrying out their roles within the plan (training)
- test established procedures to ensure they remain valid (exercise, rehearse and validate)
- provide learning to further refine the plan (review)
Developing an exercise programme.
The Business Continuity Institute (BCI) outlines five categories of exercising; they range in scale and complexity.
The main levels of exercise are:
- Discussion-based exercises
- Table top exercises
- Command post exercise
- Live
- Test
BCI Good Practice Guidelines Training Course Module Six Version 1.0
| Plan Review (Discussion based) | Table top/Command Post | Live play test |
|---|---|---|
| Very few resources are required, and can be entirely internal. No disruption to business or staff. | More resources, planning and players are required. Can include external agencies. | Significantly more resource intensive to plan and deliver. |
| Can identify systematic issues in processes or gaps in processes/policies/procedures. | Specific scenarios can be used and operational issues identified. | Allows all staff and stakeholders to practice their roles/responses and identify issues that other exercise types do not. |
| Does not address the effectiveness of processes, or allow staff to practice procedures. | Virtual nature can lead to practical issues not being identified, and does not test reality. | Greatest level of realism, providing confidence that plans are likely to work in a real no-notice event. |
Remember: the greatest vulnerability to any organisation is complacency
5. Legal requirements
Management already have health and safety responsibilities under Health and Safety Regulations, the Civil Contingency Act 2004, and the Regulatory Reform (Fire Safety) Order 2005, or in Scotland, the Fire (Scotland) Act 2005 and Fire Safety (Scotland) Regulations 2006. The Management of Health and Safety at Work Regulations 1999 (the “Management Regulations”) compliment the above legislation and set out explicit steps employers are required to take to manage and mitigate the health and safety risks present (or possible) in their working environments in line with the Health and Safety at Work Act.
As part of managing the overall health and safety of your business, you must take reasonable steps to control the risks in your workplace. To do this you need to consider what may cause harm to people and decide whether you are taking reasonable steps to prevent that harm. This is known as a “risk assessment” and it is an exercise you are required by law to carry out. If you have fewer than five employees, you are not obliged to have a written record of this risk assessment, however, an assessment of risk must be carried out regardless and you are required to implement sensible measures to tackle those risks. Having identified any threats and vulnerabilities, you are then required to assess how likely it is that harm will occur, i.e. the level of risk and what to do about it. Risk is a part of everyday life and you are not expected to eliminate all risks in their entirety, but rather, to manage the main risks responsibly.
Please note that you must seek your own independent advice in respect of the totality of your legal obligations.
6. Insurance
Insurance against damage to your own commercial buildings from terrorist acts is available but typically at an additional cost. Adequate cover for loss of revenue and business interruption during a rebuild or decontamination is expensive. Full protection against compensation claims for death and injury to staff and customers caused by terrorism is also available, and again, will attract an additional cost.
7. Further information and advice
For independent and impartial counter terrorism advice and guidance that is site specific, the security manager should establish contact with the local police Counter Terrorism Security Advisor (CTSA).
Your CTSA can:
- support you in assessing the threat, both generally and specifically
- give advice on physical security equipment and its particular application to terrorist attack methodology
- facilitate contact with emergency services and local authority planners to develop appropriate response and business continuity plans
- identify appropriate trade bodies for the supply and installation of security equipment
- offer advice on search plans etc.
It is also advisable to consult with other occupants, partners, stakeholder, neighbours, emergency services and your local authority.
ISO 31000, BS 31100 and ISO 31010 provide further guidance on risk management techniques.
Further Information
Go to the Government Workplace Fire Safety webpage
Go to the Health and Safety Executive Risk Management webpage
You may want to complete the Emergency and Business Continuity checklist
