Emerging technologies and their effect on cyber security
Published 8 August 2025
1. Executive summary
The convergence of emerging technologies is transforming industries, introducing both opportunities and unprecedented cyber security challenges. This paper explores the synergistic relationships between technologies such as Artificial Intelligence (AI), Blockchain, the Internet of Things (IoT), Edge Computing, Quantum Computing, and Brain-Computer Interfaces, analysing how their intersections reshape the cyber threat landscape.
Through a comprehensive review of the literature and real-world case studies, the study also identifies and highlights key vulnerabilities arising from these technological pairings. For example, although AI’s integration with IoT and Blockchain enhances threat detection and automation, it also amplifies risks such as adversarial attacks and data privacy concerns. Equally, the fusion of Edge Computing with IoT improves real-time decision-making but expands the attack surface, making distributed systems more susceptible to cyber threats. Moreover, quantum computing, particularly in combination with Low Earth Orbit (LEO) satellites, promises enhanced security for communication networks but introduces novel risks, such as side-channel attacks and denial-of-service vulnerabilities.
Additionally, the application of AI and Digital Twins in personalised medicine, defence, and critical infrastructure presents new cyber security risks, including data manipulation, privacy breaches, and cyber-physical system exploitation. Subsequently, the findings underscore the urgency for proactive security strategies, interdisciplinary collaboration, and the development of robust frameworks to mitigate evolving cyber threats. The report herein underlines that addressing these cyber security risks becomes imperative, as technology convergence accelerates, to ensure the resilience and security of interconnected systems across industries.
2. Introduction
In an era where technological advancements unfold at an unprecedented pace, the merging of once distinct technologies—known as technological convergence—is reshaping industries, driving innovation, and altering the cyber security landscape. As technologies like artificial intelligence, quantum computing, 6G networks, edge computing, nanotechnologies, and robotics increasingly intersect, they create both unprecedented opportunities and complex vulnerabilities.
Historical precedents highlight the significant impact of technological convergence on cyber security. For instance, the merging of mobile devices with the Internet of Things (IoT) expanded the attack surface dramatically. The proliferation of inexpensive, limited-processing devices that are often poorly managed and insecure by default led to events like the Mirai botnet attack in 2016. This large-scale distributed denial-of-service (DDoS) attack disrupted major platforms such as Dyn DNS, Twitter, and Netflix. This led to the need for policy interventions like the Product Security and Telecommunications Infrastructure Act 2022 to enhance the security of internet-connected products.
Another example is the integration of Operational Technology (OT) with Information Technology (IT) systems in critical infrastructure like energy grids, transportation, and manufacturing. The Stuxnet worm in 2010, which targeted Iranian nuclear facilities, demonstrated how convergence could enable targeted attacks on critical systems. This incident introduced the world to cyber-kinetic warfare, where cyber-attacks have physical impacts, and highlighted that systems not originally designed to face IT-based threats are now vulnerable due to technological convergence.
However, we also see security benefits from convergence - the combination of Machine Learning (ML) and threat detection has significantly advanced cyber security capabilities. Tools such as CrowdStrike’s Falcon platform and Darktrace’s AI systems utilise ML to detect anomalies in real time, enabling proactive responses to emerging threats. These technologies go beyond traditional rule-based systems by identifying novel patterns of malicious activity, allowing organisations to respond dynamically.
More recently, the combination of social engineering techniques with AI-generated deep-fakes has heightened cyber security risks. Highly convincing phishing attacks now leverage AI to create realistic deep-fake media, such as voice impersonations, leading to significant financial losses in cases where executives were impersonated to authorise fraudulent transactions. These developments have prompted a focus on detecting synthetic media, developing authenticity verification tools, and educating users about social engineering resilience.
Initiating research into the cyber security implications of technological convergence presents significant challenges. The vast scope of emerging technologies, coupled with a scarcity of documented information and the subtle nature of convergence—which often occurs without explicit recognition—complicates efforts to identify and assess potential risks. In this report we conduct a systematic review to illuminate the converged technology pairings and groupings most pertinent to cyber security concerns.
This report aims to define emerging converged technologies relevant to cyber security over the next five to ten years and beyond. Focusing on literature published from 2021 onwards, it will identify key technology pairings that are poised to significantly influence the cyber security domain by shaping both the nature and scale of cyber threats, altering the prevalence of cyberattacks, introducing new attack vectors, and enhancing cyber defence mechanisms through novel detection and mitigation strategies.
By consolidating convergent technology pairings and groupings identified in recent literature, we provide an overview of the current landscape. We offer recommendations on technology convergences of particular interest, specifying the industries or sectors where these are likely to be most prevalent, and through detailed case studies of converged technologies in specific settings, we highlight where convergence is expected to produce novel or compounding cyber security risks.
3. Definitions of emerging technologies and pairings
Technologies rarely develop in a vacuum, instead they are built on the shoulders of the technologies that came before them; new insights mean that prior developments can be iterated upon and combined with other technologies, for new uses. We often find that existing, or developing technologies can be combined with other technologies to provide new uses and improve capability or effectiveness. This is what we call technology convergence.
Technology Convergence - The tendency for technologies that were originally unrelated to become more closely integrated and even unified as they develop and advance. [footnote 1]
In this report, we are considering the convergence of emerging technologies. Rotolo et al. [footnote 2] identify five attributes that define an emerging technology - radical novelty, relatively fast growth, coherence, prominent impact, and uncertainty and ambiguity. For the purposes of this report, we are making use of technologies identified as emerging by third parties (principally UKRI), but we use the following definition of an emerging technology, which aligns with [footnote 2].
Emerging Technology - a technology whose development, practical applications, or both are largely unrealised. These technologies are generally new, but also may include old technologies finding new applications. Emerging technologies are often perceived as capable of changing the status quo.
For the purposes of this research, when two technologies converge together, we call this a converging technology pairing. We define this to be:
Converged Technology Pairing - Two technologies that are likely to converge as they develop, as each technology supports and augments the capability of the other.
Similarly, we may find that larger groups of technologies converge, we define these as technology groupings:
Converged Technology Grouping - A group of more than two technologies that are likely to converge as they develop, as each technology augments the capability of the group.
In reality, pairings and groupings will not always be balanced and bi-directional. For example, later in this report, we consider the pairing of Quantum Communications with Low Earth Orbit Satellites - though there are a small number of applications where the capabilities of Low Earth Orbit Satellites might be augmented by Quantum Communications, Low Earth Orbit Satellites are likely to be a key enabling technology for Quantum Communications. Some technologies, for example AI, are likely to be more fundamental - a pairing might augment the capabilities of AI in a specific context, or to help with a specific use case, but not materially affect use of the technology as a whole.
Where the convergence of technologies enable a practical use of technologies, we define this as an application.
Technology Application - A group of technologies come together to enable specific tasks, solve a problem, or meet user needs.
A technology application can also be a technology itself - computers and telecommunications converged to enable the internet, which could reasonably be defined as an application, whilst clearly the internet has converged with many other technologies to provide additional applications. For example, in this report we consider automated vehicles as a use case and application, which requires the convergence of technologies such as AI and IoT among others - despite Automated Vehicles likely being a technology that will enable other applications, describing it as an application remains useful as a term to explore the convergence of technologies that enable it.
4. Methodology
This section outlines the structured process undertaken to deliver the report examining the cyber security implications of the convergence of emerging technologies. The approach combined systematic literature review techniques with expert validation and categorisation to identify critical technology pairings, their risks, and their impacts on specific industries.
4.1 Research questions
The systematic review will seek to answer three key questions:
-
Which groups or pairings of emerging technologies are likely to create novel or compounding cyber security risks?
-
Which industries will be affected by the compounding cyber security risks stemming from convergence of emerging technologies?
-
Which applications of emerging technologies are most likely to be affected by technology convergence?
4.2 Stage 1: Construction of long list
Our initial list of emerging technologies was informed by authoritative reports on emerging technologies, making use of analyses of emerging technologies by diverse viewpoints from industry, government and defence, research institutions.
Key documents and publications included:
-
URKI’s report "Innovate UK’s 50 Emerging Technologies", representing a government-led perspective on future technology trends and potential areas of strategic focus. [footnote 3].
-
NATO Science and Technology Trends 2023–2043 [footnote 4], offering defence-oriented insights into technologies deemed critical for security and operational advantage over the next two decades.
-
McKinsey Technology Trends Outlook 2024 [footnote 5], reflecting a global industry and market-based perspective on emerging technology trajectories, commercial relevance, and investment patterns.
By synthesising these sources, the study captured a multidimensional view of emerging technologies, ensuring that public-sector priorities (e.g., government-led innovation programs, national security) were balanced with private-sector imperatives (e.g., commercial viability, market adoption).
Each technology identified through these sources was entered into an initial master table.
4.3 Stage 2: Initial prioritisation of Technologies, and technology pairings
To develop a short-list of technology groupings, we made an initial assessment of the technologies, following the below criteria:
-
Time to Operationalise: We determined whether the technology is expected to be widely operationalised, beyond small-scale pilots and niche use-cases, within the next 5 years. Technologies that are unlikely to reach a sufficient level of maturity or adoption in the near term will have limited immediate cyber security impact and were therefore de-prioritised in this review. Where possible we used Technology Readiness Levels from research and publications including from strategic roadmaps such as McKinsey Reports and forecast models such as Gartner Hype Cycle to gauge near-term feasibility and commercial viability. A binary Yes/No decision was made on whether there was indication that the technology would be widely operationalised within the next 5 years. Those with limited or contradictory evidence regarding near-term viability were excluded.
-
Potential Cyber Security Impact: We assessed both the intensity (disruptiveness to existing cyber systems and processes) and the breadth (range of cyber domains that could be affected) of each technology. Sources such as McKinsey Reports, and Gartner Hype Cycle were used to enable us to categorise each technology on a high, Medium and Low scale as described below:
-
Intensity The degree to which a given technology disrupts or transforms existing cyber security systems, processes, or paradigms.
-
High indicates the potential introduction of fundamentally new threats or paradigm shifts that require substantial revision of current cyber security practices.
-
Medium indicates moderate disruptiveness that may require some adjustments to existing systems but does not wholly redefine them.
-
Low indicates minimal disruption or incremental improvements, suggesting that core cyber security practices remain largely unchanged.
-
-
Breadth The range of cyber security domains the technology may affect.
-
High suggests a broad impact across all cyber security domains.
-
Medium indicates a moderate scope, affecting several cyber security domains.
-
Low denotes a narrow or specialised influence, typically confined to a single domain.
-
-
-
UK Government Prioritisation: This evaluation included examining government policy documents, strategic roadmaps, and funding initiatives to determine whether the technology fell under the DSIT’s UK Science and Technology Framework [footnote 6], specifically relating to Artificial Intelligence, Engineering Biology, Future Telecommunications, Semiconductors, and Quantum Technologies. Based on this analysis, a binary rating (Yes/No) was applied to indicate whether the technology was formally identified within these priority areas.
Figure 1 illustrates this process.
Figure 1: the longlist development process.
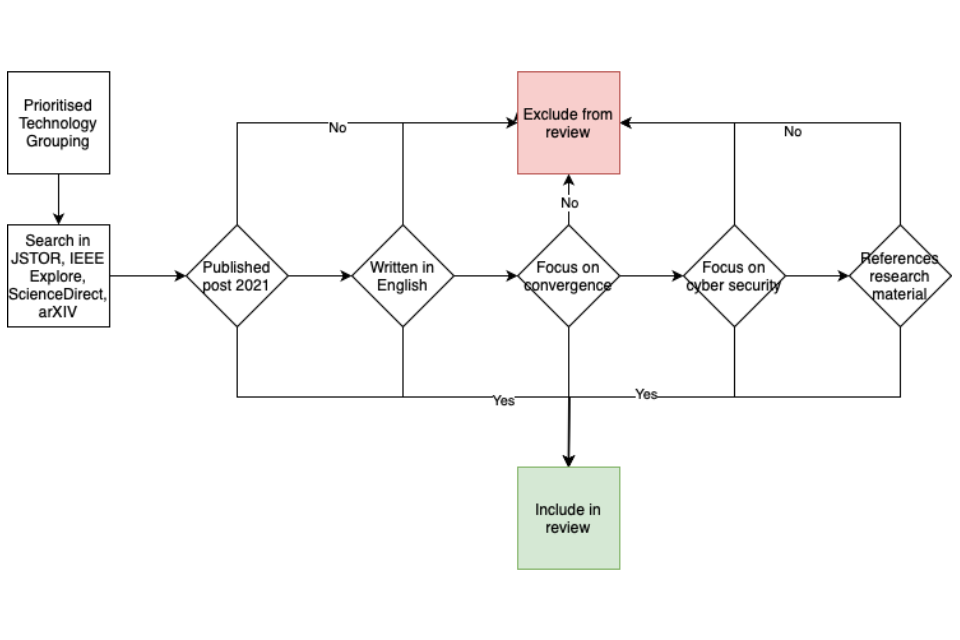
4.3.1 Pairings and groupings
The technology shortlist agreed with DSIT (see Table 1) contained a total of 46 emerging technologies. Considering just pairings (as opposed to groupings), this leads to a total of 1035 combinations - too many to assess manually.
To assist in this process, we automated searching Google Scholar, scraping the total number of results for the search terms "Technology 1" "Technology 2" cyber in the time period 2021-2024. Though Google Scholar is not a peer-reviewed academic source, it is widely regarded as a search engine for academic publications and a research tool that serves as a gateway to peer-reviewed contend and scholarly materials. As centralised and accessible collection point, this method allowed for the qualification of prioritised technology pairings phased on the volume of discussion in academic literature.
To ensure that naming conventions didn’t distort the shortlist - we grouped some technologies into broader groups to be searched - including AI related technologies, which were searched as "Artificial Intelligence".
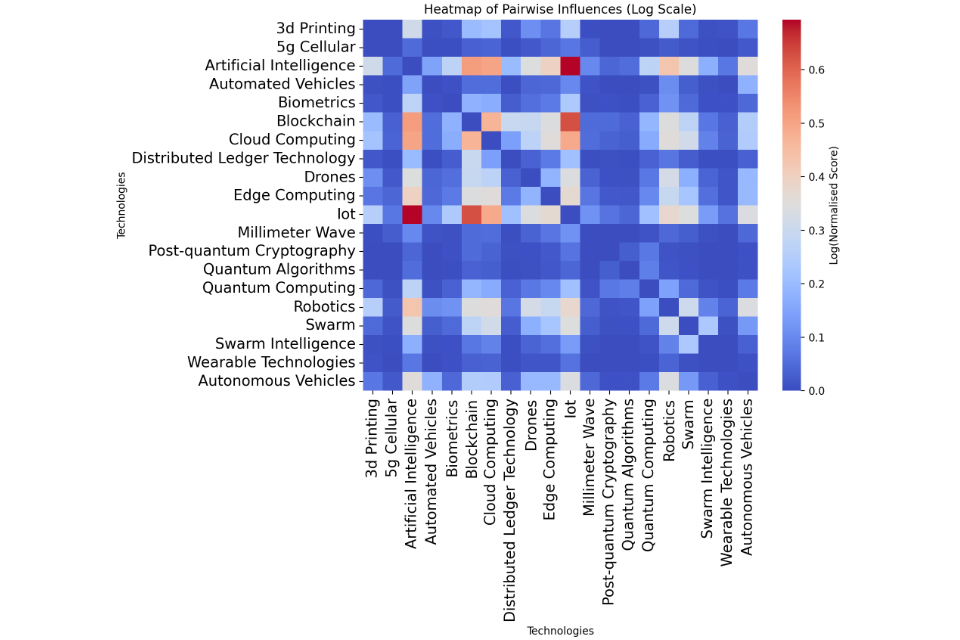
The result of the script listed the technologies that appear together most in literature. Figure 2 shows the 20 most commonly paired technologies in our initial analysis, while Figure 3 shows the most common pairings.
Figure 2: The 20 most commonly paired technologies. The normalised influence score is the sum of the Google Scholar search results for a given technology, normalised to be between 0 and 1.
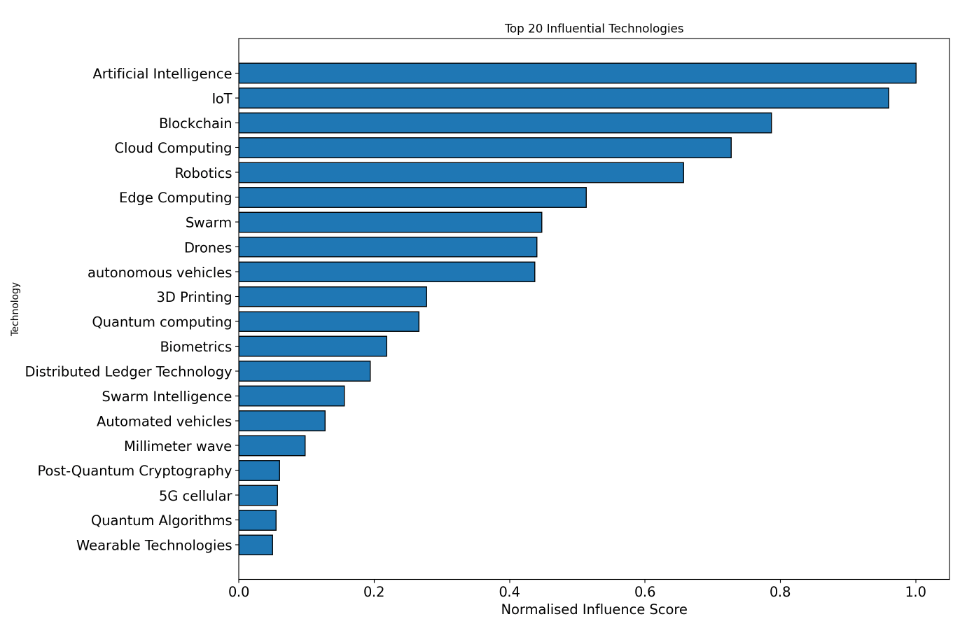
Figure 3: A heat map showing the most common technology pairings, restricted to the top 20 technologies for readability reasons.
| Shortlisted Technology | Shortlisted Technology | Shortlisted Technology |
|---|---|---|
| Very Low Orbit Satellites | 5G Cellular | 6G Cellular |
| 3D Printing | Automated Vehicles | Autonomous Vehicles |
| Artificial Intelligence | Biological Computing | Biometrics |
| Bioelectronics | Brain-computer Interfaces | Cloud Computing |
| Blockchain | DNA Data Storage | Drones |
| Distributed Ledger Technology | Electroceuticals | IoT |
| Edge Computing | Low Power Wide Area Networks | Millimetre Wave |
| Low Earth Orbit Satellites | Neuromorphic Computing | Neurotechnology |
| Nanoscale Robotics | Personalised Medicine | Photon Generators |
| Nuclear Fusion | Post-Quantum Cryptography | Private 5G Networks |
| Photonic Computing | Quantum Communications | Quantum Computing |
| Quantum Algorithms | Robotics | Room Temperature Superconductors |
| Quantum Sensing | Sensation Detection Implants | Space-based Solar Power |
| Satellite Platforms | Swarm Intelligence | Terahertz Radio |
| Swarm | Wearable Technologies | Wi-Fi 7 |
Table 1 : The technology shortlist agreed with DSIT, following our initial assessment of the technologies.
Not unexpectedly, this analysis revealed a dominance of pairings involving a small number of technologies, particularly those such as AI, which frequently appeared alongside other technologies. We were not able to review all pairings, and selecting only the most influential pairings would mean a very narrow focus for our review. To provide breadth for the report, we chose our studied pairings using the following criteria:
- Technology 1 was chosen from the list of most influential technologies (shown in Figure 2.)
This ensures the depth of the report, ensuring that the most influential technologies are considered in the review. We focused on technologies expected to mature in the timescale for this report, and on more fundamental technologies.
- Technology 2 was chosen from the technology shortlist, with the goal of developing the breadth of the report.
Each technology in the shortlist has already been assessed as suitable through our shortlist generation process. As part of this selection process, we chose combinations that scored highly in our preliminary searches of Google Scholar, to attempt to ensure a sufficient breadth of research considering the combination of technologies.
These combinations of Technology 1 + Technology 2 led us to the pairings considered as part of this report, which are:
-
Biological Computing and IoT
-
Personalised Medicine and Artificial Intelligence
-
Digital Twins and Artificial Intelligence
-
Swarm and Neurotechnology
-
Low Earth Orbit Satellites and Quantum Communications
-
Artificial Intelligence and Quantum Sensing
-
Brain-Computer Interfaces and Robotics
-
Quantum Communications and IoT
-
Artificial Intelligence and IoT
-
Blockchain and Artificial Intelligence
-
Edge Computing and IoT
These pairings are taken through to the Systematic Literature Review process.
4.4 Stage 3: Systematic literature review
We follow a systematic approach for each of our pairings, following the below process.
-
Phase 1a: We search across the following academic repositories:
-
JSTOR
-
IEEE Xplore
-
Science Direct
-
arXiv
-
using the following search terms - "Technology 1 + Technology 2 + Convergence|Converge|Synergy + Cyber|Security"
-
Phase 1b: In the case that our search terms do not lead to significant results, we rerun the search with the following search term - "Technology 1 + Technology 2 + Cyber|Security"
-
Phase 2: We search across a range of grey literature sources (list attached as Appendix 9 to this document), using the search terms - "Technology 1 + Technology 2 + Convergence|Converge|Synergy + Cyber|Security". Grey literature will be identified using Google searches, restricting to our identified sources using a "Site:" modifier.
-
Phase 3: Each identified relevant paper is be assessed using the following criteria:
-
Focuses on the technology pairing/grouping in scope.
-
Written in English
-
Must be a respected peer-reviewed academic journal article, academic review, arXiv or industry publication.
-
Must reference research material.
-
Published post November 2021 (3 years prior to this project)
-
Predominantly focusing on the effects of converging technologies and cyber security.
-
-
Phase 4: Once each paper is assessed according to Phase 3, we examine the references in each paper, and repeat the process of Phase 3 on each newly identified paper. This is conducted to a depth of one level from the initial search.
The diagram below illustrates this process.
Figure 4: The systematic review process.

4.5 Research Limitations
This study is subject to several limitations that should be acknowledged. One of the primary constraints is the novelty of some of the technological pairings discussed. While some convergences, such as AI and IoT, have been widely studied, others—particularly emerging pairings like biological computing and IoT or quantum communications and LEO satellites—have far less research available. As a result, the analysis in these areas is necessarily limited and, in some cases, relies on broader discussions of digitisation and technology adoption rather than specific cyber security insights.
Another key limitation is that not all reviewed papers directly addressed cyber security risks. While some pairings had meaningful discussions on security threats, others were more focused on operational efficiencies, technical feasibility, or broader industry applications. In these cases, cyber security implications had to be inferred from related discussions, which may introduce some degree of interpretation.
A number of false positives arose when using “Cyber” as a keyword, particularly in the context of Digital Twins. While the initial search yielded over 1,500 publications, many of these focused on Cyber-Physical Systems or referred to digitised versions of physical systems—sometimes even referring to the Metaverse—rather than cyber security. Additional exclusions were therefore made for papers addressing security issues beyond the scope of this review (e.g., logistics security, supply chain integrity, and food safety).
Some works were excluded due to superficial engagement with cyber security — treating it merely as a general concern without offering substantive analysis, specific risk identification, or evidence-based mitigation strategies. In contrast, certain technology pairings (e.g., personalised medicine, biotechnology, and IoT) included discussions of novel research such as DNA encryption, Particle Swarm Optimisation, and emerging attacks like black-hole and sentry attacks. However, this emphasis on innovative security challenges was not uniformly present across all pairings. Where it did appear, it was captured because of its direct relevance to the research questions.
Language and regional focus also present constraints. The review was conducted using English-language sources, which may have led to the exclusion of relevant insights from non-English publications. Furthermore, many of the reviewed sources originate from specific regions, meaning that findings may reflect regional priorities, regulatory landscapes, and industry-specific concerns rather than a fully global perspective.
Finally, the fast-evolving nature of emerging technologies means that cyber security risks will continue to develop alongside new use cases and threats. Although this study provides a snapshot of current risks, future research will be needed to track how these threats evolve as adoption increases and adversaries adapt their tactics. Despite these limitations, the findings offer a valuable starting point for understanding the cyber security challenges introduced by technology convergence and highlight key areas for further exploration.
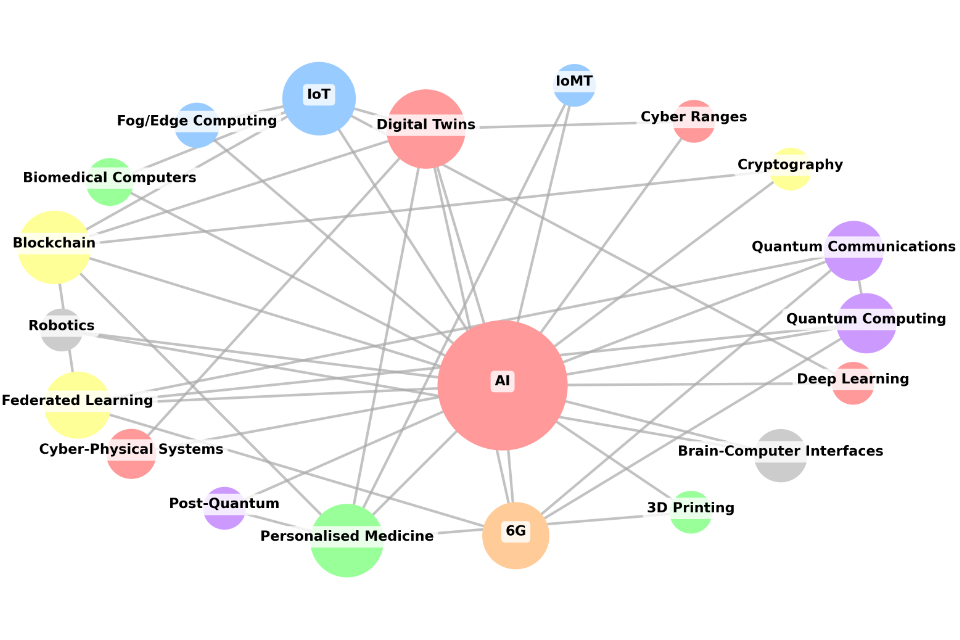
Figure 5: This graph displays the connections between technologies identified as part of our technology groupings, developed through the literature review, including only those technologies that are linked to AI. The colour of the bubbles indicate broad technology groupings, and the size of the bubbles is proportional to the number of connections for each technology.
5. Literature review
In this section of the report, we perform the systematic literature review as described in section 4, reviewing our shortlisted technology pairings, and highlighting cyber security considerations and potential groupings.
Table 2 shows the number of papers identified during the initial search phase, and following the selection of relevant papers. The selected technology pairings are presented in descending order of the number of papers included in the review.
| Pairing | Research Papers (Initial Search) | Research Papers Included |
|---|---|---|
| Digital Twins + Artificial Intelligence | 2083 | 27 |
| Blockchain + Artificial Intelligence | 75 | 19 |
| Artificial Intelligence + IoT | 264 | 18 |
| Artificial Intelligence + Personalised Medicine | 241 | 18 |
| Quantum Communications + IoT | 250 | 18 |
| Low Earth Orbit Satellites + Quantum Communications | 28 | 11 |
| Edge Computing + IoT | 112 | 8 |
| Brain Computer Interfaces + Robotics | 268 | 7 |
| Biological Computing + IoT | 2 | 5 |
| Artificial Intelligence + Quantum Sensing | 42 | 1 |
| Swarm Technology + Neurotechnology | 0 | 0 |
Table 2 : The number of research papers identified at each stage of our searches.
5.1 Digital Twins and Artificial Intelligence
5.1.1 Identified Groupings
-
AI + Digital Twins + Cyber-Physical Systems / Cyber- Physical Production Systems
-
AI + Digital Twins + Blockchain
-
AI + Digital Twins + IoT
-
AI + Digital Twins + 6G
-
AI + Digital Twins + Industry 4.0 / 5.0
-
AI + Digital Twin + Cyber Ranges
5.1.2 Summary of Digital Twins and AI
A Digital Twin is commonly defined as a virtual representation of a real-world system, object, or process, which includes real-time data and simulations to monitor, analyse, and optimise the performance of its physical counterpart. The concept was first introduced by NASA in the early 2000s to create a virtual representation of the Mars Rover for performance analysis and optimisation [footnote 7]. Digital twins are designed to improve decision-making, efficiency, and cost savings across industries by enabling real-time monitoring and predictive maintenance [footnote 7] [footnote 8].
The terms cyber-twin, cyber-range, and digital twin are often used synonymously, though they represent distinct yet interconnected concepts. A cyber-twin is closely related to a digital twin but is primarily focused on the digital representation of cyber systems and networks rather than physical assets.[footnote 9] A cyber-range refers to a virtual environment used for simulating and testing cyber security scenarios, often integrating digital twins to evaluate system resilience against cyber threats.[footnote 10]
AI also enhances digital twins by improving situational awareness and risk assessment, particularly in cyber security applications. For example, AI-powered digital twins can analyse historical and real-time data to predict and mitigate cyber threats, improving system resilience and proactive security management.[footnote 11] Techniques like transfer learning further allow digital twins to adapt to dynamic operational conditions, reducing the need for manual reconfiguration.[footnote 12]
Excluded Literature
The initial literature review identified a substantial body of work, exceeding 1,500 papers. A significant portion was excluded as many references to "Cyber" pertained to Cyber-Physical Systems with no reference to cyber security. Among the remaining papers, numerous were further excluded during the review process for their limited engagement with cyber security topics, often mentioning it as a generic challenge or concern without providing substantive analysis, specific risk identification, or evidence-based mitigation strategies.
Additional exclusions were made for papers focused on security issues outside the scope of this review, such as logistics security, supply chain integrity, and food safety.
Finally, papers were also excluded where the concept of a Digital Twin was conflated with the Metaverse, which did not align with the definition established in the introduction that defines a DT as a virtual representation of a physical asset rather than a purely virtual environment.
5.1.3 Digital Twins and AI Cyber Implications
Data Security, Privacy and Intellectual Property
In a survey conducted by Xu [footnote 13] on cyber security considerations in the context of Digital Twins and the Industrial Internet of Things (DT-IIoT), the authors identified that there was a research gap concluded that no existing studies provide a holistic examination of DT-IIoT encompassing state-of-the-art artificial intelligence (AI), advanced cyber security mechanisms, software tools, and practical case studies, demonstrating the need for more research in this domain.
Many papers have been released since the publication of Xu’s survey, with some consideration of cyber security, like the implementation of transport-specific applications described by Koroniotis [footnote 9] and Yigit [footnote 14], which will inform a Case Study later in this paper.
The overwhelming majority of papers discuss Data Security, Privacy and Intellectual Property as the most common risk associated with Digital-Twins and AI. Data manipulation, integrity and Quality was the second most common area of risk.
AI-enabled Digital Twins (DTs) introduce data security, privacy, and intellectual property challenges due to their reliance on large-scale data collection from extensive networks of Internet of Things (IoT) devices. Xu emphasises that the creation of a new virtual domain, where massive data exchanges occur across virtual, cyber, and physical spaces, significantly amplifies the complexity of securing such systems [footnote 12]. This extensive data flow from interconnected devices raises concerns around data confidentiality, integrity, and authenticity, particularly when sensitive operational data or personal information is involved.
Ferrag highlights that while federated learning can enhance privacy by limiting data transfer, it introduces vulnerabilities such as poisoning attacks that can degrade the reliability of AI-driven digital twins [footnote 15]. Similarly, Hossain and Abdulrahman that federated learning, while beneficial for handling large data volumes, presents challenges in maintaining data consistency and trust when applied across decentralised systems [^10] [footnote 16]. Zafar talks about data sensitivity processed by Digital Twins, particularly IP and discusses the need for the implementation of security controls, referencing many traditional IT security controls such as firewalls, IDS, audits, patching etc.
Ridhawi expands on these challenges within DT-enabled 6G networks, where vast numbers of interconnected devices are involved in data sharing, communication, and service provisioning. He notes that conventional security mechanisms like Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) struggle to maintain trust and security at this scale. To address these risks, he advocates for a zero-trust architecture, emphasising the need for continuous device validation, frequent auditing, and behaviour analysis to ensure a highly controlled network environment [footnote 17]. However, he also highlights limitations of current zero-trust models, as many rely on centralised key management and access control, which may still pose risks and fail to scale effectively in complex, distributed DT environments. Jagannath supports this perspective, discussing zero-trust as a critical framework for securing data-driven networks [footnote 18]. This is further supported by Menon, who discusses the need for a secure-by-design and privacy-by-design approach.
The intellectual property risks associated with DTs also arise from the exposure of proprietary designs, operational data, and AI models. Unauthorised access or tampering with these datasets can lead to IP theft or competitive disadvantages. Wang details multiple threats, including data tampering, de-synchronisation attacks, and model poisoning, all of which could compromise decision-making accuracy and physical asset safety [footnote 7].
Data manipulation, integrity and Quality
Ensuring the integrity, accuracy, and reliability of data used in DT systems is critical, as data quality directly influences decision-making, operational safety, and security resilience, potentially even impacting real-world operations.
- Data Tampering and Quality Degradation Wang provides possibly the most comprehensive analysis of the risks associated with data tampering and quality degradation in DT ecosystems, identifying several threats including unauthorised modification, data forgery, and injection of low-quality or misleading data into the digital model [footnote 7]. These attacks can result in corrupted virtual models, which may lead to inaccurate decision-making, physical asset damage, and operational failures. Wang continues, discussing Physical Damage Attacks: Compromising DTs to affect critical physical infrastructure and Single Point of Failure (SPoF) that could lead to disruption of essential nodes leading to widespread system failures. Zeb et al. expands on this concern, emphasising that sharing data across geo-distributed peers increases security risks, as variations in data quality and validation standards can lead to the propagation of erroneous or unverified data across the DT network [footnote 19].
Suhail further highlights that erroneous data insertion can compromise both the digital and physical assets, especially when dealing with multimodal heterogeneous sensor environments where data originates from multiple sources with varying levels of trust [footnote 20]. This risk is amplified when data inconsistencies arise due to synchronization issues between the virtual and physical systems, a concern also noted by Wang in his discussion of de-synchronisation attacks [footnote 7].
-
Model Poisoning and Manipulation Attacks Wang [footnote 7] emphasises the risk of model poisoning attacks, where malicious actors introduce altered data samples or tamper with the underlying AI models to degrade the accuracy of decision-making processes. These attacks can be subtle, making them challenging to detect, especially in complex AI-driven DT environments where vast amounts of data are processed continuously.
-
Data Trustworthiness and Origin Validation Later in this document we discuss Blockchain as an overwhelmingly popular mechanism for securing data integrity. Suhail [^20) raises the point that whilst it is often considered a silver bullet, it does not inherently guarantee data trustworthiness at the point of origin. Blockchain ensures immutability and traceability only after the data has been processed by validated devices and confirmed at the source. This gap in initial data validation creates a vulnerability where corrupted or manipulated data can still enter the DT system undetected, particularly in environments with multiple data sources or decentralised inputs.
AI-Enabled Digital Twins and Blockchain
Blockchain technology has emerged as a promising solution to address the security challenges associated with Digital Twins (DTs), with around half of the literature making reference to it as a mechanism to mitigate specific cyber threats and enhance data security and transparency in digital twin architectures.
Xu [footnote 21] identified multiple works where blockchain and other security frameworks were applied to DT-IIoT environments. For instance, Danilczyk [footnote 22] proposed a digital twin security framework for micro-grids designed to detect cyberattacks such as denial-of-service (DoS) attacks. Saad et al [footnote 23] explored a digital twin-based approach for detecting and mitigating DoS attacks in micro-grids. These contributions emphasise blockchain’s potential to provide decentralised security mechanisms that can safeguard critical energy infrastructure.
For broader DT-IIoT applications, Lu et al. [footnote 24] investigated a blockchain-based federated learning approach that ensures data privacy and security within edge communication networks. Maillet-Contoz et al. [footnote 25] further proposed an end-to-end security layer to validate IoT system security in digital twins. Zhang et al. [footnote 26] applied deep learning techniques for vulnerability detection in healthcare digital twins, while Hasan et al. [footnote 27] and Dietz et al. [footnote 28] explored blockchain-based digital twin architectures for securing data sharing and lifecycle management, highlighting the advantages of distributed ledgers in ensuring data immutability and integrity.
Toderan [footnote 29] extended the discussion on blockchain’s security potential, particularly for mitigating threats such as denial-of-service and session hijacking in edge, fog, and cloud environments. The author discusses how blockchain’s decentralised ledger and smart contracts can enhance energy data security, automate demand response (DR) programmes, and validate decision-making processes securely.
Suvarna [footnote 30] and Rame [footnote 31] both discuss blockchain’s role in enhancing transparency and data security in digital twins. Suvarna specifically discusses the use of blockchain for secure edge device management, while Rame explores its broader implications for data transparency and cyber resilience.
Soori [footnote 32] further elaborates on blockchain’s cryptographic capabilities, noting that its decentralised nature ensures the immutability of smart contracts, thus preventing unauthorised alterations to data. Additionally, Soori suggests that combining AI with blockchain could bolster DT security through advanced threat detection mechanisms.
Jin [footnote 33] and Jiang [footnote 34] also explore blockchain’s application in securing digital twins. Jin highlights the role of blockchain in integrating data from multiple sources while ensuring integrity, whereas Jiang emphasises the transparency, traceability, and high security offered by blockchain, making it suitable for collaborative DT applications such as construction safety management and operational cost tracking.
Opportunities
Based on Suhail’s [footnote 20] definition, an AI-enabled Digital Twin (DT) offers significant advantages in a cyber security context by providing a dynamic, real-time virtual representation of Cyber-Physical Systems (CPSs) capable of evaluating operational behaviour and security without compromising live system performance. This capability is particularly useful when working with mission critical, safety-related or high-availability systems. This approach enables proactive threat detection and response by simulating potential attack scenarios and predicting vulnerabilities across the entire product lifecycle. By integrating AI, the DT can autonomously analyse sensor data, learn from emerging threats, and enhance situational awareness.
Le Dez’s [footnote 35] military perspective further illustrates how AI and DTs can transform cyber operations by creating a cleaner digital environment and reducing complexity, thus providing commanders with a clearer view of the battlefield both in the present and the future. Clean, trusted data minimises operational uncertainties, streamlining cyber operations planning and improving predictability in decision-making. This clarity reduces the "fog of cyber warfare," allowing for more precise and effective cyber defence strategies while maintaining the integrity and security of CPSs through continuous monitoring and adaptive security protocols.
Simulation and Threat Intelligence Hossain et al. [footnote 11] discusses a Digital Twin Metaverse Network (DTMN) provides a controlled simulation environment for testing and validating security measures across both operational and consumer-facing systems. It employs adversarial emulation and threat intelligence sharing, utilising the MITRE ATT&CK framework to simulate known attack tactics, techniques, and procedures (TTPs) within a virtualised infrastructure. Real-time assessments and dynamic adjustments support the identification of vulnerabilities, enhancing cyber resilience against AI-driven threats. This ensures proactive defence strategies and improved system security in complex IT/OT environments.
Cyber-Twins for Transport Security Yigit [footnote 14] and Koronitis [footnote 9] both explore the concept of Cyber-Twins for creating environments where researchers and practitioners can remotely practice attack and defence scenarios specific to the transport sector. Yigit focuses on roads and connected autonomous vehicles (CAVs), while Koronitis examines smart airport Industrial Internet of Things (IIoT) environments. These Cyber-Twins enable the replication of various attack vectors, including information gathering, denial of service (DoS), data exfiltration, data manipulation, power depletion, fuzzing, and man-in-the-middle (MITM) attacks.
Real-Time Monitoring and Threat Detection Sarker [footnote 36] emphasises the role of digital twins in real-time monitoring, where systems continuously collect data to detect deviations from normal behaviour. Cyber professionals can gain deeper insights into the behaviour of both physical and virtual components through extensive data analysis. Suspicious activity and security issues trigger prompt notifications, enabling swift response and mitigation. Digital twins also have predictive capabilities, forecasting potential cyber security risks and vulnerabilities based on extracted data insights. This technology not only enhances automated threat management but also supports human expertise and decision-making in real-world security scenarios.
Vulnerability Management and Lifecycle Security Feng et al [footnote 37] explore the protection of industrial Internet security by focusing on the mining and repair of vulnerabilities using evolutionary game theory. Their approach considers the entire lifecycle of network security vulnerabilities to promote effective identification and mitigation strategies within digital twin networks.
Structured Threat Modelling and Risk Mitigation M.N. Al-Mhiqani et al [footnote 38] propose a structured approach that integrates threat modelling with digital twin tools. This methodology enables early identification and mitigation of cyber security risks by simulating potential threat scenarios and applying preventive measures.
Anomaly and Intrusion Detection Systems (IDS/IPS) Jagannath [footnote 18] highlights the application of digital twins in anomaly detection and intrusion detection/prevention systems (IDS/IPS). Their study describes how deep neural networks can be integrated with digital twin models to detect anomalies in smart grid infrastructure. Furthermore, a cloud-based digital twin framework is employed for detecting and mitigating both individual and coordinated security attacks on smart grid systems. In these cases, digital twins serve as models for large-scale distributed systems, supporting upper-layer detection and decision-making processes.
5.1.4 Conclusions of Digital Twins and AI for convergence
The combined application of DTs and AI has the potential to transform how industries monitor, analyse, and protect both physical and virtual assets. While the concept of DTs originated as a way to replicate and analyse physical systems in real time, it has expanded into broader cyber-focused domains, including cyber-twins and cyber-ranges. These environments use AI to rapidly detect threats, enhance situational awareness, and enable predictive maintenance—capabilities that are particularly valuable for high-stakes, safety-critical, or mission-critical operations, where otherwise would be too disruptive to assure.
Despite the clear advantages, the integration of AI and DTs also introduces complex challenges in data security, privacy, and intellectual property. Large-scale data collection from IoT networks is essential to power AI-driven insights, yet it significantly expands the attack surface. Concerns range from data manipulation and poisoning attacks to unauthorised access or theft of proprietary models and datasets. Various studies highlight the potential of blockchain and zero-trust architectures to address these issues, offering immutable records, improved transparency, and dynamic access controls. However, there is consensus that these solutions are not silver bullets; ensuring trust in original data, effectively managing cryptographic keys at scale, and coordinating decentralised systems all remain active research problems.
Looking ahead, the synergy of AI-enabled DTs with emerging technologies such as 6G and advanced blockchain frameworks holds promise for more resilient, autonomous cyber-physical systems. These systems can continuously adapt to evolving threats through real-time simulation, predictive analytics, and automated countermeasures. At the same time, the gap identified by Xu and others indicates the need for more research that integrates state-of-the-art AI, robust cyber security mechanisms, and real-world testing.
Research Question 1: Novel or Emerging Security Risks
-
Exposure of Sensitive Data and Intellectual Property Large-scale data collection across IoT networks expands the risk of unauthorised access or theft of proprietary designs, operational data, and AI models. This can lead to competitive disadvantage, loss of innovation, and significant privacy breaches.
-
Data Manipulation and Integrity Attacks Digital twins depend on accurate, real-time data for operational decision-making. Adversaries can corrupt or inject misleading data (e.g., poisoning attacks), compromising both the virtual model and its physical counterpart, potentially resulting in incorrect predictions or unsafe system behaviours.
-
Model Poisoning and Compromised AI AI-driven components can be sabotaged by adversaries who introduce subtly malicious training data, degrading the performance or reliability of digital twin models. These sophisticated attacks are especially problematic in environments where continuous learning and federated models are employed.
-
Complex, Distributed Attack Surface The interconnected ecosystem of IoT devices, edge systems, and cloud platforms creates a vast, evolving attack surface. Traditional security measures like intrusion detection/prevention systems can struggle to scale, while zero-trust solutions remain challenging to implement and maintain across heterogeneous, high-volume networks.
-
False Assumptions About Security Mechanisms While blockchain technologies can offer immutability and distributed trust, they do not inherently validate data quality at its source. Corrupted or malicious data can still enter the system, requiring robust device authentication, end-to-end data provenance, and ongoing trust verification beyond the ledger layer.
Research Question 2: Industries most affected by the compounding cyber security risks:
-
Manufacturing
-
Transport
-
Energy and Utilities
-
Aerospace and Space Exploration
-
Construction and Infrastructure
-
Healthcare
-
Defence and Military
-
Telecommunications
Research Question 3: Applications of emerging technologies most likely to be affected by technology convergence:
-
Cyber-Twins: Virtual environments mirroring real-world cyber systems, networks, or infrastructures enable the safe simulation of diverse attack and defence scenarios without affecting live operations. By replicating transportation systems, critical infrastructure, or enterprise networks, they allow the evaluation of threats such as man-in-the-middle (MITM) and denial-of-service (DoS), as seen in Yigit’s [footnote 14] work on connected autonomous vehicles and Koroniotis’ [footnote 9] smart airport simulations. These environments also facilitate remote cyber exercises for skills training and incident response, but must protect sensitive network topologies and system configurations stored within the cyber-twin.
-
Digital Twin Metaverse Network (DTMN): A metaverse-like digital twin environment integrates AI, IoT, and simulation in a shared virtual space, enabling adversarial emulation based on frameworks like MITRE ATT&CK to replicate known TTPs. It supports real-time security assessments, vulnerability scanning, and dynamic threat modelling, as highlighted by Hossain et al.[footnote 11], allowing multiple stakeholders such as IT and OT teams to collaborate in a unified environment for faster discovery and joint risk mitigation. By relying on accurate, up-to-date data flows from production systems, this environment faces heightened risks if those pipelines are compromised.
5.2 Blockchain and Artificial Intelligence
5.2.1 Identified Groupings
-
Blockchain + AI + Federated Learning
-
Blockchain + AI + Cryptography
5.2.2 Summary of Blockchain and AI
Blockchain is a digital ledger or notebook that records transactions or information in a highly secure and transparent way. It works like a chain made up of blocks, where each block stores data, such as details of a transaction or other important information. What makes blockchain unique is its decentralised nature — no single person or company controls it. Instead, copies of the ledger are distributed across many computers, so everyone has access to the same information. This makes it nearly impossible to cheat or alter the records. Each block is securely linked to the one before it, creating a chain that breaks if someone tries to tamper with it, signalling something is wrong.
When converged, blockchain and AI offer transformative solutions to key challenges in distributed systems, such as improving security, enhancing scalability, and enabling trustless interactions. A review of the identified literature highlights significant advancements in this field, showcasing its potential to revolutionise cyber security while introducing novel challenges. Despite their combined potential, the literature underscores the dual-edged nature of this convergence. On one hand, blockchain’s decentralised and immutable architecture, paired with AI’s data analysis and decision-making capabilities, improves threat detection, fraud prevention, and data integrity. On the other hand, this integration introduces complexities such as increased resource demands, potential algorithmic biases, and challenges in achieving seamless interoperability across diverse systems.
5.2.3 Cyber Security Impacts of Blockchain and AI
Across the reviewed literature, the focus is on addressing conventional cyber security challenges, particularly in safeguarding the vast amounts of sensitive data utilised and processed within systems. While familiar threats such as data breaches, denial-of-service (DoS) attacks, and algorithmic exploitation persist, the implications of these risks are amplified in blockchain-AI ecosystems due to their reliance on decentralised architectures, computational intensity, and the complexity of integrating heterogeneous technologies. [footnote 39], [footnote 40], and [footnote 41] provide an up-to-date examination of these technologies within cyber security systems. They delve into technical aspects, providing in-depth analyses of the latest developments in the field.
From the literature, the key cyber security themes relevant to blockchain and AI can be categorised into the following main areas:
-
Enhanced Data Integrity and Transparency Blockchain’s primary strength lies in its ability to create immutable ledgers, ensuring data integrity by preventing tampering and unauthorised modifications. This immutability is crucial in applications like financial transactions, supply chain monitoring, and healthcare, where trust in data is paramount [footnote 42] [footnote 43]. AI complements this by offering real-time analytics, anomaly detection, and insights into system behaviours. By integrating AI’s analytical capabilities with blockchain’s secure framework, organisations can build robust mechanisms for fraud prevention and auditability. Together, these technologies create a transparent and reliable environment for handling sensitive information [footnote 44] [footnote 45] [footnote 46] [footnote 47] [footnote 48].
-
Real-Time Threat Detection The convergence of AI and blockchain significantly enhances real-time threat detection. AI-driven algorithms are capable of identifying anomalies, intrusion attempts, and unusual behaviour patterns as they occur. This capability is particularly beneficial in dynamic environments like IoT networks and smart cities, where threats evolve rapidly [footnote 42], [footnote 43], [footnote 47]. Blockchain augments this by securely sharing training data and enabling collaborative threat intelligence systems. The combination ensures rapid and accurate detection of cyber attacks, improving overall system resilience and reducing response times [footnote 44], [footnote 46], [footnote 49].
-
Scalability and Efficiency Scalability is a critical challenge for both blockchain and AI systems, and their convergence offers solutions to these issues. AI optimises blockchain’s scalability issue by using predictive models and resource allocation techniques to improve consensus mechanisms and transaction speed [footnote 42], [footnote 43]. Blockchain, in turn, enhances AI’s scalability by securely managing and distributing data across decentralised networks, addressing bottlenecks. Together, they enable efficient and scalable systems that are better suited to handle large-scale applications [footnote 44] [footnote 45] [footnote 46].
-
Improved Privacy and Compliance The convergence of blockchain and AI addresses critical privacy concerns while ensuring compliance with regulatory standards. Blockchain provides a decentralised architecture for secure data handling, making it difficult for unauthorised entities to access sensitive information [footnote 44], [footnote 49]. AI adds another layer of protection through privacy-preserving techniques such as differential privacy and zero-knowledge proofs, which anonymise data without compromising its usability. These combined capabilities support compliance with global regulations, fostering trust and reliability among stakeholders [footnote 42], [footnote 45], [footnote 47].
5.2.4 Emerging Countermeasures
The novel challenges identified in the convergence of blockchain and AI demand innovative approaches to secure decentralised networks and their interconnected ecosystems. Based on insights from the reviewed papers, several promising strategies and countermeasures have been proposed to address vulnerabilities such as computational resource limitations, privacy risks, and threats targeting heterogeneous and distributed architectures. These advancements aim to strengthen the resilience, scalability, and security of blockchain-AI integrated systems.
-
Enhanced Data Privacy and Protection Mechanisms: Blockchain’s decentralised nature ensures that sensitive data is stored securely, preventing unauthorised access or tampering. By distributing data across multiple nodes and using cryptographic hashing, it eliminates single points of failure, reducing the likelihood of data breaches. AI complements these features by introducing privacy-preserving techniques like federated learning, where models are trained locally without sharing raw data, and differential privacy, which adds noise to datasets to mask individual records. This synergy not only protects data during storage and processing but also enables secure data sharing in highly regulated environments like healthcare and finance, ensuring compliance with privacy laws [footnote 46], [footnote 50] [footnote 51] [footnote 52] [footnote 53] [footnote 54] [footnote 55].
-
AI-Driven Threat Detection: As noted in Section 5.3.3), AI algorithms are highly effective at analysing vast amounts of data to detect anomalies and predict potential threats. Blockchain enhances these capabilities by maintaining tamper-proof logs of security events, enabling traceable and reliable forensics. Additionally, the decentralised nature of blockchain ensures that threat intelligence shared across networks remains authentic and unaltered, which is critical for collaborative cyber security frameworks [footnote 46], [footnote 47] [footnote 56].
-
Secure Data Sharing: Blockchain’s ability to create secure, transparent ecosystems for data sharing addresses the growing need for trustworthy data in AI applications. By providing tamper-proof and verifiable datasets, blockchain reduces the risks of data poisoning and ensures the reliability of AI models. This is particularly critical in collaborative AI systems, where multiple entities contribute data for model training. These secure platforms are being explored in areas such as federated learning, where data privacy and integrity are paramount [footnote 51], [footnote 52].
-
Regulatory Compliance and Transparency: Regulatory compliance is a significant challenge for organisations handling sensitive data. Blockchain’s transparency and immutability provide an auditable trail of all transactions and data exchanges, simplifying compliance with laws like GDPR. AI further aids by generating detailed compliance reports and monitoring systems for deviations from regulatory standards. Together, these technologies ensure that organisations meet compliance requirements while maintaining high levels of security and accountability [footnote 41], [footnote 50],[footnote 52],[footnote 56].
-
Scalability Improvements: One of the primary limitations of blockchain systems is their scalability, as increasing transaction volumes can lead to slower processing times and higher costs. AI-driven techniques, such as predictive resource allocation and dynamic sharding help mitigate these issues. Predictive models can forecast network demand and allocate resources efficiently, while dynamic sharding divides the blockchain into smaller, more manageable pieces, each capable of processing transactions independently. These innovations enable blockchain systems to scale effectively in large-scale applications, such as smart grids and global supply chains [footnote 47] [footnote 51] [footnote 52].
-
Decentralised Identity Management: Traditional identity management systems rely on centralised databases, making them vulnerable to breaches and unauthorised access. Blockchain-based decentralised identity systems distribute control to individual users, allowing them to manage their data securely. AI enhances these systems by enabling advanced biometric authentication and behaviour-based analysis, ensuring accurate identity verification. For example, AI can analyse user patterns, such as typing speed or navigation habits, to detect fraudulent activities. These combined technologies are particularly beneficial for applications in banking, healthcare, and digital identity ecosystems [footnote 41].
5.2.5 Case Study: AI-Blockchain Synergy for Secure Supply Chain Management
The convergence of AI and Blockchain, including DLT, has revolutionised supply chain management by enhancing transparency, security, and operational efficiency. However, while blockchain ensures tamper-proof and auditable records of transactions, AI introduces intelligence to analyse patterns, predict trends, and automate decision-making within the supply chain. Nevertheless, this synergy also introduces unique cyber security challenges and opportunities.
Real World Examples:
IBM Food Trust: A blockchain-powered platform that integrates AI to ensure food safety and traceability in global supply chains. (https://www.ibm.com/products/supply-chain-intelligence-suite/food-trust)
VeChain Thor: A blockchain solution leveraging AI for supply chain optimisation and fraud detection. (https://vechain.org/)
Key References
[footnote 46] examines how the synergy between Blockchain and AI improves operations and affects cyber security.
[footnote 48] discusses the convergence of blockchain and AI technologies, highlighting how blockchain enhances AI applications through trustworthiness, secure data sharing, and efficiency, while AI optimises blockchain’s energy consumption, scalability, and effectiveness.
Technology Convergences:
-
Blockchain/DLT: Provides immutable transaction records, enhances trust, and enables secure sharing of data across decentralised networks.
-
AI Algorithms: Analyse vast datasets to detect anomalies, predict disruptions, and optimise operations.
-
Smart Contracts: Automate processes like payments and compliance checks, ensuring efficiency and reducing human intervention.
-
IoT Integration: Enables real-time data collection and monitoring for AI and blockchain systems to analyse and secure.
Cyber Security Challenges and Solutions in AI and Blockchain Integration
The integration of AI and blockchain offers significant advancements in cyber security, leveraging blockchain’s decentralised nature to ensure data integrity and tamper resistance, while AI enhances threat detection capabilities. However, this synergy also introduces new complexities that heighten the challenge of securing these systems. Poorly coded smart contracts represent a critical vulnerability, as they may contain exploitable bugs that could lead to financial or operational losses. Adversarial attacks on AI models pose another significant threat, with malicious actors capable of manipulating these models to misclassify data or produce flawed predictions, potentially disrupting decisions in sectors like supply chain management. Moreover, blockchain’s immutable nature often conflicts with data privacy regulations such as GDPR, which mandate the right to erase personal data, presenting an unresolved tension between compliance and security. The high computational demands of AI, when combined with blockchain’s storage and processing requirements, exacerbate scalability issues, while biases or inaccuracies in AI models may propagate throughout blockchain systems, creating systemic vulnerabilities.
Addressing these challenges requires a multifaceted approach. Ensuring secure smart contracts through regular audits and formal verification methods is critical for maintaining reliability and minimising exploitable errors. To counter adversarial attacks, incorporating adversarial training and explainable AI (XAI) mechanisms can safeguard AI systems against manipulation. Scalability concerns can be mitigated by processing AI tasks off-chain, storing only critical data on the blockchain to balance performance with resource constraints. Privacy challenges can be addressed using advanced encryption techniques like zero-knowledge proofs, which enable secure data sharing while complying with regulations. Lastly, integrating AI for continuous monitoring within blockchain systems can proactively detect anomalies and respond to potential threats, enhancing the overall cyber security framework. This blend of strategies underscores the need for careful design and implementation to fully harness the potential of AI and blockchain while mitigating associated risks.
5.2.6 Conclusions
The convergence of blockchain and AI creates a transformative technological synergy, offering significant advancements in cyber security. As these technologies become integral to critical applications, they redefine the boundaries of secure data management, threat detection, and decision-making. However, this integration also introduces unique challenges, including computational resource demands, privacy concerns, and complexities in interoperability.
Emerging countermeasures such as AI-driven anomaly detection, blockchain-based decentralised frameworks, privacy-preserving mechanisms, and scalable architectures demonstrate promising potential in addressing these challenges. These solutions are specifically designed to leverage the strengths of blockchain’s immutability and decentralisation alongside AI’s predictive and adaptive capabilities, ensuring robust protection and operational resilience in distributed systems.
Moving forward, it is essential to embed security considerations at the core of blockchain-AI systems. This requires adopting interdisciplinary collaboration, developing standardised frameworks, and navigating the complexities of these technologies effectively. By proactively addressing cyber security challenges, the integration of blockchain and AI can unlock their full potential, paving the way for secure, transparent, and trustworthy digital ecosystems that empower innovation across industries.
Research Question 1: Novel or Emerging Security Risks
-
Adversarial Attacks on AI Models: Malicious actors can manipulate AI models to produce incorrect predictions or classifications. When integrated with blockchain, these adversarial attacks can disrupt operations, especially in critical sectors like supply chain management. This risk is significant because it directly undermines the reliability of AI-driven decision-making in blockchain systems.
-
Smart Contract Vulnerabilities: Poorly coded smart contracts can contain exploitable bugs, leading to financial losses or operational disruptions. These vulnerabilities are particularly concerning in blockchain-AI systems, where smart contracts automate critical processes. As such, exploits in smart contracts can have cascading effects due to blockchain’s immutable nature.
-
Data Privacy and Regulatory Compliance:Blockchain’s immutability conflicts with data privacy regulations like GDPR, which require the right to erase personal data. This creates a challenge between maintaining data integrity and complying with legal requirements. Ensuring compliance while leveraging blockchain’s transparency and AI’s data processing capabilities remains a significant challenge.
Research Question 2: Industries Most Affected by the Compounding Cyber security Risks
-
Financial Services & Banking
-
Healthcare & Medical Data Management
-
Supply Chain & Logistics
-
Smart Cities & IoT Networks
-
Autonomous Vehicles & Transportation Systems
-
Energy & Smart Grids
Research Question 3: Industries Most Affected by the Compounding Cyber security Risks
-
Decentralised Finance (DeFi) & Smart Contracts: Smart contracts based on blockchain can be exploited due to coding flaws, leading to financial losses, while AI-driven trading systems are vulnerable to adversarial attacks and market manipulation. Moreover, adversarial AI attacks can manipulate automated trading algorithms, distorting market trends and impacting investor confidence. In addition, AI-driven models used in DeFi platforms can be fooled by malicious inputs, resulting in incorrect decision-making and financial instability.
-
Enhanced Security & Data Integrity for Vehicle Networks: Blockchain ensures tamper-proof communication between autonomous vehicles (V2V) and traffic management systems, while AI analyses real-time traffic and sensor data for safe navigation and predictive maintenance. This will reduce the risk of data manipulation in vehicle-to-infrastructure (V2I) communications. Furthermore, AI models in self-driving cars can be manipulated through adversarial attacks (e.g., misleading traffic sign recognition), and if these models are integrated with blockchain for decision logging, poisoned data could persist permanently, leading to incorrect driving decisions.
5.3 Artificial Intelligence and IoT
5.3.1 Identified Groupings
-
AI + IoT + Machine Learning
-
AI + IoT + Deep Learning
-
AI + IoT + Blockchain
-
AI + IoT + Fog/Edge Computing
5.3.2 Summary of AI and IoT
The convergence of Artificial Intelligence (AI) and the Internet of Things (IoT) has led to transformative innovations across industries, enhancing automation, efficiency, and decision-making. While IoT enables the interconnection of devices, AI adds an intelligence layer by analysing and acting on the generated data. This integration promises advancements in smart cities, healthcare, manufacturing, and other domains. But, like other convergences highlighted in this review, the integration of AI and IoT also introduces new challenges, especially in security.
5.3.3 Cyber Security Impacts of AI and IoT
Across the reviewed literature, there is no evidence of a transformative new cyber security paradigm, or a fundamental redefinition of vulnerabilities introduced by the convergence of AI and IoT. Instead, the focus remains on addressing conventional cyber security challenges, particularly in safeguarding the vast amounts of sensitive data generated, transmitted, and processed within these systems. While traditional threats such as data breaches, denial-of-service (DoS) attacks, and malware remain prevalent, their implications are significantly amplified in AI-IoT ecosystems due to the reliance on distributed architectures, real-time analytics, and the heterogeneity of interconnected devices. The integration of AI into IoT adds complexity, introducing risks such as adversarial attacks on machine learning models and potential biases in decision-making, which further complicate the security landscape in these interconnected systems.
Stanko et al. [footnote 57] delve into the convergence of AI and IoT, termed AIoT, focusing on integration challenges and security concerns. The authors identify key challenges, including device and protocol compatibility, data heterogeneity, latency, and power consumption. They emphasise the complexity arising from diverse hardware and software platforms, which complicates standardisation and interoperability. Security issues such as unauthorised data access, data leakage, and vulnerabilities in AI algorithms, including data poisoning attacks, are discussed.
From the literature, the key cyber security themes relevant to AI and IoT can be categorised into the following main areas:
-
Anomaly Detection and Predictive Analytics The application of machine and deep learning models enables the processing and analysis of large volumes of IoT-generated data to dynamically identify anomalous behaviours and mitigate security threats. By analysing historical and real-time data, AI predicts vulnerabilities and initiates proactive countermeasures. This reduces downtime, enhances reliability, and prevents potential breaches. However, these AI-powered systems introduce new cyber security risks, such as:
AI-driven models process and analyse vast volumes of IoT-generated data to identify anomalous behaviours and mitigate security threats in real time. By examining historical and live data, machine and deep learning techniques predict vulnerabilities and initiate pre-emptive safeguards, reducing downtime, boosting reliability, and preventing breaches.
However, these powerful systems introduce emerging cyber security challenges. Adversaries may perform data poisoning by injecting malicious training data - data poisoning attacks - leading models to adopt flawed patterns. Attackers can reverse-engineer or extract sensitive information from AI models - model inversion or extraction attacks - compromising IoT privacy. Adversarial attacks use carefully crafted inputs to trick models into misclassification, bypassing detection systems or triggering false positives.
Flaws or biases in algorithms exacerbate inaccurate threat identification, while the massive data collection required for AI heightens privacy concerns and potential unauthorised access [footnote 58]. Over-reliance on AI can further expose critical infrastructures to cascading disruptions if a single system is compromised, with cascading effects across IoT ecosystems.
-
Decentralised and Tamper-Proof Systems Fazel et al. [footnote 59] explore the convergence of IoT, AI, and blockchain to address challenges such as scalability, interoperability, security, privacy, and heterogeneity within IoT ecosystems. The authors propose a novel classification schema for IoT integration, categorising approaches that incorporate digital technologies and data science methods.
The convergence of IoT, AI, and Blockchain provides significant benefits. Blockchain ensures data integrity, immutability, and tamper resistance, while machine learning offers predictive analytics to detect anomalies and automate threat responses. Together, these technologies enhance efficiency, enable real-time decision-making, and increase operational reliability [footnote 46] [footnote 59]. For instance, machine learning can optimise operations, improve customer engagement, and automate processes, while decentralised blockchain architectures reduce latency and increase security. Applications of this convergence extend to healthcare IoT, where patient data is monitored, and to smart cities, where secure communication platforms enhance infrastructure functionality.
Despite its advantages, the convergence faces challenges, including security vulnerabilities in AI algorithms, scalability issues in blockchain systems, and resource constraints. Technical hurdles such as computational overhead and lack of standardisation also pose significant barriers. Moreover, managing large volumes of sensitive IoT data while ensuring privacy and maintaining user trust remains a critical concern. In [footnote 59], the need for continued research to integrate machine learning and blockchain effectively is emphasised to develop energy-efficient, secure IoT systems.
-
Edge and Fog Computing for Enhanced Security Edge and fog computing plays a crucial role in enhancing security by processing data closer to its source, which minimises latency and reduces the risk of centralised data breaches. By deploying AI models at the edge or fog layer, data can be analysed locally, enabling faster responses to potential threats and improving overall system security. Additionally, edge computing integrates privacy-preserving machine learning techniques, which safeguard sensitive data while maintaining operational efficiency. This localised approach ensures both enhanced security and improved performance in managing data within distributed systems.
Firouzi et al. [footnote 60] describe how the implementation of an edge–fog–cloud computing model for AI-driven IoT applications presents several significant challenges. Interoperability remains a major hurdle due to the heterogeneous nature of IoT environments, which involve diverse devices, protocols, and standards. The lack of standardisation complicates communication between systems, necessitating the development of unified frameworks and abstraction layers to ensure seamless interaction. Scalability is another critical issue, as IoT deployments often span wide geographic areas with varying device densities and data loads. Ensuring that edge, fog, and cloud layers can dynamically adapt to these fluctuations requires flexible resource provisioning and adaptive orchestration frameworks.
Mobility introduces additional complexities, particularly in supporting mobile devices like vehicles and wearables. Continuous connectivity and service quality must be maintained as devices move across regions, requiring mobility-aware orchestration and predictive service migration. Latency and real-time processing are paramount for IoT applications such as autonomous vehicles and healthcare, where ultra-low latency is crucial for decision-making. This demands prioritising data processing closer to the source and balancing computation loads across layers to avoid bottlenecks. As noted in 5.8.3, [footnote 61] discusses the several challenges that persist, such as power constraints on edge devices that require the development of efficient models and energy-aware algorithms, while ensuring data privacy and secure handling is complex. Ethical concerns surrounding AI fairness, transparency, and accountability need to be addressed through robust ethical guidelines.
5.3.4 Emerging Countermeasures
The novel challenges identified in AI-IoT systems require innovative approaches to secure interconnected devices and their broader ecosystem. Based on insights from the reviewed papers, several promising developments and countermeasures have been proposed to address vulnerabilities such as adversarial attacks on AI models, privacy breaches in data-intensive IoT networks, and security risks arising from the heterogeneity and decentralised nature of AI-powered IoT architectures.
-
Holistic Security Frameworks: [footnote 57] highlight the importance of developing comprehensive security ecosystems that integrate AI-driven threat detection, encryption, access control, and device management to ensure end-to-end security. They suggest developing solutions that consider authentication mechanisms, advanced encryption methods, attack-resistant AI models, and the importance of standardisation and international protocols to ensure AIoT system security and interoperability.
-
Privacy-Preserving Techniques: The integration of AI into IoT ecosystems significantly enhances the ability to protect sensitive data, particularly in applications like healthcare, smart cities, and industrial systems. Studies such as those by Ruiz-Villafranca et al. [footnote 62] and Sarker et al. [footnote 63] highlight the use of AI-driven encryption, anonymisation, and tokenisation techniques to safeguard data during transmission and storage. AI also facilitates compliance with stringent data privacy regulations, including GDPR and HIPAA, by implementing intelligent auditing and data management systems. However, balancing privacy with real-time data processing requirements remains a key challenge in AI-IoT convergence.
-
Multi-Level and Lightweight AI-Driven Intrusion Detection Systems: AI empowers IoT systems with advanced anomaly detection and intrusion prevention capabilities, as highlighted in [footnote 64] and [footnote 65]. Machine learning and deep learning algorithms analyse patterns in IoT data to identify irregularities and potential threats in real time, ensuring proactive threat mitigation. For instance, AI-based intrusion detection systems are adept at recognising sophisticated cyberattacks, such as zero-day exploits, and triggering automated defensive measures. The integration of AI also extends the scope of IoT systems’ threat detection capabilities. AI-powered systems can recognise and mitigating advanced persistent threats (APTs) and detecting anomalies in encrypted traffic [footnote 64]. These enhanced detection capabilities reduce the risk of large-scale attacks such as distributed denial-of-service (DDoS) and ransomware attacks, which are common in IoT ecosystems.
-
Decentralised Security and Trust Frameworks: AI combined with blockchain technology enhances decentralised security in IoT systems by providing tamper-proof ledgers and secure transaction management, as discussed in [footnote 65] and [footnote 62]. Blockchain-enabled smart contracts, powered by AI, automate trust mechanisms and enforce access controls without manual intervention. These technologies collectively ensure data integrity and foster trust across diverse IoT networks.
-
Resource-Constrained Security Solutions: IoT devices often operate under significant resource constraints, limiting their ability to deploy computationally intensive security mechanisms. AI-driven lightweight security solutions, such as optimised cryptographic protocols and energy-efficient anomaly detection algorithms, address this issue effectively [footnote 65]. These approaches enable robust security without compromising the operational efficiency of resource-constrained IoT devices.
-
Heterogeneity and Interoperability Management: The diverse range of IoT devices, operating systems, and communication protocols poses challenges in maintaining consistent security measures. AI aids in mitigating these challenges by facilitating interoperability through intelligent middleware solutions and standardised communication frameworks, as noted in [footnote 66]. AI also automates the detection and correction of configuration vulnerabilities, ensuring seamless integration and enhanced security across heterogeneous IoT ecosystems.
-
Ethical AI and Transparency: The convergence of AI and IoT necessitates ethical considerations to ensure fairness, transparency, and accountability in system operations. Studies such as those by Rupanetti et al. [footnote 61] emphasise the importance of aligning security practices with ethical AI principles, especially in critical domains like healthcare and autonomous vehicles. Transparent data handling and accountability in AI decision-making processes are crucial for fostering trust among users and stakeholders.
-
Real-Time Security Enhancements: AI significantly enhances real-time decision-making in IoT systems, enabling predictive maintenance and rapid response to emerging threats [footnote 63]. By analysing device performance and historical data, AI predicts vulnerabilities and automates countermeasures, ensuring minimal system disruption. These capabilities are particularly vital in industrial IoT and smart city applications, where system resilience and uptime are paramount.
5.3.5 Case Study: AI-Enhanced IoT for Smart Healthcare Systems
Smart healthcare systems leverage IoT devices, such as wearable health monitors, connected medical imaging systems, and smart infusion pumps, to deliver personalised and efficient medical care. However, although, the integration of AI into these ecosystems enhances the diagnostic accuracy, real-time monitoring, and predictive maintenance of medical devices, it also introduces new and complex cyber security challenges.
Real-World Examples:
NVIDIA Clara for Smart Medical Devices: https://www.nvidia.com/en-gb/industries/healthcare-life-sciences/medical-devices/
Medtronic’s Connected Insulin Pumps: https://www.medtronic.com
Key References:
Pise et al. [footnote 67] examines the security issues that are introduced by the inclusion of AI in medical IoT
Ranaganyak et al.[footnote 68] explore the role of smart IoT devices in hospitals
Technology Convergences:
-
IoT Devices: Includes wearables, connected imaging systems, and sensors for continuous patient monitoring.
-
AI Algorithms: Analyse medical data to detect anomalies, predict patient conditions, and optimise device performance.
For instance, NVIDIA Clara enables AI-driven image reconstruction in medical imaging devices, reducing processing time and improving diagnostic accuracy. Its integration into smart healthcare ecosystems exemplifies the potential of AI-IoT convergence in enhancing patient care while maintaining robust data security.
Cyber Security Considerations:
The synergy between AI and IoT in medical devices introduces profound advancements but also significant challenges in the cyber security landscape. Together, AI and IoT transform traditional medical devices into interconnected, intelligent systems capable of real-time monitoring, decision-making, and remote operation. However, this convergence increases the attack surface and introduces complex vulnerabilities.
From a device perspective, IoT sensors and wearables collect vast amounts of patient data, which AI algorithms analyse to provide actionable insights. This interconnectedness enables seamless healthcare delivery but exposes sensitive data to cyber threats. For instance, unencrypted communication between IoT devices and AI systems creates vulnerabilities, allowing attackers to intercept, manipulate, or corrupt critical medical information.
An example of this synergy’s challenges can be seen in the 2021 vulnerability of IoT-connected infusion pumps [footnote 69]. These devices lacked sufficient security protocols, and attackers could potentially alter dosages by exploiting weak communication links. If AI-driven monitoring systems had been integrated to detect anomalies in device behaviour, these vulnerabilities could have been mitigated.
On the other hand, AI enhances cyber security in IoT ecosystems by enabling real-time anomaly detection. For example, the iRhythm Zio XT [footnote 70] wearable patch uses AI to monitor patient data and detect irregularities. AI models within the device can also identify unusual activity, such as unauthorised data access or unexpected device behaviour, thereby reducing the risk of cyberattacks. However, the AI-IoT synergy itself is not immune to risks, such as adversarial attacks that can manipulate AI models to misclassify data, potentially leading to incorrect medical interventions or system shutdowns.
The integration of AI and IoT also complicates regulatory enforcement. The global nature of IoT supply chains, combined with varying data protection laws, creates inconsistencies in how security measures are implemented. For instance, patient data transmitted via IoT devices for AI analysis often crosses borders, raising concerns about compliance with regulations like HIPAA or GDPR.
Key Security Challenges and Solutions in AI-IoT Synergy for Medical Devices:
AI-powered IoT devices in healthcare face significant cyber security challenges: an expanded attack surface where one compromised device can cascade across networks, data integrity risks from tampered IoT sensors, adversarial attacks exploiting AI weaknesses, and heightened privacy concerns from the vast amounts of sensitive data collected.
Solutions: Implementing AI-enhanced threat detection, end-to-end encryption, robust defences against adversarial attacks (e.g., adversarial training, explainable AI), and global compliance standards through collaboration is critical.
5.3.6 Conclusions
The convergence of AI and IoT creates a transformative technological framework but introduces significant cyber security challenges. As IoT devices powered by AI become integral to critical applications, in a similar fashion to the convergence of edge/fog and IoT discussed in Section 5.8, they blur the boundaries between physical and digital infrastructures, which amplifies security risks.
Emerging countermeasures demonstrate significant potential to mitigate these risks. AI-driven techniques, such as real-time anomaly detection, predictive analytics, and adaptive intrusion detection systems, enhance the ability to identify and respond to cyber threats dynamically. Blockchain-based decentralised frameworks and AI-optimised lightweight cryptographic methods address the unique constraints of AI-IoT systems, including limited computational resources, diverse device ecosystems, and real-time processing requirements. These measures collectively strengthen security, ensuring data integrity, system resilience, and trust in connected environments.
To fully harness the potential of AI-IoT ecosystems while safeguarding their applications, it is essential to embed security considerations into their design and deployment. This involves fostering interdisciplinary collaboration among technologists, policymakers, and domain experts, developing standardised security frameworks to address heterogeneity, and prioritising stakeholder education to enhance cyber security awareness and preparedness.
Research Question 1: Novel or Emerging Security Risks
-
Adversarial Attacks on AI Models: AI models integrated into IoT devices are vulnerable to adversarial attacks - where malicious actors manipulate input data to deceive the AI models. This can lead to misclassification of data, bypassing detection systems, or triggering false positives. For example, attackers could feed false sensor data to IoT devices, causing AI algorithms to make incorrect decisions. This is particularly critical in applications such as healthcare or smart cities.
-
Data Privacy Concerns: IoT devices generate and transmit vast amounts of sensitive personal data, which AI algorithms analyse to gain further insights. However, this data can be intercepted or misused, leading to privacy violations. The lack of standardised security protocols in many IoT devices escalates this risk, making it challenging to ensure data protection and compliance, especially with regulations such as GDPR or HIPAA.
Research Question 2: Industries Most Affected by the Compounding Cyber Security Risks
-
Healthcare & Medical IoT
-
Smart Cities & Infrastructure
-
Manufacturing & Industrial IoT (IIoT)
-
Autonomous Vehicles & Transportation Systems
-
Energy & Smart Grids
-
Retail & Smart Supply Chains
Research Question 3: Applications of Emerging Technologies Most Likely to Be Affected
-
Smart Healthcare Systems & Wearable Devices: AI-powered IoT devices in healthcare, such as wearable monitors, connected medical imaging systems, and smart infusion pumps, enhance patient care through real-time data analysis and predictive diagnostics. However, cyberattacks on AI models can lead to misdiagnosis, incorrect dosages of medications, or privacy breaches, which can put patient safety at risk.
Adversarial attacks could manipulate IoT-collected health data, leading to false alarms or missed critical conditions, while unsecured data transmissions may expose sensitive patient records to unauthorised access.
-
Autonomous Vehicles & Traffic Management: AI processes real-time IoT sensor data to navigate roads, optimise traffic flow, and enhance vehicle-to-vehicle (V2V) communication. However, adversarial attacks on AI models can manipulate object detection, road sign recognition, or real-time navigation systems, causing accidents or traffic disruptions. Moreover, attackers can exploit data poisoning vulnerabilities, misleading AI-driven transportation systems into making unsafe driving decisions. Additionally, weak security in IoT-enabled traffic management networks could allow adversaries to manipulate traffic lights, vehicle routes, or autonomous car software updates, creating significant safety risks.
-
Industrial IoT & Smart Manufacturing: AI-driven IoT in factories, robotics, and supply chain automation improves efficiency by enabling predictive maintenance, process automation, and real-time monitoring of machinery. However, vulnerabilities in AI-IoT systems can cause halts in production, equipment failures, and even cause supply chain disruptions due to cyberattacks. Furthermore, adversaries may inject malicious data into IoT sensors, misleading AI-driven automation systems and causing mechanical failures or quality control issues.
5.4 Personalised Medicine and Artificial Intelligence
5.4.1 Identified Groupings
-
AI + Personalised Medicine + Digital Twins
-
AI + Personalised Medicine + IoMT
-
AI + Personalised Medicine + Blockchain
-
AI + Personalised Medicine + 3D Printing
-
AI + Personalised Medicine + Post-Quantum
5.4.2 Summary of Personalised Medicine and AI
AI is central to processing vast datasets, uncovering patterns, and delivering insights that enhance diagnostic precision, disease prediction, and patient care [footnote 71] [footnote 72]. Personalised medicine, defined as "the tailoring of medical treatment to the individual characteristics of each patient," leverages an individual’s genetic, environmental, and lifestyle information to optimise therapeutic outcomes. This approach surpasses the limitations of conventional one-size-fits-all models by enabling treatments that are uniquely designed for individual needs and conditions [footnote 72], [footnote 73].
A common theme across all resources is that the integration of AI in personalised medicine introduces complex challenges as it requires processing highly sensitive data, including genomic sequences, health records, and real-time monitoring data from wearable devices (IoMT). This data-rich environment makes healthcare systems increasingly attractive targets for cyber attacks, such as ransomware, data theft, and adversarial attacks on AI models. The impact of such breaches extends beyond data privacy, potentially compromising the integrity of treatment plans and diagnostic models, endangering patient safety, and eroding trust in healthcare systems [footnote 73] [footnote 74].
A total of 18 resources were identified from across all sources when searching for literature on AI and personalised medicine. However, none were directly focused on the specific impact of this pairing on cyber security. Instead, the references tended to focus primarily on broader enabling technologies, such as federated learning [footnote 74], or niche applications like 3D bioprinting [footnote 75], [footnote 76], or post-quantum cryptography [footnote 77]. Consequently, no additional relevant papers were identified as part of the Level 1 reference review, as the scope of existing literature failed to capture the direct intersection of the technology pairing impacting cyber security.
Notably, five of the 18 texts explicitly discussed digital twins as a primary or significant technology within the broader context of personalised medicine and AI [footnote 26] [footnote 72] [footnote 78][footnote 79] [footnote 80], positioning AI as an enabling tool for digital twins rather than as a central focus. For example, [footnote 26] centres on digital twins as the primary technology in personalised medicine, leveraging AI to address heterogeneity in genomics, physiology, lifestyles, and environments. Additionally, Zhang incorporates wearable technologies (IoMT) to further enhance the personalised capabilities of digital twins, suggesting a natural grouping of AI, personalised medicine, and digital twins as an emerging technological triad.
Cyber security considerations were typically treated as secondary issues within this literature, discussing cyber security as challenges or barriers. The key risks focussed on addressing the privacy and security challenges of sensitive medical data, a current and longstanding risk in healthcare. In discussions of AI, the broader topics of ethical and responsible AI frequently appeared, often referencing security and privacy as foundational principles critical to ensuring robustness, accuracy, and trustworthiness [footnote 71] [footnote 74].
Given the lack of direct research on AI, personalised medicine, and cyber security as a combined field, the analysis below focuses on identifying intersecting areas within this technological landscape, extracting themes and challenges relevant to the cyber security implications of this coupling.
Identified Groupings
AI + Personalised Medicine + Digital Twins: Digital twins, defined as virtual replicas of physical systems, enable real-time simulation, monitoring, and optimisation in personalised healthcare. [footnote 79] highlight their ability to integrate large datasets from genomics, physiology, and lifestyle to create personalised healthcare models. [footnote 26] emphasise the role of AI within digital twins to manage the heterogeneity of patient data, while IoMT devices provide real-time inputs for continuous model updates. [footnote 78] discuss digital twins as tools for analysing and simulating complex medical conditions, aiding in personalised treatment planning.
Examples of practical applications include Dassault Systèmes’ Living Heart model, launched in 2015, which simulates the heart’s mechanical, structural, and electrical properties to forecast patient outcomes and optimise treatments. Similarly, Siemens Healthineers’ cardiac models and the broader Human Digital Twin endeavour represent comprehensive digital embodiments of human physiology, integrating internal traits with external societal and environmental impacts.
From a cyber security perspective, protecting Digital Twins can be a complex matter. Their reliance on sensitive data and IoMT inputs creates risks of data breaches, system manipulation, and unauthorised access [footnote 26] [footnote 79] .
AI + Personalised Medicine + IoMT: The Internet of Things (IoT) and the Internet of Medical Things (IoMT) are components in the integration of AI and personalised medicine, acting as data collection and transmission systems. IoMT devices, such as wearable sensors and implantable monitors, provide continuous real-time data on physiological and behavioural patterns, essential for informing AI models and digital twins. [footnote 81] highlight the emergence of the Internet of Behaviours (IoB), where IoT devices capture "patterns of life" data, encompassing a patient’s activities, preferences, and habits. This behavioural data can enhance personalised treatments but also introduces significant cyber security risks, including unauthorised profiling and misuse of sensitive information.
IoMT devices are integral to digital twins, serving as the primary sensors that feed real-time data into the twin’s virtual model. [footnote 26] emphasise this connection, explaining that digital twins rely on IoMT to update their simulations with live inputs, ensuring the accuracy of personalised treatment planning. [footnote 78] also describe how IoMT data contributes to the monitoring and prediction capabilities of digital twins in healthcare applications.
Cyber security challenges associated with IoMT include the risk of unauthorised access, data manipulation, and device tampering. Hassani [footnote 82] discusses Data Privacy and Security concerns with the processing of data from multiple data sources, whilst [footnote 73] discusses vulnerabilities in IoMT networks, including risks of malware and denial-of-service attacks, which could disrupt the flow of critical healthcare data. Sadeghi [footnote 83] further address these risks, advocating for secure IoMT communication protocols and decentralised systems like blockchain to enhance device authentication and data integrity. The significant variety and number of these devices make it a complex environment to appropriately secure o maintain patient safety and treatment outcomes.
AI + Personalised Medicine + Blockchain: Blockchain addresses key cyber security challenges in AI and personalised medicine by leveraging its decentralised and immutable ledger system. It enhances data privacy and protection by ensuring secure and auditable access to sensitive patient data. Sadeghi [footnote 83] highlight its use in federated learning, where blockchain encrypts data and logs model updates to prevent unauthorised access. [footnote 80] Castro et al. discussed its application in clinical trials, where it secures consent tracking and ensures data integrity. In mitigating AI vulnerabilities, blockchain validates and records updates in federated learning systems, reducing risks of adversarial and poisoning attacks [footnote 83]. For IoMT security, it manages device identities and secures data streams against manipulation [footnote 83]. In emerging technologies like digital twins and 3D bioprinting, blockchain ensures data integrity and provenance, as noted by Zhang et al. [footnote 26] and [footnote 75].
AI + Personalised Medicine + 3D Printing: 3D printing, combined with AI and personalised medicine, enables the creation of customised medical solutions, such as implants, prosthetics, and tissues. Ramesh et al. [footnote 75] highlight how AI optimises 3D bioprinting by improving material selection, parameter tuning, and real-time defect detection, advancing personalised tissue engineering. [footnote 76] emphasise the role of machine learning in enhancing the precision of biodegradable medical devices tailored to individual patients. These technologies converge to deliver personalised healthcare solutions, but they also introduce cyber security challenges, such as safeguarding sensitive design files and ensuring data integrity during production and distribution processes.
AI + Personalised Medicine + Post-Quantum: [footnote 77] discuss its importance in protecting sensitive medical data, such as genomic and treatment information, from potential quantum decryption capabilities. This technology ensures long-term data security by implementing encryption schemes resilient to quantum attacks. While current literature primarily highlights its theoretical importance, its practical application remains limited. In the context of personalised medicine, post-quantum cryptography safeguards critical systems, including IoMT networks and federated learning models, ensuring data integrity and confidentiality as healthcare increasingly integrates advanced AI technologies.
5.4.3 Personalised Medicine and AI Cyber Implications
Across the research, there is no evidence of a disruptive new cyber security application or a fundamental shift in the nature of vulnerabilities introduced by the integration of AI and personalised medicine. Instead, the focus predominantly revolves around conventional threats and vulnerabilities, particularly concerning the sensitive data generated and utilised within personalised medicine. While the types of threats remain familiar—such as data breaches, adversarial attacks, and system integrity compromises—the impact of these threats in this specific context is what sets them apart. The implications are heightened due to the critical nature of the data and the reliance on AI for diagnostic precision and treatment planning.
From the literature, the key cyber security themes relevant to AI and personalised medicine can be categorised into six main groups:
-
Data Privacy and Protection: The literature consistently highlights the need to safeguard sensitive patient data, such as genomic information, medical histories, and real-time health metrics from IoMT devices. [footnote 81] (discusses how the Internet of Behaviours (IoB) within IoMT offers unprecedented opportunities for personalised medicine and remote patient monitoring. By analysing health behaviours such as exercise patterns, sleep quality, and dietary habits, IoMT devices enable healthcare providers to tailor interventions, improve treatment outcomes, and promote preventive care. Ensuring compliance with privacy regulations (e.g., GDPR) and implementing robust encryption techniques are critical to prevent unauthorised access and data breaches [footnote 71] [footnote 74].
-
Vulnerabilities in AI Systems: AI models used in personalised medicine are vulnerable to adversarial attacks (manipulating inputs to produce erroneous outputs) and poisoning attacks (introducing malicious data during model training). These attacks can undermine diagnostic accuracy and treatment recommendations, highlighting the need for resilient AI systems and secure training environments [footnote 74] [footnote 77].
-
Ethical and Responsible AI: Cyber security is discussed in the context of ethical AI principles, such as fairness, transparency, and robustness. Ensuring that AI systems are free from bias and operate transparently while maintaining privacy and security is a recurring theme. Ethical frameworks often tie security to the broader goal of building trust in AI-driven personalised medicine systems [footnote 71] [footnote 72].
-
IoMT and Systemic Risks: The interconnected nature of IoMT devices expands the attack surface for cyber threats, posing significant challenges to patient monitoring and personalised medicine. These devices, which provide critical real-time data for AI models, are vulnerable to malware, ransomware, and denial-of-service attacks. Compromising IoMT systems can disrupt healthcare networks, jeopardising patient monitoring and treatment outcomes.[footnote 73] [footnote 81]
-
Insufficient Integration of Security in Emerging Technologies: Emerging technologies like digital twins, federated learning, and 3D bioprinting often address cyber security as a secondary consideration. While these technologies promise advancements in personalised medicine, their rapid deployment without robust security frameworks creates gaps. The papers call for interdisciplinary approaches to design systems where cyber security is embedded from the outset [footnote 26] [footnote 78]. Motwani also discusses that technologies like IoMT are not secure by default, using weak or default protocols.
-
Security Awareness across stakeholders: Motwani [footnote 73] raises that stakeholders in healthcare are less aware of information security vulnerabilities and attacks.
Cyber Security Research:
- Federated Learning (FL) is an approach to preserving privacy while enabling the development of robust AI models in personalised medicine. By training models on decentralised data without transferring sensitive information, FL addresses privacy concerns associated with data centralisation. A significant framework discussed by Mohammadi et al., 2024 [footnote 74] is FedHealth, which facilitates the creation of AI models by leveraging data from separate hospitals and wearable IoMT devices. This enables accurate and personalised healthcare solutions without exposing private medical data.
FL has been trialled in combating infectious diseases, such as COVID-19. This allow healthcare institutions to collaborate securely, sharing insights from CT scans and other medical data while maintaining privacy. For instance, the Pain-FL framework integrates privacy-preserving incentives, compensating data contributors for privacy costs, while ensuring model performance and convergence.
-
Blockchain [footnote 26] discuss the integration of blockchain technology within medical digital twin platforms as a method to address data security and privacy challenges. Blockchain’s decentralised framework mitigates risks of data tampering by providing transparency in consent management and enabling patients to monitor who accesses their data and for what purpose. The use of smart contracts allows the automation of regulatory compliance, translating governance requirements into enforceable digital processes. Additionally, blockchain’s tokenisation capabilities enable individual data ownership, empowering users to control sensitive healthcare information. Zhang et al. emphasise that these features enhance data auditability, prevent unauthorised access or manipulation, and foster trust among stakeholders by protecting sensitive healthcare data within digital twin ecosystems.
-
Trustworthy AI [footnote 71] highlights the imperative of evaluating Trustworthy AI within healthcare, focusing on the critical aspects of security, privacy, fairness, and interpretability. This work is one of the few that explores AI security risks through the lens of Responsible and Ethical AI, particularly addressing emerging concerns surrounding robustness and adversarial machine learning in healthcare applications. However, while the discussion extensively covers data confidentiality and its frequent pairing with privacy, it offers limited insights into the broader impacts of AI beyond these dimensions. This narrower focus presents an opportunity to expand the discourse on how Trustworthy AI frameworks can address systemic challenges and operational complexities within healthcare ecosystems.
-
Human-Centred Design [footnote 84] examines security primarily from the perspective of safety, addressing challenges related to data processing and security, particularly for users with limited technological proficiency or those affected by cognitive ageing.
5.4.4 Conclusions of Personalised Medicine and AI
A lack of research directly focussing on the convergence of AI and personalised medicine is notable. Despite identifying 18 relevant resources on AI and personalised medicine, none explicitly examined the cyber security implications of integrating these technologies. Instead, the literature primarily emphasised enabling technologies like federated learning or niche applications such as 3D bioprinting, neglecting the critical interplay between AI, personalised medicine, and cyber security. Cyber security concerns were often relegated to secondary importance, with an emphasis on privacy and data security rather than addressing systemic risks or the broader operational challenges posed by this technological intersection.
Where security is considered, the reviewed works largely adopt traditional perspectives on security, focusing on established threats and vulnerabilities in healthcare contexts. There was little evidence of disruptive or innovative thinking that redefines the frameworks used to evaluate threats or vulnerabilities. This lack of transformative insights limits the ability to anticipate and mitigate novel or emerging risks, leaving a gap in the strategic approach to cyber security in this rapidly evolving domain.
While the literature extensively covers data privacy, there is limited consideration of integrity and availability—critical pillars of cyber security. This oversight is notable, especially in the context of recent events like the Synnovis incident earlier this year, which highlighted the cascading impacts of compromised data integrity and availability, such as disruptions to blood group services. The focus on privacy likely stems from the scope of the reviewed works, which prioritised targeted research objectives over comprehensive security evaluations.
Research Question 1: Novel or Emerging Security Risks
-
Data Privacy and Confidentiality Personalised medicine relies on processing large volumes of sensitive patient information—including genomic data and detailed health records. This high-value data is at increased risk of unauthorised access or disclosure, leading to significant regulatory, reputational, and ethical consequences.
-
AI Model Integrity AI systems in personalised medicine are susceptible to adversarial and poisoning attacks that can introduce errors into diagnostic models or training datasets. Such compromises may result in incorrect treatment recommendations or clinical decisions.
-
IoMT Vulnerabilities The proliferation of wearable and implantable medical devices expands the potential attack surface, while insufficient security controls can undermine trust in these “smart” healthcare solutions. Unauthorised access to IoMT devices could disrupt patient monitoring, compromise treatment efficacy, and expose systems to broader network attacks.
-
Digital Competence Limited awareness and training on cyber security best practices among clinicians, patients, and healthcare administrators heightens the risk of human error. A robust cyber security culture and ongoing stakeholder education are essential for minimising these vulnerabilities.
-
Digital Twin Manipulation Digital twin ecosystems rely on real-time data feeds—including sensitive patient information—from IoMT devices. If attackers gain access or tamper with these data streams or the twin models themselves, they could compromise treatment simulations, undermine diagnostic outcomes, and breach patient confidentiality.
Research Question 2: Industries most affected by the compounding cyber security risks:
- Healthcare
Research Question 3: Applications of emerging technologies most likely to be affected by technology convergence:
-
3D Printing and Bioprinting: Additive manufacturing techniques used to create customised medical implants, prosthetics, and tissues demand strong safeguards for sensitive design files and manufacturing blueprints. Malicious alterations to device configurations could endanger patients if implants or prosthetics fail to meet requisite specifications.
-
Healthcare Digital Twins: Virtual replicas of patient physiology or healthcare systems enable real-time simulation, monitoring, and treatment optimisation, but they rely on sensitive data such as genomics and lifestyle factors, making them prime targets for data breaches or unauthorised manipulation. When compromised, these digital twins risk producing incorrect diagnoses or misguided treatments, eroding trust in healthcare providers.
-
Internet of Medical Things (IoMT): A specialised branch of IoT, these medical devices—such as wearable sensors and implantable monitors—capture continuous, real-time patient data yet face an expanded attack surface due to numerous connected endpoints, making them more vulnerable to malware, denial-of-service attacks, and unauthorised data profiling. If compromised, critical patient monitoring and life-saving interventions can be disrupted, posing serious risks to patient safety.
5.5 Quantum Communications and IoT
5.5.1 Identified Groupings
-
Quantum Communications + IoT + Blockchain + Quantum Cloud
-
Quantum Communications + Federated Learning + 6G + Quantum Computing + AI
5.5.2 Summary of Quantum Communications + IoT
As noted in Section 5.6, quantum communications use the principles of quantum mechanics to provide security that is theoretically immune against tampering or interception, and when combined with satellite communications, could enable global networks for secure transmission of data.
IoT enables interconnected devices to communicate and share data, via the internet. IoT is already becoming widespread across the world, finding applications across a wide range of industries, including healthcare, manufacturing, transport, and logistics, and with a wide range of applications. Widespread application of IoT has the potential to reduce human intervention, improve data collection, and streamlined data analysis. However, the increasing number of devices and connections in use pose a challenge to the security of these systems. (Cherbal et al. [footnote 85]).
IoT devices are used across a wide-range of applications and industries, and plays an important role in our lives which means that there is a wide range of sensitivities in their use, and protecting the data involved is important (Singh et. Al [footnote 86]). Cherbal et al. [footnote 85] discuss improving the security of IoT devices in a medical context, where devices may transmit sensitive medical information, whilst Zaballos et al.[footnote 87] discusses the internet of remote things, where disparate devices around the globe may be used to record data about the earth. Senapate et al. [footnote 88] write that in the modern age, industry and manufacturing depend of technologies such as IIOT (Industrial IoT), and securing their data is critical to a successful enterprise.
However, IoT devices have faced a number of security vulnerabilities in the past. Cherbal et al. [footnote 85] review the range of attacks that IoT devices have been subject to, including man-in-the-middle attack, denial-of-service attacks, eavesdropping attacks, among others. Cherbal et al. note that for IoT devices, quantum communications has important implications for IoT that enhances the security of IoT devices and networks. Importantly, the development of quantum computers will mean that current cryptography will mean that current public key cryptography methods will no longer be secure, and quantum communications are a method to mitigate this risk.
The papers reviewed as part of this literature review cited several ways in which convergence of IoT with quantum communications provide better capabilities for IoT, and enable secure use of IoT in new situations. These include:
-
Quantum Key Distribution (QKD) - QKD is the most common technology described in the reviewed papers, with [footnote 89] describing how it can be used to facilitate secure IoT data exchanged, in an inherently tamper proof manner. Qu et al. [footnote 90] write that Quantum Key Distribution has the potential to solve challenges to IoT communications stemming from attack by quantum computers, which is essential to sensitive IOT use cases such as IoMT (Internet of Medical Things). Cherbal et al. [footnote 85] that QKD has the potential to enhance the confidentiality and integrity of transmitted data.
-
Quantum Direct Communications, Quantum Internet, Quantum Cloud - Quantum Direct Communications enable direct communications of quantum information (as opposed to just a key, as with QKD). The reviewed papers considered these systems as part of a quantum internet, or quantum cloud, allowing IoT devices to communicated directly using quantum technology.
-
Singh et al. [footnote 86] expects that the quantum internet will operate alongside the classical internet, enhancing IoT by providing a channel that safeguards data integrity and privacy.
Zaballos et al. [footnote 87] expand on the potential benefits of the quantum internet to IoT, proposing that a quantum internet, with a quantum consensus layer, could minimise communication overheads in IoT environments, by reducing reliance on traditional fault tolerance mechanisms that use network bandwidth. This could have particular benefit in constrained environments, where connectivity is challenging (such as Antarctica), combining with satellites to obtain connectivity.
El-Azzaoui et al. [footnote 91] explore how this could be used in a medical setting, describing a quantum system, including IOT devices, which makes use of Quantum Secure Direct communications to enable a Quantum Cloud Infrastructure. El-Assaoui et al. explain a system that enables distributed use of quantum computers to enable large amounts of processing power, enabling better processing of IOT data, in a medical setting. De Alwis et al.
De-Alwis et el. [footnote 92] explain how quantum optical networks, a form of Quantum Direct Communications could be used to acquire IOT sensor data in the quantum form - improving speed and accuracy - and expects that quantum communications will form a part of 6G networking, enabling these applications.
-
Quantum Signatures, Quantum Hashes - Liu et al. [footnote 93] describe how the use of quantum signatures and quantum hashes for IoT devices could enable quantum secure non-reputability and data integrity, allowing the use of blockchains in an IOT setting, secure against attack by quantum computers.
These individual quantum communications technologies can be combined together to provide network and enable IoT applications. Liu et al. [footnote 93] and El-Azzaoui et al. [footnote 91] present architectures for combining these technologies into architectures to enable networks of IOT devices to communicate securely. Liu et al. describe a network that combines QKD networks with classical networks to provide an IoT network that is secure against classical and quantum attackers. El-Azzaoui et al. [footnote 91] proposes a system where quantum terminals are as endpoint devices to provide quantum network access to low-powered, cheap devices such as IoT sensors.
As quantum communications mature, convergence with IoT will enable integration with other quantum use case, improved privacy, data integrity, and could improve the capabilities of IoT in constrained environments. There are a range of quantum technologies that could be integrated, from QKD, which enables key agreement, through to quantum internet and quantum clouds which may enable IoT data to be processed by future quantum computers.
Identified Technology Groupings
Section 5.6 identified that IOT would group with Quantum Communications and LEO satellites to provide wide-ranging communications. In addition to this grouping, this pairing identified the following groupings:
-
Quantum Communications + IoT + Blockchain + Quantum Cloud - [footnote 91] proposed a quantum cloud architecture to improve the security of Medical IOT devices. El-Azzaoui posits the idea of a Quantum Terminal - which acts as a translator, meaning that each endpoint device doesn’t need a quantum processor. [footnote 89] describes a quantum inspired blockchain which makes use of quantum principals to improve blockchain security, while [footnote 90] suggests a system for secure Internet of Medical Things, making use of blockchains and quantum communications to securely share medical information.
-
Quantum Communications + Federated Learning + 6G + Quantum Computing + AI - Javeed et. al [footnote 94] discuss how IoT sensors, combined with quantum communications could allow for secure federated learning, allowing for IoT data to train large AI models in a decentralised manner.
5.5.3 Quantum Communications + IoT Cyber Implications
In this section, we explore the cyber security consequences of the convergence of quantum communications with IoT technologies. A primary consequence of this convergence, covered by multiple papers reviewed in this process [footnote 89], [footnote 88], [footnote 95], [footnote 96], [footnote 90], [footnote 97]) is that quantum communications address the threat to cryptography from quantum computers. Quantum communications, including QKD, provide improved privacy and integrity protection. Eavesdropping and man-in-the-middle attacks are protected against by allowing a user to detect if someone is intercepting their communications.
-
Secure Federated Learning: Javeed et al. [footnote 94] discusses how quantum communications could help secure federated learning, where machine learning or AI algorithms are trained in a decentralised manner, combining results following the training stage. Data from a large number of IoT sensors can be processed to train a model - integrity and privacy of the data can be assured using QKD, or quantum direct communications using quantum teleportation can be used to transport data quickly and efficiently - maximising transmission efficiency when combining data from geographically disparate sensors, and enabling quantum-secure-multi-party-computation.
-
Resilience: Zabellos et al. [footnote 87] suggests that quantum communications could provide more resilient communications in restrictive environments - Zaballos gives the example of IoT sensors deployed in Antarctica. This is due to the overhead required to ensure data integrity and deploy fault tolerance with classical communications. The data overhead can restrict the amount of data sent from an IoT sensor. Quantum communications, with a quantum consensus layer could reduce this overhead and increase the bandwidth.
-
Scalability: Javeed et al. [footnote 94] highlight potential risks with the scalability of quantum communications, with quantum entanglement potentially introducing additional communication overheads. Limitations in the distances that quantum communications can be transmitted, and the current need for communications to be point to point - discussed in section 5.6 - contribute to the challenges surrounding the scalability of IoT networks with quantum communications.
-
Denial-of-Service: Chawla et al. [footnote 97] discuss vulnerabilities that may occur during quantum communications - as discussed in Section 5.6, while presence of an eavesdropper is detectable, it also prevents communication until no eavesdropping is found on the channel - potentially leading to a denial-of-service - in the case of IoT devices, this could lead to real world consequences if data from IoT sensors is used to make decisions, or if IoT devices are used to affect the real world.
-
Side Channel Attacks:[footnote 95] notes that quantum secured IoT networks will face challenges from side channel attacks, where measurements such as power consumption, electromagnetic fields, or timing information reveal secret information about QKD derived secrets. Side-channels are a consideration in classic communications and cryptography, as the implementation of quantum communications is more complex and so likely to leak information.
-
Cost and Security Trade-offs: Quantum communications are likely to be expensive, especially in the context of IoT devices where millions of sensors may be deployed. El-Azzaoui et al. [footnote 91] suggest a solution with quantum terminals, which translates classical communications into quantum data for a quantum internet. Cao et al. [footnote 98] propose a solution of offline ‘charging’ of IoT devices with keys to enable cheap devices to use QKD derived keys. This introduces a physical security risk of an attacker accessing pre-charged keys from a device - leading to a security trade-off.
-
Power and Resource Constraints: Kumar et al. [footnote 95] extend the concept of IoT to drones, and highlights that power and resource constraints are likely to be a challenge, as quantum technologies, such as quantum drones, consume significantly more power, especially in real-time applications. The need for low size, weight, and power solutions presents a major hurdle.
5.5.4 Conclusions of Quantum Communications + IoT
Though quantum communications and IoT are distinct technologies, their convergence offers potential to enhance data security and operational capabilities of IoT. Quantum communications provide inherently secure data transmission methods, addressing vulnerabilities in IoT networks, particularly against threats from quantum computers. Technologies such as QKD, quantum internet, and quantum cloud are poised to strengthen IoT applications, improving privacy, data integrity, and resilience in constrained environments.
However, the convergence introduces challenges, including the scalability and cost of quantum technologies, the complexity of their implementation, and risks including side-channel attacks and the denial-of-service attacks having real world implications. These issues, alongside power and resource constraints, are critical to address for widespread adoption, particularly in IoT deployments requiring large-scale, low-cost sensors.
While early-stage demonstrations and proposals suggest promising use cases—such as secure medical IoT, federated learning, and blockchain — the practical implementation of these systems will depend on advancements in quantum communications. As the technologies mature, the integration of quantum communications with IoT is expected to become a cornerstone of secure, next-generation networks.
Research Question 1: Novel or Emerging Security Risks
-
Physical Security: For quantum communications to be secure, devices must act as trusted nodes. For IoT devices, trade-offs due to cost, and the physical locations of devices - may lead to devices being more accessible to attackers, and harder to secure. This influences the other key risks identified in this pairing.
-
Denial-of-Service: Eavesdropping on quantum communications leads to a denial-of-service for the system, rendering it unable to communicate securely. The distributed nature of IoT devices may make it harder to physically prevent this, and in the case of IoT devices, could lead to real-world consequences.
-
Side Channels: Side Channel Attacks, where indirect observations like timing, power consumption, or electromagnetic emissions are used to leak information from a system - can impact the security of quantum communications. The wide scale use of IoT devices could make physical access to attack quantum communications more possible for IoT than with other use cases.
Research Question 2: Industries Most Affected by the Compounding Cyber Security Risks
-
Healthcare
-
Manufacturing
-
Transport and Logistics
Research Question 3: Applications of Emerging Technologies Most Likely to Be Affected
-
Quantum Internet: The review highlighted the concept of quantum communications combining with IoT and quantum repeaters to create a quantum internet, creating a unified, tamper-proof network.
-
Federated Learning: Federated learning involves training models across multiple IoT devices while preserving data privacy. Javeed et al. [footnote 94] describe how quantum communications, such as QKD or quantum direct communications, can securely combine the training results from decentralised IoT sensors and protect the data from eavesdropping - enabling federated learning with sensitive data.
5.6 Low Earth Orbit Satellites and Quantum Communications
5.6.1 Identified Groupings
-
Large Scale IOT + LEO Satellites + Quantum Communications
-
Terrestrial Networks + Drone Swarms + LEO Satellites + Quantum Communications
5.6.2 Summary of Quantum Communications + Low-Earth Orbit Satellites
Low-Earth Orbit (LEO) Satellites, those that operate between 160km and 1600km above Earth’s surface, have emerged over the last few years with the potential to revolutionise wireless communications around the world. Services such as Starlink offer fast, low latency internet connections from anywhere with an uninterrupted view of the sky.
Alongside LEO satellites, quantum communications are being developed. Quantum communications make use of quantum phenomena to transfer information securely, with benefits including the theoretical inability for an observer to eavesdrop on communications.
There are a range of technologies that can be considered part of quantum communications, that the searches for this pairing returned. The majority of quantum communications with satellites focusses on Quantum Key Distribution, where a key is agreed using a quantum channel, and used to secure messages over a classical communications channel. However, Yue et al. [footnote 99] write about ongoing, rapidly progressing, research into Quantum Direct Communications, where quantum messages are used to directly transfer information.
As Quantum Communications are primarily a security technology, a range of the papers reviewed discussed how the convergence of Quantum Communications and Low-Earth Orbit Satellites could augment existing cryptography. A key current limitation of Quantum Communications and QKD is the distance and rate that information can be transferred. Terrestrial Quantum Communications requires high-quality direct fibre optic connections. The requirement to detect individual photons means that imperfections and losses in the fibre limits the distance that information can be transferred. The signals cannot be amplified, otherwise the quantum state collapses [footnote 99] limiting usage to point-to-point key distribution and short range communications. Saifur et al. [footnote 100] reports that satellites are developing as a more effective technique for distributing secure keys across long-distances, with research showing that ultimate limits of secret bit distribution through satellites is higher than a terrestrial chain of quantum repeaters, taking into account issues of background noise, diffraction. The authors claim that quantum communications will enable a new computing applications, such as ultra-secure communications and a new generation of high performance computers.
In Low Earth Orbit Satellite Security and Reliability, Yue et al. [footnote 99] review challenges encountered when implementing quantum communications via satellite - where Free-Space-Optical (FSO) communications are used with satellites, clouds and water molecules in the atmosphere may increase dispersion of signals. Aligned telescopes are required for communications, and the orbital heights of LEO satellites necessarily mean they move quickly across the sky, exacerbating the challenges of quantum communications with LEO. However, Beddington et al. [footnote 101] write that LEO satellites reduce signal losses due to beam diffraction compared to geostationary orbits, though connections to a base station can only occur when a satellite is overhead. The Chinese Micius satellite, for example only passes over its ground station for five minutes each night - limiting the security utility of the connection.
Xu et al. [footnote 12] extend the security provided by LEO satellites and quantum communications through exploring the concept of Quantum-Secured Space-Air-Ground integrated networks, potentially deployed as part of 6G cellular networks, where a combination of ground based, drone based, and satellite-based communications are used to provide ubiquitous network connections. This could mitigate some of the trade-offs of making use of satellite-based communications - limitations due to weather or atmospheric conditions, whilst enabling the long-distance secure quantum communications that satellites enable - making highly secure quantum networks more scalable.
The majority of the literature reviewed considered how LEO technology could enable widespread quantum communications. However, Khan et al. [footnote 102] consider how quantum communications could be used to secure satellites - the communications channel being one threat vector affecting satellites. Quantum communications have the potential to enable robust secure communications vital for satellite cyber security, however, there are engineering issues that remain, including the miniaturisation of equipment, and the need for equipment to tolerate extreme temperatures and radiation to provide resilient communications. Khan proposes combining quantum communications with blockchain, zero trust infrastructure, and AI driven intrusion detection/prevention (IDS/IPS) to enable robust security for satellite communications.
Identified Technology Groupings
Several additional convergences of technologies emerged from the literature. Broadly, the research showed quantum communications as forming a part of a wide-scale, futuristic global communications networks, providing secure, ubiquitous connectivity across the globe. Research forecast 6G cellular networks including LEO satellite communications, and quantum communications playing a role in securing these networks.
-
Large Scale IOT + LEO Satellites + Quantum Communications - Dhar et al. [footnote 103] discusses how QKD and LEO might enable large scale IOT, providing integrity and authenticity to data for a huge number of internet connected devices. Yue et al. [footnote 99] describes a similar concept, with LEO providing connectivity for remote devices - the Internet of Remote Things (IoTR). However, Dhar acknowledges that there are significant issues to be resolved to enable this, including how to prevent denial-of-service attacks against quantum communications.
-
Terrestrial Networks + Drone Swarms + LEO Satellites + Quantum Communications - Wang et al. [footnote 104] describe how quantum communications could form part of the security of a Space-Air-Ground network as part of 6G cellular communications, enabling a resilient, far-reaching network. Wang describes how this system could enable use cases where there is a need for a large amount of data to be transferred securely - for example digital twin or metaverse use cases. These networks could also enable security to enable widespread federated learning for AI systems.
5.6.3 Quantum Communications + Low-Earth Orbit Satellites Cyber Implications
As quantum communications and quantum key distribution is a security technology, cyber security aspects of their convergence are widely considered across the reviewed literature. A key feature of quantum communication is the ability to provide theoretically secure communications, with the ability to detect eavesdroppers. [footnote 102] considers how this could be used alongside other technologies to enable secure command and control of satellites. However, other research considers facets of quantum communication security that would be affected through making use of LEO satellite communications.
As a rule, where vulnerabilities are considered, they apply to quantum communications as a whole - the impact from convergence with LEO satellites is a change in the threat surface and how an attacker might exploit a vulnerability.
From the literature, the key cyber security themes relevant to Quantum Communications and Satellite Communications can be categorised into the following areas:
-
Eavesdropper Detection - One of the key benefits of quantum communications is the ability to detect when eavesdroppers are intercepting a message, as measurement of the signal affects the quantum attributes. This is widely discussed across the reviewed literature.
-
Side Channels - Dhar et al. [footnote 103] state that in principle, passive side-channels attacks could be carried out against quantum communications equipment, revealing information leading to loss of security, Tedeschi et al. [footnote 105] highlights the need to develop testing equipment to develop resilience against this.
-
Resilience of Communications - Though quantum communications prevent eavesdropping leading to loss of sensitive information, Dhar et al. [footnote 103] that attempts to eavesdrop lead to denial-of-service attacks, as the quantum channel is rendered unusable, and there is a need to develop defences to prevent these attacks. Beddington et al. [footnote 101] considers that LEO satellites could be more resistant to Denial-of-Service attacks in this way, as targeting a fast moving satellite for interception may be more difficult than other quantum communications methods.
-
Physical security - The security of quantum communications depends on the security of trusted nodes. Bedington et al explain that in the case of LEO enabled quantum communications, the satellite will be a trusted node, and so the security of the satellite against attack is important. [footnote 101]. The approach suggested by Khan et al. [footnote 102] shows how quantum communications, alongside other technologies, could form a part of this solution.
5.6.4 Case Study: Space Air Ground Integrated Networks
Identified by research papers ([footnote 12], [footnote 104]) as part of the literature review as a technology that could be used to enable 6G cellular networks, Space Air Ground Integrated Networks (SAGIN) are an example of a wide-range of technologies converging to provide new capabilities, and extend the capabilities of the contributing technologies, that could, in turn, be used as an enabling technology to allow further use cases, such as the Internet of Remote Things described by Zaballos [footnote 87], referenced in section 5.5.
In recent years, we’ve seen the development of the technologies that could combine to form a SAGIN network. Ground-based networks are commonly used, whilst Alphabets Project Loon [footnote 106] has been testing the use of balloon-based networks to provide internet to remote areas, and SpaceX [footnote 107] offers global, space based connectivity, making use of a large constellation of low earth orbit satellites.
Wang [footnote 104] explores the benefits of combining Space, Air, and Ground networks in the context of a quantum secured SAGIN. Figure 8 shows the strengths and weaknesses of each network technology.
Space-based networks are expensive to deploy, have limited bandwidth - today, despite global coverage, SpaceX have limit customers in a geographical area - and are hard to reconfigure. However, they enable global coverage, and can be available at all times.
Air-based networks are affected by weather, and have a limited energy capacity - especially in the case of drone-based networks - meaning a need to constantly refuel or recharge, and will have less geographical coverage than a satellite-based network. However, an air-based network is easily reconfigurable, mobile, and is scalable to different bandwidth needs.
Ground-based networks have limited coverage, are hard to scale, and are not easily reconfigurable once installed. However, they enable high bandwidth, low latency, and are relatively cheap to construct.
SAGINs combine these technologies, using heterogeneity to optimise the performance of a global network, utilising the advantages of each kind of technology to provide high-reliability and network throughput.[footnote 108]
Figure 6: An internet balloon as used by Alphabet’s Project Loon.

Figure 7: A Space-X rocket carrying a payload of 60 StarLink satellites into orbit.

Technology Convergences
Space-Air-Ground Integrated Networks are enabled by the convergence of a wide range of technologies. Drones Technology, though Project Loon makes use of internet balloons, Air-based networks are likely to make use of networks of drones. As large networks of drones working together will be necessary to provide connectivity, Swarm Technology will be needed to ensure that drones work together to provide the best capability. Artificial Intelligence will be widely used throughout the network, including control of drone swarms and optimising network routing to ensure that user traffic takes the most efficient route through the network. [footnote 108]
SAGIN networks will enable a wide range of other technologies. Xu et al. [footnote 12] describe SAGIN being used to provide a reliable network for widespread quantum communications and predicts SAGIN networks becoming a central part of 6G connectivity. Chen [footnote 108] describes SAGIN networks enabling a wide range of capabilities, including large networks of widely spread IOT devices, Intelligent Transport Systems, alongside applications such as disaster recovery.
Cyber Security Considerations
-
Network resilience - A key benefit of SAGIN is network resilience. Where single network technologies are used, there is an increased risk of failure - whether natural disasters affect terrestrial networks, or owners of space based networks restricting access, as Starlink have during the Ukrainian war. ([footnote 109],[footnote 110]), or whether network technologies is affected by a cyber attack. The combination of technologies aligned with advanced AI-based network routing will mean that failure of one technology type could lead to traffic being seamlessly rerouted through alternative technologies, ensuring continued connectivity. This multi-layered approach reduces the risk of complete network outages and enhances the overall robustness of communication systems, particularly in critical scenarios such as disaster recovery, military operations, and remote area coverage.
-
Regulatory compliance and cross-border issues are a key consideration for SAGINs, as the integration of space, air, and ground networks often involves cross-border data transmission, leading to conflicts between national laws on privacy, data protection, and surveillance. Operators must navigate varying legal and regulatory environments to ensure that data protection, encryption, and operational security measures meet local and international requirements.
-
Development of SAGINs will require coordination of regulations across national boundaries, and across industry regulatory bodies - to handle demand such as spectrum management, airspace regulation, and security in three-dimensional spaces. [footnote 111]
-
Legal Intercept - Countries may have differing legal frameworks governing lawful intercept, making it difficult to implement consistent policies across the network. The technical implementation of lawful intercept in a SAGIN environment will be challenging, as it requires access to diverse and often highly secured communication channels, such as satellite links and encrypted air-to-ground transmissions, without compromising the overall security of the network.
-
Cross-domain attacks - The integration of different network layers in SAGINs—spanning space, air, and ground—introduces unique vulnerabilities specific to each domain, creating cross-domain attack vectors. Satellites can be targeted through interception or signal jamming, unmanned aerial vehicles (UAVs) may face risks of hijacking or data breaches, and ground stations are susceptible to physical and cyber intrusions. These interconnected vulnerabilities mean that a successful attack in one layer could potentially compromise other parts of the network. Networks will need to be designed to ensure that security controls ensure that compromise of one aspect of the network doesn’t lead to failure or compromise of other aspects.
Figure 8: Strengths and weaknesses of each component of a Space-Air-Ground (Quantum Secured) network.
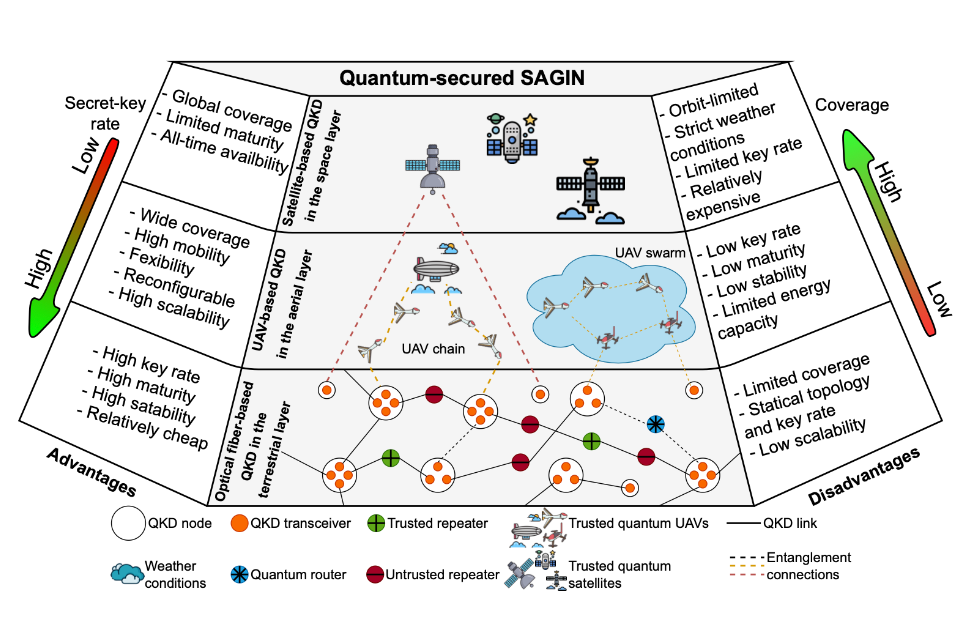
5.6.5 Conclusions of Quantum Communications + Low-Earth Orbit Satellites
Though considered as a pairing of emerging technologies for this analysis, most of the research considers LEO satellite communications as an enabling technology for quantum communications, with a minimal amount of research looking at the potential opposite directions. This is possibly because while LEO satellites are an emerging technology in terms of new use cases and the opportunities they may bring - command and control of satellites is mature and understood.
This is also reflected in the security aspects considered - the affects look at the security of quantum communications, not how it would affect the LEO satellite use itself - because LEO satellites are enabling quantum communications rather than converging together.
From the use cases presented in the research, it appears unlikely that LEO satellites and Quantum Communications will directly enable new applications - though Chinese demonstrations of secure video calling were discussed, the main use cases see quantum communications and LEO satellites as forming part of a wider network, enabling secure communications as part of next generation networks.
Research Question 1: Novel or Emerging Security Risks:
-
Communication Resilience: Attempts to eavesdrop on quantum communications can lead to denial-of-service, as measurement changes the quantum information. The use of LEO satellites mean that the information is transmitted across free space, and an attacker may be able to intercept the information to cause a denial-of-service. Use of LEO satellites may mitigate this risk compared to higher orbit satellites, as they move faster across the sky, making interception more difficult.
-
Physical Security: The security of quantum communication relies on the security of trusted nodes. The use of LEO satellites for quantum communications will mean that the satellite is a trusted node. Robust satellite security is important to ensure that the communications channel remains secure.
-
Side Channels: Quantum communications equipment could be vulnerable to side channel attacks. Side channel attacks are unintended information leak from a system, often exploited through indirect observations like timing, power consumption, or electromagnetic emissions. Attackers could exploit side channels by analysing hardware imperfections, detecting stray optical signals, or measuring fluctuations in system operations to infer secret quantum key exchanges without breaking quantum cryptographic principles.
Research Question 2: Industries most affected by the compounding cyber security risks:
-
Telecommunications
-
Defence
Research Question 3: Applications of emerging technologies most likely to be affected by technology convergence:
-
SAGIN Networks: As explored in the use case, Space-Air-Ground Integrated Networks are likely to make use of, or support the use of, the integration of quantum communications to provide secure global connectivity. These networks will potentially form part of 6G wireless communications.
-
Large Scale IoT: As IoT deployments increase in breadth and coverage, LEO and quantum communications have the potential to provide wide-scale, global, secure network coverage.
5.7 Edge Computing and IoT
5.7.1 Identified Groupings
-
Fog/Edge Computing + IoT + AI
-
Fog/Edge Computing + IoT + Machine Learning
-
Fog/Edge Computing + IoT + Cryptography
-
Fog/Edge Computing + IoT + Blockchain
5.7.2 Summary of Fog/Edge Computing and IoT
Fog and edge computing, combined with the Internet of Things (IoT), offer a transformative solution to key challenges in distributed systems, such as reducing latency, improving scalability, and enhancing security. A review of the identified literature reveals advancements in this field, highlighting its potential to enhance cyber security while introducing novel challenges. The reviewed papers collectively explore applications in smart cities, healthcare, and vehicular networks, providing information on the theoretical and practical implications of integrating these technologies.
Despite their contributions, the literature highlights the dual-edged nature of this convergence. On the one hand, localised data processing and decentralised architectures improve threat detection and privacy preservation. On the other hand, they expand the attack surface, complicate interoperability, and impose resource constraints.
5.7.3 Cyber Security Impacts of Fog/Edge Computing and IoT
Across the reviewed literature, there is no evidence of a transformative new cyber security paradigm, or a fundamental redefinition of vulnerabilities introduced by the convergence of edge computing and IoT. Instead, the focus remains on addressing conventional cyber security challenges, particularly in protecting the vast quantities of sensitive data generated and processed within these systems. While familiar threats such as data breaches, denial-of-service (DoS) attacks, and malware persist, the implications of these risks are amplified in edge-IoT ecosystems due to their reliance on distributed architectures, real-time processing, and the heterogeneity of connected devices.
From the literature, the key cyber security themes relevant to edge computing and IoT can be categorised into the following main areas:
-
Data Privacy and Protection: The distributed nature of edge computing, combined with the vast data generated by IoT devices, increases the importance of robust measures for data privacy and protection. Ruiz-Villafranca et al. [footnote 62] and Rupanetti and Kaabouch [footnote 61] emphasise the need to protect sensitive data, such as healthcare records, vehicular telemetry, and real-time sensor outputs. Techniques such as encryption, tokenisation, and anonymisation are critical to preventing unauthorised access and data breaches. Moreover, compliance with privacy regulations, such as GDPR and HIPAA, is essential to maintaining trust in edge-IoT systems. Despite these measures, the real-time nature of data processing at the edge introduces challenges in balancing privacy with performance requirements.
-
Vulnerabilities in Edge-IoT Systems The decentralised and resource-constrained architecture of edge-IoT systems makes them susceptible to a range of cyber threats. Senthil et al. [footnote 64] and Burhan et al. [footnote 65] highlight vulnerabilities in edge nodes, including the risk of malware injection, data manipulation, and physical attacks. Additionally, the heterogeneity of IoT devices complicates the development of uniform security protocols, increasing the likelihood of misconfiguration and security gaps. These weaknesses require the implementation of lightweight yet effective security solutions, such as secure boot mechanisms, intrusion detection systems, and secure firmware updates.
-
Resource Constraints in Edge-IoT Systems Edge devices often operate with limited computational power, memory, and energy, as highlighted in [footnote 65] and [footnote 61]. These resource constraints restrict the deployment of robust, resource-intensive security measures, such as advanced encryption algorithms or deep learning-based intrusion detection systems. For instance, while traditional cloud systems can rely on centralised and resource-rich environments for complex security operations, edge devices must prioritise lightweight and efficient solutions. This limitation makes them more susceptible to attacks, as attackers can exploit the reduced defensive capabilities of resource-constrained edge nodes. Addressing this challenge requires innovations in lightweight cryptographic techniques, optimised intrusion detection system algorithms, and energy-efficient security protocols tailored to edge environments.
-
Heterogeneity and Policy Enforcement Challenges The vast diversity of IoT devices and edge nodes in terms of hardware capabilities, operating systems, and communication protocols creates significant challenges in enforcing consistent security policies, as emphasised in [footnote 66]. This heterogeneity increases the likelihood of configuration errors, leaving devices vulnerable to exploitation. For example, a single insecure IoT device within a network can act as a weak link, compromising the entire system. Moreover, maintaining interoperability while implementing robust security measures becomes complex when dealing with devices from different manufacturers with varying standards and specifications. Mitigating these issues requires standardised security frameworks, universal communication protocols, and automated tools for detecting and rectifying configuration vulnerabilities.
-
Ethical and Responsible Use Ethical considerations in the deployment of edge-IoT systems include ensuring fairness, transparency, and accountability in their operations. Humayun et al. [footnote 66] and Rupanetti et al. [footnote 61] discuss the importance of aligning security practices with ethical AI principles, particularly in applications such as healthcare and autonomous vehicles. Transparency in data handling and security protocols is vital to building trust among stakeholders, while fairness ensures that security mechanisms do not disproportionately disadvantage specific user groups or regions.
-
Expanded Attack Surface and Systemic Risks The proliferation of IoT devices and edge nodes significantly expands the attack surface, as noted in [footnote 65] and [footnote 66]. Each device and node become a potential entry point for attackers, increasing the likelihood of systemic risks. Distributed denial-of-service (DDoS) attacks, ransomware, and supply chain attacks are particularly concerning in edge-IoT environments. These risks underscore the need for proactive measures such as network segmentation, device authentication, and anomaly detection to minimise vulnerabilities and ensure system resilience.
-
Insufficient Integration of Security in Emerging ApplicationsEmerging edge-IoT applications, such as smart cities, healthcare monitoring, and vehicular networks, often prioritise functionality over security in their initial design phases. Jamshidi et al. [footnote 112] and Ruiz et al. [footnote 62] highlight the lack of robust security frameworks in these domains, which can lead to significant vulnerabilities. For example, while healthcare IoT systems leverage edge computing for real-time patient monitoring, insufficient encryption and access controls can expose sensitive data to breaches. The literature calls for interdisciplinary approaches to embed security considerations into the design and deployment of these systems from the outset.
-
Stakeholder Awareness and Training: As highlighted in [footnote 66], a lack of cyber security awareness among stakeholders remains a critical challenge. This gap is particularly evident in industries adopting IoT and edge technologies, where operational priorities often overshadow security concerns. Effective training programs and awareness campaigns are necessary to equip stakeholders with the knowledge to identify and mitigate cyber threats, ensuring the secure deployment and operation of edge-IoT systems.
5.7.4 Emerging Countermeasures
The novel challenges identified in edge-IoT systems require innovative approaches to secure distributed networks and their broader ecosystem. Based on the insights from the reviewed papers, several promising developments and countermeasures have been proposed to address vulnerabilities such as resource constraints, privacy breaches, and attacks on heterogeneous and decentralised architectures.
-
Lightweight Cryptographic Techniques: [footnote 65] and [footnote 61] highlight the use of lightweight encryption algorithms and hashing techniques that balance security and computational efficiency. These approaches are particularly effective for securing IoT devices with limited processing power and energy capacity and are designed to secure data transmission and storage.
-
Multi-Level Intrusion Detection Systems: [footnote 64] proposes a novel multi-level intrusion detection system that dynamically adjusts security measures based on the severity of detected anomalies. This adaptive approach protects edge-IoT networks by identifying and responding to potential threats in real-time and optimising resource usage while maintaining robust defence mechanisms.
-
Decentralised Security Frameworks: [footnote 66] and [footnote 61] discuss the integration of blockchain technology for managing device authentication and ensuring the integrity of data across distributed edge nodes. Blockchain’s decentralised ledger system is effective in mitigating data tampering and enhancing transparency.
-
AI-Driven Threat Detection: [footnote 65] and [footnote 66] highlight the use of machine learning algorithms for detecting anomalies in network behaviour and identifying malicious activities. Techniques such as federated learning enable secure model training across decentralised datasets without exposing sensitive information.
-
Secure Communication Protocols: [footnote 62] and [footnote 66] emphasise the development of secure communication protocols tailored for IoT and edge devices, such as lightweight Transport Layer Security (TLS) variants and end-to-end encryption techniques. These protocols ensure the confidentiality and integrity of data streams in highly dynamic environments.
-
Privacy-Preserving Techniques: [footnote 61] highlights the use of differential privacy and anonymisation techniques to safeguard sensitive information without compromising data utility for analytics and AI model training.
5.7.5 Case Study: Edge Computing and IoT Synergy for Smart Manufacturing Systems
The synergy between Edge Computing and IoT has brought transformative changes to industries like smart manufacturing by enabling real-time decision-making, reducing latency, and enhancing cyber security. By processing data closer to its source, edge computing minimises the need for sensitive information to be transmitted to centralised cloud servers, thereby reducing exposure to potential cyber threats. This convergence improves operational efficiency and strengthens security but also introduces unique challenges that demand innovative solutions.
Real-World Examples:
AWS IoT Greengrass a cloud-based service that extends AWS capabilities to local edge devices. It enables secure and efficient data processing, machine learning inference, and device management at the edge, allowing IoT systems to operate even when not connected to the cloud. (https://aws.amazon.com/greengrass/)
Cisco Edge Intelligence: A solution designed to streamline IoT data processing and enhance security at the network edge. (https://developer.cisco.com/edge-intelligence/)
Key References
[footnote 113] explores how edge computing can enhance IoT security by integrating machine learning techniques with key agreement protocols.
[footnote 114] discusses the security, privacy, trust, and regulatory challenges associated with the integration of edge computing and IoT. The authors discuss how the convergence of these technologies introduces new vulnerabilities, particularly concerning data breaches, and examine the implications for user trust and compliance with regulations
Technology Convergences
The synergy between edge computing and IoT is characterised by their complementary roles in enhancing data handling and security. IoT devices, such as sensors, collect vast amounts of real-time data in manufacturing systems. Edge computing processes this data locally, reducing latency and enabling rapid responses to potential security threats. This integration is further strengthened by AI, which analyses edge-processed data for anomaly detection and predictive analytics. Secure communication protocols ensure data integrity during transmission between IoT devices and edge nodes, while privacy-preserving techniques safeguard sensitive information. Together, these technologies optimise performance, improve system reliability, and enhance security.
Cyber Security Challenges and Solutions
While the synergy between edge computing and IoT enhances cyber security by decentralising data processing, it also introduces new risks. Edge devices are often deployed in physically accessible or less secure environments, making them vulnerable to tampering or unauthorised access. These nodes can act as entry points for attackers to infiltrate broader IoT networks, leading to data breaches and system disruptions. Insecure communication protocols between IoT devices and edge nodes can further compromise data integrity, while the heterogeneity of IoT devices and edge platforms complicates standardisation efforts and creates inconsistencies in security implementations. Additionally, resource constraints on edge devices, such as limited computational power, make deploying robust security measures challenging. Managing the security of distributed edge nodes across large IoT networks and ensuring real-time threat detection are also significant hurdles.
Despite these challenges, the synergy offers numerous opportunities to strengthen cyber security. A zero-trust architecture enforces strict access controls and authentication mechanisms to protect both edge nodes and IoT devices. Privacy-preserving techniques, including data anonymisation and encryption, secure sensitive information during edge processing. AI-driven threat detection systems tailored to the resource-constrained edge environment enable real-time anomaly identification and proactive responses to threats. Standardisation and interoperability frameworks ensure secure communication and seamless integration across diverse edge-IoT ecosystems. Regular firmware updates address emerging vulnerabilities, enhancing the resilience of edge devices against cyber threats. These solutions collectively ensure that the benefits of edge computing and IoT synergy are realised without compromising system security.
5.7.6 Conclusions
The combination of edge computing and IoT creates a powerful technological framework but also introduces significant cyber security challenges. As IoT devices become integral to critical applications such as healthcare, smart cities, and autonomous systems, they blur the boundaries between physical and digital infrastructures. This convergence creates unique security risks, where cyberattacks not only heighten the risks of data breaches but can disrupt essential services, jeopardising safety and trust in these systems.
Emerging countermeasures, such as lightweight cryptographic techniques, adaptive intrusion detection systems, decentralised frameworks like blockchain, and AI-driven threat detection, demonstrate significant potential in mitigating these risks. These solutions are specifically tailored to address the unique constraints of edge-IoT systems, such as limited resources and diverse device ecosystems while enhancing security and resilience.
Moving forward, it is critical to embed security considerations into the design and deployment of edge-IoT systems. This includes fostering interdisciplinary collaboration, developing standardised security frameworks, and prioritising stakeholder education to ensure comprehensive protection. By addressing these cyber security challenges proactively, edge-IoT ecosystems can achieve their transformative potential while maintaining trust and safety in their applications.
Research Question 1: Novel or Emerging Security Risks
-
Increased Attack Vector:The proliferation of IoT devices and edge nodes creates more entry points for cyberattacks, such as Distributed Denial-of-Service (DDoS) attacks, ransomware, and supply chain compromises. Each device and node becomes a potential target, amplifying the risk of systemic breaches.
-
Limited Security Capabilities Due to Resource Constraints: Edge devices often have limited computational power, memory, and energy, making it challenging to implement robust security measures. This limitation leaves them vulnerable to exploitation, as attackers can target their reduced defensive capabilities.
-
Decentralised System Vulnerabilities: The decentralised architecture of edge-IoT systems makes them more susceptible to malware, data tampering, and physical attacks. The lack of uniform security protocols across heterogeneous devices further increases these vulnerabilities.
Research Question 2: Industries Most Affected by the Compounding Cyber Security Risks
-
Healthcare & Medical IoT
-
Smart Cities & Infrastructure
-
Autonomous Vehicles & Transportation Systems
-
Industrial IoT & Smart Manufacturing
-
Energy & Smart Grids
-
Retail & Supply Chain Logistics
Research Question 3: Applications of Emerging Technologies Most Likely to Be Affected
-
Smart Healthcare & Medical IoT: Edge computing in healthcare enables real-time patient monitoring and AI-driven diagnostics, but vulnerabilities in data privacy, device authentication, and resource-constrained security mechanisms pose significant cyber security risks. A compromised edge node could expose sensitive patient data, disrupt medical operations, or cause faulty AI-driven diagnoses.
-
Autonomous Vehicles & Transportation Systems: Edge computing allows low-latency data processing for self-driving vehicles and smart traffic management, but attackers could exploit data poisoning vulnerabilities, sensor manipulations, or real-time communication failures to mislead autonomous vehicles or disrupt road safety infrastructure.
-
Industrial IoT & Smart Manufacturing: Edge computing supports predictive maintenance, automation, and AI-driven optimisation in smart factories. However, adversaries can target edge nodes controlling critical industrial processes, leading to malfunctions, production halts, or cyber-physical attacks that compromise factory operations.
5.8 Brain-Computer Interfaces and Robotics
5.8.1 Identified Groupings
- Brain-Computer Interfaces + Robotics + AI/ML
5.8.2 Summary of Brain-Computer Interfaces + Robotics
A brain-computer interface (BCI) is a system that enables direct communication between the brain and an external device, typically by interpreting neural activity - though as part of this literature review, we have considered papers which make use of both EEGs (Electroencephalograms), which measure electrical activity of the brain by detecting voltage changes on the scalp caused by neuronal firing, and EMGs (Electromyograms) which measure the electrical activity of muscles during contraction, a less direct connection to the brain. BCI technology can make communication with computers easier for humans, particularly in the case of people with severe neurological or muscular disorders, where BCIs can enable more natural control of, for example, speech software or prosthetics. [footnote 115].
Robotics combines principles from engineering, computer science, and artificial intelligence to develop systems that replicate or enhance human capabilities. These systems are employed across various industries, including manufacturing, healthcare, and exploration, to enhance efficiency, safety, and precision. A critical element of robotics is the human-machine interface, which plays a pivotal role in controlling robotic systems. This is where BCIs converge with robotics, with the potential to enable innovative applications, better control of robots, and human-robot co-operation, expanding the use of each technology.
Patel et al. [footnote 116] explains that BCIs enable intuitive and natural control of robots by decoding motor intentions from neural signals. A key application of this, from across the literature is assistive technologies, enabling individuals with neurological or physical disabilities to live more independent lives. Patel et al. [footnote 116] writes that BCIs can facilitate the control of prosthetic devices by decoding neural signals and translating them into commands for movement. Meng et al. [footnote 117] expand this use case to include exoskeletons - potential augmenting the capabilities of individuals with musculoskeletal issues, or motorised wheelchairs controlled by BCI interfaces.
Meng et al. [footnote 117] also explores non-medical use cases, including improved control of military robotics, or drones. Ouyang et al. [footnote 118] present a more complex set of use cases, with a framework to enable multi-brain, multi-robot co-operation, citing use cases such as co-creation, manufacturing, and immersive technologies such as the metaverse. The same paper describes how BCIs have been used to enable feedback from tactile feedback, allowing the user to ‘feel’ what a robotic arm is touching, demonstrating two-way communication via the brain interface.
A brain-computer-interface measures changes in voltage, whether directly from the brain, via the scalp, in the case of EEGs, or via muscular contractions in the case of EMG control - the traces of these measurements are commonly called brainwaves. There is a need to extract information from these brainwaves to determine the intention of the user. Patel et. al [footnote 116] describes how this makes use of machine learning and deep learning techniques to classify and interpret EEG signals and generate robotic control commands. The convergence of AI and machine learning techniques with robotics can mean that control accuracy reaches between 70% and 90%. Real time robotic control can be augmented through hybrid BCI models, combining both EEG and EMG control to reach higher accuracy rates.
Identified Technology Groupings
Brain-Computer Interfaces + Robotics + AI/ML: A key grouping described in the literature, and a key aspect leading to cyber security consequences in section 5.8.3, is the integration of AI algorithms with BCI and Robotics. Patel et al. [footnote 116] assess how various machine learning algorithms affects the accuracy of the system. Robust, trustworthy, AI models are required to ensure that BCI-robotic systems can be safely used and trusted by their uses.
5.8.3 Brain-Computer Interfaces + Robotics Cyber Implications
The convergence of BCIs with robotics means that cyber security attacks on systems could lead to dangerous situations. If an attacker were able to gain control of BCI controlled prosthetics or wheelchairs they may be able to lead users into physically dangerous situations, while denial-of-service attacks could cause users to lose personal independence.
Outside of assistive technologies, attacks on BCI interfaces could lead to unsafe situations. For example, where BCIs are being used for military applications, an attack that compromises the integrity of the system could lead to unintended actions - i.e. friendly fire incidents. [footnote 117]
Attacks against AI models:
As described in section 5.8.2, BCIs make use of machine learning interfaces to extract information from EEG or EMG signals and convert them into commands for the robotic system. Xue et al. (2021) [footnote 119] demonstrate how adversarial attacks on CNNs (Convolutional Neural Networks) can be used to compromise commands sent from an EMG based BCI to a robotic system. In 2022, Xue et. al (2022)[footnote 21] extend their attack to EEG-based BCIs.
An adversarial attack involves an attacker injecting a small change (or perturbation) into a signal which is designed to cause the machine learning algorithm to incorrectly classify the signal. These have previously been demonstrated on image recognition algorithms, with small perturbations to a captured image causing a stop sign to be interpreted as a national speed limit sign, for example. Xue et al. [footnote 119] state that in the case of BCI controlled systems and robotics, adversarial attacks are a security concern as attacks could lead to unintended commands being executed by a system.
Meng et al. [footnote 117] differentiates between white-box and black-box adversarial attacks on BCIs. A white-box attack assumes that the attack knows the details of the model, whilst a black-box attacker is not aware of the details of the system they are attacking. Meng shows that while white-box attacks are typically more powerful, both black-box and white-box attacks against BCIs are feasible.
Xue et al. (2022)[footnote 21] and Liu et al. [footnote 120] demonstrate Universal Adversarial Perturbation attacks against BCI systems, where attacks against systems are transferable - that is a perturbation which is likely to affect multiple AI models - meaning attacks are likely to be transferable between BCI systems.
Xue et al. [footnote 21] demonstrate a detection methodology for UAPs, allowing a user to detect when a system is subject to an adversarial attack, providing an early warning to the user. The framework achieves a detection rate of over 90%, demonstrating its potential as a defence mechanism.
Various mitigations against these attacks are considered in the literature. Meng et al. [footnote 117] consider defence approaches including more robust training of models, adversarial pruning, and model ensemble to improve resilience against attacks. These defences are used for other, non-BCI, adversarial attack mitigation. A common mitigation technique is input transformation, where model inputs are subject to some transformation to prevent adversarial attacks. In image recognition use cases, this could include compressing the image, or converting it to a difference file format. However, these transformations need to be specialised to BCI applications - Meng proposes six potential BCI data transformations including Gaussian noise addition or shifting the input.
Brainwave Information Recovery:
Patel et al. [footnote 116] describe the need to protect the personal information of users. As BCI interfaces are accessing and transferring information relating to a users brain activity, there is a risk of private or personal information being encoded in the signal outside of the control of the user. Li et al.[footnote 115] describe an attack where users of a BCI system are shown visual stimuli that increase the likelihood of private information being shared through brain activity, and transmitted brainwaves could include information about users feelings or emotions. Li proposes a BCI anonymiser to prevent this, stripping non-essential information from EEG data before transmission.
Ouyang et. al [footnote 118] propose a methodology to protect users privacy in a multi-user, multi-robot system. Heterogenous devices could lead to vulnerabilities in data processing and recognition. An encoding/decoding system that works at a semantic level is proposed to protect against this, encoding the meaningful information stored in EEG data before transmission to preserve privacy, and prevent private information being extracted from transmitted EEG data. The system describes making use of compressed AI models to allow this decoding to take place in resource-restricted environments.
BCI Device Wireless Interfaces:
Li et al. [footnote 115] describes how BCI devices could be exploited via their wireless interfaces, which are often put in place to allow doctors to adjust system settings remotely. Li describes that an attacker could remotely exploit these devices, only requiring a malicious device to be in proximity to the BCI user. Patel et al. [footnote 116] describe how devices should implement good security controls, including biometrics, authentication, and encryption to protect users sensitive data. Patel also describes how user consent and an ethical approach is necessary to ensure that users understand the risks.
5.8.4 Conclusions of Brain-Computer Interfaces + Robotics
The literature review found that the convergence of BCIs and robotics could have transformative implications across a wide range of applications, not least in assistive technologies, where improvements to prosthetics, wheelchairs, and emerging technologies such as exoskeletons could lead to wide improvements in people’s standards of living.
However, as the convergence of these technologies relies on AI/ML models, systems are vulnerable to similar attacks as other AI/ML applications. Given the real-world, physical aspects of robotics, this has the potential to lead to safety implications. The literature also showed that, since BCIs are, by definition linked to user’s brains, there is a risk of private data - thoughts and emotions - being leaks by the systems. Approaches to handle this range from standard cyber security measures, through to developing specialised semantic encoding methods to minimise data transfer. The research shows that as the technologies are adopted it will be critical to consider how the convergence of BCIs and robotics will have unique and specialist impacts on cyber security.
Research Question 1: Novel or Emerging Security Risks
-
Novel Privacy Risks: BCIs introduce novel privacy risks, due to being able to directly access a user’s brainwaves - an attacker able to access raw data may be able to recover private thoughts or feelings. Methods are proposed to mitigate these risks, including stripping non-essential information from brainwave date prior to transmission.
-
AI Attacks: AI introduces new classes of vulnerabilities, unique to AI applications. For BCIs, adversarial AI attacks could be used to prevent robotics from working as intended - potentially putting the user at physical risk. Mitigations are proposed to improve resilience against these attacks, including adversarial pruning, and techniques to detect when systems are under attack.
-
Medical Device Vulnerabilities: Data can be leaked, or BCI interfaces compromised via the wireless interfaces used to adjust system settings - like any medical IoT device. These risks can be mitigated with robust cyber security, such as authentication and strong encryption.
Research Question 2: Industries most affected by the compounding cyber security risks:
-
Defence
-
Healthcare
-
Manufacturing
Research Question 3: Applications of emerging technologies most likely to be affected by technology convergence:
-
Assistive Technologies: Adaptive technologies, such as prosthetics, wheelchairs, and exoskeletons, stand to benefit significantly from the convergence of BCIs and robotics, enabling more intuitive control through neural control - potentially improving user’s independence and quality of life. However, the novel risks and vulnerabilities discovered in this literature review show the potential for users’ privacy to be compromised, and for users to be placed in physically dangerous situations through AI attacks.
-
Drone Control: BCIs have the potential to enable more precise control of drones and other robotics, potentially allowing closer human/machine working, and reduced reliance on manual input. However, adversarial attacks in these situations could lead to a loss of control integrity, with the potential for dangerous or unintended actions.
5.9 Biological Computing and IoT
5.9.1 Identified Groupings
-
Biomedical Computers + IoT + AI
-
Biomedical Computers + IoT + DNA-based cryptography
5.9.2 Summary of Converged Pairing: Biomedical Computers and IoT
[footnote 121] is the only paper that appears at the first layer of review, this paper explores the security considerations at the intersection of biological computing and the Internet of Things (IoT). The study highlights the use of tiny, biocompatible, and non-intrusive devices that sense biological signals from the environment and transmit this data to centralised processing facilities via the Internet. This convergence has given rise to the concept of the Internet of Bio-Nano Things (IoBNT), which represents a significant advancement in sophisticated healthcare solutions. The nanoscale nature of these devices offers a distinct advantage for medical applications, enabling access to hard-to-reach areas, such as deep within tissues, for both sensing and actuation. Promising applications of IoBNT include the early detection of severe diseases like cancer, as well as remote diagnostics and treatment, such as targeted drug delivery.
5.9.3 Biomedical Computers and IoT Cyber Implications
Zafar discovered that through their literature survey in the field of security in bio-cyber interfaces, that research in this field is nascent, with only a small number of publications covering the topic. Since its publication in 2021, it appears that there has been no further published research in this field. The main sources of challenges in this paper has therefore been extracted related healthcare applications such as implanted medical devices (IMD) Camara, Peris-Lopez and Tapiador [footnote 122], Wireless sensor networks (WSN) Sharma, Bala and Verma [footnote 123] and Wireless Body Area Networks (WBAN) Usman et al [footnote 124].
Inherent Risks and Limitations of Nano-devices
Nano-devices, the foundational components of IoBNT, are inherently resource-constrained due to their miniature size. Their limited computational capacity, storage, and energy resources significantly hinder direct communication with macro-scale devices. To overcome these limitations, a hybrid Bio-Cyber Interface is employed, serving as a bridge between biochemical signals within the human body and electromagnetic signals for external processing, as outlined by Zafar et al. [footnote 121]. However, these constraints make nano-devices particularly vulnerable to attacks that exploit their limited resources, such as eavesdropping or manipulation of molecular communication channels.
Usman et al. [footnote 124] further highlight an additional challenge: the restricted access to medical devices like implants for security evaluation. Due to regulatory and ethical constraints, researchers often face difficulties in assessing these devices for vulnerabilities and testing the effectiveness of proposed defences. Many of these devices require specific justification and a prescription from a physician, making widespread testing and evaluation a significant hurdle. This lack of accessibility creates a gap in understanding and mitigating potential security threats to IoBNT systems.
Security Threats to the Bio-Cyber Interface
The Bio-Cyber Interface is a fundamental component of the IoBNT ecosystem, acting as the bridge between the biological signals within the human body and the external digital world. This interface enables critical functionalities such as real-time monitoring, data processing, and control of embedded nanoscale devices. However, its central role in facilitating communication and control also makes it a significant attack vector. Malicious actors could exploit vulnerabilities in the Bio-Cyber Interface to gain unauthorised access to sensitive biological data or to manipulate critical systems, with potentially life-threatening consequences.
Zafar et al. [footnote 121] describe several specific attacks targeting this interface:
-
Eavesdropping: Intercepting sensitive patient data transmitted via the interface, which may include physiological parameters, device identifiers, and location details. Camara et al [footnote 122] discusses that if these channels are not encrypted, that private information could be disclosed and even if they are encrypted, detecting their radio channel in the 401-406MHz band could reveal the presence of an implant from up to 10m away.
-
Man-in-the-Middle (MitM) Attacks: Altering or forging communications between the nano-network and external systems, potentially leading to inappropriate medical decisions
-
Device Tampering: Physically compromising or replacing the device to send fake data or disrupt its operation
-
Firmware Attacks: Exploiting the need for periodic firmware updates by injecting malicious updates to alter device functionality.
Molecular Communication and Attack Taxonomy
Molecular communication within the IoBNT paradigm leverages biochemical signalling to encode, transmit, and receive information at the nanoscale. Unlike traditional electromagnetic communication, this process relies on the interactions of molecules to propagate information through biological environments. While this approach enables seamless integration with living systems and allows for revolutionary applications such as targeted drug delivery, remote monitoring, and molecular diagnostics, it also introduces a range of unique vulnerabilities due to the inherent properties and constraints of biochemical communication and the nanoscale environment.
-
Biochemical Signal Manipulation: Molecular communication is inherently susceptible to interference due to the physical and chemical nature of the medium. For example, Zafar et al. [footnote 121] highlight that signal integrity can be compromised by attacks such as black-hole and sentry attacks, where adversaries manipulate ligand-binding processes to either repel required ligands or attract unwanted ones. Such disruptions can alter biochemical signalling and result in errant behaviour in BioFET-based interfaces
-
Resource Constraints at the Nanoscale: Nano-devices operating in IoBNT systems are highly resource-constrained due to their size. As discussed in Usman et al. [footnote 124], these devices lack the computational, energy, and storage capacity necessary for implementing robust traditional cryptographic defences. This constraint limits their ability to counter sophisticated attacks such as man-in-the-middle or replay attacks
-
Eavesdropping and Privacy Risks: Biochemical signals transmitted within the IoBNT system can be intercepted by adversaries, leading to privacy breaches. Sensitive patient data, such as physiological parameters or device identifiers, can be extracted and potentially misused. This is particularly concerning in medical applications where confidentiality is paramount. Camara et al. [footnote 122] emphasise that the open and unregulated nature of molecular communication makes it vulnerable to unauthorised monitoring
-
Man-in-the-Middle (MitM) Attacks: Adversaries can exploit the Bio-Cyber Interface to alter biochemical signals or inject falsified data into the communication chain. For instance, Zafar et al. [footnote 121] describe how tampered molecular signals could send incorrect feedback to healthcare providers, potentially leading to misdiagnoses or harmful treatments
-
Environmental Sensitivity: Biochemical signalling is heavily influenced by environmental factors such as pH, temperature, and molecular density. Adversaries could exploit this sensitivity by introducing environmental changes that degrade signal quality or disrupt communication altogether. Such disruptions could affect the reliability of IoBNT systems in critical applications, as highlighted in the security considerations for BioFET-based bio-cyber interfaces
-
Denial-of-Service (DoS) Attacks: Molecular communication systems are susceptible to DoS attacks, where an adversary overwhelms the communication channel with extraneous molecules or interferes with the biochemical pathways. This could prevent critical real-time data from reaching healthcare providers, as noted in studies of molecular nano-networks
Cryptographic Management in IoBNT
Key management remains a key challenge in nano-networks, primarily due to the unique constraints of these systems, including their nanoscale size, limited computational resources, and the dynamic nature of their environments. As Usman et al.[footnote 124] highlight, the distribution of cryptographic keys among nano-devices presents significant complexities.
To address these challenges, researchers have begun exploring innovative approaches tailored to the nanoscale environment. One promising avenue is the use of Deoxyribonucleic Acid (DNA) nanostructures for data encryption. DNA-based encryption leverages the unique molecular properties of DNA to encode and secure data. This approach not only aligns with the biocompatible nature of nano-networks but also provides a dual benefit: preserving genetic privacy in applications like DNA sequencing while establishing a foundation for bio-molecular computing.
The use of DNA encryption exemplifies how emerging technologies can overcome traditional cryptographic limitations in nano-networks. By integrating biological and computational principles, these methods offer a secure and scalable solution for key management in highly constrained environments, opening new pathways for secure communication in the IoBNT (IoBNT). However, further research is required to refine these techniques and address their practical implementation challenges.
Emerging countermeasures The novel challenges identified in IoBNT systems necessitate innovative approaches to secure molecular communication pathways and the broader ecosystem. Based on the work of Zafar et al [footnote 121]. and other referenced studies, several promising developments and countermeasures have been proposed to address vulnerabilities such as resource constraints, privacy breaches, and attacks on the Bio-Cyber Interface.
-
Machine Learning and AI for Anomaly Detection: Machine learning (ML) and artificial intelligence (AI) are at the forefront of IoBNT security enhancements. Zafar et al [footnote 121] propose the use of Particle Swarm Optimisation (PSO) algorithms to optimise Artificial Neural Networks (ANN) for detecting anomalous behaviours in Bio-Cyber Interface communications. Their approach demonstrates high accuracy in identifying abnormal activities in molecular communication systems, enabling real-time threat detection and response
-
DNA-Based Cryptography: To overcome the resource constraints of nano-devices, DNA-based encryption has emerged as a promising solution. This technique leverages the unique molecular properties of DNA for secure data encoding. As highlighted by Usman et al [footnote 124], DNA-based encryption aligns with the biocompatible nature of IoBNT systems and provides dual benefits: preserving genetic privacy and laying the foundation for bio-molecular computing
5.9.4 Conclusion of Biomedical Computers and IoT for convergence
The convergence of biomedical computing and IoT through the IoBNT represents a transformative technological frontier in healthcare that brings with it many more cyber-safety challenges. As nanoscale devices become integral to medical applications, such as targeted drug delivery and in-body diagnostics, they blur the boundaries between technology and biology. This convergence introduces new security challenges, where cyberattacks not only compromise data but also have the potential to directly endanger human lives.
Traditional threat and risk frameworks appear to be used but adapted to address the unique characteristics of IoBNT systems. Attacks such as denial-of-service (DoS) on molecular communication systems exploit the constraints of nano-devices, including limited computational resources and the sensitivity of biochemical signalling. Similarly, vulnerabilities in the Bio-Cyber Interface, such as eavesdropping, device tampering, and man-in-the-middle attacks, necessitate innovative security measures that extend beyond conventional approaches.
These challenges require us to innovate in our approach to cyber security countermeasures. Machine learning (ML) and artificial intelligence (AI), particularly through techniques like PSO, are enabling real-time anomaly detection in molecular communication systems, enhancing the resilience of IoBNT infrastructure against sophisticated threats. PSO, as an optimisation algorithm, has proven effective in improving the accuracy of Artificial Neural Networks (ANNs), enabling the precise identification of anomalous behaviours in Bio-Cyber Interface communications. Additionally, DNA-based cryptography offers a groundbreaking approach to secure data in nanoscale environments, leveraging the molecular properties of DNA to overcome the limitations of traditional cryptographic methods. These advancements not only address technical challenges but also align with the biocompatible nature of IoBNT systems.
Research Question 1: Novel or Emerging Security Risks
-
Resource Constraints at the Nanoscale Nanoscale devices face extreme limitations in computing power, memory, and battery life, making traditional security protocols—such as robust encryption—difficult to implement. As a result, even basic defences can overwhelm device resources, leaving these systems highly susceptible to a wide range of attacks.
-
Vulnerabilities in the Bio-Cyber Interface The interface linking biochemical signals with external networks is a particularly attractive target for cyber threats. When left unsecured, it can expose sensitive data—like physiological readings or device identifiers—and allow adversaries to compromise or manipulate implanted devices, potentially leading to severe health risks or privacy breaches.
-
Molecular Communication Threats Biochemical signals, essential for nanoscale data exchange, can be disrupted by attacks like black-hole or sentry exploits that redirect or corrupt message flows. , The high sensitivity of molecular communication to environmental factors (e.g., pH and temperature) makes it vulnerable to both denial-of-service (DoS) attacks and more subtle tampering that degrades overall system performance.
-
Device Tampering and Firmware Attacks Tiny implants and sensors can be physically accessed, altered, or removed, providing adversaries with opportunities to introduce false data or completely disrupt functionality. In addition, firmware updates intended to fix bugs can become another attack vector if not properly secured, allowing malicious actors to install harmful code or override security features.
-
Novel Detection and Response Requirements Effective protection against these complex threats demands swift, real-time anomaly detection methods capable of identifying and mitigating risks before harm occurs. Machine learning and AI techniques, including those optimised by PSO, can help detect unusual device behaviours, but they also bring their own vulnerabilities if adversarial actors manage to manipulate or corrupt the underlying models.
Research Question 2: Industries most affected by the compounding cyber security risks:
- Healthcare
Research Question 3: Applications of emerging technologies most likely to be affected by technology convergence:
- Bio-nano things: An advanced extension of the Internet of Things, where tiny, biocompatible nanoscale devices sense biological signals and communicate them to external systems, faces distinct challenges. Minimal computational and energy capacity in these nano-devices constrains traditional controls such as encryption, leaving biochemical signals vulnerable to interception or manipulation through attacks like black-hole or sentry, potentially causing false readings or denial-of-service. The Bio-Cyber Interface—the critical bridge between biological signals and external networks—also becomes a prime target for eavesdropping, tampering, and firmware exploits.
5.10 Artificial Intelligence and Quantum Sensing
Quantum sensing uses the principals of quantum mechanics to enable high precision measurements, enabling the measurement of very small changes in gravitational or electrical fields. Potential uses for quantum sensing include applications such as accurate dead reckoning or more capable ground penetrating radar.
The search for Artificial Intelligence converging with Quantum Sensing resulted in very limited results, with Bonab et al. [footnote 125] highlighting that quantum sensors could provide high quality data to enable the training of AI. However, there was no consideration of cyber security implications of convergence found in our search process.
5.11 Swarm and Neurotechnology
Following a comprehensive search of academic journals aligned with the research plan, the proposed technology pairing of "neurotechnology" and "swarm" failed to produce relevant results. The method used to identify widely discussed pairings have unintentionally generated false positives, where on closer review the results did not focus on the intersection with cyber security. Despite a thorough exploration, including adjustments such as excluding terms like "converged," "convergence," and "synergy" from the criteria, no publications met the threshold for inclusion. Therefore, we conclude that there are currently no significant cyber security considerations between these domains at this time.
6. Exploring technology synergies beyond academic publications
This Section delves into insights drawn from grey literature, moving beyond traditional academic publications to include reports, white papers, and policy briefs from reputable organisations including the the World Economic Forum, OECD, Turing Institute, Rand, and MIT Technology Review, listed in Appendix 9. These sources provide practical, real-world perspectives on the technology synergies mentioned in the report herein, and their impacts on cyber security, offering a comprehensive view of emerging challenges and solutions in the technological landscape.
Our searches of these sources did not lead to results on every pairing considered in our review, this section reviews the viewpoints where information was found.
Brain-Computer Interfaces and Robotics
Georgetown University’s Centre for Security and Emerging Technology (CSET) conducted a bibliographic review of China’s Non-Therapeutic Brain-Computer interface work [footnote 126]. The report notes that China’s research in the area is world class - comparable to the United States and the United Kingdom. The report notes that Chinese institutions have a focus on adversarial attacks on Brain-Computer Interfaces - highlighting a need for investment into defences against these attacks, and that China seeks to develop more sophisticated UAV control algorithms, making use of BCI interfaces.
The report highlights the dual-use nature of the research - both military and civilian use cases exist, suggesting that China is likely to use brain-computer interfaces and robotics in a military context. The European Commission’s JRC Science for Policy Report [footnote 127] reinforces the dual use viewpoint of BCIs with robotics, noting that the US’s DARPA has consistently funded research into the technology.
RAND Corporation [footnote 128] acknowledge the potential military applications of BCIs, including human-machine collaboration. They highlight the the IOB (Internet of Bodies) creates new vulnerabilities by expanding the attack surface, and opens the potential for loss of sensitive personal details, or manipulation of devices, both of which could have dire consequences in a military or civilian context. They also note that regulation of IOB (and hence BCI) is fragmented, leading to a lack of robust cyber security measures in the area.
RAND briefly considers the impact on the human in [footnote 129], and how they trust the machine - considering that a user might feel an extension of being into the machine, which may impact interpersonal relationships, noting that these ethical and trust considerations may be important to understand how BCI controlled robotics can integrate into a military context.
Finally, the World Economic Forum briefly considers policy considerations of brain-computer interfaces in [footnote 130]. There is concern that BCIs would be used in autonomous lethal weapons systems, may amplify existing inequities, and could lead to enfeeblement of their uses. The report recommends privacy approaches that consider cognitive freedom, highlights the need for internationally harmonised ethical standards, and moral examination of neural systems as part of research.
AI and IOT
As mentioned in the previous Sections, the synergy between AI and IoT has transformed cyber security by enabling advanced threat detection and predictive analytics, but it also amplifies data privacy risks and increases the attack surface. According to a report by the World Economic Forum (WEF), AI’s integration into IoT ecosystems enhances real-time monitoring and decision-making, which is crucial for industries like healthcare and smart cities. However, the interconnected nature of these systems makes them susceptible to cyber threats, such as adversarial AI attacks and unauthorised data access [footnote 131]. Similarly, a white paper by PwC [footnote 132] highlights the role of AI in anomaly detection and predictive maintenance within IoT networks, particularly in industrial applications, but notes vulnerabilities in IoT device security that could lead to cascading failures. Additionally, MIT Technology Review emphasises how AI and IoT improve resilience in energy systems but warns of adversarial attacks targeting IoT devices, which could compromise data integrity [footnote 133].
Edge Computing and IOT
Finally, regarding the integration of Edge Computing and IoT, The World Economic Forum emphasises that edge computing minimises the reliance on centralised servers, thereby reducing risks of data interception during transmission. However, it also expands the attack surface due to the decentralised nature of edge nodes [footnote 134]. Furthermore, the European Commission highlights its investments in edge-IoT technologies to strengthen cyber security but warns of compliance challenges in regulated industries [^135]. Moreover, a white paper by Panduit emphasises that while edge computing enables faster data generation and processing by positioning resources closer to data sources, it also expands the attack surface for potential cyber threats. The paper highlights the necessity for robust security measures to safeguard these distributed networks.
Biotechnology and IOT
No literature explicitly explores the cyber security implications of the convergence of biotechnology and the Internet of Things (IoT). Current discussions within the cyber security domain provide limited recognition of biotechnology and IoT as emerging technologies, focusing more on their transformative potential than their direct security risks. The importance of increased investment and sustained funding in groundbreaking technologies—particularly nanoscale electronics, biological computing, and optical computing—is discussed at a superficial level. Some sources highlight the disruptive potential of advances in computing technologies, such as quantum, optical, and biological computing, to drive transformational change. Long-term innovation relies on research funding across the entire development lifecycle, from foundational scientific discovery to industrial standardisation, often supported by public-private partnerships such as the Fraunhofer Institutes and the ITRI Institute. Furthermore, the need for people-centred, data-driven strategies—such as those seen in Norway’s health sector—demonstrates the importance of leveraging biotechnological advancements for societal benefit while simultaneously addressing associated ethical and legal challenges.
7. Conclusion
In this section, we return to the research questions as set out in section 4, analysing the outputs from our literature reviews.
7.1 Which groups or pairings of emerging technologies are likely to create novel or compounding cyber security risks?
Our review explored the convergence of emerging technologies and the resulting novel or compounding cyber security risks across a range of technologies. A key theme is that new security threats emerge from converging pairs of technologies where a convergence significantly changes the attack surface of another technology, or where a technology introduces a new class of vulnerabilities. In certain cases, the convergence of specific technologies reveals novel, industry specific risks that emerge from their close alignment with a particular sector - for example in personalised medicine and healthcare.
If realised, many of these risks can have severe real-world implications. The convergence of technologies, and the continued embedding into everyday life as essential public services, increases the potential for cyber security threats to translate into real-world hazards. As technology systems become more interconnected and embedded in critical functions, the potential for malicious manipulation - such as data corruption, device tampering, or disruption of automated processes - introduces new vulnerabilities where cyber security incidents can directly affect physical safety.
A key trend observed in our literature review was the convergence of artificial intelligence (AI) with a wide range of technologies. This convergence brings novel classes of vulnerabilities, such as adversarial attacks, which exploit weaknesses in AI algorithms to produce incorrect outputs. These attacks can lead to safety risks - in the case of brain-computer interfaces, potentially leading to users being put in dangerous situations, or incorrect treatment plans in personalised medicine use cases leading to poor outcomes for patients.
New classes of vulnerabilities were also seen to impact privacy. With brain-computer interfaces, gathering data directly from the human brain creates new forms of attack to compromise privacy. In the case of biological computing, devices that are embedded into human tissue may provide attackers with new ways to retrieve private information, through routes enabled by the convergence of technologies.
The physical expansion of technological infrastructure, seen in edge computing, IoT, and satellite technologies, introduces new challenges. For quantum communications, particularly when paired with satellite technologies the attack surface changes, increasing the risk of denial-of-service attacks compared to terrestrial-based quantum communications systems. This demonstrates how the physical deployment of technologies can introduce distinct security concerns. For IoT systems, or edge computing, we saw emerging vulnerabilities from the increased physical attack surface, and the increased volumes of private data that might be available to access, particularly when combined with medical applications.
The increased physical footprint of these systems necessitates improved physical security measures, as evidenced in the literature on quantum communication and IoT pairings.
Data integrity issues were a recurring theme across the reviewed technologies. As technologies such as IoT, BCIs, digital twins, and personalised medicine become more integrated into daily life, compromised data can lead to far-reaching real-world consequences, highlighting the critical need for robust data validation and protection mechanisms.
In summary, the convergence of emerging technologies reshapes the cyber security landscape by introducing novel vulnerabilities and expanding attack surfaces. The prevalence of AI as a paradigm changing technology brings new classes of vulnerability that require innovative controls to defend against, whilst changes in the attack surface from increased volumes of data and physical footprint brings new risk. Addressing these challenges requires a proactive approach that combines interdisciplinary research, innovative security solutions, and global collaboration to mitigate the risks posed by these rapidly evolving technological ecosystems.
7.2 Which industries will be affected by the compounding cyber security risks stemming from convergence of emerging technologies?
The convergence of emerging technologies introduces unprecedented opportunities for industries, but it also compounds cyber security risks in sectors that rely on interconnected systems, sensitive data, and real-time operations. Industries such as healthcare, defence and aviation, energy and utilities, transportation, and telecommunications are at the forefront of this risk from the technological convergence, making them especially vulnerable to advanced cyber threats.
Healthcare & Biotechnology
The integration of AI and IoT in healthcare drives advancements like personalised medicine, remote monitoring, and predictive diagnostics However, these systems rely on vast amounts of sensitive patient data and interconnected devices, creating significant cyber security risks including:
-
Data Breaches: Unauthorised access to medical records can lead to identity theft and privacy violations. As BCI interfaces interpret brainwaves, there is a risk of private information being leaked in case of a cyber security attack. Research has shown that visual stimuli, shown to a user, can increase this risk. There is a need to implement good security on the device to prevent attackers from accessing raw brain signals.
-
Device Manipulation: IoT-enabled medical devices, such as infusion pumps or wearable sensors, are susceptible to tampering, potentially endangering patient lives.
-
Adversarial AI Attacks: Malicious actors can exploit AI algorithms to cause diagnostic errors or manipulate treatment plans. Where brain-computer interfaces are used for control of assistive devices, there is a risk that adversarial attacks against the AI used to interpret brain signals could lead to users being put into dangerous situations, or devices not functioning.
-
Digital Twin Exploitation: The use of digital twins for simulating patient conditions or treatment plans introduces risks of unauthorised access or data tampering, compromising the accuracy of these systems.
Defence
The convergence of Edge Computing and IoT and Digital Twins and AI in defence systems significantly enhances real-time operations, but it also magnifies cyber security risks. The reliance on distributed architectures and interconnected systems creates new vulnerabilities that adversaries can exploit, including:
-
Digital Twin and AI Exploitation: military simulations and aviation systems using digital twins and AI face risks such as data exfiltration and system manipulation, threatening the integrity of strategic planning and execution. As seen in the Brain-Computer Interfaces and Robotics sections, attacks on the AI systems that will interpret brainwaves for robotics control leads to risk of unintended actions from equipment controlled by brainwaves.
-
Mission Planning Compromise: Advanced simulations for mission planning relying on edge-IoT systems are particularly vulnerable to cyberattacks if security measures are not embedded during design, leading to flawed operations. With BCI interfaces interpreting brainwaves, there is a risk of private information being leaked in case of a cyber security attack. In the military cases, if interpretable, this could include sensitive information about military operations.
-
Edge and IoT Vulnerabilities: Distributed edge devices and IoT sensors i.e. military-grade drones are highly susceptible to unauthorised access, tampering, and data breaches, potentially compromising mission-critical information and operations.
-
Ethics and Human Factors: Grey literature detailed concerns around the ethics and human factors of brain-computer interfaces in a military setting, including understanding how brain-controlled devices integrate within a military setting, and the risks of loss of cognitive freedom for users.
Transport
The transportation sector is undergoing a technological transformation driven by the convergence of AI, IoT, Edge Computing, and Digital Twins, enabling advancements such as autonomous vehicles, smart traffic management, and real-time logistics. However, this convergence also introduces significant cyber security risks:
-
Data Breaches: IoT-enabled devices, such as connected vehicle sensors and smart traffic systems, are vulnerable to breaches, exposing sensitive data.
-
AI Manipulation: Autonomous vehicles rely on AI for navigation and decision-making. Adversarial attacks, such as manipulating visual data from cameras or LIDAR, can cause vehicles to misinterpret their surroundings, leading to accidents or unsafe decisions.
-
Digital Twin Exploitation: Digital Twins used in predictive maintenance or transportation planning can be manipulated to provide false data, impacting system reliability and operational decisions.
-
Privacy Risks: Connected vehicles and transport systems collect user data, including travel patterns and behavioural information, which can be exploited if unauthorised access occurs.
-
Service Disruptions: Edge devices managing traffic signals or vehicle-to-infrastructure communication are susceptible to Denial-of-Service (DoS) attacks, disrupting traffic flow and safety-critical operations.
Telecommunications
Emerging technologies, including AI, IoT, and applications such as Connected and Autonomous Vehicles or Smart Cities mean an increasing need for fast, widespread network connections. We found that this sector will face the following cyber security risks due to emerging technology convergences:
-
Denial-of-Service Attacks: While quantum communications have the potential to enhance privacy and security in next-generation (6G) networks, denial-of-service remains a risk if an attacker is attempting to eavesdrop on communications. Convergence with LEO satellites changes the likelihood and impact of this risk being realised due to the physical nature of the communications.
-
Side channel attacks: Where quantum communications are used, there is an increased risk of side channel attacks due to the complexity of quantum operations. Depending on how these materialise, additional physical security may be required for endpoints to defend against attacks.
-
Physical Security: The need for trusted nodes in quantum communications increases the need for improved physical security to ensure the quantum communications remain secure.
Utilities and Energy:
Connected technologies have the potential to make the transition to green energy easier, with technologies such as digital twins and IoT having the potential to offer big increases in efficiency. However, our review identified risks associated to this sector:
-
Smart grids and energy management systems incorporating Digital Twins and IoT face data integrity risks and potential physical disruption.
-
Cyber-Twins and AI for predictive maintenance could be vulnerable to data manipulation attacks impacting power delivery systems.
Manufacturing and Industry 4.0:
Manufacturing and Industry 4.0 leverage advanced technologies like IoT, AI, and automation to revolutionise production processes, but face significant threats from the convergence of emerging technologies, including threats from intellectual property theft, and systemic threats from a lack of cyber security frameworks.
-
AI and 3D printing in manufacturing raise concerns about intellectual property theft, process sabotage, and compromised digital design files.
-
Limited exploration of cyber security frameworks in Industry 4.0 applications introduces potential systemic vulnerabilities.
Table 3 illustrates the cyber security risks across the different industries, emphasising vulnerabilities introduced by the various technological synergies. It provides an overview of how these integrations expand attack surfaces and create new security challenges in sectors like healthcare, transportation, energy, and more.
| Sector | Key Threats |
|---|---|
| Utilities & Energy | Data integrity risks, predictive maintenance manipulation |
| Telecommunications | Denial-of-service attacks, side-channel attacks, physical security risks |
| Manufacturing & Industry 4.0 | Intellectual property theft, process sabotage, systemic vulnerabilities |
| Healthcare | Data breaches, adversarial AI attacks, device manipulation, digital twin exploitation |
| Defence & Aviation | Digital twin and AI exploitation, mission planning compromise, edge and IoT vulnerabilities, ethics and human factors risks |
| Transportation | Data breaches, AI manipulation, digital twin exploitation, privacy risks, service disruptions |
Table 3: Prominent Cyber security risks across industries
7.3 Which applications of emerging technologies are most likely to be affected by technology convergence?
In the Sections above, we examined the impact of technology convergence by reviewing key literature and presenting in-depth case studies. These analyses focused on the intersections of emerging technologies such as Quantum, AI, IoT, Blockchain, Edge Computing, and others, exploring how these synergies reshape industries and address complex challenges. A central theme throughout this exploration has been the implications for cyber security — a critical area where these technological convergences both enhance defences and introduce new vulnerabilities. By analysing theoretical insights and real-world applications, we provide an understanding of the cyber security dynamics within specific industries and use cases, identifying the applications most significantly influenced by this convergence. Subsequently, this section synthesises these findings to identify the applications most significantly influenced by the convergence of emerging technologies.
The convergence of emerging technologies including AI, IoT, Blockchain, and Edge/Fog Computing has shown to profoundly transform a range of industries, as discussed in the aforementioned Sections. More specifically, the literature has demonstrated that these integrations address critical challenges, improve operational efficiency, and improve cyber security. However, their application varies depending on the industry, technological compatibility, and cyber security requirements.
One area significantly impacted is healthcare, particularly through the convergence of AI and IoT. The integration of IoT-enabled medical devices with AI enhances real-time monitoring, personalised diagnostics, and predictive analytics. For example, systems like NVIDIA Clara and Medtronic’s connected insulin pumps use AI algorithms to process data from IoT devices for anomaly detection and predictive maintenance, or brain-computer interfaces allowing better control of prosthetic devices. However, the synergy introduces vulnerabilities, such as an expanded attack surface and risks of adversarial attacks on AI systems. As a result, healthcare applications must navigate these challenges while benefiting from increased operational efficiency and improved patient care.
Smart cities represent another domain where technology convergence is likely to have a transformative impact. The combination of IoT and Edge/Fog Computing enables real-time data processing for traffic management, public safety, and energy optimisation. By analysing data locally, edge computing reduces latency and minimises exposure to cyber threats associated with centralised systems. Nevertheless, the heterogeneity of devices and the expanded attack surface in smart city networks highlight the need for robust interoperability and cyber security measures.
The supply chain and logistics industry is also undergoing a revolution through the integration of AI and Blockchain. Platforms like IBM Food Trust leverage blockchain’s tamper-proof ledger to ensure transparency in global supply chains, while AI predicts disruptions and automates processes. This convergence enhances traceability and fraud prevention but introduces challenges, such as resource demands and ensuring compliance with privacy regulations like GDPR.
Moreover, in the finance sector, Blockchain combined with AI and Cryptography is driving innovations in secure transactions, fraud detection, and decentralised finance. Blockchain ensures data integrity and auditability, while AI algorithms provide real-time threat detection and anomaly analysis. However, the high computational intensity and algorithmic biases pose challenges, necessitating scalable and privacy-preserving solutions.
Many of the applications discussed require connectivity, and 6G wireless networks are likely to be needed to meet their needs. SAGIN networks, making use of the benefits of Space, Air, and Ground telecommunications could provide ubiquitous networking to provide that connectivity, but come with wide security challenges - including potential denial-of-service attacks where quantum communications are implemented - and will require international agreement on standards as a technology that could span international borders.
Finally, vehicular networks and autonomous systems exemplify the convergence of AI, IoT, and Edge Computing. These technologies enable real-time decision-making for autonomous vehicles and intelligent transportation systems. The localised processing capabilities of edge computing reduce latency, while AI enhances predictive capabilities. However, vulnerabilities in IoT sensors and edge devices can compromise safety, necessitating secure communication protocols and adaptive intrusion detection systems.
Table 4 below highlights the potential applications most impacted by specific technological pairings, illustrating how convergences like AI + IoT or Blockchain + IoT align with critical sectors such as healthcare, transportation, and energy. This underscores the varying degrees of influence these synergies have across different domains, shaping their operational and cyber security landscapes.
| Technologies | Applications |
|---|---|
| AI + Personalised Medicine | Healthcare |
| Blockchain + IoT | Supply Chain, Healthcare |
| Biological Computing + IoT | Healthcare |
| Digital Twins + AI, Manufacturing and Industry 4.0 | Transport, Energy, Aerospace & Defence, Telecommunications, Smart Cities |
| AI + IoT | Healthcare, Smart Cities |
| IoT + Edge | Connected Vehicles, Smart Cities |
| LEO + Quantum Communications | 6G/Next Generation Networking (SAGIN networks: Space Air Ground Integrated Networks) |
| Blockchain + AI | Finance, Supply Chain |
| Brain-Computer Interfaces + AI + Robotics | Healthcare (Assistive Care), Military |
Table 4 : An overview of where the technological synergies are expected to have the most pronounced influence across various industries.
7.4 Observations and Recommendations
This report presents a systemic literature review, focussed on answering the research questions discussed above. It’s focus has been on pairs of emerging technologies, and the cyber security implications of their convergence. Our analysis found that the quantity of research focussed on convergent pairs varied a lot between dependant pairs, with some pairings - which our initial searches deemed likely to have coverage, and where we believed there would be significant security implications stemming from convergence - having little or no research covering the security of convergence.
Table 4, summarises the applications that may be more affected by the respective technological pairings. Our pairings, and the groupings that they led to, demonstrate that Artificial Intelligence is likely to have an outsized impact on technology convergence in emerging technologies. Figure 5 shows the technologies that have been identified as paring with AI. This outsized influence is not unexpected, as Artificial Intelligence is widely being seen as a paradigm shifting technology. However, Artificial Intelligence brings new classes of vulnerabilities to the technologies it is converging with, often not considered as part of standard security controls.
Our literature review found little research specifically focussing on the impacts of technology convergence on cyber security - indeed, we needed to drop the term "convergence" from our searches to discover relevant research, suggesting a lack of research directly studying the subject. As noted in Section 4.5, this could be due to the novelty of the converging pairings, and the changing and evolving nature of cyber security and emerging technologies. For some pairings, we found very minimal literature discussing the security implications of convergence - despite our process being designed to give a non-biased view of research - funding and interest in technology pairings will influence results, potentially giving AI outsized representation.
In answering our research questions, we have begun to discuss when technology convergence will bring novel or compounding risks, and which industries this is likely to affect - further research in this area could lead to better understanding of the potential converging security risks.
Whilst the research methodology being focussed on cyber security impact means that we are unable, directly from the literature review, to assess the broader impact or likelihood of specific converging pairs or groupings, our assessment in Section 7.2 provides a view of which industries are likely to be affected by each of our pairings. We expect that differences in industries, the appetite for innovation in an industry, and the willingness to adopt lower TRL (Technology Readiness Level) technologies could provide insight to where broader impact may be seen From our identified industries, we expect that defence and healthcare are likely to be more innovative in these areas. However, research with a broader scope, considering impacts outside of cyber security, could provide a more principled view on which pairing are most likely to have an impact.
The diagram below below summarises the interconnected cyber security risks and advancements across various technology pairings, such as AI + IoT, Blockchain + Cryptography, and IoT + Quantum. It highlights how specific synergies, like AI and IoT, contribute to enhanced cyber security while also introducing challenges such as data privacy concerns, emphasising the dual-edged nature of technological convergence.
Figure 9: This Sankey diagram illustrates the cyber security risks emerging from various technology synergies, showing how specific technological pairings contribute to distinct security challenges. The different colours shown on the left next to each pairing are for differentiation and do not carry categorical significance. The width of the connections represents the equal weighting given to each pairing. Lastly, the red lines indicate where the pairing introduces cyber security risks, while the green highlights positive cyber security effects, such as enhanced threat detection or improved data security.
Appendix
Grey Literature Sources
| Organisation | Organisation |
|---|---|
| World Economic Forum | OECD |
| National Institute of Standards and Technology (NIST) | RAND Corporation |
| Brookings Institution | UK Government Office for Science |
| Accenture Research | European Commission Reports |
| PwC Research | MIT Technology Review |
| Centre for International Governance Innovation (CIGI) | Chatham House |
| The Alan Turing Institute | World Bank |
| Australian Strategic Policy Institute (ASPI) | CETaS |
| The Alan Turing Institute | Atlantic Council Cyber Statecraft Initiative |
| CSET | RUSI |
| Chatham House | ASPI |
| IISS |
Authors and institutions
This report was written by:
Maxwell Ash
Inceptiv Ltd.
max@inceptiv.co.uk
Emyr Thomas
Enovity Ltd.
emyr@enovity.co.uk
Eirini Anthi
Cardiff University
anthies@cardiff.ac.uk
References
-
Technology convergence and cyber relevance. Department of Science, Innovation,; Technology; 2024. ↩
-
Rotolo D, Hicks D, Martin B. What is an emerging technology? Research Policy. 2015 Dec;44:1827–43. doi: 10.1016/j.respol.2015.06.006 ↩ ↩2
-
UKRI. Insights report: Innovate UK’s 50 emerging technologies. UKRI Publication. 2023; Available from: https://www.ukri.org/publications/insights-report-innovate-uks-50-emerging-technologies/ ↩
-
Nato - science and technology trends - 2023-2043. Available from: https://www.nato.int/nato_static_fl2014/assets/pdf/2023/3/pdf/stt23-vol1.pdf ↩
-
McKinsey technology trends outlook 2024. Available from: https://www.mckinsey.com/capabilities/mckinsey-digital/our-insights/the-top-trends-in-tech ↩
-
UK science and technology framework. ↩
-
Wang Y, Su Z, Guo S, Dai M, Luan TH, Liu Y. A survey on digital twins: Architecture, enabling technologies, security and privacy, and future prospects. IEEE Internet of Things Journal. 2023 Sep;10:14965–87. doi: 10.1109/JIOT.2023.3263909 ↩ ↩2 ↩3 ↩4 ↩5 ↩6
-
Menon D, Anand B, Chowdhary CL. Digital twin: Exploring the intersection of virtual and physical worlds. IEEE Access. 2023;11:75152–72. doi: 10.1109/ACCESS.2023.3294985 ↩
-
Koroniotis N, Moustafa N, Schiliro F, Gauravaram P, Janicke H. The SAir-IIoT cyber testbed as a service: A novel cybertwins architecture in IIoT-based smart airports. IEEE Transactions on Intelligent Transportation Systems. 2023 Feb;24:2368–81. doi: 10.1109/TITS.2021.3106378 ↩ ↩2 ↩3 ↩4
-
Hossain MN, Rahman MM, Ramasamy D. Artificial intelligence-driven vehicle fault diagnosis to revolutionize automotive maintenance: A review. Vol. 141, CMES - Computer Modeling in Engineering and Sciences. Tech Science Press; 2024. p. 951–96. doi: 10.32604/cmes.2024.056022 ↩
-
Hossain MS, Islam MS, Rahman MA. A cyber range framework for emulating secure and private IT/OT consumer service verticals toward 6G. IEEE Transactions on Consumer Electronics. 2024;70:4709–16. doi: 10.1109/TCE.2024.3387055 ↩ ↩2 ↩3
-
Xu M, Niyato D, Xiong Z, Kang J, Cao X, Shen XS, et al. Quantum-secured space-air-ground integrated networks: Concept, framework, and case study. 2022 Apr; ↩ ↩2 ↩3 ↩4 ↩5
-
Xu H, Wu J, Pan Q, Guan X, Guizani M. A survey on digital twin for industrial internet of things: Applications, technologies and tools. IEEE Communications Surveys & Tutorials. 2023;25(4):2569–98. doi: 10.1109/COMST.2023.3297395 ↩
-
Yigit Y, Panitsas I, Maglaras L, Tassiulas L, Canberk B. Cyber-twin: Digital twin-boosted autonomous attack detection for vehicular ad-hoc networks. In: IEEE international conference on communications. Institute of Electrical; Electronics Engineers Inc.; 2024. p. 2167–72. doi: 10.1109/ICC51166.2024.10622784 ↩ ↩2 ↩3
-
Poisoning attacks in federated edge learning for digital twin 6G-enabled IoTs: An anticipatory study. 2023 Mar; Available from: http://arxiv.org/abs/2303.11745 ↩
-
Abdulrahman S, Otoum S, Bouachir O, Mourad A. Management of digital twin-driven IoT using federated learning. IEEE Journal on Selected Areas in Communications. 2023 Nov;41:3636–49. doi: 10.1109/JSAC.2023.3310102 ↩
-
Ridhawi IA, Otoum S, Aloqaily M. Decentralized zero-trust framework for digital twin-based 6G. 2023 Feb; Available from: http://arxiv.org/abs/2302.03107 ↩
-
Jagannath J, Ramezanpour K, Jagannath A. Digital twin virtualization with machine learning for IoT and beyond 5G networks: Research directions for security and optimal control. In: WiseML 2022 - proceedings of the 2022 ACM workshop on wireless security and machine learning. Association for Computing Machinery, Inc; 2022. p. 81–6. doi: 10.1145/3522783.3529519 ↩ ↩2
-
Zeb S, Mahmood A, Khowaja SA, Dev K, Hassan SA, Gidlund M, et al. Towards defining industry 5.0 vision with intelligent and softwarized wireless network architectures and services: A survey. Vol. 223, Journal of Network and Computer Applications. Academic Press; 2024. doi: 10.1016/j.jnca.2023.103796 ↩
-
Suhail S, Jurdak R. Towards trusted and intelligent cyber-physical systems: A security-by-design approach. 2021 May; Available from: http://arxiv.org/abs/2105.08886 ↩ ↩2
-
Xue B, Wu L, Liu A, Zhang X, Chen X, Chen X. Detecting the universal adversarial perturbations on high-density sEMG signals. Computers in Biology and Medicine. 2022 Oct;149:105978. doi: 10.1016/j.compbiomed.2022.105978 ↩ ↩2 ↩3 ↩4
-
Danilczyk W, Sun Y, He H. ANGEL: An intelligent digital twin framework for microgrid security. In: 2019 north american power symposium (NAPS). 2019. p. 1–6. doi: 10.1109/NAPS46351.2019.9000371 ↩
-
Saad A, Faddel S, Youssef T, Mohammed OA. On the implementation of IoT-based digital twin for networked microgrids resiliency against cyber attacks. IEEE Transactions on Smart Grid. 2020;11(6):5138–50. doi: 10.1109/TSG.2020.3000958 ↩
-
Lu Y, Huang X, Zhang K, Maharjan S, Zhang Y. Communication-efficient federated learning and permissioned blockchain for digital twin edge networks. IEEE Internet of Things Journal. 2021;8(4):2276–88. doi: 10.1109/JIOT.2020.3015772 ↩
-
Maillet-Contoz L, Michel E, Nava MD, Brun P-E, Leprêtre K, Massot G. End-to-end security validation of IoT systems based on digital twins of end-devices. In: 2020 global internet of things summit (GIoTS). 2020. p. 1–6. doi: 10.1109/GIOTS49054.2020.9119570 ↩
-
Zhang K, Zhou H-Y, Baptista-Hon DT, Gao Y, Liu X, Oermann E, et al. Concepts and applications of digital twins in healthcare and medicine. Patterns. 2024 Aug;5:101028. doi: 10.1016/j.patter.2024.101028 ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7 ↩8 ↩9
-
Hasan HR, Salah K, Jayaraman R, Omar M, Yaqoob I, Pesic S, et al. A blockchain-based approach for the creation of digital twins. IEEE Access. 2020;8:34113–26. doi: 10.1109/ACCESS.2020.2974810 ↩
-
Dietz M, Putz B, Pernul G. A distributed ledger approach to digital twin secure data sharing. In: Data and applications security and privacy XXXIII: 33rd annual IFIP WG 113 conference, DBSec 2019, charleston, SC, USA, july 15–17, 2019, proceedings 33. Springer; 2019. p. 281–300. ↩
-
Toderean L, Cioara T, Anghel I, Sarmas E, Michalakopoulos V, Marinakis V. Demand response optimization for smart grid integrated buildings: Review of technology enablers landscape and innovation challenges. Vol. 326, Energy and Buildings. Elsevier Ltd; 2025. doi: 10.1016/j.enbuild.2024.115067 ↩
-
Suvarna M, Yap KS, Yang W, Li J, Ng YT, Wang X. Cyber–physical production systems for data-driven, decentralized, and secure manufacturing—a perspective. Engineering. 2021 Sep;7:1212–23. doi: 10.1016/j.eng.2021.04.021 ↩
-
Rame R, Purwanto P, Sudarno S. Industry 5.0 and sustainability: An overview of emerging trends and challenges for a green future. Vol. 3, Innovation and Green Development. Elsevier B.V.; 2024. doi: 10.1016/j.igd.2024.100173 ↩
-
Soori M, Dastres R, Arezoo B. AI-powered blockchain technology in industry 4.0, a review. Journal of Economy and Technology. 2023 Nov;1:222–41. doi: 10.1016/j.ject.2024.01.001 ↩
-
Jin L, Zhai X, Wang K, Zhang K, Wu D, Nazir A, et al. Big data, machine learning, and digital twin assisted additive manufacturing: A review. Materials and Design. 2024 Aug;244. doi: 10.1016/j.matdes.2024.113086 ↩
-
Jiang Y, Su S, Zhao S, Zhong RY, Qiu W, Skibniewski MJ, et al. Digital twin-enabled synchronized construction management: A roadmap from construction 4.0 towards future prospect. Vol. 19, Developments in the Built Environment. Elsevier Ltd; 2024. doi: 10.1016/j.dibe.2024.100512 ↩
-
Dez AL. Cyber data sanitization: A cyber revival at the heart of the next data battle. The Cyber Defense Review. 2024;9(2):pp. 17–26. [accessed 11 Jan 2025] Available from: https://www.jstor.org/stable/48784773 ↩
-
Sarker IH, Janicke H, Maglaras L, Camtepe S. Data-driven intelligence can revolutionize today’s cyber security world: A position paper. 2023 Aug; Available from: http://arxiv.org/abs/2308.05126 ↩
-
Feng H, Chen D, Lv H, Lv Z. Game theory in network security for digital twins in industry. Digital Communications and Networks. 2024 Aug;10:1068–78. doi: 10.1016/j.dcan.2023.01.004 ↩
-
Al-Mhiqani MN, Alsboui T, Al-Shehari T, Abdulkareem K hameed, Ahmad R, Mohammed MA. Insider threat detection in cyber-physical systems: A systematic literature review. Computers and Electrical Engineering. 2024;119:109489. ↩
-
Maleh Y, Baddi Y, Alazab M, Tawalbeh L, Romdhani I. Artificial intelligence and blockchain for future cyber security applications. Vol. 90. Springer Nature; 2021. ↩
-
Bhushan B, Sangaiah AK, Nguyen TN. AI models for blockchain-based intelligent networks in IoT systems. ↩
-
Kaushik K. Next-generation cyber security: AI, ML, and blockchain. Springer Nature; 2024. ↩ ↩2 ↩3
-
Bhumichai D, Smiliotopoulos C, Benton R, Kambourakis G, Damopoulos D. The convergence of artificial intelligence and blockchain: The state of play and the road ahead. Information. 2024;15(5):268. ↩ ↩2 ↩3 ↩4
-
Zhang Z, Song X, Liu L, Yin J, Wang Y, Lan D. Recent advances in blockchain and artificial intelligence integration: Feasibility analysis, research issues, applications, challenges, and future work. Security and Communication Networks. 2021;2021(1):9991535. ↩ ↩2 ↩3
-
Alzoubi MM. Investigating the synergy of blockchain and AI: Enhancing security, efficiency, and transparency. Journal of Cyber Security Technology. 2024;1–29. ↩ ↩2 ↩3 ↩4
-
Alharbi S, Attiah A, Alghazzawi D. Integrating blockchain with artificial intelligence to secure IoT networks: Future trends. Sustainability. 2022;14(23):16002. ↩ ↩2 ↩3
-
Zuo Y. Exploring the synergy: AI enhancing blockchain, blockchain empowering AI, and their convergence across IoT applications and beyond. IEEE Internet of Things Journal. 2024; ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7
-
Kuznetsov O, Sernani P, Romeo L, Frontoni E, Mancini A. On the integration of artificial intelligence and blockchain technology: A perspective about security. IEEE Access. 2024;12:3881–97. ↩ ↩2 ↩3 ↩4 ↩5
-
Singh P, Elmi Z, Lau Y, Borowska-Stefańska M, Wiśniewski S, Dulebenets MA. Blockchain and AI technology convergence: Applications in transportation systems. Vehicular Communications. 2022;38:100521. ↩ ↩2
-
Li DCY. The synergistic potential of AI and blockchain for organizations. AI & SOCIETY. 2024;1–2. ↩ ↩2
-
Ullah Z, Waheed A, Mohmand MI, Basar S, Zareei M, Granda F. AICyber-chain: Combining AI and blockchain for improved cyber security. IEEE Access. 2024; ↩ ↩2
-
Bellagarda JS, Abu-Mahfouz AM. An updated survey on the convergence of distributed ledger technology and artificial intelligence: Current state, major challenges and future direction. IEEE Access. 2022;10:50774–93. ↩ ↩2 ↩3
-
Jain V, Chouhan S, Kate V, Nigam N, Bhalerao S. Enhancing data security and data sensitivity: Leveraging the synergy of blockchain artificial intelligence. In: 2023 IEEE international conference on ICT in business industry & government (ICTBIG). IEEE; 2023. p. 1–8. ↩ ↩2 ↩3 ↩4
-
Alenizi A, Mishra S, Baihan A. Enhancing secure financial transactions through the synergy of blockchain and artificial intelligence. Ain Shams Engineering Journal. 2024;15(6):102733. ↩
-
Mason J, David J. Blockchain and AI integration: Strengthening cyber security frameworks in digital business infrastructures. INTERNATIONAL BULLETIN OF LINGUISTICS AND LITERATURE (IBLL). 2024;7(3):38–47. ↩
-
Odeyemi O, Okoye CC, Ofodile OC, Adeoye OB, Addy WA, Ajayi-Nifise AO. Integrating AI with blockchain for enhanced financial services security. Finance & Accounting Research Journal. 2024;6(3):271–87. ↩
-
Noman R, Shahid M, Alam M. The synergy of blockchain and artificial intelligence in fintech: Revolutionizing the financial landscape. In: 2023 4th international conference on data analytics for business and industry (ICDABI). IEEE; 2023. p. 425–30. ↩ ↩2
-
Stanko A, Duda O, Mykytyshyn A, Totosko O, Koroliuk R. Artificial intelligence of things (AIoT): Integration challenges and security issues. 2024; ↩ ↩2
-
Yogi MK, Aiswarya D, Mundru Y. Security for AI and IoT convergence: Novel perspectives. Int J Sci Res in Network Security and Communication Vol. 2023;11:5. ↩
-
Fazel E, Nezhad MZ, Rezazadeh J, Moradi M, Ayoade J. IoT convergence with machine learning & blockchain: A review. Internet of Things. 2024;101187. ↩ ↩2 ↩3
-
Firouzi F, Farahani B, Marinšek A. The convergence and interplay of edge, fog, and cloud in the AI-driven internet of things (IoT). Information Systems. 2022;107:101840. ↩
-
Rupanetti D, Kaabouch N. Combining edge computing-assisted internet of things security with artificial intelligence: Applications, challenges, and opportunities. Applied Sciences. 2024;14(16):7104. ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7 ↩8
-
Ruiz-Villafranca S, Carrillo-Mondéjar J, Castelo Gómez JM, Roldán-Gómez J. MECInOT: A multi-access edge computing and industrial internet of things emulator for the modelling and study of cyber security threats. The Journal of Supercomputing. 2023;79(11):11895–933. ↩ ↩2 ↩3 ↩4 ↩5
-
Sarker IH, Khan AI, Abushark YB, Alsolami F. Internet of things (iot) security intelligence: A comprehensive overview, machine learning solutions and research directions. Mobile Networks and Applications. 2023;28(1):296–312. ↩ ↩2
-
Senthil G, Prabha R, Pomalar A, Jancy PL, Rinthya M. Convergence of cloud and fog computing for security enhancement. In: 2021 fifth international conference on i-SMAC (IoT in social, mobile, analytics and cloud)(i-SMAC). IEEE; 2021. p. 1–6. ↩ ↩2 ↩3 ↩4
-
Burhan M, Alam H, Arsalan A, Rehman RA, Anwar M, Faheem M, et al. A comprehensive survey on the cooperation of fog computing paradigm-based IoT applications: Layered architecture, real-time security issues, and solutions. IEEE Access. 2023; ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7 ↩8
-
Humayun M, Alsirhani A, Alserhani F, Shaheen M, Alwakid G. Transformative synergy: SSEHCET—bridging mobile edge computing and AI for enhanced eHealth security and efficiency. Journal of Cloud Computing. 2024;13(1):37. ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7 ↩8
-
Pise AA, Almuzaini KK, Ahanger TA, Farouk A, Pant K, Pareek PK, et al. Enabling artificial intelligence of things (AIoT) healthcare architectures and listing security issues. Computational Intelligence and Neuroscience. 2022;2022(1):8421434. ↩
-
Ranganayaki RS, Sreeja B, Gandhari S, Ranganath PT, Kumar S. Cyber security in smart hospitals: A investigational case study. In: 2021 10th international conference on system modeling & advancement in research trends (SMART). IEEE; 2021. p. 92–8. ↩
-
Das A. Infusion pump vulnerabilities: Common security gaps. 2022. Available from: https://unit42.paloaltonetworks.com/infusion-pump-vulnerabilities/?utm_source=chatgpt.com ↩
-
Zio by iRhythm UK - uninterrupted cardiac monitoring service. Available from: https://irhythmtech.co.uk/ ↩
-
Singh A, Sharma KK, Bajpai MK, Sarasa-Cabezuelo A. Patient centric trustworthy AI in medical analysis and disease prediction: A comprehensive survey and taxonomy. Vol. 167, Applied Soft Computing. Elsevier Ltd; 2024. doi: 10.1016/j.asoc.2024.112374 ↩ ↩2 ↩3 ↩4 ↩5
-
Chakraborty C, Bhattacharya M, Pal S, Lee SS. From machine learning to deep learning: Advances of the recent data-driven paradigm shift in medicine and healthcare. Vol. 7, Current Research in Biotechnology. Elsevier B.V.; 2024. doi: 10.1016/j.crbiot.2023.100164 ↩ ↩2 ↩3 ↩4
-
Motwani A, Shukla PK, Pawar M. Ubiquitous and smart healthcare monitoring frameworks based on machine learning: A comprehensive review. Vol. 134, Artificial Intelligence in Medicine. Elsevier B.V.; 2022. doi: 10.1016/j.artmed.2022.102431 ↩ ↩2 ↩3 ↩4 ↩5
-
Mohammadi S, Balador A, Sinaei S, Flammini F. Balancing privacy and performance in federated learning: A systematic literature review on methods and metrics. Journal of Parallel and Distributed Computing. 2024 Oct;192. doi: 10.1016/j.jpdc.2024.104918 ↩ ↩2 ↩3 ↩4 ↩5 ↩6
-
Ramesh S, Deep A, Tamayol A, Kamaraj A, Mahajan C, Madihally S. Advancing 3D bioprinting through machine learning and artificial intelligence. Vol. 38, Bioprinting. Elsevier B.V.; 2024. doi: 10.1016/j.bprint.2024.e00331 ↩ ↩2 ↩3
-
Dananjaya SAV, Chevali VS, Dear JP, Potluri P, Abeykoon C. 3D printing of biodegradable polymers and their composites – current state-of-the-art, properties, applications, and machine learning for potential future applications. Vol. 146, Progress in Materials Science. Elsevier Ltd; 2024. doi: 10.1016/j.pmatsci.2024.101336 ↩ ↩2
-
SaberiKamarposhti M, Ng KW, Chua FF, Abdullah J, Yadollahi M, Moradi M, et al. Post-quantum healthcare: A roadmap for cyber security resilience in medical data. Vol. 10, Heliyon. Elsevier Ltd; 2024. doi: 10.1016/j.heliyon.2024.e31406 ↩ ↩2 ↩3
-
Liu A, Lu S, Tao F, Anwer N. Integration of data science with product design towards data-driven design. CIRP Annals. 2024 Jan;73:509–32. doi: 10.1016/j.cirp.2024.06.003 ↩ ↩2 ↩3 ↩4
-
Kaur H, Bhatia M. Digital twins: A scientometric investigation into current progress and future directions. Expert Systems with Applications. 2025 Mar;265:125917. Available from: https://linkinghub.elsevier.com/retrieve/pii/S0957417424027842 ↩ ↩2 ↩3
-
Castro C, Leiva V, Garrido D, Huerta M, Minatogawa V. Blockchain in clinical trials: Bibliometric and network studies of applications, challenges, and future prospects based on data analytics. Vol. 255, Computer Methods and Programs in Biomedicine. Elsevier Ireland Ltd; 2024. doi: 10.1016/j.cmpb.2024.108321 ↩ ↩2
-
Abbes AC, Khanouche ME, Cheklat L, Ghedira-Guégan C, Biennier F. Online and physical internet of behaviors: A literature review. Procedia Computer Science. 2024;246:3522–31. Available from: https://linkinghub.elsevier.com/retrieve/pii/S1877050924022191 ↩ ↩2 ↩3
-
Hassani S, Dackermann U, Mousavi M, Li J. A systematic review of data fusion techniques for optimized structural health monitoring. Information Fusion. 2024 Mar;103. doi: 10.1016/j.inffus.2023.102136 ↩
-
Sadeghi M, Mahmoudi A. Synergy between blockchain technology and internet of medical things in healthcare: A way to sustainable society. Information Sciences. 2024 Mar;660. doi: 10.1016/j.ins.2023.120049 ↩ ↩2 ↩3 ↩4
-
Thapa R, Poudel S, Krukiewicz K, Kunwar A. A topical review on AI-interlinked biodomain sensors for multi-purpose applications. Vol. 227, Measurement: Journal of the International Measurement Confederation. Elsevier B.V.; 2024. doi: 10.1016/j.measurement.2024.114123 ↩
-
Cherbal S, Zier A, Hebal S, Louail L, Annane B. Security in internet of things: A review on approaches based on blockchain, machine learning, cryptography, and quantum computing. The Journal of Supercomputing. 2024;80(3):3738–816. doi: 10.1007/s11227-023-05616-2 ↩ ↩2 ↩3 ↩4
-
Singh A, Dev K, Siljak H, Joshi HD, Magarini M. Quantum internet- applications, functionalities, enabling technologies, challenges, and research directions. 2021; ↩ ↩2
-
Zaballos A, Mallorquı́ A, Navarro J. Unboxing trustworthiness through quantum internet. Computer Networks. 2023;237:110094–4. Available from: https://www.sciencedirect.com/science/article/pii/S138912862300539X ↩ ↩2 ↩3 ↩4
-
Senapati B, Rawal BS. Quantum communication with RLP quantum resistant cryptography in industrial manufacturing. Cyber Security and Applications. 2023;1:100019–9. Available from: https://www.sciencedirect.com/science/article/pii/S2772918423000073 ↩ ↩2
-
Abd El-Latif AA, Abd-El-Atty B, Mehmood I, Muhammad K, Venegas-Andraca SE, Peng J. Quantum-inspired blockchain-based cyber security: Securing smart edge utilities in IoT-based smart cities. Information Processing & Management. 2021;58(4):102549–9. Available from: https://www.sciencedirect.com/science/article/pii/S0306457321000546 ↩ ↩2 ↩3
-
Qu Z, Zhang Z, Zheng M. A quantum blockchain-enabled framework for secure private electronic medical records in internet of medical things. Information Sciences. 2022;612:942–58. doi: 10.1016/j.ins.2022.09.028 ↩ ↩2 ↩3
-
EL Azzaoui A, Sharma PK, Park JH. Blockchain-based delegated quantum cloud architecture for medical big data security. Journal of Network and Computer Applications. 2022;198:103304–4. Available from: https://www.sciencedirect.com/science/article/pii/S1084804521002952 ↩ ↩2 ↩3 ↩4 ↩5
-
De Alwis C, Kumar P, Pham Q-V, Dev K, Kalla A, Liyanage M, et al. Towards 6G: Key technological directions. ICT Express. 2023;9(4):525–33. Available from: https://www.sciencedirect.com/science/article/pii/S2405959522001485 ↩
-
Liu A, Zhang Q, Xu S, Feng H, Chen X, Liu W. QBIoT: A quantum blockchain framework for IoT with an improved proof-of-authority consensus algorithm and a public-key quantum signature. Computers, Materials and Continua. 2024;80(1):1727–51. Available from: https://www.sciencedirect.com/science/article/pii/S1546221824005228 ↩ ↩2
-
Javeed D, Saeed MS, Ahmad I, Adil M, Kumar P, Islam AKMN. Quantum-empowered federated learning and 6G wireless networks for IoT security: Concept, challenges and future directions. Future Generation Computer Systems. 2024;160:577–97. Available from: https://www.sciencedirect.com/science/article/pii/S0167739X24003236 ↩ ↩2 ↩3 ↩4
-
Kumar A, Augusto de Jesus Pacheco D, Kaushik K, Rodrigues JJPC. Futuristic view of the internet of quantum drones: Review, challenges and research agenda. Vehicular Communications. 2022;36:100487–7. Available from: https://www.sciencedirect.com/science/article/pii/S2214209622000341 ↩ ↩2 ↩3
-
Ye F, Zhou Z, Li Y. Quantum-assisted blockchain for IoT based on quantum signature. Quantum Information Processing. 2022;21(9):327–7. doi: 10.1007/s11128-022-03676-6 ↩
-
Chawla D, Mehra PS. A survey on quantum computing for internet of things security. Procedia Computer Science. 2023;218:2191–200. doi: 10.1016/j.procs.2023.01.195 ↩ ↩2
-
Cao Y, Zhao Y, Wang Q, Zhang J, Ng SX, Hanzo L. The evolution of quantum key distribution networks: On the road to the qinternet. IEEE Communications Surveys & Tutorials. 2022;24(2):839–94. doi: 10.1109/COMST.2022.3144219 ↩
-
Yue P, An J, Zhang J, Ye J, Pan G, Wang S, et al. Low earth orbit satellite security and reliability: Issues, solutions, and the road ahead. 2022 Jan; ↩ ↩2 ↩3 ↩4
-
Sabuj SR, Alam MS, Haider M, Hossain MA, Pathan A-SK. Low altitude satellite constellation for futuristic aerial-ground communications. CMES - Computer Modeling in Engineering and Sciences. 2023;136:1053–89. Available from: https://www.sciencedirect.com/science/article/pii/S1526149223002771 ↩
-
Bedington R, Arrazola JM, Ling A. Progress in satellite quantum key distribution. Nature. 2017 Jul; doi: 10.1038/s41534-017-0031-5 ↩ ↩2 ↩3
-
Khan SK, Shiwakoti N, Diro A, Molla A, Gondal I, Warren M. Space cyber security challenges, mitigation techniques, anticipated readiness, and future directions. International Journal of Critical Infrastructure Protection. 2024;47:100724. Available from: https://www.sciencedirect.com/science/article/pii/S1874548224000659 ↩ ↩2 ↩3
-
Dhar S, Khare A, Dwivedi AD, Singh R. Securing IoT devices: A novel approach using blockchain and quantum cryptography. Internet of Things. 2024 Apr;25:101019. doi: 10.1016/j.iot.2023.101019 ↩ ↩2 ↩3
-
Wang C, Rahman A. Quantum-enabled 6G wireless networks: Opportunities and challenges. IEEE Wireless Communications. 2022 Feb;29:58–69. doi: 10.1109/MWC.006.00340 ↩ ↩2 ↩3
-
Tedeschi P, Sciancalepore S, Pietro RD. Satellite-based communications security: A survey of threats, solutions, and research challenges. Computer Networks. 2022 Oct;216:109246. doi: 10.1016/j.comnet.2022.109246 ↩
-
Loon - x, the moonshot factory. Available from: https://x.company/projects/loon/ ↩
-
SpaceX. Available from: https://www.spacex.com ↩
-
Chen J, Zhang H, Xie Z. Space-air-ground integrated network (SAGIN): A survey. 2023 Jul; ↩ ↩2 ↩3
-
Kim V. Elon musk acknowledges withholding satellite service to thwart ukrainian attack. The New York Times. 2023 Feb; Available from: https://www.nytimes.com/2023/09/08/world/europe/elon-musk-starlink-ukraine.html ↩
-
Fitzgerald J. Ukraine war: Elon musk’s SpaceX firm bars kyiv from using starlink tech for drone control. BBC News. 2023. ↩
-
Mölleryd B, Ozger M, Westring M, Nordlöw A, Schupke D, Engström U, et al. Regulatory and spectrum policy challenges for combined airspace and non-terrestrial networks. Telecommunications Policy. 2025 Mar;49:102875. doi: 10.1016/j.telpol.2024.102875 ↩
-
Jamshidi M, Moztarzadeh O, Jamshidi A, Abdelgawad A, El-Baz AS, Hauer L. Future of drug discovery: The synergy of edge computing, internet of medical things, and deep learning. Future Internet. 2023;15(4):142. ↩
-
Shen T, Ding L, Sun J, Jing C, Guo F, Wu C. Edge computing for IoT security: Integrating machine learning with key agreement. In: 2023 3rd international conference on consumer electronics and computer engineering (ICCECE). IEEE; 2023. p. 474–83. ↩
-
Kolevski D, Michael K. Edge computing and IoT data breaches: Security, privacy, trust, and regulation. IEEE Technology and Society Magazine. 2024;43(1):22–32. ↩
-
Li Q, Ding D, Conti M. Brain-computer interface applications: Security and privacy challenges. In: 2015 IEEE conference on communications and network security (CNS). IEEE; 2015. p. 663–6. doi: 10.1109/CNS.2015.7346884 ↩ ↩2 ↩3
-
Patel N, Verma J, Jain S. Emerging applications of brain computer interfaces: A comprehensive review and future perspectives. In: 2023 IEEE 11th region 10 humanitarian technology conference (R10-HTC). IEEE; 2023. p. 312–7. doi: 10.1109/R10-HTC57504.2023.10461739 ↩ ↩2 ↩3 ↩4 ↩5 ↩6
-
Meng L, Jiang X, Wu D. Adversarial robustness benchmark for EEG-based brain–computer interfaces. Future Generation Computer Systems. 2023 Jun;143:231–47. doi: 10.1016/j.future.2023.01.028 ↩ ↩2 ↩3 ↩4 ↩5
-
Ouyang J, Wu M, Li X, Deng H, Wu D. BRIEDGE: EEG-adaptive edge AI for multi-brain to multi-robot interaction. 2024 Mar; ↩ ↩2
-
Xue B, Wu L, Liu A, Zhang X, Chen X. White-box attacks on the CNN-based myoelectric control system. In 2021. p. 149–57. doi: 10.1007/978-3-030-93046-2_13 ↩ ↩2
-
Liu Z, Meng L, Zhang X, Fang W, Wu D. Universal adversarial perturbations for CNN classifiers in EEG-based BCIs. Journal of Neural Engineering. 2021 Aug;18:0460a4. doi: 10.1088/1741-2552/ac0f4c ↩
-
Zafar S, Nazir M, Sabah A, Jurcut AD. Securing bio-cyber interface for the internet of bio-nano things using particle swarm optimization and artificial neural networks based parameter profiling. Computers in Biology and Medicine. 2021 Sep;136. doi: 10.1016/j.compbiomed.2021.104707 ↩ ↩2 ↩3 ↩4 ↩5 ↩6 ↩7
-
Camara C, Peris-Lopez P, Tapiador JE. Security and privacy issues in implantable medical devices: A comprehensive survey. Vol. 55, Journal of Biomedical Informatics. Academic Press Inc.; 2015. p. 272–89. doi: 10.1016/j.jbi.2015.04.007 ↩ ↩2 ↩3
-
Sharma G, Bala S, Verma AK. Security frameworks for wireless sensor networks-review. Procedia Technology. 2012;6:978–87. doi: 10.1016/j.protcy.2012.10.119 ↩
-
Usman M, Asghar MR, Ansari IS, Qaraqe M. Security in wireless body area networks: From in-body to off-body communications. IEEE Access. 2018;6:58064–74. doi: 10.1109/ACCESS.2018.2873825 ↩ ↩2 ↩3 ↩4 ↩5
-
Bashirpour Bonab A, Fedele M, Formisano V, Rudko I. In complexity we trust: A systematic literature review of urban quantum technologies. Technological Forecasting and Social Change. 2023;194:122642. Available from: https://www.sciencedirect.com/science/article/pii/S004016252300327X ↩
-
Hannas WC et al. Bibliometric analysis of china’s non-therapeutic brain-computer interface research. https://cset.georgetown.edu/wp-content/uploads/CSET-Bibliometric-Analysis-of-Chinas-Non-Therapeutic-Brain-Computer-Interface-Research.pdf: Center for Security; Emerging Technology; 2024. ↩
-
Bordin G et al. JRC horizon scanning on dual-use civil and military research. European Commission; 2020. ↩
-
Blumenthal MS. Technological approaches to human performance enhancement. RAND Corporation; 2021. ↩
-
Black M et al. Supporting the royal australian navy’s campaign plan for robotics and autonomous systems. RAND Corporation; 2022. ↩
-
Chakraborty A et al. Governance in the age of generative AI: A 360º approach for resilient governance in the age of generative AI: A 360 approach for resilient policy and regulation. World Economic Forum; 2024. ↩
-
Navigating cyber resilience in the age of emerging technologies: Collaborative solutions for complex challenges. Available from: https://www3.weforum.org/docs/WEF_Navigating_Cyber_Resilience_in_the_Age_of_Emerging_Technologies_2024.pdf ↩
-
Untitled. Available from: https://www.pwc.com/gx/en/industries/communications/assets/pwc-ai-and-iot.pdf ↩
-
Simonovich L. Securing the energy revolution and IoT future | MIT technology review. 2021. Available from: https://www.technologyreview.com/2021/09/21/1036050/securing-the-energy-revolution-and-iot-future/ ↩
-
Chapter 3.digital dependencies and cyber vulnerabilities - global risks report 2023 | world economic forum. Available from: https://www.weforum.org/publications/global-risks-report-2023/in-full/chapter-3-digital-dependencies-and-cyber-vulnerabilities/ ↩
