10 Steps: Executive Companion
Updated 16 January 2015
1. Foreword by Robert Hannigan, Director GCHQ
Two years have passed since we launched the 10 Steps to Cyber Security booklet. Over that period it has become an effective resource in the UK for businesses looking to protect themselves in cyberspace, with around two thirds of the FTSE350 using it. So why are we republishing now?
Quite simply, because those who would do us harm remain busy:
- There have been the high-profile, global cyber incidents such as Gameover ZeuS and Cryptlocker, which between them have defrauded over half a million people worldwide of millions of pounds; or the more recent attack on Sony Pictures which resulted in the leaking of sensitive data as well as a number of the studio’s unreleased films
- Then there are those attacks closer to home, that might not result in the big headlines, but which nevertheless are hugely damaging, both to the UK economy and individuals. The BIS 2014 Information Security Breaches Survey reported that 81% of large organisations had experienced a security breach of some sort. This costs each organisation, on average, between £600,000-£1.5 million and in some cases, the organisation was so badly damaged by the attack that they had to change the nature of their business
- And it is not just financial and reputational losses organisations have to worry about. Hostile activity on the networks of companies that own and operate the UK’s critical infrastructure is a key concern
In GCHQ we continue to see real threats to the UK on a daily basis, and I’m afraid the scale and rate of these attacks shows little sign of abating. The good news is that, despite the increase in sophistication and volume, it remains as true today as it did two years ago there is much you can do to protect your organisation by adopting the basic cyber security procedures in this guidance. The 10 Steps themselves remain the same, but, in response to your feedback, we have simplified some of the presentation and highlighted a number of the new cyber security schemes and services coming out of the National Cyber Security Programme.
Alongside this second version of the 10 Steps we are publishing a new paper, ‘Common Cyber Attacks: Reducing The Impact’. This sets out what a common cyber attack looks like and how attackers typically execute them. We believe understanding the cyber environment and adopting the 10 Steps are effective means of protecting your organisation from these attacks. I hope you will find them useful in managing your own cyber risk and thereby contributing to the UK’s continued rise as a digital nation.
Robert Hannigan, Director GCHQ
2. Cyberspace poses risks as well as opportunities
2.1 What is cyberspace?
Cyberspace is an interactive domain made up of digital networks that is used to store, modify and communicate information. It includes the internet, but also the other information systems that support our businesses, infrastructure and services.
– UK Cyber Security Strategy, 2011.
Common usage of the term also refers to the virtual environment of information and interactions between people.
2.2 Information is critical to today’s business
Information and the ICT (Information and Communication Technologies) that store and process it are critical to business success. Your intellectual property, confidential or sensitive information provide competitive advantage, whether in the form of a product design, a manufacturing and industrial control systems process or a negotiating strategy. At the same time the need to access and share information more widely, using a broad range of connecting technologies is increasing the risk to the corporate information base.
2.3 What is information?
Information, whether financial or about people and systems, is the lifeblood of any organisation. Yet, with increasing automation and interconnectivity of information systems, a compromise in one area could impact the entire organisation and its customers. Information is everywhere from customer facing systems (ATMs, points of sale, mobile phones), to business systems (research data and other intellectual property, management and customer relationship information) and operational systems (safety, protection, process control). When identifying information assets, all of these different areas need to be taken into consideration.
2.4 Compromise of information assets can damage companies
Compromise of information through, for example, staff error or the deliberate actions of an outsider could have a permanent or at least long-term impact on a business. A single successful attack could destroy a company’s financial standing or reputation. Information compromise can lead to material financial loss through loss of productivity, of intellectual property, reputational damage, recovery costs, investigation time, regulatory and legal costs. This could lead to reduced competitive advantage, lower market share, impact on profits, adverse media coverage, bankruptcy, or even, where safety-critical systems may be concerned, loss of life.
In addition to an accurate picture of those information assets that are critical to business success, Boards will wish to reassure themselves that they have regular up-to-date information on the threats and known business vulnerabilities to make informed information risk decisions.
We can all name companies whose cyber security has been very publicly compromised: where it has happened, this has caused tangible damage. Your business is not immune to such attacks.
2.5 Many players pose a risk to information
There are many types of people and organisations who pose a risk to business information assets:
- cyber criminals interested in making money through fraud or from the sale of valuable information
- industrial competitors and foreign intelligence services, interested in gaining an economic advantage for their own companies or countries
- hackers who find interfering with computer systems an enjoyable challenge
- hacktivists who wish to attack companies for political or ideological motives, or just to show they can
- employees, or those who have legitimate access, either by accident or deliberate misuse
2.6 It’s not just about the technology
Many attempts to compromise information involve what is known as social engineering, or the skilful manipulation of people and human nature. It is often easier to trick someone into clicking on a malicious link in an email that they think is from a friend or colleague than it is to hack into a system, particularly if the recipient of the email is busy or distracted. And there are many well documented cases of hackers persuading IT support staff to open up areas of a network or reset passwords, simply by masquerading as someone else over the phone.
2.7 The key is effective enterprise-wide risk management and awareness
Being aware of potential threats is a normal part of risk management across the private sector. Alongside financial, legal, HR and other business risks, companies need to consider what could threaten their critical information assets and what the impact would be if those assets were compromised in some way. The key is mitigating the majority of risks to critical information assets and being better able to reduce the impact of and recover from problems as they arise.
3. Put cyber security on the agenda before it becomes the agenda
A major cyber attack may feel like the stuff of popular culture. It’s not. Although many never hit the headlines, such attacks are increasing in prevalence and scale all the time. The impact of not recognising and pre-empting cyber risks can be long term.
Risks to all forms of information should be treated in the same way as other financial or business risks, especially where threats and vulnerabilities are constantly changing. Ultimate responsibility for cyber security rests at Board level, with the correct governance, management and culture throughout the business. The Board should seek assurance that key information risks are both assessed and prioritised, and that there is regular monitoring where threats and vulnerabilities are constantly changing. The Board should also consider the risks to its personnel and set the value the company places on its various information assets such as company pricing data, business strategies, online services and industrial process control systems, and communicate this throughout the business.
3.1 Do you have the right skills to effectively manage your cyber risk?
Ensure that you have access to people with the right skills levels either within your organisation or through your service providers. Whilst information security as a discipline has been around for a number of years, the additional risks today’s cyberspace brings is not always well understood, requiring people with different skills than many realise. You will need access to a broad spectrum of people including those who can establish the governance and policies needed, those who can ensure your systems are designed to meet your cyber threats, those that can help you identify when you have been compromised and those that can respond and investigate when incidents happen.
3.2 What information should you protect?
All business activity relies on information in a number of forms; it may be supporting corporate management decisions, user access to information, networks or industrial process control systems. Review your information assets and agree which are the most critical to the success and competitive advantage of your company.
3.3 What players might pose a risk to your information?
Understand your likely adversaries and their capabilities. Who might want to gain access to your information or disrupt your business in some way? Your adversary’s abilities and the potential impact they could have on your business will not only determine the sorts of security controls you will need to put in place, but will help gauge the investment needed. If you want to mitigate the risks and impacts from a well-resourced and capable adversary then you will need to invest appropriately. Mitigating the risk from a competitor that could be supported by their national intelligence agency will obviously require more investment than mitigating the risk from a hacktivist group.
3.4 What are the risks to your information and how much risk can you accept?
Identify the risks to information assets. Assess who has access to those assets and who may wish to target the company. Consider the circumstances in which the risks have or could become a reality. Quantify the level of risk to those assets that the business is willing to accept and communicate your risk appetite across the business, especially to those who implement and manage the company’s security. Ensure your assessments keep pace with technological advances, such as Cloud Computing, which may affect the balance of risk over time.
3.5 What measures do you need?
Ensure that your governance framework encompasses information risk across the business and apply the same degree of rigour to these risks as financial and other risk management regimes. Implement security controls and supporting policies that are commensurate with the level of risk that the business is willing to tolerate. To support this process we have identified 10 steps that support a robust information risk and cyber security regime. If any of these areas are not covered in your framework, is there a sound business rationale?
3.6 Do the security measures work?
Regularly review and test the effectiveness of, and adherence to, current controls, and investigate any anomalies. Often well intentioned policies believed to be critical to preventing disaster are not being followed in practice. This could be down to a lack of training, a culture of complacency or simply because they are not usable.
3.7 What would happen to the business if one of your risks became a reality?
Plan for a realistic worst case scenario. Have robust, regularly tested, incident management processes and contingency planning in place to recover from and reduce the impact of any compromises to the business. Understanding why an attack occurred and what was compromised is critical to recovering successfully and protecting the business in the future. The Cyber Incident Responses services can help you with this.
3.8 How do you embed risk management within your company?
Effectively managing the process of assessing risks and implementing controls is essential - both in the business and supply chain. The appropriate people need to be accountable for information and its protection, and should have the right authority, tools and training to achieve this. Use your corporate governance structures such as your audit and risk committees to provide you with confidence that you have the right cyber security posture for the risks you face.
3.9 How can you ensure that you have the best possible understanding of the threat to your business?
Empower selected senior staff to share appropriate information with others in your and related business sectors, both to help build best practice and warn of potential upcoming attacks. Report crime to the relevant agencies to help law enforcement build a fuller picture of the threat to business, share the findings and deploy appropriate support.
4. Ten steps to reduce your cyber risk
Defining and communicating your Board’s Information Risk Management Regime is central to your organisation’s overall cyber security strategy. CESG recommend you review this regime - together with the 9 associated security areas in order to protect your business against the majority of cyber threats.
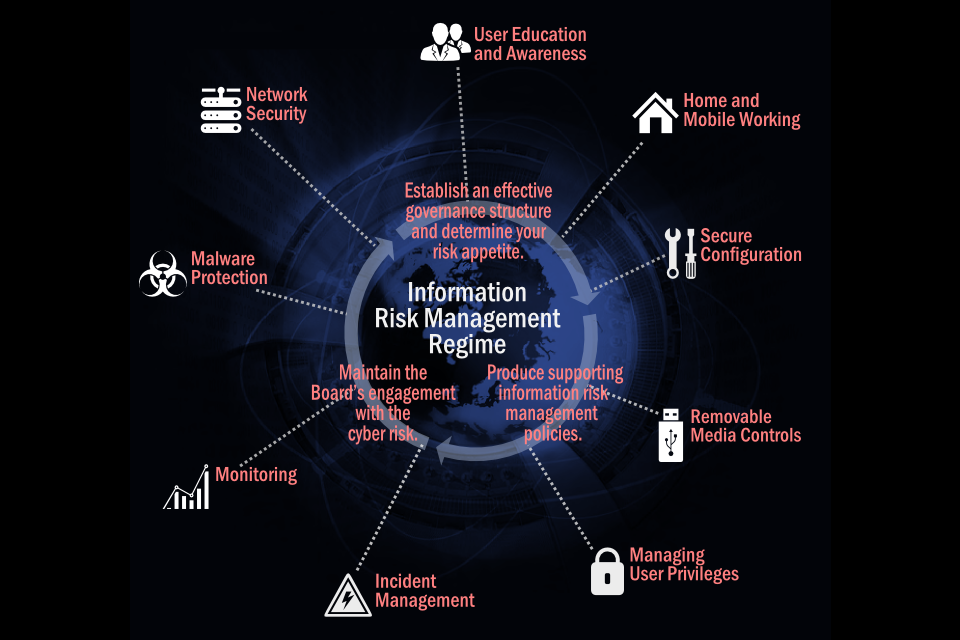
10 Steps to Cyber Security
4.1 Cyber Essentials
The analysis of a number of cyber attacks has shown that time and again attackers are exploiting basic weaknesses in your systems using freely available tools and techniques. Even those who have the resources to develop more sophisticated techniques will usually start with what’s freely available. For many organisations removing these basic weaknesses should be the first step in implementing an effective risk management strategy.
For some organisations effectively implementing these basic controls effectively may be all they need to do in order to mitigate the risk from their particular adversaries. Cyber Essentials defines the minimum set of security controls an organisation (large or small) should have in place. Cyber Essentials has been developed to mitigate the risks from the most common tools and techniques that are available to anyone on the Internet. In recognition of the need to encourage all organisations to implement the basic controls set out in Cyber Essentials, Government has mandated it for certain categories of HMG procurement.
5. Be a hard target - learn from others
GCHQ through its Information Security arm, CESG, has with Cert UK published Common Cyber Attacks: Reducing The Impact. The aim of this paper is to help you understand what a common cyber attack looks like and provide a rationale for establishing basic security controls and processes (such as those set out in the Cyber Essentials Guidance). Understanding this can help you manage the most common cyber risks faced by your organisation on a daily basis.
In recognition of the criticality of improving cyber defences, GCHQ has included case studies based on real incidents where commodity tools and techniques have been used successfully in attacks against UK organisations. The key principles of the 10 Steps can help to mitigate or prevent these attacks.
6. Managing cyber risks within corporate governance
Like other corporate risks, cyber risks need to be managed proactively by the Board, led by senior management and assured by corporate governance. A model for managing cyber risks is suggested below. Implementation will clearly need to reflect the nature of your business and your appetite for risk.
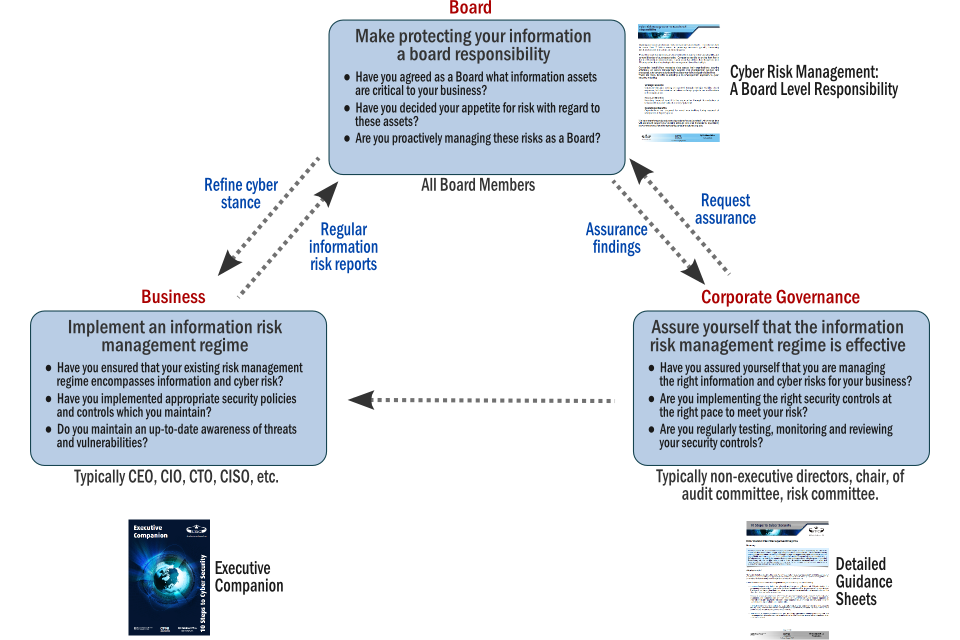
10 Steps: A Board Level Responsibility
7. Cyber security: the next steps
If you are uncertain about your company’s ability to manage its information risks, here are some practical steps that can be taken through corporate governance mechanisms:
- confirm that you have identified your key information assets and the impact on your business if they were to be compromised
- confirm that you have clearly identified the key threats to your information assets and set an appetite for the associated risks
- consider gaining independent verification that you are appropriately managing the cyber risks to your information and have the necessary security policies and processes in place
- confirm that you have processes in place that can support continual improvement
Companies may not have all the expertise needed to implement some of these steps and assure themselves that the measures they have in place meet today’s threats; in the first instance audit partners should be able to provide assistance. For information risk management expertise, organisations should seek advice from members of appropriate professional bodies or those who have attained industry recognised qualifications.
8. Cyber security: schemes and services
There is a variety of advice, services and products available to help with cyber security. Listed below are various initiatives that have been set up by government (CESG and CPNI) with the aim of ensuring the quality of the services provided.
Need cyber security training?
The CESG Certified Training (CCT) Scheme is designed to assure high quality cyber security training courses delivered by training providers. The CCT scheme offers UK cyber security professionals the opportunity to gain appropriate knowledge and skills through training and is useful for anyone seeking to improve or acquire cyber security skills.
Need to find organisations that can help clean up after a cyber incident?
Cyber Incident Response (CIR) services provide access to organisations certified by CESG and CPNI to respond effectively to cyber incidents.
Need to know more about how to protect your organisation against common cyber attacks?
- Cyber Essentials is a government-backed, industry supported scheme to help organisations protect themselves against common cyber attacks. Organisations are awarded the Cyber Essentials badge (provided they meet the standard) and demand is expected to grow as Government mandate Cyber Essentials for certain categories of HMG procurement.
- CERT-UK is the UK National Computer Emergency Response Team, formed in March 2014 in response to the National Cyber Security Strategy. CERT-UK works with partners across industry, government and academia to enhance the UK’s cyber resilience.
Need cyber security specialists?
The CESG Certified Professional (CCP) scheme has been developed to address the growing need for specialists within the cyber security profession and is building a community of recognised professionals in both the UK public and private sectors. CCP has been acknowledged as HMG’s standard for cyber security professionals.
Sharing information – where do I go?
CPNI Information Exchanges allow information to be shared amongst trusted contacts: this is key to successful security planning in many sectors. Where appropriate information is also shared about threats, vulnerabilities and effective mitigation measures, so that businesses and organisations in the national infrastructure can protect their assets better.
Need a penetration tester?
CHECK enables penetration testing by CESG approved companies, employing penetration testing personnel qualified to assess HMG and other public sector bodies.
Other CESG guidance published on www.gov.uk
- Bring Your Own Device (BYOD) Guidance: this guidance is for organisations considering a Bring Your Own Device (BYOD) approach, and describes the key security aspects to consider in order to maximise the benefits of BYOD whilst minimising the risks. It also provides a useful reminder for those already implementing a BYOD approach.
- End User Devices Guidance: this guidance is for public sector organisations to follow when deploying end user devices for remote working at OFFICIAL.
- Cloud Security Guidance: this guidance is for public sector organisations who are considering using cloud services for handling OFFICIAL information. This guidance will also help cloud service providers present their services to public sector consumers in a consistent and comparable fashion.
- Browser Security Guidance: this ALPHA guidance is for the use of web browsers to access enterprise web applications and browse the Internet. It describes the key security aspects to consider when deploying web browsers while maximising the benefits of using modern products. It is particularly relevant for public sector organisations operating at OFFICIAL.
GCHQ through its Information Security arm, CESG, has with Cert UK produced a paper entitled: Common Cyber Attacks: Reducing The Impact. The aim of this paper is to help you understand what a common cyber attack looks like and provide a rationale for establishing basic security controls and processes (such as those set out in the Cyber Essentials Guidance). Understanding this can help you manage the most common cyber risks faced by your organisation on a daily basis.
