Cyber security of consumer IoT - manufacturer survey
Published 5 December 2024
Executive summary
In the context of a growing market for consumer Internet of Things (IoT) products and an increasing risk of cyber attacks, consumer IoT products can be exploited to cause harm to individuals, companies, government, and society at large. In response, the UK Government introduced the world’s first legislation on the cyber security of consumer connectable products: the Product Security and Telecommunications Infrastructure (PSTI) Act 2022 and the PSTI Regulations 2023.
Prior to the entry into force of the PSTI Regulations 2023 on 29th April 2024, the UK Government’s Department for Science, Innovation and Technology (DSIT) commissioned this study, which aimed to:
-
Map and analyse the market for consumer connectable products; and
-
Collect and analyse evidence on the compliance of manufacturers with the PSTI legal regime, as well as evidence on awareness and impacts of the legislation.
To achieve these aims, the project team from DJS Research and the Centre for Strategy & Evaluation Services (CSES) used a combination of research methods. Desk research was used to map the UK market for consumer connectable products, and collect available market data. This desk research was facilitated by data from two external data sources: Copper Horse and Beauhurst. The desk research was supplemented by a quantitative telephone survey to collect primary data from manufacturers. Given the challenges in reaching manufacturers, the survey was supplemented by a second round of desk research to assess publicly available evidence of manufacturer compliance with the PSTI requirements. Finally, we conducted qualitative interviews with manufacturers and industry associations.
However, the research process faced significant challenges, impacting the robustness and generalisability of the findings:
-
Mapping the UK market for consumer connectable products: the main challenges included the scale of products available on online third-party marketplaces, and the availability and quality of data, in particular, information on the size of the manufacturers (turnover and employee numbers).
-
Surveying the manufacturers; the main challenge was engaging manufacturers. A lack of contact information made it difficult to reach companies, while it was often difficult to find the right person. Finally, when the right person was identified, some companies were reluctant to participate due to concerns about the potential repercussions of demonstrating a lack of compliance (despite reassurances to the contrary). Therefore, less than 10% of the manufacturers initially mapped engaged in the research (33 of 394).
Chapter 2 (Methodology) further details these challenges and the mitigation measures implemented.
Analysis of manufacturer compliance levels and challenges
A key finding from the consultations with manufacturers and industry representatives was that the security requirements themselves are generally straightforward to implement. There was only one exception: the requirement to provide transparency on the length of time security updates are provided. Moreover, industry representatives strongly agreed with the need to introduce baseline security requirements for consumer connectable products. Respondents appreciated the approach of phasing in a selection of requirements, within the broader context of the UK Code of Practice for Consumer IoT Security and ETSI EN 303 645.
Regarding current compliance levels, the quantitative survey found the highest levels of compliance with the requirement to provide information on how to report security issues: 58% (19/33) of manufacturers consulted have already introduced the requirement for all products. The second highest levels of compliance were found for the provisions on passwords, implemented by 52% (17/33), while compliance with requirements on information about minimum security update periods was lower: only 27% (9/33) of manufacturers have already introduced this requirement for all products. However, 39% (13/33) reported that they intend to introduce the requirement within a certain time frame.
The current status of compliance, as reported by the surveyed manufacturers, is demonstrated in the below figure.
Figure 1: Compliance status for each of the three requirements (Question 6, Base: 33)[footnote 1]
| Compliance status | Passwords | Public point of contact | Security updates |
|---|---|---|---|
| Introduced for all products | 52% | 58% | 27% |
| Introduced for some products | 12% | 0% | 6% |
| Looking to introduce within a certain time | 9% | 24% | 39% |
| Looking to introduce in the near future but not sure when | 12% | 18% | 21% |
| Not looking to introduce for some products | 3% | 3% | 3% |
| Not looking to introduce at all | 0% | 0% | 0% |
| This requirement is not relevant to us | 18% | 3% | 21% |
These findings were also validated through an in-depth desk research exercise. Examining a subset of 70 companies, we attempted to assess evidence of manufacturer compliance based on publicly available information. Here, we found similar levels of compliance with the provisions on passwords: 46% (32/70) were already compliant or somewhat compliant with the new password provisions. Compliance with the requirement to provide information on how to report security issues was slightly lower: only 33% (24/70) of the sample showed publicly available evidence of compliance, contrasting with the 58% (19/33) compliance rate found in the quantitative survey.
The third security requirement – information on minimum security update periods – was more difficult to assess due to a lack of clear information: for 49% (34/70), we were unable to find whether the companies had published relevant information. These differences further highlight the difficulty of assessing compliance, and the generalisability challenges of the quantitative survey findings. In this context, challenges related to the overarching regime have resulted in compliance processes that are more complex, uncertain and costly than anticipated:
-
Product scope: Manufacturers reported uncertainty regarding which products are within scope. For instance, many were unsure whether products that can connect to internet-connected devices via Bluetooth, or products that can manage multipoint connections were in scope. They were also unsure about products that are sold business-to-business (B2B) but used by consumers.
-
Requirement for information on minimum security update periods: Manufacturers reported challenges indicating a minimum support period for each product, given the impacts of complex, global supply chains and minor differences with the requirements anticipated in the EU Cyber Resilience Act (CRA).
-
Timelines for implementation: The most prominent concern of manufacturers and industry associations related to the implementation timeline. Under the current scenario, stakeholders raised a significant risk that existing stock may need to be scrapped or recycled due to the fact that the legislation applies to products that are ‘made available’ rather than ‘placed on the market’ and the resulting need to retrospectively ensure compliance of products that are already in the supply chain and the market.
-
Demonstrating compliance: Despite the minimum information required for statements of compliance (SoC) being set out in Schedule 4 of the PSTI Regulations 2023, manufacturers reported uncertainty and challenges regarding the required content and form of the SoC.
In this context, many respondents highlighted that ensuring compliance was still an ongoing process. Moreover, manufacturers noted that these challenges increase the scale of the activities they need to take to ensure compliance, as well as the associated costs of compliance.
The quantitative survey asked manufacturers how likely they are to be compliant with each requirement by 29th April 2024. As illustrated in the below figure, most manufacturers consider that they are either ‘Very likely’ or ‘Quite likely’ to be compliant with each of the requirements (at least 85% for each requirement).
Figure 2: Likelihood of being compliant with each security requirement by 29th April 2024 (Question 14, Base: 33)
| Likelihood of being compliant | Very likely | Quite likely | Quite unlikely | Very Unlikely | Don’t know |
|---|---|---|---|---|---|
| Passwords are unique, not guessable or based on incremental counters | 76% | 9% | 0% | 3% | 12% |
| The manufacturer provides a public point of contact to enable security issues to be reported | 85% | 0% | 3% | 6% | 6% |
| Information on the minimum length of time for which security updates will be provided must be made available | 64% | 24% | 6% | 0% | 6% |
Compliance activities, costs and other impacts
The main activities manufacturers have taken or plan to take to ensure compliance with the legislation included familiarising themselves with the legislation (87%, 27/31) and preparing a self-declaration/assessment of compliance (81%, 25/31). Manufacturers have also obtained legal advice (68%, 21/31); conducted or plan to conduct third-party testing (52%, 16/31); undertaken or will seek to undertake a formal third-party compliance assessment (42%, 13/31); and amended compliance information at the point of sale (48%, 15/31).
While difficult to quantify, the consulted manufacturers noted that they had already incurred, and anticipate incurring additional costs to comply with the legislation. The compliance costs stem from the abovementioned activities and the cost of additional staff, as well as anticipated action needed to deal with non-compliant stock (i.e. dispose, recycle or pivot to non-UK markets). Manufacturers expect to have to absorb some of those additional costs themselves, but are likely to pass on other costs to consumers and retailers.
Manufacturers also stated concerns that the time, effort and costs required to implement the legislation and the possibility of future regulatory divergence with EU legislation in this field could have a negative effect on industry innovation and competitiveness. In addition, they expressed concerns regarding the environmental impact of certain regulatory decisions. These were mainly due to concerns around the possible need to dispose of stock that is already on the market and cannot be made compliant, as well as the use of paper instead of digital SoC.
Notwithstanding the above, manufacturers and consumers are expected to experience significant benefits as a result of the legislation. At the manufacturer level, these include improvements in: product security; cyber security; consumer confidence in connectable products; customer satisfaction and loyalty; and reputation of products and manufacturers.
Moreover, significant indirect benefits for both consumers and businesses can be expected through improved resillience to cyber attacks and a reduction in the costs / impacts of cyber attacks.
Awareness of the PSTI regime
Almost all manufacturers surveyed were aware of relevant regulations on cyber security: 91% of manufacturers surveyed (30/33) stated they were aware of UK cyber security regulations related to consumer connectable products. They were slightly less certain when prompted with regard to specific regulations, including the PSTI Act 2022, the PSTI Regulations 2023, ETSI EN 303 645 and ISO/IEC 29147: 2018 on vulnerability disclosure. Yet overall, awareness of even specific provisions was high: 76% of manufacturers (25/33) reported being fully aware of the specific provisions of the PSTI Act and Regulations, with a further four stating that they were partially aware.
Considering manufacturers’ sources of information, most of those who were moderately aware reported having received information from industry or trade bodies (48%, 14/29), UK Government public consultations (28%, 8/29), and/or internal legal, compliance or product security teams (21%, 6/29). Similar responses were given when respondents were asked how they planned to make themselves aware of future regulations.
These results indicate that manufacturers may under-utilise available mechanisms of acquiring information. For instance, only 3% (1/29) stated that they engage with past government research; 7% (2/29) proactively track relevant legislation, and 15% (4/29) engage directly with the UK Government.
Analysis of consumer connectable product market
Within the market research task, a total of 394 manufacturers, 416 brands and 1,024 consumer connectable products were mapped. These were disaggregated to the extent possible by the following variables:
-
Product types: The most common types of products included safety and security (22%, 225/1024 products) and lighting products (11%, 117 products), followed by smart home (10%, 98 products), kitchen appliances (7%, 75 products), audio (7%, 70 products), health, fitness, and wellbeing (6%, 65 products), wearables (6%, 59 products), environmental control (6%, 59 products), and home appliances (4%, 42 products).
-
Geographical location: Just over half of the products were either manufactured by US (28%, 283 products) or Chinese companies (25%, 254 products), with around 15% (141) manufactured by UK companies. The remaining products came from Germany (7%, 69 products), Japan (4%, 44 products), the Netherlands (4%, 37 products), France (4%, 39 products), and other countries.
-
Manufacturer size: The majority of manufacturers in the sample were large: 37% (145 manufacturers) were large companies with 250 or more employees; 21% (82 manufacturers) were medium-sized companies with 50-249 companies; 20% (80 manufacturers) were small companies with 10-49 employees; and 8% (32 manufacturers) were micro companies with 1-9 employees. We were unable to find information on the size of the remaining 14% (55 manufacturers).
-
Manufacturer turnover: Just under one third (29%, 114 manufacturers) of manufacturers had a turnover of more than £50 million; 15% (60 manufacturers) had a turnover between £10 and £50 million; and around 22% (87 manufacturers) had a turnover below £10 million. We were unable to find information on the turnover of the remaining 34% (133 manufacturers). Because information is more likely to be publicly available for larger firms, we suspect that many of the companies we were unable to find information on are smaller, both in terms of employees and turnover.
-
Routes to the market: The overwhelming majority of manufacturers use online shops to sell their products. Because some manufacturers own more than one brand, the following statistics are based on the total population of brands, not manufacturers: 88% (368 brands) are sold on online third-party marketplaces like amazon; 72% (299 brands) are made products available in the UK through company’s own online shop. Physical shops were somewhat less common: 45% (186 brands) are sold in a third-party physical shop; 9% (38 brands) are in companies’ own physical shops.
In this context, key trends and challenges within the UK market for consumer connectable products include that companies are entering and exiting the market relatively quickly, the general impact of Brexit and the anticipated risk of regulatory divergence with the EU, as well as the important roles of online third-party marketplaces and Chinese manufacturers in the market, even when acting as OEMs/ODMs.
1. Introduction
This research report presents the results of the project “Manufacturer Survey in Relation to the Cyber Security of Consumer IoT in the UK”, commissioned by the Department for Science, Innovation and Technology (DSIT) and conducted by DJS Research and the Centre for Strategy & Evaluation Services (CSES) from November 2023 to April 2024.
1.1 Project background and context
The number of consumer Internet of Things (IoT) devices on the market is rising and the number of cyber-attacks on such devices is also increasing. To address this challenge, the UK Government introduced the Product Security and Telecommunications Infrastructure (PSTI) Act 2022 and the PSTI Regulations 2023. This regime builds on long-standing non-legislative initiatives, including the UK Code of Practice for Consumer IoT Security, the European standard on the Cyber Security for Consumer IoT (ETSI EN 303 645) and the work of the National Cyber Security Centre (NCSC)[footnote 2]
The growth of the consumer IoT market
IoT (‘or smart’) devices are on the rise. YouGov (2022) estimates that 1% of UK adults own a (voice-activated) smart kettle, 2% own a smart thermostat (allowing users to control heating from their phone), 3% own a smart security product such as a motion camera sensor to monitor activity around doors and windows, and 11% own a smart speaker. Ofcom (2023) reports even higher numbers for certain types of device (e.g. 40-50% of UK consumers own a smart speaker), while recent research commissioned by DSIT on device ownership amongst individuals found that 64% of surveyed consumers own a smart TV.[footnote 2]The types of ‘products’ that are being connected to the internet is continuously growing. Amongst many others, connected versions of door locks, children’s toys, washing machines, and refrigerators exist, alongside larger products such as cars, scooters and drones.
Foreshadowing future trends, nearly 40% of YouGov’s respondents agreed that smart appliances made their life easier. As a result, the expected economic value of IoT is rising rapidly. McKinsey research from 2017 estimated that 127 new devices are connected every second, with the potential to generate USD 4-11 trillion in economic value by 2025 (albeit including non-consumer IoT). More recently, Statista estimated in 2020 that each UK household had an average of nine IoT devices, with 2022 research estimating that the total number of consumer IoT connected devices worldwide will exceed 17 billion in 2030.
The cyber challenge for IoT devices
While consumers have come to see IoT devices as part of their everyday lives and assume they are secure, the number of cyber-attacks is increasing. IoT devices often lack even minimum levels of security and can act as low-hanging fruit for cyber attacks. Cyber security experts at Kaspersky found that attacks targeting IoT devices (including consumer, business and industrial devices) doubled between 2020 and 2021, allowing access to sensitive user data and potential for further exploitation.
According to Kaspersky, the two most prominent methods used to infect IoT devices are to crack weak passwords and to exploit vulnerabilities in network services. In a 2022 study for Which?, a team of ethical hackers seeking to disclose security issues in IoT devices in the UK were able to hack dozens of test devices, including a smart doorbell, a smart speaker/hub, a smart TV, and a smart baby monitor.
The UK product security regime
Prior to the introduction of the PSTI Act 2022 and PSTI Regulations 2023, the UK Government took steps to tackle the cyber security challenges facing IoT devices, the most prominent of which are explained in the below box.
Table 1: Summary of policy actions leading to the adoption of the PSTI legal regime
The UK Code of Practice (CoP) for Consumer IoT Security was published in March 2018 as part of the Secure by Design report. The CoP was developed by the Department for Digital, Culture, Media and Sport (DCMS), in conjunction with the NCSC and cyber experts, on the basis of a mapping of IoT security recommendations, guidance and standards. The CoP aimed to support all entities involved in the design, development, manufacturer and retail of consumer IoT devices by outlining 13 outcome-focused guidelines based on good practice in IoT security.
Following the publication of the CoP, the European Standards Organisation ETSI[[footnote 4] launched the first globally applicable industry standard on internet-connected consumer devices in February 2019 (ETSI Technical Specification 103 645). This was complemented in June 2020 by European standard EN 303 645 on the Cyber Security for Consumer IoT, which established 13 security baseline requirements for such devices, mirroring the CoP.
Alongside the development of the European standard, the UK Government continued to investigate the best way to regulate the issue, with extensive research commissioned on the nature of the challenges, the regulatory possibilities and the anticipated impacts and costs of such interventions.[footnote 5]
On this basis, and within the context of the National Cyber Strategy 2022, the UK Government introduced a product security regime for consumer connectable products that aims to protect individual privacy and security and guard citizens, networks, and infrastructure against cyber-attacks. The regime consists of two key pieces of legislation:
-
The Product Security and Telecommunications Infrastructure Act 2022 (PSTI Act), which requires manufacturers, importers, and distributors of consumer connectable products to comply with new security requirements, establishes the enforcement mechanisms and creates civil and criminal sanctions to prevent unsecure consumer connectable products from entering the UK market. It was introduced in November 2021 and came into force in December 2022.
-
The Product Security and Telecommunications Infrastructure (Security Requirements for Relevant Connectable Products) Regulations 2023 (PSTI Regulations) specifies the security requirements. It was made in September 2023 and comes into force on 29th April 2024.
Different terms are used to describe these devices: the terms ‘smart’, ‘IoT’ or ‘connectable’ products are used interchangeably. The PSTI Act (s 5) uses the term ‘connectable’ products, defining an ‘internet-connectable’ product as ‘capable of connecting to the internet’, and a ‘network-connectable product’ as one that is ‘capable of sending and receiving data by means of a transmission involving electrical or electromagnetic energy’. ‘UK consumer connectable products’ are defined as internet or network-connectable products that are made available to consumers in the UK.
The PTSI Act places a duty on manufacturers of consumer connectable products that are or will be sold in the UK to comply with security requirements (s 8) and to ‘take action’ if they become aware (or ought to be aware) that a product does not comply with a relevant security requirement (s 11). In case of a ‘compliance failure’, manufacturers are to ‘take all reasonable steps’ to ‘remedy the compliance failure’. Manufacturers must also notify importers, distributors and any other manufacturers they are aware of, and if necessary, stop sales and inform consumers. Manufacturers must also keep a record of any compliance failures, or investigations in relation to a real or suspected compliance failure for a period of 10 years (s 12). Similar rules apply to importers (s 14-20) and distributors (s 21-25) of consumer connectable products. Chapter 3 references the enforcement actions, including compliance, stop and recall notices, as well as monetary penalties; Sections 36-38 enable the Secretary of State to give maximum fixed monetary penalties of GBP 10 million or 4% of worldwide turnover, in addition to daily penalties of up to GBP 20,000 for each day for which the relevant breach continues after the end of the period specified for payment of the fixed penalty.
The specific security requirements are set out in the PSTI Regulations 2023. They apply to both the hardware and the associated software of the consumer connectable product and include requirements regarding:
-
Passwords, which must be unique, not guessable or based on incremental counters.
-
Information on how to report security issues, which requires that manufacturers publish: i) information on at least one point of contact for reporting of security issues; and ii) information on when a person reporting an issue will receive acknowledgement of receipt of the issue report and when they will receive status updates until resolution.
-
Information on minimum security update periods, which requires that manufacturers must specify the minimum length of time for which the connectable device will receive security updates.
For the latter two requirements, the information must be accessible, clear and transparent (e.g. made available without prior request, in English, free of charge, and ‘in such a way that is understandable by a reader without prior technical knowledge’). Manufacturers must also prepare a statement of compliance (SoC) to accompany all consumer connectable products made available on the UK market.
The Regulations also list connectable products that are exempt from the regulatory regime: products for the Northern Irish market, charging points for electrical vehicles, medical devices, smart meter products, and tablets and computers (unless they are designed exclusively for children and young people under the age of 14) are exempt.
1.2 Research purpose, objectives and scope
The purpose of the project was to identify the compliance levels amongst manufacturers in the lead up to the PSTI Regulations 2023 coming into force on 29th April 2024, specifically by collecting information on current compliance levels and providing a baseline dataset that can be used in future monitoring and evaluation.
In this context, the research aimed to achieve two objectives:
-
Map and collect market data on manufacturers of consumer connectable products that make available or sell relevant products to UK consumers and are subject to the PSTI Act 2022 and PSTI Regulations 2023. This seeks to assess the number of manufacturers selling to the UK market and the types of consumer connectable devices produced, as well as the geographical location, turnover, number of employees, and routes to market of these manufacturers.
-
Collect evidence on compliance levels with the cyber security requirements stipulated in the PSTI Act 2022 and the PSTI Regulations 2023 amongst manufacturers, as well as evidence on awareness and the anticipated impacts of the legislation.
Considering the scope of the research, the following factors are important:
-
Consumer connectable products and manufacturers within scope align to the definition of consumer connectable products stipulated in the PSTI legal regime.
-
All manufacturers that sell or make consumer connectable products available to UK consumers are within scope, regardless of where they are based.
1.3 Report structure
This research report contains:
-
Methodology – Summary of the research methods used, as well as the challenges faced (Chapter 2).
-
Analysis of consumer connectable product market– Overview of the market for consumer connectable products (Chapter 3).
-
Analysis of PSTI awareness, compliance and impacts (Chapter 4).
-
Conclusions – Conclusions drawn from the research findings (Chapter 5).
These sections are supplemented by Annexes presenting a bibliography, data tables supporting the market analysis and the full results of the CATI survey.
2. Methodology
The following research methods were deployed to achieve the above objectives:
Quantitative telephone survey to collect primary data from manufacturers on awareness, compliance and impacts of the PSTI regime. As a result of the challenges experienced (detailed below), this survey was supplemented by targeted desk research to identify evidence of compliance with the three security requirements outlined in the PSTI Regulations 2023 across a sample of manufacturers.
-
Qualitative semi-structured interviews with manufacturers and industry associationsto complement the quantitative survey with more in-depth exploration of the research issues.
-
Desk research and liaison with an external data provider to map manufacturers of consumer connectable devices and collect relevant market data on that sample of companies.
Using the data collected through the above methods, the research team analysed the size, structure and dynamics of the UK consumer connectable device market (see Chapter 3), the awareness and compliance levels with the PSTI regime, and the impacts of the regime (see Chapter 4).
The approach to each method and the challenges faced are now presented.
Quantitative telephone/CATI survey
Based on the research objectives, DJS Research with input from CSES designed and scripted the computer assisted telephone interview (CATI) questionnaire. After the setup was complete, a series of quality checks were undertaken before fieldwork began.
An initial database of around 400 business records was used during the fieldwork. Due to various challenges with contacting non-UK businesses, DJS obtained support from experienced international partners to help contact around 150 overseas businesses from the list (more detail below).
At the start of fieldwork, a highly experienced team of business to business (B2B) interviewers was fully briefed on the project background and questionnaire.
The fieldwork lasted a total of ten weeks, starting on 10th January 2024 and ending on 20th March 2024.
The original intention was that the survey questionnaire should take an average of 15 minutes to complete. However, the interviews took between 30 and 70 minutes due to the depth of feedback interviewees were keen to provide. All interviews were conducted in English with senior individuals responsible for product cyber security.
A total of 33 responses were obtained from the quantitative survey. This comprised 32 telephone interviews and one online completion.
The final profile of interviewed businesses indicates a good spread of respondents by business size, location and product type:
-
Geographical location: Just under half (16) of the companies that participated have their headquarters in the UK, around a quarter in the rest of Europe (9) and the remaining quarter in the USA/Canada (6) or Asia (2).
-
Business size: Nine are micro or small employers (fewer than 50 employees), five are medium-sized employers (50-249 employees) and the remainder are large employers with 250 or more employees.
-
Range of products manufactured by the companies surveyed also varies considerably, with the majority producing a wide range of home and personal electronic appliances/devices (e.g. TVs, home cinemas, mobile phones and laptops) and white goods (e.g. washing machines, dryers, fridges and ovens), as well as products such as air conditioning and heating systems, security devices, cameras, smart watches, kettles/coffee machines, garage doors, mobility devices, lighting, navigation devices and audio equipment.
However, the research team faced significant challenges in the delivery of the quantitative survey. In line with the specification, DJS Research and CSES estimated that they would achieve up to 150 interviews in their proposal, albeit citing risks related to engagement and response rates. In practice, this proved challenging for the following reasons:
-
Lack of available and accessible contact information. Whilst CSES provided DJS Research with a detailed database of contacts, it was difficult and time consuming to find named contacts. DJS Research continued this activity after taking receipt of the contact database but encountered very similar issues. The majority of businesses either do not publish telephone numbers and/or email addresses on their company websites or provide generic contact details. In most cases, the only method of contact was submitting an online form (which was often targeted at technical support or general product queries). In the rare instances where it was possible to speak to a ‘gatekeeper’, they were often unsure who was the most appropriate person to contribute. We also found that several numbers went straight to answer phone, were unobtainable or were more designed for consumers to allow them to get through to a Customer Service/Technical helpline, rather than Senior Managers/Directors of the business.
-
Unwillingness or concerns about the potential repercussions if they indicated a lack of compliance in their reponse. Another key challenge experienced throughout the fieldwork was the unwillingness to participate. This appeared to be due to concerns about potential consequences if they disclosed a lack of compliance (despite reassurances that this would not be the case).
To address these challenges, the team implemented extensive mitigation measures, including: preparing and disseminating communication materials, including via DSIT channels, including via a supporting letter to manufacturers from DSIT, social media and established industry associations; amending interview staffing to ensure coverage of North American and Asian markets; and purchasing an additional database of named contacts.
Furthermore, it should be noted that, despite the relatively low number of interviews, the quantitative survey has provided a good cross-section and wealth of detailed information, supplemented with the depth interviews.
As the interview numbers remained low after implementing the above mitigation actions, DJS Research and CSES conducted an in-depth desk research exercise to assess compliance levels using the information provided on manufacturers websites. A data collection tool was developed in Excel and a pilot was conducted across 10 manufacturers to test the utility of the method and the availability of data. Once quality assured, reviewed and agreed with DSIT, a sample of manufacturers was chosen, and the researchers were briefed on the purpose of the activity and the research process.
With the aim of reaching a combined total of 100 businesses across the quantitative survey and the desk research, this activity was conducted for a sample of 70 businesses representing a balanced coverage of business sizes, geographical locations and product types.
Following the selection of the sample of manufacturers to be covered by the desk research exercise, the DJS and CSES researchers reviewed the websites of the manufacturers, including product descriptions for products within scope, terms of service, privacy and security information and other relevant documentation, to identify and assess evidence of compliance with each of the three security requirements stipulated in the PSTI Regulations 2023.
However, as this exercise was conducted prior to the entry into force of the Regulations, explicit references to compliance and key compliance documents (i.e. SoCs) were not found. Therefore, it is important to note that, as the research aimed to identify publicly available evidence of compliance, it was not feasible, in many cases, to provide a definitive judgement on compliance. Instead, each manufacturer was assessed against a scale of the level of evidence of compliance, accompanied by a qualitative description of the evidence identified. The following scale was used:
-
Strong evidence of compliance: Evidence identified of compliance with all elements of the security requirement.
-
Somewhat compliant: Evidence identified of compliance with at least one element of the security requirement, or indications of full compliance but formulated in a way that is unclear.
-
No evidence of compliance: No evidence of compliance identified.
-
Information not available: Limited or no information of relevance available.
Qualitative semi-structured interviews
The purpose of the qualitative interviews was to supplement the quantitative survey data through more in-depth discussions with both manufacturers and industry associations. These discussions should cover all key research issues, including market challenges, cyber security approaches, awareness of and compliance with the PSTI Act 2022, the PSTI Regulations 2023 and the ETSI standard, and the actual or anticipated impacts of the new legal regime.
DJS Research, with input from CSES, drafted and circulated two interview guides (one for manufacturers and one for industry associations).
With a target of 10-20 qualitative interviews, the original intention was to select and source manufacturers for more in-depth discussions following their participation in the quantitative survey. However, given the engagement challenges detailed above and the extent of the information provided through many of the quantitative survey interviews (which acted as combined quantitative and qualitative interviews), a total of nine additional semi-structured interviews were conducted: five with manufacturers and four with relevant representatives of industry.
Manufacturer mapping and collection of market data
The purpose of this activity was to map manufacturers of consumer connectable products selling into the UK and the products they sell, producing as complete a database as possible. Where available, additional data, including turnover, number of employees, geographical location, routes to market and contact details, were added. This required the following steps:
-
Step one: Define broad product categories and sub-categories. Building on previous research[footnote 6] CSES defined an initial list of product types and overarching product categories to be used in the dataset. These were consistently reviewed throughout the exercise based on new insights.
-
Step two: Develop a data collection matrix. To support the data collection and extraction process, CSES developed a matrix in which the key data for each manufacturer/product can be collated in a structured manner.
-
Step three: Review literature/data sources and extract relevant data on IoT manufacturers selling to the UK. Primarily, this focused on the open data developed through research conducted by Copper Horse for the IoT Security Foundation (IoTSF) on the state of vulnerability disclosure, but also other market research sources and literature identified through targeted desk-based research. The list of manufacturers prepared by Copper Horse was reviewed and edited to ensure the companies/products identified were in scope.
Step four: Conduct desk-based research to complete the matrix. This was achieved through three sub-steps: i) search key online / high street retailers to validate and enhance the Copper Horse/IoTSF open data, and ultimately identify
DSIT, with a third-party data provider (Beauhurst) to access company data on UK-based legal entities linked to manufacturers of consumer connectable products; and iii) review other data sources, such as web data (e.g. lists of members of IoT industry associations), Companies House registration data, LinkedIn and market research reports to complete the matrix for each manufacturer/product to the extent possible.
- Step five: Analyse the data to provide results on key indicators, including number of manufacturers, disaggregated by the following variables: product type/category, geographical locations, routes to market, number of employees, and turnover. The results of this analysis are presented in Chapter 3.
This exercise faced significant challenges, for instance related to the availability and quality of company data. These challenges, and the mitigation measures taken, are detailed in Chapter 3.
3. Analysis of consumer connectable product market
3.1 Market size and structure
Consumer connectable products sold in the UK
This section analyses the market of consumer connectable products mapped as part of the desk research. It begins with an analysis of the types of consumer connectable products sold in the UK, before it presents their manfacturers in more detail.
Figure 3 shows the number of consumer connectable products (n=1024) by type. Most products were categorised as ‘Safety & Security’ products (e.g. smart security cameras, video doorbells, or smart smoke alarms), followed by ‘Lighting’ products (e.g. smart light bulbs, or smart lamps), ‘Smart Home’ products (e.g. smart plugs, switches, or outlets), ‘Kitchen appliances’ (e.g. smart dishwasher, smart coffee machine), ‘Environmental control’ products (e.g. smart air conditioning), and ‘Health, Fitness, and Wellbeing’ products (e.g. smart body scales, or smart water bottles).
Figure 3: Consumer connectable products sold in the UK, by category (n=1024 products)
| Safety & Security | 22% |
| Lighting | 11% |
| Smart Home | 10% |
| Kitchen appliances | 7% |
| Audio | 7% |
| Health, Fitness & Wellbeing | 6% |
| Wearables | 6% |
| Environmental Control | 6% |
| Home appliances | 4% |
| Home entertainment | 3% |
| Heating | 3% |
| Tablets and e-readers | 2% |
| WIFI and Networking | 2% |
| Mobile | 2% |
| Workplace | 2% |
| Pet Care | 2% |
| Garden appliances | 1% |
| Leisure & Hobbies | 1% |
| Hub/Home Control | 1% |
| Children’s toys and appliances | 1% |
| Service & Care | 1% |
| Other | 0% |
These products were made by companies headquartered in 28 countries across the globe. However, as shown in Figure 2, about four fifth of the products come from manufacturers in just five countries: the USA (28%), China (25%), the UK (14%), Germany (7%) and Japan (4%).
Figure 4: Consumer connectable products sold in the UK, by country of origin (n=1024 products)
| USA | 28% |
| China | 25% |
| Other | 23% |
| UK | 14% |
| Germany | 7% |
| Japan | 4% |
The importance of these countries as manufacturers of UK consumer connectable products depends on the type of product. The below figure breaks down the country of origin by product category. It focuses on the six main product categories: safety and security, lighting, smart home, kitchen appliances, audio, health, fitness & wellbeing, and wearables which account for almost 70% of the products mapped. The USA manufactures 43% of health, fitness and wellbeing products, 36% of kitchen appliances, and 30% of safety and security products. China, in turn, manufactures 41% of lighting products, 24% of smart home products, and 23% of safety and security products. The UK manufactures 24% of audio products, 23% of health, fitness and wellbeing products and 17% of safety and security products. The final two players only manufacture a significant share of one type of products: Germany manufactures 15% of kitchen appliances; Japan manufactures 14% of audio devices mapped in our dataset.
Figure 5: Consumer connectable products sold in the UK, by category and country of origin (n=1024 products)
| Audio | Health, Fitness & Wellbeing | Kitchen appliances | Lighting | Safety & Security | Smart Home | Wearables | |
|---|---|---|---|---|---|---|---|
| USA | 20% | 43% | 36% | 25% | 30% | 22% | 24% |
| Other | 20% | 15% | 37% | 19% | 22% | 27% | 17% |
| China | 20% | 6% | 3% | 41% | 23% | 24% | 31% |
| UK | 24% | 23% | 8% | 5% | 17% | 15% | 24% |
| Germany | 1% | 6% | 15% | 9% | 6% | 10% | 0% |
| Japan | 14% | 6% | 1% | 1% | 2% | 1% | 5% |
The products we mapped were produced by 394 different companies under 416 different brand names. The next subsection illustrates where the manufacturers are headquartered; how large they are in terms of employees and turnover data, and where they sell their products.
Manufacturers of consumer connectable products sold in the UK
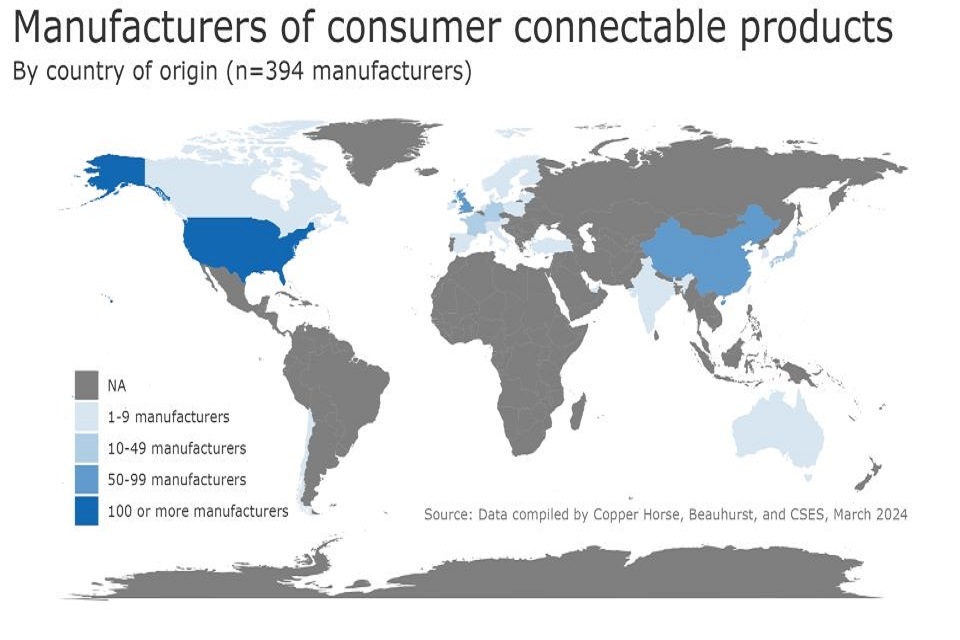
The map in figure 4 illustrates the countries of origin of the products we mapped. The darker shades of blue show a higher number of manufacturers from the respective country; the lower shades illustrate a lower number of manufacturers. The main players are the US (n=134 manufacturers), China (83), and the UK (67). Smaller players include Japan (18), Germany (16), France (11), the Netherlands (8), Canada (9), (Taiwan (7), Switzerland (5) and South Korea (4).
Figure 6: Manufacturers of consumer connectable products by country of origin (n=394 manufacturers)
Size of manufacturers of consumer connectable products
As shown in Figures 5 and 6, the market is dominated by large players: 37% of the companies in our dataset were large businesses with more than 250 employees; 21% were medium-sized businesses with 50-249 employees; 20% were small businesses with 10-49 employees, and 8% were micro businesses with fewer than ten employees. It was not possible to find information on the number of employees for the remaining 14% of companies.
The turnover data reflects this trend. 29% of the companies in our dataset had a turnover of over GBP 50 million; 15% had a turnover between 10 and 50 million; and 22% had a turnover of up to GBP 10 million. It was not possible to find information on turnover for the remaining 34% of companies. It is worth noting that the missing data was not random. In particular, a relatively larger share of the missing data came from China: 35% of the companies we did not find turnover data from were headquartered in China – 10% more than in the whole sample.
Figure 7: Manufacturers of consumer connectable products, by size (n=394)
| Micro: 1-9 employees | 8% |
| Small 10-49 employees | 20% |
| Medium: 50-249 employees | 21% |
| Large: 250+ employees | 37% |
| Data unavailable | 14% |
Figure 8: Manufacturers of consumer connectable products, by turnover (n=394)
| Up to £10m | 22% |
| £10m - £50m | 15% |
| More than £50m | 29% |
| Data unavailable | 34% |
Routes to market
Figure 7 shows where these manufacturers sell their products. Because some manufacturers manufacture products for more than one brand, and because they sometimes use different routes for their different brands the graph shows the statistics for the population of brands (n=416), not manufacturers. Note, too, that manufacturers usually use more than one route to the market. The overwhelming majority of brands are sold online: 88% of brands were sold on at least one online third-party marketplace like Amazon or ebay; 72% were also sold on companies’ own websites. The importance of online third-party marketplaces was confirmed in the CATI survey: 68% of manufacturers consulted as part of the telephone interviews (21/31) sold their products on an online third-party marketplace; 74% of manufacturers (23/31) sold them on their own website. For the time being, however, the online market has not crowded out the physical retail market. Almost half of the brands in our dataset (45%) and 74% of the manufacturers we telephoned (23/31) sold their consumer connectable products in physical shops such as Currys or Argos.
The least common route to market was company’s own physical shops. Just 9% of the brands in our desk research dataset and a fifth of the companies consulted through the CATI survey (5/31) maintain their own physical shops. Typically, these were large, global brands such as Apple, Bang & Olufson, Dyson, Nespresso, Samsung, and Siemens. As the CATI survey consulted a higher share of larger manufacturers it showed a relatively larger share of manufacturers who had their own in-person shops. While data was not collected on sales in the online and the offline market, the fact that many small and medium-sized manufacturers opted not to enter the retail market indicates that the offline market is less profitable than the online market. In-person shops may, however, serve other purposes, such as brand recognition, customer experience and trust.
Figure 9: Brands of consumer connectable products by routes to market (n=416 brands)
| Routes to market | Yes | No | Data unavailable |
|---|---|---|---|
| Own physical shops | 9% | 89% | 2% |
| Physical shops | 45% | 53% | 2% |
| Own online shops | 72% | 26% | 2% |
| Third party online Marketplaces | 88% | 9% | 2% |
The routes to market chosen by manufacturers also vary based on the types of products sold. In the technical report, we show the routes to market for each product type. In particular, physical shops were far more common for some products than others: All of the service and care products and all tablets and e-readers mapped in our dataset, as well as 84% of kitchen appliances, 83% of audio devices were sold in physical shops such as Currys, or Argos. Similarly, some types of products were more likely to be sold in a company’s own physical shop. This was particularly true for technical devices: 38% of mobile devices, 25% of heating devices, and 18% of home appliances were sold in companies’ own physical shops.
Challenges in securing the data
Carrying out the desk research on these products, we faced a number of challenges. First, it was often difficult to determine whether a given consumer connectable product was in scope. The research was restricted to manufacturers who will need to comply with the cyber security requirements stipulated in the PSTI Regulations 2023. The word ‘smart’ or ‘connectable’ was not always a reliable indicator of whether a product was in scope. For instance, not every ‘smart treadmill’ can be connected to the internet, or to a phone. In addition, many websites of IoT devices do not disclose shipping information until the last step of a purchase and sometimes require registration, making it difficult to determine whether the products would be available in the UK. Moreover, a number of manufacturers in the original datasets were found to be industrial IoT manufacturers, component/part manufacturers, or even consultancies with expertise in IoT product development. These were excluded from the dataset.
At the product level, there is also limited data available on the number of products sold by each manufacturer in the UK and no reliable estimates across the market as a whole. This is further exacerbated by the role of online third-party marketplaces, which provide access to the market for a significant array of ‘smart’ products.
Second, it was often difficult to find the manufacturer. While most websites disclosed information on the company behind their products, some did not. In some cases, additional research led to Chinese manufacturers, but that information was often difficult to verify. Names of Chinese manufacturers, in particular, were often similar, raising questions on whether they were the same entities. Even in cases where it was not possible to find the name of a company, the legal role of that company was not always provided, making it difficult to understand whether it was a manufacturer, or merely a seller or a distributor. Initially, we attempted to find factory locations. Because this data was almost never disclosed, we removed this variable. Furthermore, the complexity of corporate structures often made it difficult to determine which branch, or division of a manufacturer was responsible for complying with the PSTI Regulations.
Third, finding turnover and employee data was not always possible. Here, the reliability of the data depends on the origin and size of the manufacturers. For UK-based companies, Companies House information allowed us to find reliable numbers. Similarly, large international companies tend to publish reliable turnover data in their annual reports. Both sources provided us with reliable data. In many cases, however, reliable estimates were not available. For smaller international companies, we often relied on websites collecting finance data on different companies. In some cases, various websites provided conflicting information about a company’s turnover. In other cases, we found no information at all.
3.2 Market Dynamics
The market for IoT devices is on the rise. According to data from Statista, the UK IoT market is expected to reach GBP 24.74 billion by the end of 2024. At an estimated annual growth rate of 11.8%, the UK IoT market is expected to reach GBP 38.65 billion by 2028.[footnote 7] These developments reflect a global trend: worldwide, the IoT market is expected to reach GBP 1,100.72 billion by the end of the year. At an estimated annual growth rate of 12.57%, the global IoT market is expected to reach a staggering GBP 1,767.35 billion by 2028.[footnote 8]
While the overall UK IoT market is growing, players are entering and exiting at a fast pace. Many of the companies compiled by Copper Horse in the autumn of 2023 are either no longer manufacturing consumer connectable products in early 2024 or they are not available in the UK, showing a market in flux. Manufacturers in our telephone interviews noted that the consumer connectable market was a diffult market. In some areas, sales are declining, and there are indications of oversaturated markets and/or dominant manufacturers for some categories of consumer connectable products (e.g. smart cameras and smart watches). This is also reflected by statements from companies who have left the consumer connectable products market. For instance, in its Fiscal Year 2023 Results, Fossil cited low and declining sales as a reason to exit the smart watch market in 2024.[footnote 9] Low sales have reportedly also reduced the market for large appliances (which includes ‘smart’ freezers, ovens, dishwashers etc.) According to data from the Association of Manufacturers of Domestic Appliances (AMDEA), the large appliances marked dropped 11% in 2023, and is expected to continue to fall in 2024.[footnote 10]
Another challenge continues to be the UK’s departure from the single European market. Through the CATI survey, representatives from five large consumer connectable product manufacturers reported that Brexit had challenged their business operations. Some of these challenges relate to marketing. For instance, one company reported that it had to separate their UK marketing from their EU marketing in response to Brexit.
However, another more substantive challenge relates to regulatory alignment. Manufacturers reported that complying with UK regulation, as well as EU regulation takes time and adds considerable costs without offering significant benefit from a consumer perspective. Ultimately, the cost associated with doing business in the UK after Brexit led at least one company in our sample to streamline some of their product portfolio.
Looking ahead, companies see risks related to the prospect of increasingly diverging regulations, including any divergence brought by the EU Cyber Resilience Act (which is still under negotiation). These issues are not confined to IoT companies – according to December 2023 research by the BBC’s Insights Unit, almost two thirds of UK firms (n=733) said that trading with the EU had become more difficult than it was a year ago.[footnote 11]
In addition to the high levels of turnover in the IoT market and continued issues around Brexit, the market is also seeing developments in the origin of smart products. In particular, a large, and growing share of IoT products sold in the UK come from China. This is true for the majority of low-cost consumer connectable products sold on Amazon. In addition, relatively large shares of consumer connectable products in the areas of service and care, tablets and mobile devices, home appliances, smart home devices, and leisure and hobby products are manufactured in China. In addition to brands that are transparently manufactured in China, our research found many brands that do not publicise the Chinese origins or Original Equipment Manufacturers (OEM) of their products. For instance, the manufacturer Havit (Guangzhou Havit Technology Co., LTD), which itself markets two smart product brands, also provides an OEM / ODM (Original Design Manufacturer) service to more than 35 companies globally, including many that are present on the UK market such as Polaroid, Lidl, Aldi, Hema and Costco.[footnote 12] This also illustrates the complexity of modern, global supply and value chains.
In some product categories, the top hits on Amazon.co.uk led to brands that were not clearly linked to any manufacturer. For many of these, careful searches revealed Chinese manufacturers, parent companies, sellers, or distributors. This lack of transparency was particularly notable in the area of security cameras, where English-sounding names were used to disguise products of Chinese origin. In addition, recent years have seen a number of Chinese acquisitions of IoT manufacturers, including long-standing European companies, such as the 2022 acquisition of Suunto by Lieshing[footnote 13], or acquisitions of larger shares of IoT companies.
The increasing importance of Chinese products also reflects a broader trend. Fuelled by investments and advancements in 5G technologies, artificial intelligence, and smart cities, China’s position in the global IoT market is strong, and poised to grow. Between 2024 and 2028, the Chinese IoT market is projected to grow at a rate of 13.5%.[footnote 14] According to estimates, it will surpass the United States by 2027, and will reach a market volume of USD 290.80 billion by 2028.[footnote 15]
The growing number of cyber attacks and the sensitive nature of the information that can be accessed through consumer connectable products (including, for instance, audio data, video footage, data on movement, or credit card information) should make cyber security and the regulation of smart devices a top priority for businesses and governments.[footnote 16]
4. Analysis of PSTI awareness, compliance and impacts
Triangulating the data from the CATI survey, the desk research and the qualitative interviews, this section presents an analysis manufacturer awareness of and compliance with the PSTI Act 2022 and the PSTI Regulations 2023, as well as other related standards. It also summarises evidence on the anticipated economic, social and/or environmental impacts of the PSTI regime.
4.1 Awareness of the PSTI regime
The awareness of manufacturers of the PSTI Act 2022, the PSTI Regulations 2023 and their provisions was primarily examined through the CATI survey conducted with manufacturers of consumer connectable products. This was supplemented by in-depth qualitative interviews with manufacturers and representatives of industry.
While the total number of manufacturers that participated in the CATI survey does not allow for robust extrapolation to the entire population of consumer connectable product manufacturers, this sample is clearly conscious of the introduction of cyber security regulations in the UK market: 91% (30 of 33 respondents) reported being aware of relevant regulations, while 56% specifically mentioned the ‘PSTI’ and 17% noted the April 2024 entry into force unprompted.
When prompted with a list of specific regulations, including the PSTI Act 2022, the PSTI Regulations 2023, ETSI EN 303 645 and ISO/IEC 29147: 2018 on vulnerability disclosure, the awareness levels of manufacturers reduced slightly, but remained strong. As illustrated in the below figure, all the regulations and standards were known by at least 70% of respondents. Awareness was highest regarding the ETSI standard (88%), while 79% were aware of the PSTI Regulations and 73% were aware of the PSTI Act. Only two manufacturers were not aware of any of these core regulations and standards.
Figure 10: Awareness of specific regulations and standards (Question 3, Base: 33)
| PSTI Act (n=24) | 73% |
| PSTI Regulations 2023 (n=26) | 79% |
| ETSI EN 303 645 (n=29) | 88% |
| ISO/IEC 29147:2018 (n=23) | 70% |
| I am not aware of any of these regulations or standards (n=2) | 6% |
Looking in more detail at the specific provisions of the PSTI Act and Regulations, including the three security requirements, most manufacturers (76%, 25 of 33) said that they were fully aware of the specific provisions, with a further four partially aware. The remaining four manufacturers were ‘not aware at all’.
Considering differences across manufacturers, industry interviewees noted the possible impact of manufacturer size on awareness levels, stating that smaller companies often have fewer resources available to proactively track regulatory developments, engage with Government (e.g. directly or through consultations) or participate in industry groups. However, due to the small sample size, the data does not provide any indications whether and to what extent business demography factors, such as manufacturer size or location, have an impact on awareness levels. There were also no indications that the lack of industry engagement in the CATI survey stems from a lack of awareness of the PSTI Act and Regulations.
Beyond the core regulations and standards noted above, respondents across both the CATI survey and the qualitative interviews highlighted awareness of other existing or proposed cyber security-related legislation. The following UK and EU legislative developments were raised:
-
Proposal for a Regulation on horizontal cybersecurity requirements for products with digital elements (also known as the Cyber Resilience Act, CRA). Published in September 2022, the proposed legislation, which will be applicable across all EU Member States, aims to create conditions for the development of more secure products and greater consumer awareness. As of March 2024, the CRA remains under negotiation.
-
Delegated Act to the Radio Equipment Directive. Published in October 2021, the delegated act established new legal requirements for the implementation of cybersecurity safeguards in connected products. The delegated act was originally scheduled for enforcement in August 2024; however, as highlighted by interviewees who will be required to adhere to both the delegated act and the PSTI legal regime, the entry into force has been delayed until August 2025 due primarily to the time required to prepare harmonised standards supporting the legislative amendment.[footnote 17]
-
Certain types of manufacturers, such as those that are also telecommunications service providers, also highlighted other legislation that introduces cyber security requirements (albeit not for consumer products). These include the UK Telecommunications (Security) Act 2021 and EU Directive 2022/2555 on measures for a high common level of cybersecurity (NIS 2 Directive).
The impact of these interrelated laws on manufacturer compliance are examined further in section 4.2.
In addition to ascertaining awareness levels amongst manufacturers, the research investigated the mechanisms by which businesses became aware of the PSTI regulatory regime. For manufacturers at least partially aware of the new regulations, the most likely source of this awareness was industry or trade bodies (48%). After some margin, the second most common source of awareness was public Government consultations (28%), followed by internal legal, compliance or product security teams (21%). These data are illustrated in the below Figure.
A large proportion also mentioned ‘other’ sources (45%). These alternative sources included: partner organisations, such as distributors, importers and laboratories; LinkedIn and in-person networking events; EU Parliament discussions; customers (i.e. retailers) and consumer organisations (e.g. Which).
In terms of under-utilised mechanisms, respondents report low levels of proactive tracking of cyber security or trade legislation (e.g. through internet alerts) (7%), as well as engaging with past government research (3%) or communicating directly with Government (14%).
Figure 11: Sources of awareness of new regulations (Question 12, Base: 29, multiple responses possible)
| Industry trade/membership body (n=14) | 48% |
| Public Consultations, Gov.uk website or cal for views (n=8) | 28% |
| Internal legal, compliance or product security teams (n=6) | 21% |
| From others in the industry (n=5) | 17% |
| Media, press releases or communications (n=5) | 17% |
| Direct engagement with Government (n=4) | 14% |
| Engagement with standards bodies (n=4) | 14% |
| Proactive tracking of cyber security or trade legislation (n=2) | 7% |
| Previous research surveys conducted by government/third parties (n=1) | 3% |
| Other (n=13) | 45% |
Similarly, the most common mechanisms through which manufacturers will ensure awareness with any future regulations include 49% via industry or trade bodies (16/33), and 42% via UK Government public engagements (14/33).
4.2 Compliance with the PSTI regime
The CATI survey with manufacturers, complemented by desk research and in-depth qualitative interviews, examined compliance with the PSTI regime and its impacts.
Compliance context and challenges
Regarding compliance with the PSTI regime, a key finding from the research with manufacturers and industry representatives was that the security requirements themselves are generally technically straightforward to implement, with some exceptions related to the requirement on transparency on the minimum length of time for security updates. However, challenges related to the overarching regime have resulted in compliance processes that are more complex, uncertain and costly than anticipated.
The representatives of industry associations interviewed for this research strongly agree with the need to introduce baseline security requirements for consumer connectable products.[footnote 18] They also strongly appreciate the use of a phased approach to placing cyber security-related legal obligations on manufacturers – i.e. the initial introduction of three key cyber security requirements, in the context of the wider set of guidelines documented in the UK CoP and the ETSI standard.
However, manufacturers report experiencing the following challenges when implementing the legislation:
Product scope: Many stakeholders, across the CATI survey and the in-depth interviews, reported uncertainties regarding what products should be within scope. Key ‘grey areas’ highlighted by stakeholders include how to deal with: (i) products that connect to internet-connected devices via Bluetooth (e.g. the case of earbuds with or without multipoint connection[footnote 19]; and (ii) connectable products that are only sold B2B but are ultimately used by consumers in a given setting (e.g. manufacturers in the print device space[footnote 20]. In these instances, manufacturers report having to invest time liaising with industry associations, technical cyber security experts and others to determine whether their products are in scope, often without a clear conclusion.
In addition, while the Government’s 2021 response to the call for views presents an explanation of the rationale, some manufacturers report being unclear why desktop, laptop and tablet computers (that do not have the capability to connect to cellular networks) are excepted under Schedule 3 of the PSTI Regulations 2023.[footnote 21]
‘Information on minimum security update periods’: Considering the third security requirement, detailed in paragraph 3 of Schedule 1, manufacturers reported challenges indicating a minimum support period for each product, meaning the “minimum length of time, expressed as a period of time with an end date, for which security updates will be provided”. In particular, the complexity of modern supply chains contributes to this challenge; for instance, one manufacturer highlighted that it may be difficult to ensure support from suppliers (e.g. component manufacturers) for a named period of time.
Others noted the implications of differences in terminology between the PSTI Regulations 2023 and European legislation. While the PSTI regime requires both the period of time and an end date, the proposal for a Cyber Resilience Act only requires the end date (i.e. products shall be accompanied by information on “the type of technical security support offered by the manufacturer and until when it will be provided, at the very least until when users can expect to receive security updates”). The manufacturers interviewed for this research noted that the PSTI requirement is more difficult to establish as, from the consumer perspective, the period of time for which a product is supported will differ depending on the date of purchase.
Timelines for implementation: While the extensive policy work that led up to the adoption of the legislation (e.g. on the CoP and the ETSI standard) was acknowledged by manufacturers and industry associations, these stakeholders countered that, in practice, industry does not initiate compliance activities until the final legal text has been enacted. As such, while the PSTI Act was adopted in December 2022 and a full draft of the PSTI Regulations was published in April 2023 (thereby providing an initial implementation timeline of 12 months), the Regulations were signed into law on 14 September 2023.
Primarily due to the challenges of ensuring the compliance of stock that is already on the market (e.g. in the possession of retailers) but may not be sold by 29th April 2024, many respondents perceive that the timeline for implementation is insufficient.
Specifically, industry associations note the difference in terminology between the PSTI regime, which applies to products that are ‘made available’ in the UK, and other product safety legislation, which more commonly applies to products that are ‘placed on the market’. The reason for this, as detailed in the Government’s 2021 response to the call for views, was that consumer connectable products remain connected and compliance can change after entering the supply chain. However, when combined with the implementation timeline, industry understands that all consumer connectable products that are “currently in production or available for sale in stores and warehouses will need to demonstrate compliance in accordance with the new regime”[^22] by 29th April 2024.
Citing vast global supply chains within the production ecosystem, as well as long shipping timelines, some industry representatives say that this could lead to existing stock being scrapped or recycled. This perspective was supported by individual manufacturers that engaged in this research, who questioned how these requirements and statements of compliance can be retrospectively applied to products that are already in the supply chain and market.
Demonstrating compliance: Linked to the above point on timelines, manufacturers reported that they are “still consulting with [their] distributors and cyber security expert[s]”, as the requirements for the format and contents of the Statement of Compliance (SoC), while detailed in Schedule 4 of the PSTI Regulations 2023, are perceived to be unclear. For instance, while some manufacturers deem it sufficient to state that they are compliant, others are considering if they need to provide details or evidence of exactly how they comply.
“There are a number of industry stakeholder groups including retailers. One thing they are looking at is how the statement of compliance should look. As an industry, we feel it would be better if there were a standard format for the statement of compliance. But there is doubt as to who the statement of compliance is aimed at. If there is a standard way everybody knows what they are looking at. Unfortunately, legislation is very unclear on the format”.
Compliance levels
In this context, many respondents highlighted that ensuring compliance was still an ongoing process, although this varies depending on the requirement. As illustrated in the following figure, the second requirement, related to providing ‘Information on how to report security issues’, has been introduced for all products by the highest number of manufacturers consulted (58%, 19/33), closely followed by the provisions on passwords (52%, 17/33). Regarding ‘Information on minimum security update periods’, the number of manufacturers that have already introduced this requirement for all products drops to only 27% (9/33), with a higher proportion reporting that they intend to introduce the requirement within a certain time frame (39%, 13/33).
Figure 12: Compliance status for each of the three requirements (Question 6, Base: 33)
| Compliance status | Passwords | Public point of contact | Security updates |
|---|---|---|---|
| Introduced for all products | 52% | 58% | 27% |
| Introduced for some products | 12% | 0% | 6% |
| Looking to introduce within a certain time | 9% | 24% | 39% |
| Looking to introduce in the near future but not sure when | 12% | 18% | 21% |
| Not looking to introduce for some products | 3% | 3% | 3% |
| Not looking to introduce at all | 0% | 0% | 0% |
| This requirement is not relevant to us | 18% | 3% | 21% |
Positively, none of the manufacturers consulted stated that they are ‘Not looking to introduce the requirement at all’, while only one respondent for each requirement noted that they will not introduce the requirement for some products and around 20% of manufacturers responded that the requirements related to passwords and security updates were not relevant to their products. The reasons provided included:
- Passwords: As illustrated by the following manufacturer quotes, the primary reason was that the products do not use or store passwords and/or use other methods for authentication.
“We don’t set any passwords or store any passwords”.
“Never used passwords, we have another method. Already compliant connecting to back end services”.
- Information on minimum security update periods: Reasons raised by manufacturers indicated a lack of understanding of the requirement, tying into the abovementioned challenges. For instance, the reasons included not wanting to be ‘locked down’ to a minimum period and the intention to service products indefinitely. However, the law does not prevent manufacturers from providing support beyond the minimum support period.
“We are very transparent, never locked down to a minimum period, just pragmatic based on number of users using products. Products last a long time. Also, we provide care for over 7 years”.
“Our claim is to service products indefinitely. This also includes software updates. No exact end date. Over full life time”
Besides implementing the three security requirements, a key part of compliance is demonstrating compliance, including the requirement that all products will need to be accompanied by a Statement of Compliance (SoC). In this regard, manufacturers were asked how they intend to demonstrate compliance for each requirement.
Notwithstanding the abovementioned challenges related to the SoC, the most common response was to state that the manufacturer deems the product to be
compliant within the SoC. In addition, for the requirement on passwords, manufacturers highlighted work with internal/third-party testing or third-party compliance assessment companies and made direct reference to the provisions of ETSI EN 303 645. Responses on the information-related requirements focused on supplementing the SoC with publicly available information on points of contact, vulnerability disclosure processes and security updates. Across the manufacturers consulted, this information will be made available through websites, apps and product instruction manuals.
Specifically considering the SoC, manufacturers were asked whether they have been contacted by distributors or retailers asking for information on compliance or a SoC. Around 70% of manufacturers (23/33) have been contacted by distributors, including retailers, indicating that these stakeholders are generally aware of the legislation and the implications for products they sell or distribute. To illustrate, a selection of manufacturer responses is presented below:
Manufacturer responses on SoC development and deployment:
“We’ve had direct engagement with distributors and retailers planning what we are going to do. They will be able to access it and put it with their own needs”.
“All new products coming into the country will have [an SoC] already in a box. We are contacting the retailers to label packaging allowed by the regulation so we can retro-actively provide SoC to any stock they have got”.
“Normally when we do new products, with safety, we issue a Declaration of Conformity. Similar process”.
“We are working with cross industry groups to establish a working template of SoC, tick boxes, to integrate into our systems. We have already been doing this since the back end of last year trying to whittle down stock in the warehouse to reduce resource required for this work. We have the SoC built into this, so we can include it in our document bags. Just profiling what stock is in retailer or warehouses, and then we will create a plan for the resource to go in and rework the stock including the SoC as required”.
The results of the CATI survey were also validated through in-depth desk research to assess evidence of manufacturer compliance based on publicly available information. As illustrated in the below figures, this exercise generated mixed results regarding evidence of compliance[footnote 23] for each requirement across a sample of 70 manufacturers representing a balance of business sizes and locations of headquarters:
- Passwords: For the requirement on passwords, manufacturers are relatively evenly spread across the categories, with 15 of 70 companies (21%) considered to show strong signs of compliance, 17 (24%) were somewhat compliant, and 19 (27%) not compliant. Limited information was available on the approach of the remaining 19 (27%) companies to passwords.
Figure 13: Evidence of compliance with the PSTI security requirement on passwords (n=70)
| Passwords | Total |
|---|---|
| Compliant | 21% |
| Somewhat compliant | 24% |
| Not compliant | 27% |
| Information not available online | 27% |
- Information on how to report security issues: Most manufacturers reviewed (66%, 46/70) are not compliant with the provisions of this requirement, while just over a quarter are considered to be compliant (26%, 18/70). Given the public nature of this requirement, which requires manufacturers to provide information to consumers (on point(s) of contact for reporting security issues and acknowledgement/updates on security reports), only two manufacturers (3%) were identified where not enough information was available to make a judgement. Most commonly, manufacturers were assessed to be non-compliant as they do not provide specific contact details for security reporting. As discussed through the below table, these results mirror the global findings of 2022 research conducted on the state of vulnerability disclosure policy (VDP) usage by the IoT Security Foundation (IoTSF) and Copper Horse, which found that 73% of companies reviewed did not have a VDP. However, a ‘dip test’ conducted on the UK market in the same research revealed contrasting results.
Figure 14: Evidence of compliance with the PSTI security requirement on how to report security issues (n=70)
| Reporting security issues | Total |
|---|---|
| Compliant | 26% |
| Somewhat compliant | 6% |
| Not compliant | 66% |
| Information not available online | 3% |
Table 2: Overview of IoTSF/Copper Horse research on vulnerability disclosure
The State of Vulnerability Disclosure Policy (VDP) Usage in Global Consumer IoT in 2022
Since 2018, IoTSF and Copper Horse have published annual research on the adoption of vulnerability disclosure practices by connected device manufacturers worldwide. Specifically, this research assesses whether such manufacturers have a publicly available VDP and, if yes, whether they provide key information on the timelines for acknowledgement and resolution of reported issues.
Globally, the research has found low, but increasing, levels of VDP adoption by the reviewed companies since 2018, rising from 9.7% in 2018 to 31.08% (101/332) in 2023. However, in 2023, only 9.42% (42/446) of the sample were considered to be compliant with the PSTI requirements on providing information on how to report security issues.
In 2022, IoTSF and Copper Horse reviewed 17 manufacturers of popular devices sold by retailers selling in the UK. This ‘dip test’ found much higher levels of adoption: 70.59% (12/17) of reviewed companies had a VDP, with 41.18% (7/17) of those including information about the timeline, thus indicating compliance with regulatory requirements under the PSTI regime.
While it is not possible to extrapolate to the entire population of manufacturers selling to the UK market based on these data, the findings of both the desk research conducted for this research and the IoTSF/Copper Horse research indicate that, while there is still much room to improve, the UK market has higher levels of VDP usage compared to the situation worldwide.
- Information on minimum security update periods: Limited evidence of manufacturer compliance was available for this security requirement. In fact, a total of 57 of 70 manufacturers (81%) were either considered to be non-compliant (33%, 23/70) or that there was not enough information available online to make a suitably informed judgement (49%, 34/70).
Figure 15: Evidence of compliance with the PSTI security requirement on information on minimum security update periods (n=70)
| Compliance with minimum security update periods | Total |
|---|---|
| Compliant | 9% |
| Somewhat compliant | 10% |
| Not compliant | 33% |
| Information not available online | 49% |
Figure 16: Evidence of compliance with each PSTI security requirement (n=70)
| PSTI security requirement | Compliant | Somewhat compliant | Not compliant | Information not available online |
|---|---|---|---|---|
| Passwords | 21% | 24% | 27% | 27% |
| How to report security issues | 26% | 6% | 66% | 3% |
| Minimum security update periods | 9% | 10% | 33% | 49% |
The CATI survey also asked manufacturers how likely they are to be compliant with each requirement by 29th April 2024. Most manufacturers consider that they are ‘Very likely’ to be compliant with each of the requirements. As illustrated below, this number is highest for the requirement on ‘Information on how to report security issues’ – 28 of 33 (85%) manufacturers are very likely to be compliant in time. This figure reduces to 25 (76%) for the requirement on passwords and 21 (64%) for the requirement on security updates, although a further eight are ‘Quite likely’ to be compliant with this requirement in time.
Figure 17: Likelihood of being compliant with each regulation by 29th April 2024 (Question 14, Base: 33)
| Regulation | Very likely | Likely | Unlikely | Very unlikely | Don’t know | |
|---|---|---|---|---|---|---|
| Passwords are unique, not guessable or based on incremental counters | 76% | 9% | 0% | 3% | 12% | |
| The manufacturer provides a public point of contact to enable security issues to be reported | 85% | 0% | 3% | 6% | 6% | |
| Information on the minimum length of time for which security updates will be provided must be made available | 64% | 24% | 6% | 0% | 6% |
It is not possible to disaggregate the results by different groups of manufacturers (e.g. by manufacturer size or location of headquarters) due to the small sample size.
Compliance activities
The main activities that manufacturers have taken or plan to take to ensure compliance with the legislation are presented in the below figure. The most common activity was to familiarise themselves with the legislation (87%, 27/31), followed by preparing a self-declaration/assessment of compliance (81%, 25/31). At least 80% of manufacturers that expect to be compliant by the 29 April 2024 say they have undertaken each of these or plan to.
Indicating the impact of the abovementioned challenges, around two thirds of manufacturers have obtained legal advice (21/31), just over half have conducted or plan to conduct third-party testing (16/31), while up to 42% (13/31) have undertaken or will seek to undertake a formal third-party compliance assessment. Just under half will amend compliance information at the point of sale (15/31).
Only around 20% of manufacturers have already or plan to take steps regarding the re-design of physical labelling.
Figure 18: Steps that manufacturers have already taken or plan to take to ensure they comply (Question 16, Base: 31)
| Familiarisation with the legislation (n=27) | 87% |
| Self-declaration/assessment of compliance of consumer connectable products (n=25) | 81% |
| Obtain legal advice (n=21) | 68% |
| Third party testing of compliance (n=16) | 52% |
| Amend compliance information at point of sale (n=15) | 48% |
| Send products to a third party to undertake a compliance assessment (n=13) | 42% |
| Re-design physical labelling (n=7) | 23% |
| Other (n=5) | 16% |
The interviewed and surveyed manufacturers noted that, while difficult to quantify, they have and will incur additional costs due to these compliance activities. In fact, as illustrated in the below figure, ‘Additional/increased costs’ were flagged as a key impact of compliance by 81% (25/31) of manufacturers. These comprise costs associated with familiarisation with the legislation, obtaining legal advice, conducting third-party testing or compliance assessment, preparing the compliance documentation and appending that to the product (e.g. through amended product labelling).
Further manufacturer-level impacts that would also impact costs include:
-
Staffing costs: 16 of 31 manufacturers (52%) stated that they would need to upskill/train staff, while seven manufacturers (23%) reported that they would need to recruit additional staff. For instance, one manufacturer noted that, concerning the requirement to have at least one point of contact, they will set up a specialised means of contact, which will go to a customer service ticket that will be directed to and serviced by a dedicated member of staff.
-
Dealing with non-compliant stock: A small number of manufacturers anticipate impacts resulting from the challenges with stock that is downstream of the manufacturer in the supply chain and is non-compliant (in relation to the substantive security requirements and/or the administrative requirements, such as the SoC). These challenges will necessitate that the manufacturers sell non-compliant stock to non-UK markets (23%, 7/31) or dispose of it (19%, 6/31). For instance, one manufacturer stated that the “Biggest concern or impact is dumping of non-compliant stock. Would have to change the plugs for sale to another market, we will not do this”, while another will be “[pushing] to sell stock before the deadline”.
Figure 19: Cost impacts of the PSTI legal regime at the manufacturer-level (Question 17, Base: 31)
| Additional/increased costs (n=25) | 81% |
| A need to upskill/train current staff (n=16) | 52% |
| Selling non-compliant products to non-UK markets (n=7) | 23% |
| Needing to dispose of non-UK stock (n=6) | 19% |
In most cases it seems manufacturers will be taking a mixed approach to managing these increased costs, absorbing some costs themselves (33%, 11/33) and passing some costs on to consumers (52%, 17/33) and/or retailers (27%, 9/33). Only three manufacturers reported that they will pass all costs on to retailers or consumers (9%), with nine stating that they will absorb all costs themselves (27%).
Compliance with ETSI standard EN 303 645
Beyond compliance with the PSTI regime, manufacturers were also asked whether and to what extent their consumer connectable products comply with the additional ten provisions detailed in ETSI standard EN 303 645 on cyber security consumer internet of things devices. The provisions of the ETSI standard and their associated reference numbers, excluding those covered by the PSTI regime, are listed in the below table and indicated in the text.
In general, the surveyed manufacturers reported relatively strong implementation of the ETSI standard, with all provisions bar one implemented by more than 50% of manufacturers. Of the ten provisions not covered by the PSTI regime, devices being easy to install and maintain (provision 5.12) is most likely to have been introduced by manufacturers across all their products (85%, 28/33 manufacturers).
The provision that manufacturers are next most likely to be compliant with across all their consumer connectable products is that devices and related services shall be resilient to outages (provision 5.9). This provision has already been introduced across all products by just over two thirds of manufacturers (73%, 24/33). Similar proportions have also introduced allowing users to easily delete user data (provision 5.11), ensuring the security of personal data (provision 5.8), ensuring the integrity of device software (provision 5.7) (all 67%), and communicating securely using best practice cryptography (provision 5.5) (64%).
The provisions least likely to have been introduced across all products are that devices shall validate input data (provision 5.13) (55%), that telemetry data from devices and services shall be examined to identify and address security anomalies
(provision 5.10) (52%), and that devices shall securely store sensitive security parameters (provision 5.4) (48%). Around half of manufacturers say these provisions have been introduced across all their products.
Where manufacturers have not introduced these provisions across all products, it is most likely to be because they say the requirement is not considered relevant to them. Between 12% and 36% of respondents stated that the requirement is not relevant to their products; the second most common response option across all ETSI requirements. While a detailed table of the reasons given by manufacturers is presented in Annex 2, example responses related to the provisions least likely to have been introduced are presented in the below table.
Table 3: Reasons given by manufacturers for certain ETSI provisions being considered not relevant
| Reasons given for certain ETSI provisions being considered not relevant | |
| Devices shall validate input data (5.13) | Data collected by sensors. Third-party not relevant to us. No data input |
| Telemetry data from devices and services shall be examined to identify and address security anomalies (5.10) | Not sure about cameras we sell. Probably do but not sure. Device not holding any data. |
| Devices shall securely store sensitive security parameters (5.4) | Our devices don’t store this. We do not store sensitive data in the device. The device to send telemetry data only. Our tracking devices don’t store any data, collected data is stored safely on an AWS server. |
The full findings on self-reported compliance with the provisions of the ETSI standard are presented in the below table.
Table 4: Whether or not each cyber security provision from the ETSI standard has been introduced for manufacturers’ consumer connectable products (Question 7, Base: 33)
| Introduced for all products | Introduced for some Products | Looking to introduce within a certain time | Looking to introduce in the near future but not sure when | Not looking to introduce for some products | Not looking to introduce at all | Not relevant | |
| Devices shall be easy to install and maintain (5.12) | 85% | 3% | 0% | 3% | 0% | 0% | 12% |
| Devices and related services shall be resilient to outages (5.9) | 73% | 9% | 3% | 3% | 3% | 0% | 18% |
| The integrity of device software shall be ensured (5.7) | 67% | 15% | 3% | 9% | 6% | 0% | 15% |
| Devices shall allow users to easily delete user data (5.11) | 67% | 12% | 3% | 3% | 0% | 0% | 27% |
| Devices shall ensure the security of personal data (5.8) | 67% | 9% | 6% | 3% | 3% | 0% | 21% |
| Devices shall communicate securely Using best practice cryptography (5.5) | 64% | 15% | 3% | 3% | 6% | 0% | 21% |
| The exposed attack surfaces of the device shall be minimised (5.6) | 58% | 15% | 3% | 9% | 3% | 0% | 21% |
| Devices shall validate input data (5.13) | 55% | 6% | 0% | 6% | 3% | 0% | 36% |
| Telemetry data from devices and services shall be examined to identify and address security anomalies (5.10) | 52% | 9% | 6% | 9% | 6% | 0% | 33% |
| Devices shall securely store sensitive security parameters (5.4) | 48% | 15% | 12% | 6% | 6% | 0% | 27% |
Anticipated economic, social and environmental impacts
As noted above, the activities necessary to implement the PSTI legislation will have firm-level impacts on manufacturers, including costs associated with staffing, dealing with non-compliant stock, obtaining legal advice and others. However, these activities are also likely to have positive economic impacts for manufacturers, as well as wider economic, social and environmental impacts.
At the manufacturer level, a range of positive impacts were tested through the CATI survey. As illustrated in the below figure, around half of manufacturers (52%, 16/31) anticipated that the implementation of the PSTI regime will result in improved consumer confidence in products. Over a third of manufacturers think the legislation will improve their reputation (12/31) and improve product security, including reducing product cyber security vulnerabilities (11/31), while 29% (9/31) believe it will improve customer satisfaction and loyalty.
Figure 20: Positive manufacturer impacts resulting from compliance with the PSTI regime (Question 17, Base: 31)
| Improved consumer confidence in products (n=16) | 52% |
| Improved reputation (n-12) | 39% |
| Improved product security (n=11) | 35% |
| Reduction in product cyber security vulnerabilities (n=11) | 35% |
| Increased customer satisfaction/loyalty (n=9) | 29% |
In relation to the impact of the legislation on reducing cyber security vulnerabilities with consumer connectable products, the CATI survey also examined the level of manufacturer concern with regard to cyber attacks. As illustrated below, it found that nearly half of manufacturers (48%, 16/33) were ‘Quite concerned’ (39%, 13/33) or ‘Very concerned’ (9%, 3/33) about cyber attacks on their products. These stakeholders highlighted significant business risks (e.g. from reputation damage, theft of business data) and different types of negative imapcts on consumers (e.g. privacy issues, loss of consumer trust and confidence in connectable devices). A selection of manufacturer comments are now provided:
“Consumers and businesses are a nice target for bad actors, and with social engineering activities that they will engage in, consumers might not always be aware of what is being attempted”.
“Lots of reputation, damages for the customer, mostly. Also, to some degree liability. Trust in and security of our devices”.
This illustrates the need and scope for measures to improve the cyber security of consumer connectable products, for both manufacturers and consumers, and the potential economic and social impacts such improvments can have in terms of reduced exposure to these risks and cost savings.
Figure 21: How concerned manufacturers are about cyber-attacks on their products (Question 9, Base: 33)
| Not concerned at all (n=12) | 36% |
| Quite concerned (n=13) | 39% |
| Very concerned (n=3) | 9% |
| Don’t know (n=5) | 15% |
Beyond these implications, manufacturers raised broader concerns regarding the possible negative impact on industry innovation and competitiveness. These stakeholders and other industry representatives stated that any time, effort and costs required to implement the legislation and ensure compliance of products will likely have knock-on effects of reduced investment in research and innovation.
In addition, while the EU CRA is still under negotiation, the possibility of regulatory divergence between the UK and EU markets (no matter how minor), as well as other jurisdictions such as the US, could exacerbate this challenge by further increasing compliance costs for manufacturers of consumer connectable products.
According to manufacturers and industry associations, this could impact the attractiveness of the UK market to innovative companies and products, as well as the global competitiveness of UK-based companies, who may be required to comply with slightly divergent legislation across different jurisdictions. While anecdotal at this stage, Chapter 3 of this report highlighted examples of companies exiting the UK market for consumer connectable products in recent years.
Furthermore, a lack of competition within the market could impact consumer choice.
On top of these economic and social impacts, the manufacturers and industry associations consulted for this research highlighted key negative environmental impacts that could stem from certain regulatory decisions. Industry stakeholders of all types have challenged the timelines established for implementation and entry into force of the legislation, with a prominent potential impact being the need to dispose of existing stock that cannot be sold or brought into compliance within the timeframe. Complementary to this point, other manufacturers raised questions regarding the possible environmental impact of including printed paper Statements of Compliance alongside each product, rather than digital versions of the SoC.
5. Conclusions
With the PSTI Regulations 2023 coming into force on 29th April 2024, this research aimed to: (i) map and analyse the population of manufacturers that will be subject to the PSTI regime; and (ii) analyse the compliance levels of these manufacturers with the cyber security requirements stipulated in the legislation, supplemented by evidence on awareness of the rules and anticipated impacts.
While it has been possible to generate useful insights related to both objectives, a key overarching conclusion is that conducting research in this field continues to be challenging. Most prominently, as experienced in previous UK Government research exercises[footnote 24], relevant manufacturers were: (i) hard to reach due to a lack of available and accessible contact information; and/or (ii) unwilling or reluctant to participate due to concerns about potential repercussions if they indicated a lack of compliance. This being despite reassurances to the contrary and the implementation of extensive mitigation measures.
Moreover, developing a comprehensive and accurate assessment of the UK market for consumer connectable products is challenging given the core characteristics of the market:
-
Importance of e-commerce – the most common route to market – and the role of online third-party marketplaces, which allow for the circulation of a substantial number of consumer connectable products with limited or no information on the responsible seller, let alone the manufacturer.
-
Large proportion of manufacturers mapped are based outside the UK (86%), with the US (28%) and China (25%) representing the biggest proportions.
-
Complex corporate structures, supply chains and value chains, which result in the roles of individual companies in the market being unclear.
Therefore, considering the first research objective, the dataset generated through this research is the most comprehensive and tailored to date; however, it does not map the entire population of consumer connectable products sold in the UK, while important caveats should be considered when reviewing company data (e.g. on turnover, company size).
In this context, conclusions on compliance levels are based on a combination of: (i) results from a quantitative ‘CATI’ survey with 33 manufacturers; (ii) supplementary desk research on 70 companies; and (iii) in-depth qualitative interviews with manufacturers and industry associations. While the lack of manufacturer engagement affects the generalisability of the CATI survey findings and the ability to disaggregate by key variables (e.g. company size, country of HQ, etc.), the triangulation of the results provide useful indications of the status quo regarding manufacturer compliance with the PSTI Regulations 2023.
Overall, the research found relatively high levels of awareness of the PSTI legal regime among manufacturers: 91% (30/33) reported being generally aware of relevant regulations in the field, while 79% reported being specifically aware of the PSTI Regulations 2023. Industry bodies and UK Government public engagements were and will continue to be the most commonly used sources of awareness, while prior governmental research and proactive tracking (e.g. through internet alerts) appear to be under-utilised.
While there is regulatory awareness amongst the population of manufacturers surveyed, ensuring compliance was found to be an ongoing process at the time of the research, particularly regarding information on minimum security update periods:
-
52% of manufacturers report being fully compliant with the requirement to introduce unique passwords, while the desk research identified some evidence of compliance for 45% of manufacturers.
-
58% report being fully compliant with the requirements related to information on how to report security issues, while the desk research identified some evidence of compliance for 32% of manufacturers.
-
27% report being fully compliant with the requirement to provide information on the minimum length of time for which security updates are available. The desk research found some evidence of compliance for only 19% of manufacturers.
But, high levels of compliance are anticipated prior to the entry into force of the legislation: for all three requirements, at least 85% of manufacturers stated that they are ‘Very’ or ‘Quite’ likely to be compliant by 29th April 2024, while none of the manufacturers are ‘Not looking to introduce the requirement at all’.
Although anticipated compliance is high, manufacturers and industry bodies highlighted challenges related to the overarching regime that have resulted in more complex, uncertain and costly compliance processes. Specifically, these relate to the amount of time available for implementation, as well as a lack of clarity and detailed guidance on which products are in scope, the requirement on information on minimum security update periods and how to demonstrate compliance. Manufacturers also stated concerns regarding the costs of compliance, in relation to the disposal of non-compliant products when the regulations come into effect, as well as the cost of the activities required to ensure compliance.
Manufacturers also continue to see Brexit as an obstacle: beyond general market impacts, companies stated concerns regarding the possibility of regulatory divergence between the UK and EU approaches to regulating the cyber security of consumer connectable products, as well as the secondary impacts of those differences (e.g. on costs, competitiveness, innovation). Most companies, however, were confident they would comply with all requirements by the 29th April 2024.
Besides the costs and negative impacts, manufacturers and consumers are expected to experience significant benefits as a result of the legislation. At the manufacturer level, these could include improved consumer confidence in products, reputation, product security, and customer satisfaction/loyalty, as well as reduced product cyber security vulnerabilities. Moreover, significant indirect benefits for both consumers and businesses can be expected through improved resilience to cyber attacks and reductions in the costs and impacts of cyber attacks.
Index of tables and figures
Tables
Table 1: Summary of policy actions leading to the adoption of the PSTI legal regime. (10)
Table 2: Overview of IoTSF/Copper Horse research on vulnerability disclosure (35)
Table 3: Reasons given by manufacturers for certain ETSI provisions being considered not relevant (40)
Table 4: Whether or not each cyber security provision from the ETSI standard has been introduced for manufacturers’ consumer connectable products (Question 7, Base: 33) (41)
Table 5: Product types, and countries of origin for each product (n=1024 products) (53)
Table 6: Employees and turnover data for each manufacturer (n=394 manufacturers) (54)
Table 7: Routes to the market for each brand (n=416 brands) (54)
Table 8: Whether or not each cyber security provision from the ETSI standard has been introduced for manufacturers’ consumer connectable products (Question 7, Base: 33) (79)
Figures
Figure 1: Compliance status for each of the three requirements (Question 6, Base: 33) (4)
Figure 2: Likelihood of being compliant with each security requirement by 29th April 2024 (Question 14, Base: 33) (6)
Figure 3: Consumer connectable products sold in the UK, by category (n=1024 products) (17)
Figure 4: Consumer connectable products sold in the UK, by country of origin (n=1024 products) (18)
Figure 5: Consumer connectable products sold in the UK, by category and country of origin (n=1024 products) (18)
Figure 6: Manufacturers of consumer connectable products by country of origin (n=394 manufacturers) (19)
Figure 7: Manufacturers of consumer connectable products, by size (n=394) (20)
Figure 8: Manufacturers of consumer connectable products, by turnover (n=394) (20)
Figure 9: Brands of consumer connectable products by routes to market (n=416 brands) (21)
Figure 10: Awareness of specific regulations and standards (Question 3, Base: 33) (25)
Figure 11: Sources of awareness of new regulations (Question 12, Base: 29, multiple responses possible) (27)
Figure 12: Compliance status for each of the three requirements (Question 6, Base: 33) (31)
Figure 13: Evidence of compliance with the PSTI security requirement on passwords (n=70) (34)
Figure 14: Evidence of compliance with the PSTI security requirement on how to report security issues (n=70) (35)
Figure 15: Evidence of compliance with the PSTI security requirement on information on minimum security update periods (n=70) (36)
Figure 16: Evidence of compliance with each PSTI security requirement (n=70) (36)
Figure 17: Likelihood of being compliant with each regulation by 29th April 2024 (Question 14, Base: 33) (37)
Figure 18: Steps that manufacturers have already taken or plan to take to ensure they comply (Question 16, Base: 31) (38)
Figure 19: Cost impacts of the PSTI legal regime at the manufacturer level (Question 17, Base: 31) (39)
Figure 20: Positive manufacturer impacts resulting from compliance with the PSTI regime (Question 17, Base: 31) (43)
Figure 21: How concerned manufacturers are about cyber-attacks on their products (Question 9, Base: 33) (44)
Figure 22: Brands sold on online third-party marketplaces (55)
Figure 23: Brands sold on companies’ own websites. (56)
Figure 24: Brands sold in physical shops (57)
Figure 25: Brands sold in companies’ own physical shops (57)
Figure 26: Whether company currently manufactures consumer connectable products that are sold in the UK, and/or has plans to do so (Question: S01, Base: 33, multiple choice question) (58)
Figure 27: Where company’s headquarters are based (Question S04, Base:33) (59)
Figure 28: Business size (Question S06, Base: 33) (59)
Figure 29: Business turnover (Question S07, Base: 33) (59)
Figure 30: Where consumer connectable products are sold in the UK (Question S02a, Bases: 31 and 12) (60)
Figure 31: Proportion of sales of consumer connectable products that are sold in the UK (Question 3, Base: 31) (61)
Figure 32: Awareness of any cyber-attacks on their products within the last 12 months (Question 8, Base:33) (61)
Figure 33: How concerned manufacturers are about cyber-attacks on their products (Question 9, Base: 33) (62)
Figure 34: Awareness of any cyber security regulations being introduced in the UK market (Question 1, Base: 33) (65)
Figure 35: Awareness of specific regulations and standards (Question 3, Base: 33) (67)
Figure 36: Awareness of when PSTI regulations will come into force (Question 5, Base: 26) (71)
Figure 37: Awareness of detailed description of the PTSI Act and Regulations (Question 11, Base: 33) (72)
Figure 38: Sources of awareness of new regulations (Question 12, Base: 29) (73)
Figure 39: Sources used to make themselves aware of new regulations (Question 13, Base: 33) (74)
Figure 40: Whether the requirements related to passwords have been introduced (Question 6, Base: 33) (75)
Figure 41: Whether the requirements related to the public point of contact have been introduced (Question 6, Base: 33) (76)
Figure 42:Whether the requirements related to security updates have been introduced (Question 6, Base: 33, multiple choice question) (77)
Figure 43: Likelihood of being compliant with each regulation by 29th April 2024 (Question 14, Base: 33) (82)
Figure 44: Steps that manufacturers have already taken or plan to take to ensure they comply (Question 16, Base: 31) (88)
Figure 45: Whether manufacturers have been contacted by distributors or retailers asking for information on compliance or a Statement of Compliance (Question 19a, Base: 33) (90)
Figure 46: Key impacts of compliance that manufacturers anticipate (Question 17, Base: 31) (93)
Figure 47: How manufacturers expect to manage increased costs as a result of the new regulations (Question 18, Base: 33) (94)
Annexes
The Annexes contain the following:
-
Bibliography – a list of sources reviewed and used within the research.
-
Market analysis: Supporting data – tables presenting data tables to illustrate the disaggregation of products, by manufacturer location of headquarters, by number of employees, turnover and routes to market.
-
CATI survey analysis – results from the CATI survey, by question.
Annex 1: Bibliography
-
Association of Manufacturers of Domestic Appliances (AMDEA). (2023). A Year in Review: 2023 report.
-
AMDEA and TechUK. (2024). Letter to the Government on the UK PSTI regime.
-
British Chambers of Commerce. (2023). “Brexit at three: Fresh trade challenges growing”
-
Centre for Strategy & Evaluation Services (CSES). (2020). Framing the Nature and Scale of Cyber Security Vulnerabilities within the Current Consumer IoT Landscape.
-
Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on measures for a high common level of cybersecurity across the Union, amending Regulation (EU) No 910/2014 and Directive (EU) 2018/1972, and repealing Directive (EU) 2016/1148 (NIS 2 Directive).
-
Daws, R. (2021). Kaspersky: Attacks on IoT devices double in a year. IoTnews.
-
European Telecommunications Standards Institute (ETSI). (2020). ETSI EN 303 645 V2.1.1 (2020-06), European Standard, Cyber; Cyber Security for Consumer Internet of Things: Baseline Requirements.
-
ETSI. (2020). ETSI TS 103 645 V2.1.2 (2020-06), Technical Specifications, Cyber; Cyber Security for Consumer Internet of Things: Baseline Requirements.
-
European Commission. (2021). Commission strengthens cybersecurity of wireless devices and products – Delegate Act to the Radio Equipment Directive.
-
European Commission. (2022). Proposal for a Regulation of the European Parliament and of the Council on horizontal cybersecurity requirements for products with digital elements and amending Regulation (EU) 2019/1020.
-
Frank-Keyes, J. (2023). Malware attacks on UK government devices up by 75 per cent, report reveals. Article in CITY A.M.
-
Fossil Group. (2024). Fossil Group, Inc. Reports Fourth Quarter and Fiscal Year 2023 Results.
-
Havit. (2023). Presentation about Havit.
-
IoT Security Foundation. (2023). The State of Vulnerability Disclosure Policy (VDP) Usage in Global Consumer IoT in 2022. A report prepared by Copper Horse Ltd. Published January 2023.
-
IoT Security Foundation. (2023). The State of Vulnerability Disclosure Policy (VDP) Usage in Global Consumer IoT in 2023. A report prepared by Copper Horse Ltd. Published October 2023.
-
Kaspersky. (2023). Press release: Kaspersky unveils an overview of IoT-related threats in 2023.
-
Laughlin, A. (2022). Smart products from the biggest tech brands easily hacked in Which? tests. Article in Which?
-
London Economics and YouGov. (2024). Consumer Survey on App Stores, Internet of Things (IoT), and Connected Places.
-
McKinsey. (2017). What’s new with the Internet of Things?
-
National Cyber Security Centre (NCSC). (2018) Secure by Default.
-
National Cyber Security Centre (NCSC). (2022) Device Security Guidance.
-
Ofcom. (2023). Communications Market Report 2023.
-
Product Security and Telecommunications Infrastructure Act 2022 (PSTI Act).
-
Quocirca Insights. (2024). Blogpost: The UK PSTI Act and its implications for the print market.
-
Rajnovic, G. (2024). Blogpost: UK Product Security and Telecommunication Infrastructure Act 2022.
-
Rajnovic, G. (2024). Blogpost: UK PSTI Act 2022 – Examples.
-
RSM. (2020). Evidencing the cost of the UK Government’s Proposed Regulatory Interventions for Consumer IoT Products.
-
SGS. (2023). Radio Equipment Directive (RED) Delegated Act for Cybersecurity Officially Postponed to 2025: What Does it Mean?
-
Shirer, M. (2023). “Worldwide Spending on the Internet of Things is Forecast to Surpass $1 Trillion in 2026, According to a New IDC Spending Guide”
-
Statista. (2020) “Average number of devices residents have access to in UK households in 2020, by device”.
-
Statista. (2022) “Number of Internet of Things (IoT) connected devices worldwide from 2019 to 2030, by vertical”.
-
Statista. (2024). “Internet of Things - China”.
-
Statista. (2024). “Internet of Things - United Kingdom”.
-
Statista. (2024). “Internet of Things – Worldwide”
-
Suunto. (2022). New ownership broadens Suunto’s shoulders in developing fit-for-purpose outdoor products.
-
UK Government. (2018). Guidance: Code of Practice for Consumer IoT Security.
-
UK Government. (2018). Mapping of IoT Security Recommendations, Guidance and Standards to the UK’s Code of Practice for Consumer IoT Security.
-
UK Government. (2021). Policy paper: Government response to the call for views on consumer connected product cyber security legislation.
-
UK Government. (2022). Policy paper: National Cyber Strategy 2022.
-
UK Government. (2023) Secure by design.
-
YouGov. (2022) The dawn of the connected home: YouGov current and future analysis of the smart home market.
Annex 2: Market analysis: Supporting data
This Annex presents data tables to illustrate the disaggregation of products, by manufacturer location of headquarters, by number of employees, turnover and routes to market. The following tables show the summary statistics that form the basis of the graphs in the main body of the text.
Table 5: Product types, and countries of origin for each product (n=1024 products)
| Variable | Category | N | % |
|---|---|---|---|
| Product type | Audio | 70 | 6.8 |
| Children’s toys and appliances | 10 | 1.0 | |
| Environmental Control | 59 | 5.8 | |
| Garden appliances | 14 | 1.4 | |
| Health, Fitness and Wellbeing | 65 | 6.3 | |
| Heating | 29 | 2.8 | |
| Home appliances | 42 | 4.1 | |
| Home entertainment | 29 | 2.8 | |
| Hub / Home control | 10 | 1.0 | |
| Kitchen appliances | 75 | 7.3 | |
| Leisure & Hobbies | 12 | 1.2 | |
| Lighting | 117 | 11.4 | |
| Mobile | 19 | 1.9 | |
| Other | 4 | 0.4 | |
| Pet Care | 16 | 1.6 | |
| Safety & Security | 225 | 22.0 | |
| Service & Care | 8 | 0.8 | |
| Smart Home | 98 | 9.6 | |
| Tablets and e-readers | 25 | 2.4 | |
| Wearables | 59 | 5.8 | |
| WiFi and Networking | 20 | 2.0 | |
| Workplace | 18 | 1.8 |
| Company headquarters | Australia | 6 | 0.6 |
| Austria | 4 | 0.4 | |
| Canada | 12 | 1.2 | |
| Chile | 1 | 0.1 | |
| China | 254 | 24.8 |
| Variable | Category | N | % |
|---|---|---|---|
| Denmark | 3 | 0.3 | |
| United Arab Emirates | 4 | 0.4 | |
| Finland | 7 | 0.7 | |
| France | 39 | 3.8 | |
| Germany | 69 | 6.7 | |
| India | 6 | 0.6 | |
| Ireland | 3 | 0.3 | |
| Italy | 10 | 1.0 | |
| Japan | 44 | 4.3 | |
| Latvia | 5 | 0.5 | |
| Lithuania | 1 | 0.1 | |
| Netherlands | 37 | 3.6 | |
| Norway | 4 | 0.4 | |
| Poland | 13 | 1.3 | |
| Singapore | 6 | 0.6 | |
| South Korea | 20 | 2.0 | |
| Spain | 6 | 0.6 | |
| Taiwan | 17 | 1.7 | |
| Turkey | 13 | 1.3 | |
| UK | 141 | 13.8 | |
| USA | 283 | 27.6 |
The table below shows the size of the manufacturers of these products (n=394).
Table 6: Employees and turnover data for each manufacturer (n=394 manufacturers)
| Variable | Category | N | % |
|---|---|---|---|
| Employees (range) | Large: 250+ employees | 145 | 36.8 |
| Medium: 50-249 employees | 82 | 20.8 | |
| Small: 10-49 employees | 80 | 20.3 | |
| Micro: 1-9 employees | 32 | 8.1 | |
| Data unavailable | 55 | 14.0 | |
| Turnover (range) | Up to £10m | 87 | 22.1 |
| £10m - £50m | 60 | 15.2 |
| Variable | Category | N | % |
|---|---|---|---|
| More than £50m | 114 | 28.9 | |
| Data unavailable | 133 | 33.8 |
The table below shows the routes to the market for each brand. Note that the population shifts from manufacturers to brands—that is because a few manufacturers own various brands, and use different routes to the market for each brand.
Table 7: Routes to the market for each brand (n=416 brands)
| Variable | Category | N | % |
|---|---|---|---|
| Sold in own online shop | Not sold in own online shop | 110 | 26.4 |
| Sold in own online shop | 299 | 71.9 | |
| Data unavailable | 7 | 1.7 | |
| Sold in online third-party marketplace | Not sold in online third-party marketplaces | 39 | 9.4 |
| Sold in online third-party marketplaces | 368 | 88.5 | |
| Data unavailable | 9 | 2.2 | |
| Sold in physical shop | Not sold in physical shop | 221 | 53.1 |
| Sold in physical shop | 186 | 44.7 | |
| Data unavailable | 9 | 2.2 | |
| Sold in own physical shop | Not sold in own physical shop | 369 | 88.7 |
| Sold in own physical shop | 38 | 9.1 | |
| Data unavailable | 9 | 2.2 |
Finally, the figures below break up the routes to market for each type of product. Here, too, the total population are the brands (n=416).
Figure 22: Brands sold on online third-party marketplaces
Figure 23: Brands sold on companies’ own websites.
Figure 24: Brands sold in physical shops.
Figure 25: Brands sold in companies’ own physical shops
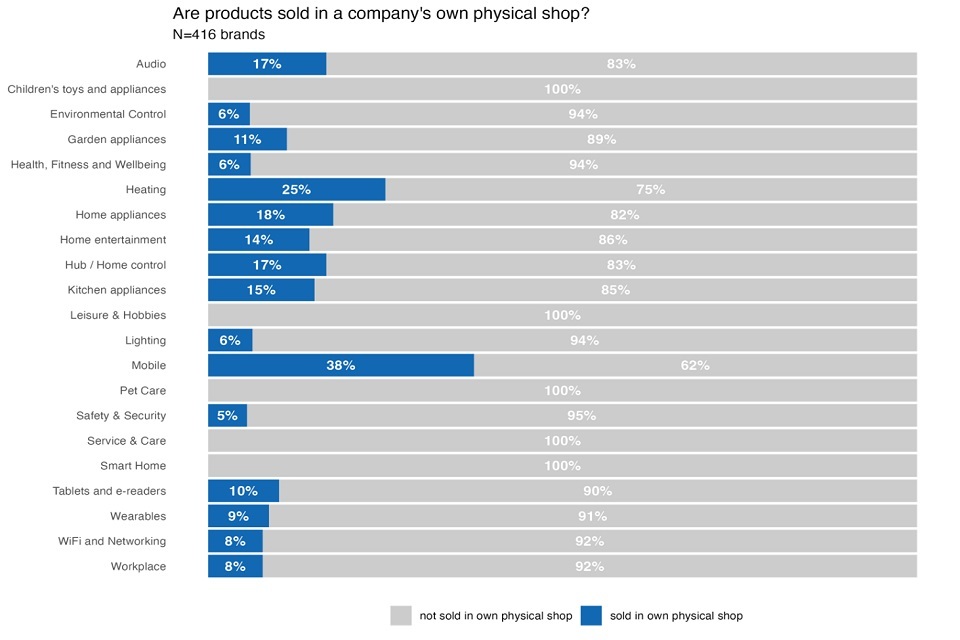
Annex 3: Quantitative telephone survey analysis
This section details the sample profile from the quantitative telephone (CATI) survey. It also includes any charts which were not included in the main body of this report. More information can be found in the separate technical report.
Sample profile
Of the 33 companies surveyed, 94% currently manufacture consumer connectable products that are sold in the UK, with just 6% that do not currently but do have plans to do so.
33% of companies that participated in the survey currently manufacture consumer connectable products and have plans to extend their range in the future.
Figure 26: Whether company currently manufactures consumer connectable products that are sold in the UK, and/or has plans to do so (Question: S01, Base: 33, multiple choice question)
| Currently manufactures at all (n=31) | 94% |
| Plan to manufacture at all (n=12) | 36% |
| Currently AND plan to (n=11) | 33% |
| Not currently, but do plan to (n=2) | 6% |
Looking at the geographical spread of manufacturers, the survey captured responses from manufacturers with headquarters in Europe, North America and Asia. Just under 50% of the companies that participated have their headquarters in the UK, 27% in the rest of Europe and the remaining 24% in the USA/Canada or Asia.
Figure 27: Where company’s headquarters are based (Question S04, Base:33)
| UK (n=16) | 48% |
| Elsewhere in Europe inc, Germany, Denmark, Netherlands, Poland (n=9) | 27% |
| USA/Canada (n=6) | 18% |
| Asia inc.Taiwan, Hong Kong (n=2) | 6% |
Figure 28: Business size (Question S06, Base: 33)
| Micro (1-9 employees, n=1) | 3% |
| Small (10-49 employees, n=8) | 24% |
| Medium (50-249 employees, n=5) | 15% |
| Large (250 or more employees, n=19) | 58% |
Figure 29: Business turnover (Question S07, Base: 33)
| Up to $10 million (n=6) | 18% |
| Between$10 million and $50 million (n=3) | 9% |
| More than $50 million (n=21) | 64% |
| Prefer not to say (n=3) | 9% |
Sale of consumer connectables in the UK market
When asked to specify where their consumer connectable products are sold within the UK, as Figure 6 summarises, this varies, with the highest proportions selling their products via third-party physical stores or their own website (both 74%). These channels are closely followed by 68% that sell the consumer connectable products they currently manufacture via online third-party marketplaces, with a similar proportion via online retailers (61%). Where manufacturers specified ‘other’ locations this includes wholesalers, distributors and independent retailers.
Figure 30: Where consumer connectable products are sold in the UK (Question S02a, Bases: 31 and 12)
| Products currently manufactured | Products they plan to manufacture | |
| Physical store third party (n= 23 and 10) | 74% | 83% |
| Online website linked to your store/brand (n= 23 and 8) | 74% | 67% |
| Third party online market place e.g. Amazon (n= 21 and 9) | 68% | 75% |
| Third party online retailer e.g. Argos (n= 19 and 9) | 61% | 75% |
| Physical store linked to your brand (your own shops (n=6 and 2)) | 19% | 17% |
| Other (n=11 and 6) | 35% | 50% |
Figure 31: Proportion of sales of consumer connectable products that are sold in the UK (Question 3, Base: 31)
| 1-20% (n=16) | 52% |
| 21-40% (n=5) | 16% |
| 41-60% (n=0) | 0% |
| 61-80% (n=2) | 6% |
| 81-99% (n=2) | 6% |
| 100% (n=3) | 10% |
| Prefer not to say (n=3) | 10% |
Concerns over Cyber Security
Figure 32: Awareness of any cyber-attacks on their products within the last 12 months (Question 8, Base:33)
| Yes (n=3) | 9% |
| No (n=27) | 82% |
| Don’t know (n=3) | 9% |
Figure 33: How concerned manufacturers are about cyber-attacks on their products (Question 9, Base: 33)
| Very concerned (n=3) | 9% |
| Quite concerned (n=13) | 39% |
| Not concerned at all (n=12) | 36% |
| Don’t know (n=5) | 15% |
Manufacturers reasons for being concerned about security
The manufacturers ‘very concerned’ gave the following reasons:
“Consumers and businesses are a nice target for bad actors, and with social engineering activities that they will engage in, consumers might not always be aware of what is being attempted”.
“The brand damage. If it happens with our devices, and all involved costs. Reputation. Also the impact on customers”.
Manufacturers who are ‘quite concerned’ also cite concerns over reputational damage, the impact on their customers and the continuous need to try and protect their products, and stay on top of potential threats.
“Lots of reputation, damages for the customer, mostly. Also to some degree liability. Trust in and security of our devices”.
“Devices have payment functionalities, privacy data, photographic information. This is top priority. We are concerned that users are not compromised. Others believe they have the processes in place to make them less vulnerable, which is why they are not very concerned”.
“Hackers are getting more and more clever. They will find vulnerabilities sometimes. There are more and more updates, we are being forced to make updates. If we weren’t and industry could stick with one OS over the years, it would be very secure. But regulators are encouraging updates, which in turn will create vulnerabilities. This will continue to happen and industry has to nail down the hatches as needed”.
“It’s from prior experience, it happens more frequently than you would expect. Secondly reputation of data being leaked out. Don’t want to give somebody the attack that would exploit and access customer or business data”.
“Slightly less than quite concerned. We are not blasé, but well-established security for products. Reputationally it would be appalling for any vulnerabilities to become apparent. But I am very confident there are none because of the simple nature of our devices. We do worry about it, but we design things properly and act on any vulnerabilities that are brought to light”.
Manufacturers reasons for not being concerned about security
The manufacturers that are ‘not concerned at all’ about cyber-attacks on their products explain that this is due to the nature of their processes and products. For some, their beliefs are also based on the fact that they are unaware of any attacks on their products or they think it is unlikely their products would be attacked.
“The system is very secure, existing since 2011 in the US, so far not heard of any major security breach happening. 13 years of constant good reputation. In the US our company is quite strong. The team is working specially on this platform, highly educated, well known, doing a lot of additional steps in order to protect the system … It’s been in the UK and EU since 2013, more than 10 years with no issues”.
“Our US department did some tests and the only data they could compromise was local data – which was fixed in the space of a few minutes”.
“Communication on most of our products is Bluetooth. If you want to hack it, you would have to be in my kitchen. The Bluetooth range is normally 10 metres”.
“Our tracking devices don’t interact directly with the consumer, tracking data is sent to our cloud-based servicer via GPS or Wi-Fi and data provided to consumers comes from our data centres”.
“It’s because of the way our products have been designed and built. The devices are connected in the same place as the smart devices they are connected to”.
“We adhere to 303 645 in terms of security, we could be concerned if it happened, but we adhere to those requirements. There is constant hacking on our website. Always somebody trying to do something to the product. Any product can be hacked… Our products are built safe”.
“The effort that goes into protecting the products. If you are concerned, you are aware your product has vulnerabilities for cyber-attacks. We have a vast network that keep this safe”.
“Our devices are not always on the internet. There would be cases where you could break in, get subscriptions to our map services to save some money. But a major scale attack is very unlikely”.
PSTI Awareness
When asked, without any prompting, whether they are aware of any cyber security regulations (related to consumer connectable products) that are being introduced in the UK market 90% of all manufacturers said they are aware.
Of the three manufacturers unaware, two have headquarters based in the UK, and one in the USA; two are smaller employers with 10-49 employees and one is a medium-sized employer with 50-249 staff.
Figure 34: Awareness of any cyber security regulations being introduced in the UK market (Question 1, Base: 33)
| Aware of any regulations being introduced (n=30) | 90% |
| Not aware (n=3) | 10% |
Those aware of any regulations coming in were asked to specify (unprompted) what they know about them. In response, many companies provided quite lengthy responses, some examples include:
“The CRA, EU wide. PSTI which is UK specific, then various initiatives by retailers to adhere to cyber security. Also the parts of CE regulations and the changes to RED [Radio Equipment Directive] which will apply to the UK, because we have pan American products”.
“Designed to increase security of connected products so they can’t be used to attack infrastructure. No default passwords, disclosure policies to put in place that if vulnerabilities are found they can be responded to.”
“I don’t know the details by heart. However, we are working with cyber security experts to guide us with compliance.”
“PSTI Act, also the Telecoms Security Act for which we are a Tier 1 operator. Enforcement by Ofcom, regulations governing network and cyber security across UK operations. There are plenty we are bound by these include NIS regulations. DSIT initiative, not sure who regulator will be, so I’m working on a Cyber Security Code of Practice being introduced as well. Also, cyber security and energy. We are aiming to widen that scope.”
“We know about the PSTI Regulations 2023 that is being introduced in spring 2024”.
“We know about the PSTI Regulations 2023 which comes into force on the 29th of April 2024 and we have been working with our UK partner to make sure we will comply for some time”.
“We know them backwards, password security, monitoring, non-compliance, the SoC we need to do, at a manufacturer, exporter and distributor level, including retail.”
Several manufacturers expressed concern based on their knowledge of the regulations coming into force in the UK. Comments include concerns over timeframes and lack of guidance, clarity and consultation.
“There is a lack of detailed guidance, what it looks like, what to aim for. Engagement at the UK level came too late. It seemed like it’s been done in a really big rush.”
“PSTI is one of the main banes of my life. They are ill conceived, badly thought through and incredibly badly brought to market”.
“Some consultation was missing here. In the EU they did not consult. Need some structure, website for feedback, not only from UK industry but also EU industry side. We identified some concerns afterwards”.
“This is the first legislation I am aware of where there is a hard immediate cut off, even items on the market had been available for sale, I can understand the technical aspects, but the addition of a SoC to products in warehouse and on shelves. I don’t feel the repercussions were properly thought out.”
“Other companies have grey zone questions and are looking at those. Bluetooth pairing we are not sure of the relevance. This is a problem with the whole law. Certain points are not 100 per cent clear. Security wise we comply but might be different interpretation in parts of Bluetooth. We had lengthy discussions with OPSS. The standards are longer than the headline. … We have checked some of our appliances with third parties against all requirements and they passed, including those 3 requirements for PSTI. But there is constant discussion on what the detail means.”
Overall, out of the 30 companies that are aware that some regulations are being introduced:
-
56% specifically mentioned the ‘PSTI’.
-
17% mentioned the deadline of April 2024.
Next, when prompted with a list of specific regulations and standards, all but 2 of the 33 manufacturers surveyed were aware of at least one of these. Awareness is highest with regards to ETSI (88%), with 79% aware of the PSTI Regulations 2023 and a similar proportion (73%) are aware of the PSTI Act. Both manufacturers not aware of any of these regulations or standards are small employers with 10-49 employees, one has their headquarters in the UK and the other in Asia.
Figure 35: Awareness of specific regulations and standards (Question 3, Base: 33)
| PSTI Act (n=24) | 73% |
| PSTI Regulations 2023 (n=26) | 79% |
| ETSI EN 303 645 (n=29) | 88% |
| ISO/IEC 29147: 2018 (n=23) | 70% |
| I’m not aware of any of these regulations or standards (n=2) | 6% |
For each regulation or standard manufacturers were aware of, they were asked to provide details about what they know about each.
Some examples of the comments received for each are summarised below. With regards to the PSTI regulations, once again some concerns are raised, including lack of clarity and concerns/difficulties in trying to ensure existing stock complies, within the timeframes set:
The PSTI Act 2022
“It comes into force 29 April. Originally published in Sept 2023, there was some work in the period up to making that piece of legislation. The scope of products is generally anything electronic that connects to the internet. There are some exemptions, which are somewhat strange … Desktops and laptops not in scope, but that’s the way the legislation has been written”.
“We have to have vulnerability, disclosure policy. Vulnerability management policy or processes for handling those. We need to make sure our connectable products are secure in the way the law defines, not to have standard passwords and other things. We also need to service products for over the lifetime, in regards to cyber security for expected product lifetime”.
“This is the underlying act in the UK that sets the framework for cyber security regulations for manufacturers and importers and distributors of relevant connectable products in the UK.”
“No default passwords. Simple things manufacturers can put in place in terms of design, like disclosure policy. It has become the standard that people quote”.
“When we have to develop just for the UK market, we used the PSTI, that was our first reference. The PSTI has 3 requirements. Use of passwords. The vulnerability policy, we are fine tuning it. On support period, we are having difficulties, with legacy products and those in stock already”.
“Product security and telecommunications infrastructure element. Product security, aim to bring in baseline minimum standard for security on internet devices. Not having default passwords at point of sale on any one device. Having clear transparent information on length of time for product security updates. Clear and easily located point of contact for any vulnerabilities”.
“Adopted in 2022. Framework, responsibilities of manufacturers, import, distributors. Not only security but telecom infrastructure. Possibilities for SoC, full SoC or summary of SoC. It gives powers secretary of state to adopt other regulations, like the PSTI regulations and make applicable to certain products”.
The PSTI Regulations 2023
“How you go about meeting the requirements. The Act says you must comply to stuff in future regulations, the regulation says the three requirements, but this is not in the Act. No easily guessable or default passwords, vulnerability disclosure methodology, support period publication. It also lays out the minimum information you need on SoC”.
“April, May this year. Products at point of sale, not just making sure products comply that we are currently bringing to into country, but those already in stock must also comply. Compliance also applied to those refurbished products, not repaired products. This topic has crawled out of the woodwork. We could have placed a product onto the market 3 years ago for example, then if we upgrade it and refurbish it, it needs to comply”.
“It’s a little bit confusing the way it is done. I am used to having everything done in one document. It’s a bit messy, not clean. I would advise having different schedules, different regulations. PSTI act 2022, part 1, then the regulations in 2023 is definitely confusing. Much easier to have single legal instrument that updates or replaces the original”.
“Came off back off the PSTI Act 2022. It’s the overarching legislation”.
“UK specific regulations that mirrors quite heavily the EU cyber [resilience act] and the ETSI regulations, 303 645”.
“Not much information on this. I guess how to comply with this act, with the manufacturers. I’m not sure about that”.
“We had quite large knowledge of PSTI coming into effect. Government guidance said it’s a 12-month implementation period, but the actual published date of 14 September is coming into effect on the 29 April. Frustratingly, the regulations apply from point of making the product available. Whereas all other key regulations we work to as manufacturers are in effect from point of placing on the market. The change in terminology in regulations for PSTI, it opens manufacturer to stock issues. The compliant requirements mention about clause 1A, mentions the product, type and batch. From a new production perspective, the inclusion of a specific production batch is not necessarily problematic, but the requirement for both info to be included on statement, or distributors warehouses, will be almost impossible for us to get that level of detail from those holding stock at the time. There is a lot of work going on in AMDEA and manufacturers with similar feedback, asking for an extension of at least 6 months in terms of compliance for old stock to be sold, then allow new stock to come through with new type batch info included. Requirement for signatures is not the same as Certificate of Conformity. It is a blanket statement from our company to say schedule 2, the necessity for signature, name and function of the signatory, is a challenge, as it’s consumer documentation, not included in our surveillance. It’s sensitive information, name, function, protected characteristics. We are asked to make these available for little or no benefit to consumer”.
ETSI EN 303 645 – the European standard on Cyber Security for Consumer Internet of Things
“It shows what to do when designing a secure product. Basic level. Very usable for people familiar with the matter”.
“The base requirement for cyber security in connectable devices. It covers all products that fall under PSTI”.
“Original code of conduct that was given some clout by being voted by multiple countries as a consensus”.
“This harmonises the standards to comply with the PSTI standard”.
“List of European, global document, standard rather than a regulation. It gives best practice on what you could include in your products to make them better”.
“Less knowledge compared to PSTI. I know the PSTI is based largely on the ETSI code, but however I know there are differences. The PSTI takes the ETSI requirements as a guideline”.
ISO/IEC 29147: 2018 – Standard on Vulnerability disclosure
“Standard particularly focused on disclosure requirements. Some of it is comparable to 303 645, but it’s an alternative methodology that could be applied when being compliant with PSTI regulation for products”.
“This sets out expectations of best practices for connectable devices. I am aware of it but not as aware as the PSTI regulations. My clients have been looking at our devices in line with the standard”.
“Limited knowledge”.
“This is a supplementary standard in order to comply with the PSTI requirement.”
“That one is covered generally by our legal department - we submit data and documents to them – review it – and advise if we conform or not. It’s done by a different department.”
“It’s fortunate I am member of BSI technical committee so I can access these international standards online. ETSI is a free public standard. You can download it quite easily, but for 29147, 150 … there is one free reference standard, and one chargeable standard which has a slightly different take on things. Using this approach is strange. Clause 6.2.5 defines a specific acknowledgment period for responding to vulnerability reports. You have to do it within 7 calendar days but the ETSI guidance doesn’t mention any response times. Just gives reference to another part, not mandated within PSTI regulations. This caused confusion in the factory as it is connected to a provision defined in PSTI. Talks about conventional timeline of 90 days for software solution. We don’t think it’s a legal requirement. but we had to double check before taking out from our worries list. Also caught out other manufacturers. The comparison between 5.2-1, and clause 29147, should have same requirements defined. 7 calendar days should be in both”.
Figure 36: Awareness of when PSTI regulations will come into force (Question 5, Base: 26)
| End of March 2024 (n=1) | 4% |
| April 2024 (n=4) | 15% |
| 26 April 2024 (n=1) | 4% |
| 29 April 2024 (n=15) | 58% |
| May 2024 (n=1) | 4% |
| April or May 2024 (n=1) | 4% |
| Spring 2024 (n=1) | 4% |
| Autumn 2024 (n=1) | 4% |
| Not aware (n=1) | 4% |
To further explore manufacturers levels of understanding and awareness, respondents were read out the following paragraph and then asked, in this context, were they aware of these new requirements.
“The PSTI Act 2022 establishes a duty for manufacturers of consumer connectable products that are to be sold or supplied in the UK to comply with security requirements and to take action if they become aware (or ought to be aware) that a product does not comply with a relevant security requirement.
In case of non-compliance, manufacturers are to take all reasonable steps to remedy the compliance failure. In particular, manufacturers must notify importers, distributors, and any other manufacturers they are aware of, as well as the enforcing authority. Manufacturers must also keep a record of any compliance failures, or investigations in relation to a real or suspected compliance failures for a period of 10 years. Compliance failures will be dealt with on a case-by-case basis but it could lead to appropriate enforcement action such as enforcement notices, fines or penalties.
The specific security requirements are set out in the PSTI Regulations 2023 and will come into force on 29th April 2024. They apply to both the hardware and associated software of the consumer connectable device and include:
-
Regulations regarding passwords (which must be unique, not guessable or based on incremental counters)
-
Vulnerability disclosure (i.e. a policy and public point of contact with details on how to report any security issues)
-
Manufacturers must also specify the minimum length of time for which the connectable device will receive security updates.”
Based on this context, 76% of manufacturers surveyed said that they were fully aware of this. Just 12% manufacturers that they were ‘not aware at all’.
Figure 37: Awareness of detailed description of the PTSI Act and Regulations (Question 11, Base: 33)
| Fully aware (n=25) | 76% |
| Partially aware (n=4) | 12% |
| Not aware at all (n=4) | 12% |
For manufacturers at least partially aware of the new regulations, the most likely source of this awareness is via industry or trade bodies (48%). After some margin, of the 29 manufacturers aware, the second most common source of their awareness is public consultations (28%), followed by internal legal, compliance or product security teams (21%).
A significant proportion (45%) also mention ‘other’ sources which includes distributors; EU Parliament discussions; an email from a CE/UK CA Testing partner; their customers (i.e. retailers) and Which.
Figure 38: Sources of awareness of new regulations (Question 12, Base: 29)
| An industry trade/membership body (n=4) | 48% |
| Public Consultations, Gov.uk website or Call for views (n=8) | 28% |
| Internal legal, compliance or product security teams (n=6) | 21% |
| From others in the industry (n=5) | 17% |
| Media, press releases or communications (n=5) | 17% |
| Direct engagement with Government (n=4) | 14% |
| Engagement with standards bodies (n=4) | 14% |
| Proactive tracking of cyber security or trade legislation (n=2) | 7% |
| Previous research surveys conducted by government or through third parties (n=1) | 3% |
| Other (n=13) | 45% |
Figure 39: Sources used to make themselves aware of new regulations (Question 13, Base: 33)
| An industry trade or membership body (n=16) | 48% |
| Public Consultations, Gov.uk website or Call for views (n=14) | 42% |
| Media, press releases or communications (n=11) | 33% |
| From others in the industry (n=10) | 30% |
| Internal legal, compliance or product security teams (n=10) | 30% |
| Direct engagement with Government (n=7) | 21% |
| Proactive tracking of cyber security or trade legislation (n=7) | 21% |
| Engagement with standards bodies (n=6) | 18% |
| Previous research surveys conducted by government or through third parties (n=1) | 3% |
| Other (n=9) | 27% |
Compliance levels
The next section of the survey told respondents that a list of the three cyber security requirements in the PSTI regulations would be read out. They were asked to indicate for each whether they have already introduced them or are looking to introduce them in the near future in their consumer connectable products.
Unique Passwords
52% of manufacturers surveyed say they have already introduced the requirement for unique passwords to all their consumer connectable products. For 18% of manufacturers, this requirement is not believed to be relevant. This leaves around 30% of manufacturers that indicated they are either partially compliant (i.e. that they have introduced this for some products), or they have plans to do so. None of the manufacturers surveyed said they were not looking to introduce this at all.
Figure 40: Whether the requirements related to passwords have been introduced (Question 6, Base: 33)
| Introduced for all products (n=17) | 52% |
| Introduced for some products (n=4) | 12% |
| Looking to introduce within a certain time (n=3) | 9% |
| Looking to introduce in the near future but not sure when (n=4) | 12% |
| Not looking to introduce for some products (n=1) | 3% |
| Not looking to introduce at all (n=0) | 0% |
| This requirement is not relevant to us (n=6) | 18% |
Reasons provided for this requirement not being relevant include:
“We don’t set any passwords or store any passwords”.
“Never used passwords, we have another method. Already compliant connecting to back end services”.
“No passwords, based on security certificates, mutual PLS1.3”.
“No privacy on it apart from routes you have taken. No need for passwords on the hardware. Only on connecting the connection has passwords. Authentication is required”.
Public Point of contact
Regarding the requirement to provide a public point of contact for security issues to be reported, compared with the requirement for unique passwords, a slightly higher proportion of manufacturers (58%) say they have already introduced this for all their products.
Just one manufacturer said that they consider this requirement not to be relevant to them, leaving 42% of manufacturers surveyed who mostly have plans to introduce this either within a certain time frame or in the near future but are not sure when.
Figure 41: Whether the requirements related to the public point of contact have been introduced (Question 6, Base: 33)
| Introduced for all products (n=19) | 58% |
| Introduced for some products (n=0) | 0% |
| Looking to introduce within a certain time (n=8) | 24% |
| Looking to introduce in the near future but not sure when (n=6) | 18% |
| Not looking to introduce for some products (n=1) | 3% |
| Not looking to introduce at all (n=0) | 0% |
| This requirement is not relevant to us (n=1) | 3% |
Security updates
For the third requirement, regarding information on minimum time periods for security updates, this has the lowest number of manufacturers that indicate this has already been introduced for all their products. 27% indicate this requirement has already been achieved for all their consumer connectable products. A slightly lower proportion (21%) say this requirement is not relevant to them. This leaves over 50% of manufacturers that are either partially compliant (i.e. this has been introduced for some products) or they are looking to introduce this either within a certain time frame, or at some point in the future but are not sure when that will be.
Figure 42:Whether the requirements related to security updates have been introduced (Question 6, Base: 33, multiple choice question)
| Introduced for all products (n=9) | 27% |
| Introduced for some products (n=2) | 6% |
| Looking to introduce within a certain time (n=13) | 39% |
| Looking to introduce in the near future but not sure when (n=7) | 21% |
| Not looking to introduce for some products (n=1) | 3% |
| Not looking to introduce at all (n=0) | 0% |
| This requirement is not relevant to us (n=7) | 21% |
Reasons for this requirement not being relevant include not wanting to be ‘locked down’ to a minimum period and that they offer to service their products indefinitely:
“We are very transparent, never locked down to a minimum period, just pragmatic based on number of users using products. Products last a long time. Also, we provide care for over 7 years”.
“Our claim is to service products indefinitely. This also includes software updates. No exact end date. Over full lifetime”.
“Device must be capable of receiving security updates. If not able to receive security updates, it will not be applicable”.
Cyber security provisions from ETSI
Next, the survey told respondents we were going to read out a list of ten additional cyber security provisions from ETSI standard EN 303 645 on cyber security for consumer internet of things devices.
It was explained that these provisions are complementary to the requirements in the UK’s PSTI Regulations 2023. Companies were then asked to indicate whether they have already introduced them or are looking to introduce them in the near future in their products.
Table 1 summarises manufacturer responses, with each of the ten provisions presented in rank order based on the number of manufacturers that have already introduced this for all their consumer connectable products.
The table illustrates that of the ten provisions, devices being easy to install and maintain is most likely to have been introduced by manufacturers across all their products (85% of manufacturers).
The provision that manufacturers are next most likely to be compliant with across all their consumer connectable products is that devices and related services shall be resilient to outages. This provision has already been introduced across all products by around three quarters of manufacturers (73%). Similar proportions have also introduced allowing users to easily delete user data, ensuring the security of personal data, and communicating securely using best practice cryptography.
The provisions least likely to have been introduced across all products are that telemetry data from devices and services shall be examined to identify and address security anomalies, and that devices shall securely store sensitive security parameters. Around 50% of manufacturers say these provisions have been introduced across all their products.
Where manufacturers have not introduced these provisions across all products, it is most likely to be because they say the requirement is not considered relevant to them.
Table 8: Whether or not each cyber security provision from the ETSI standard has been introduced for manufacturers’ consumer connectable products (Question 7, Base: 33)
| Introduced for all products | Introduced for some Products | Looking to introduce within a certain time | Looking to introduce in the near future but not sure when | Not looking to introduce for some products | Not looking to introduce at all | Not relevant | |
| Devices shall be easy to install and maintain | 85% | 3% | 0% | 3% | 0% | 0% | 12% |
| Devices and related services shall be resilient to outages (e.g. data network or Power outages) | 73% | 9% | 3% | 3% | 3% | 0% | 18% |
| The integrity of device software shall be ensured | 67% | 15% | 3% | 9% | 6% | 0% | 15% |
| Devices shall allow users to easily delete user data | 67% | 12% | 3% | 3% | 0% | 0% | 27% |
| Devices shall ensure the security of personal data | 67% | 9% | 6% | 3% | 3% | 0% | 21% |
| Devices shall communicate securely Using best practice cryptography | 64% | 15% | 3% | 3% | 6% | 0% | 21% |
| The exposed attack surfaces of the device shall be minimised | 58% | 15% | 3% | 9% | 3% | 0% | 21% |
| Devices shall validate input data | 55% | 6% | 0% | 6% | 3% | 0% | 36% |
| Telemetry data from devices and services shall be examined to identify and address security anomalies | 52% | 9% | 6% | 9% | 6% | 0% | 33% |
| Devices shall securely store sensitive security parameters | 48% | 15% | 12% | 6% | 6% | 0% | 27% |
Examples are provided in the following table for the reasons given by manufacturers as to why they think each provision is not relevant to them. In some instances, it seems manufacturers chose this option where they were unsure as to their level of compliance or not clear on what the provision means. Not all manufacturers were willing to provide reasons.
| Reasons given for each provision being considered not relevant | |
| Devices shall be easy to install and maintain | No installation and maintenance needed. Unwilling to comment to what status that is. |
| Devices and related services shall be resilient to outages (e.g. data network or Power outages) | Not holding any data. Might already be introduced, not checked. |
| The integrity of device software shall be ensured | Don’t know how to answer. Might already be introduced, not checked. |
| Devices shall allow users to easily delete user data | Our speakers don’t hold user data. No user data stored on the device. |
| Devices shall ensure the security of personal data | That’s controlled by Google and Windows on our machines – 3rd party activity – not us. Our speakers don’t hold any personal data. You just connect through the router and that is it. Consumers don’t have to provide any data at all. Our speakers can be compared to smart light bulbs there is no data input. |
| Devices shall communicate securely Using best practice cryptography | We are not in control of that – if we use Wi-Fi you have to use WPS-k2 – we don’t have a choice to use it or not – that’s the industry standard. For our lights, they only change colour, dim up and down, the devices. Camera feeds are encrypted. |
| The exposed attack surfaces of the device shall be minimised | I don’t actually know what exactly that means. Might already be introduced, not checked. Unwilling to comment to what status that is. |
| Devices shall validate input data | Data collected by sensors. Third party – not relevant to us. No data input. |
| Telemetry data from devices and services shall be examined to identify and address security anomalies | Not sure about cameras we sell. Probably do but not sure. Device not holding any data. |
| Devices shall securely store sensitive security parameters | Our devices don’t store this. We do not store sensitive data into the device. The device is to send telemetry data only. Our tracking devices don’t store any sensitive information. Device does not store any data, collected data is stored safely on an AWS server. |
Likelihood of compliance by 29th April 2024
Next in the survey all manufacturers were asked directly how likely they are to be compliant with the three regulations set out in the PSTI Regulations by the due date of 29th April across all their products sold in the UK.
Manufacturers were given the following reassurance:
Please be honest with your response to this question. You can rest assured that there will be no consequences for your organisation if you tell us that you are unlikely to be compliant by 29th April 2024. These responses will not be attributable unless you agree for them to be shared. Individual responses will not be shared with DSIT or the enforcing authority.
Overall, as Figure 19 summarises, the majority of manufacturers think it is ‘very likely’ that they will be compliant with each regulation by the deadline.
Manufacturers are most certain of the regulation concerned with providing a public point of contact, with 85% of manufacturers) indicating that it is ‘very likely’ that this will be in place by 29th April 2024.
For ensuring passwords are unique, not guessable or based on incremental counters, 76% of manufacturers say it is very likely this will be achieved in time. Around 10% say this is ‘quite likely’ or they are unsure.
In terms of the regulation on security updates, the proportion that indicate compliance is very likely drops to 64%, with 24% saying that this is only quite likely.
Figure 43: Likelihood of being compliant with each regulation by 29th April 2024 (Question 14, Base: 33)
| Very likely | Quite likely | Quite unlikely | Very Unlikely | Don’t know | |
|---|---|---|---|---|---|
| Passwords are unique, not guessable or based on incremental counters | 76% | 9% | 0% | 3% | 12% |
| The manufacturer provides a public point of contact to enable security issues to be reported | 85% | 0% | 3% | 6% | 6% |
| Information on the minimum length of time for which security updates will be provided must be made available | 64% | 24% | 6% | 0% | 6% |
Of the 4 manufacturers that are not sure they will be compliant with regards to passwords, all are micro or small employers; two have headquarters within the UK, one elsewhere in Europe and one in Asia. The manufacturer that says they are very unlikely to be compliant is a medium manufacturer with headquarters in Poland.
For providing a public point of contact, the two manufacturers that indicate this will be very unlikely by 29th April are both large manufacturers with headquarters in the UK and USA. For one of these their products are not currently being manufactured/sold in the UK, but are due to enter the UK market this year.
The two manufacturers not sure if they will be compliant with providing a public point of contact and with security updates are small and medium employers with headquarters in Asia and Poland.
Demonstrating compliance
For each regulation they had indicated they are very or quite likely to be compliant with by 29th April, manufacturers were asked to state in their own words how they aim to demonstrate compliance with each.
For the regulation onpasswords, responses from manufacturers include references to compliance documents or statements of compliance, as well as independent/third-party assessments and checks. There does seem some uncertainty however and ‘grey areas’, with one for example pointing out that their interpretation of the act/regulations is that they just need to state that they comply not show how they comply. Others just make reference to how their passwords are set up:
“We are required by the law to have the compliance document in place, that will accompany the product”.
“We will draft a Statement of Compliance, like the 4th requirement. Saying we meet the standards, whether the ETSI EN. Schedule 1 or Schedule 2 from PSTI regulations”.
“Via schedule 2. Either deemed compliant or the other description”.
“Working with a third party to show we are doing this. So, we have some form of independent backing”.
“Report showing compliance with EN 303 645 with passwords. Something in writing, then at any time, take the product and physically demonstrate it”.
“We know there is a requirement to provide a Statement of Compliance. We are currently consulting with our distributors and cyber security expert on this. We are currently not clear what the Statement of Compliance needs to show. Do we just write a letter that we comply or do we have to provide details on how exactly we comply”.
“You state that you deem to comply with the security compliance. There is nothing in the act asking you to show how you do”.
“Demonstrate to whom? For an end user by the fact the moment they start subscription for the service, they would be sent a secure link to email, to create a unique user”.
“We have designed the products that way”.
“Our password requires a combination of letters, numbers (and) special characters”.
“This is by design. The majority of our devices do not use passwords, nor are they accessible outside local, trusted networks”.
“Test the product, internally. Some don’t have passwords in that sense anyway. A range of samples and see they have default passwords or not. We could demonstrate the design process to show they don’t have default passwords, but this would not be proof. We would need to test the products to prove this. A regulatory or enforcing body would need to test them”.
For the regulation on providing public points of contact, references were again made to statements of compliance (SoC), several mention providing information online/on their websites, as well as in instruction manuals. Some comments also suggest there is some uncertainty as to exactly what is required:
“In two ways. There is information in the Declaration of Conformity for each product. There is information available in internet searches, in multiple different locations to access the information”.
“We publish this information on our website where we currently accept vulnerability reports for our products”.
“Through the instruction booklet and hosted online. On its bespoke website. Schedule 2”.
“Already on our website. We’re going to put a reference to it on instruction books, physical books by 29th April”.
“We have a Vulnerability disclosure website that explains all the process, specific handler for the vulnerability, timeline for responses, dependent on the severity”.
“On our proof of compliance, but also available on our website”.
“It’s public, so you can go to the internet, write an email, you can receive an email from the PSRT team”.
“Again, we are consulting on this with our distributor and cyber security expert. Consumers can already get in touch with us through our UK website. Do we need to create a special section for this or is what we have already sufficient”.
“I was not aware of this requirement, but we have a website where we can make this information available”.
“Put this on our website, as list a of contacts. Specialised contact or support in FAQs, a separate email, like security@ directed to our CRM software, then goes to customer service tickets, and this is redirected to a person internally in charge of security. We already have a dedicated member of staff for this”.
“Going forward from the next production run, it will be in the instruction manual. Prior to that, we can put on our website and app
For the third regulation on security updates, responses were similar to the points of contact, with several references to the information being available online, in product documentation and statements of compliance. Some manufacturers again outline some concerns regarding their ability to demonstrate compliance within the timeframes required:
“Required to be on the statement of compliance”.
“Website support periods for current and historic products”.
“In our manuals and website referring to those particular products”.
“We say the product information in the documentation. Also, in our company policy (which is) available on our website”.
“Through our public information in vulnerability policy. On the website. The products will contain some information on SoC declaration”.
“The information is provided in the declaration of conformity, in standard non-technical language for all consumers”.
“We will not use reference to standards, we will say we are compliant”.
“If we need to physically put this information with the product, it will take up to 4 to 6 months to get fully in place”.
“We are struggling a bit whether we can put the information on a website or put it in a leaflet and how we do demonstrate compliance”.
“These will be published on the website by March 2024. The printed matter will take longer”.
Next in the survey, all manufacturers that had indicated they are very or quite likely to be compliant with at least one of the three regulations by 29th April, were asked which of a list of steps they have already taken or will take to comply.
As Figure 20 summarises, the steps that manufacturers are most likely to have taken, or plan to take, to ensure they comply by 29th April is familiarising themselves with the legislation (87%), followed by a self-declaration/assessment of compliance (81%).
Figure 44: Steps that manufacturers have already taken or plan to take to ensure they comply (Question 16, Base: 31)
| Familiarisation with the legislation (n=27) | 87% |
| Self-Declaration/assessment of compliance of consumer connectable products (n=25) | 81% |
| Obtain legal advice (n=21) | 68% |
| Third party testing of compliance (n=16) | 52% |
| Amend compliance information at point of sale (n=15) | 48% |
| Send products to a third party to undertake a compliance assessment (n=13) | 42% |
| Re-design physical labelling (n=7) | 23% |
| Other (n=5) | 16% |
Reasons for non-compliance with PSTI Regulations
Manufacturers that consider it unlikely they will be compliant with each of the three regulations by 29th April were asked their reasons for this.
For complying with the requirement on passwords just one manufacturer had indicated they would be unlikely to achieve this within the timeframes and explained this is down to a lack of resource and knowledge:
“Lack of resources, lack of knowledge or experience or experienced people to introduce the changes in the software or the hardware. For the previous large company I worked for, the situation is different, they have resources and knowledge, they will, if they are aware about it, be able to meet all of them.”
For providing public points of contact, the three manufacturers that indicated they are unlikely to be able to comply with this in time mentioned concerns over timeframes, existing stock and the need for the information to be in a written format:
“No reasons why we shouldn’t be. It’s a matter of time”.
“If we need to update product documentation, it can take up 6 months to purge stocks”.
“We are likely to be non-compliant if the information is required to be written in a leaflet”.
For the third regulation, on security updates, which two manufacturers indicated they are unlikely to be able to comply with, their reasons for this include the practicalities and short transition period involved, how it is applied to products retrospectively (i.e. those already in stock) and confusion as to whether documentation needs to be on paper or electronic:
“Making a statement on minimum length of time, there is a challenge. It’s not about whether we are willing to make it or not, we are planning to. There are 3 other sets of regulations across Europe, with similar requirements. The definition of start of support period is very different. If you consider Lot X, an econ regulation coming into Europe. There is a defined period from last sale of the product. Then we have CRA Europe regulations, from time of sale, whereas UK DSIT is from sale date. Going back in time, from a consumer perspective is a bit odd. Something we sold 5 years ago; we have 5 years to support. Consumer will ask, am I already out of support? It’s strange, not market access, not forward looking. Also, we have the N Ireland issue to take care of, they comply to EU regulations. Practicalities. The biggest thing is the transition period. One of the Government websites talks about a 12-month transition. But its September to April, about 6 months. In general terms, short transition periods are bad”.
“We don’t know the answer yet from our suppliers. Non-European suppliers, they are in China. They are not used to supporting this particular bit of hardware, software or development. The two combined together is tricky, because development tools move on. So, we need ten years’ worth of support, and to ask them to make sure these tools will work in ten years’ time is a bit of a head scratcher. This is a general issue, not specific to the country of manufacture”.
“The terms of compliance are no problem in themselves, but there is a whole level of supply chain adjustment needed. 6 months is pushing the boundaries in terms of what businesses can do with a complex supply chain, complex organisation. There were several sessions with BST staff which led to further confusion. Several discussions in November, December time that struck industry. There was a lot of work with OPSS to ask and get answers. The clarity was not good enough. In terms of the backwardness of the regulation. How do you backwardly apply this to products already in supply chain and market. Retailers are asking are we able to return products. Why return a product? If you are not compliant by this date? Why are we not compliant? There is confusion about physical pieces of paper or it can be electronic? But this clarification has not been formalised. Everybody is trying to pass the buck and some are trying to manipulate the situation to avoid losses”.
Statement of compliance
Figure 45: Whether manufacturers have been contacted by distributors or retailers asking for information on compliance or a Statement of Compliance (Question 19a, Base: 33)
| Yes (n=23) | 70% |
| No (n=10) | 30% |
Regardless of whether manufacturers had been contacted by distributors or retailers, they were asked to describe what steps they are taking to prepare and provide the Statement of Compliance (SoC) to distributors and retailers.
The comments provided include preparing declarations/statements of conformity, direct engagement with distributors and retailers. Some raised queries/concerns, including that the legislation relating to the SoC is unclear and that providing hard copies are not a sustainable solution.
“Signing off the declaration and making the product compliant in time”.
“We are working with cross industry groups to establish a working template of SoC, tick boxes, to integrate into our systems. We have already been doing this since the back end of last year trying to whittle down stock in the warehouse to reduce resource required for this work. We have the SoC built into this, so we can include it in our document bags. Just profiling what stock is in retailer or warehouses, and then we will create a plan for the resource to go in and rework the stock included as required”.
“We’ve had direct engagement with distributors and retailers planning what we are going to do. They will be able to access it and put it with their own needs”.
“All new products coming into the country will have them already in a box. We are contacting the retailers to label packaging allowed by the regulation so we can retro-actively provide SoC to any stock they have
“Normally when we do new products, with safety, we issue a Declaration of Conformity. Similar process”.
“Some products will have it from the factory, inserted in the box, the packing from China. Others will have inserted at local warehouse in EU and UK. Some others we will not insert anything. We will use a current simplified statement in the manual which refers to the website. This is because the products are not in our control anymore, they are sold to distributors. Also, because we have a line up for a whole year decided last year. We have stock everywhere, it’s not easy to modify … Gradually it will be inserted, it will take some time. Not possible to do by April for some products”.
“There is a shortened statement on the device box, on the exterior packaging and interior packaging. There are websites with information that retailers and others can access. There is a council of distributors and resellers and some have requested a written statement on letter head and company stationery and we have provided it”.
“We are in close contact with the UK importer of our products about this and we are engaging with our regulatory experts … We are still trying to get a full understanding of the potential legal implications”.
“We support our UK dealers with the declarations or certification that shows compliance. We are in the good position; a lot of customers all have a good understanding as well … We support them in providing the documentation. We have a discussion with a test house about how the Declaration of Conformity should look for a specific topic like cyber security”.
“There are a number of industry stakeholder groups including retailers. One thing they are looking at is how the statement of compliance should look. As an industry, we feel it would be better if there were a standard format for the statement of compliance. But there is doubt as to who the statement of compliance is aimed at. If there is a standard way everybody knows what they are looking at. Unfortunately, legislation is very unclear on the format”.
“If we had a digital solution like QR codes. The only cost is the physical paper and the staff recruited to do this. This would have been much appreciated, faster for us, save costs related to the paper. Not sustainable as solution. We plan to send it electronically”.
“The products are currently undergoing testing with the local CE / UK CA house”.
Anticipated impact of compliance
All manufacturers that indicated they are very or quite likely to be compliant with at least one of the three regulations by 29th April (31 out of the 33 manufacturers surveyed) were asked, from a list read out to them, what they think are the key impacts of compliance on their organisation. Manufacturers could also provide details of any other impacts not already listed.
Of the suggestions made, manufacturers are most likely to indicate that increased costs will be an impact of compliance on their organisation. 81% of manufacturers expect this to be the case.
52% of manufacturers think there will be a need to train or upskill their staff and the same proportion recognise the positive impacts of the regulations, in terms of improved consumer confidence.
At least a third of manufacturers surveyed believe that compliance will improve their reputation (39%), improve product security or reduce product cyber security vulnerabilities (both 35%). 19% of manufacturers believe they will need to dispose of non-compliant stock, while a slightly higher proportion (23%) say they will sell non-compliant stock to non-UK markets.
Figure 46: Key impacts of compliance that manufacturers anticipate (Question 17, Base: 31)
| Additional/increased costs (n=25) | 81% |
| A need to upskill/train current staff (n=16) | 52% |
| Improved consumer confidence in products (n=16) | 52% |
| Improved reputation (n=12) | 39% |
| Improved product security (n=11) | 35% |
| Reduction in product cyber security vulnerabilities (n=11) | 35% |
| Increased customer satisfaction/loyalty (n=9) | 29% |
| Improved product safety (n=9) | 29% |
| Selling non-compliant products to non-UK markets (n=7) | 23% |
| Recruiting additional staff (n=7) | 23% |
| Needing to dispose of non-compliant stock (n=6) | 19% |
| Other (n=5) | 16% |
Two of the manufacturers that provided ‘other’ responses expect there to be no impact on their organisation of compliance, with one stating that they already need to be that secure. The other comments outline concerns regarding existing/non-compliant stock and additional costs:
“Push to sell stock before the deadline”.
“Biggest concern or impact is dumping of non-compliant stock. Would have to change the plugs for sale to another market, we will not do this”.
“Our products already meet the cyber security regulation. However, this creates additional cost because England is no longer in the EU”.
All manufacturers, regardless of their likelihood to be compliant, were next asked how they plan to manage any increased costs as a result of the new regulations coming out.
As Figure 22 indicates in most cases it seems manufacturers will be taking a mixed approach, that will involve absorbing some costs themselves, passing on some costs to consumers and/or passing some costs onto retailers.
60% of manufacturers plan to absorb some or all the costs themselves. A similar proportion (61%) plan to pass on at least some costs to consumers. While 36% of manufacturers are likely to pass at least some costs onto retailers.
Figure 47: How manufacturers expect to manage increased costs as a result of the new regulations (Question 18, Base: 33)
| Absorb all additional costs ourselves (n=9) | 27% |
| Absorb some additional costs ourselves (n=11) | 33% |
| Pass on all additional costs to consumers (n=3) | 9% |
| Pass on some of the additional costs to consumers (n=17) | 52% |
| Pass on all costs to retailers (n=3) | 9% |
| Pass on some costs to retailers (n=9) | 27% |
| Make cost savings/efficiencies elsewhere (n=1) | 3% |
| Other (n=6) | 18% |
| | James Hinde, Research Director
jhinde@djsresearch.com
Julie Hollingsworth, Associate Director
jhollingsworth@djsresearch.com
Clare Rapkins, Senior Research Manager
crapkins@djsresearch.com |
| — | |
| — |
[22] AMDEA and techUK. (2024). Letter to the Government on the UK PSTI regime.
-
For those responding ‘This requirement is not relevant to us’, the responses differed by requirement. Further details are presented throughout the report and in Annex 3. ↩
-
For instance, the NCSC’s Device Security Guidance and information on Secure by Default. ↩ ↩2
-
ETSI stands for the European Telecommunications Standards Institute. ↩
-
See research here: https://www.gov.uk/government/collections/secure-by-design ↩
-
For instance, see: IoT Security Foundation. (2023). The State of Vulnerability Disclosure Policy (VDP) Usage in Global Consumer IoT in 2023. A report prepared by Copper Horse Ltd; or the research at: https://www.gov.uk/government/collections/secure-by-design. ↩
-
Statista. (2024). “Internet of Things - United Kingdom” ↩
-
Statista. (2024). “Internet of Things – Worldwide” ↩
-
Fossil Group. (2024). Fossil Group, Inc. Reports Fourth Quarter and Fiscal Year 2023 Results. Accessed on 25 March 2024. ↩
-
The Association of Manufacturers of Domestic Appliances (AMDEA). (2024). A Year in Review: 2023 report. Accessed on 25 March 2024. ↩
-
British Chambers of Commerce. (2023). “Brexit at three: Fresh trade challenges growing.” ↩
-
Havit. (2023). Presentation about Havit, p.16. Accessed on 25 March 2024. ↩
-
Suunto. (2022). New ownership broadens Suunto’s shoulders in developing fit-for-purpose outdoor products. Accessed on 25 March 2024. ↩
-
Statista. (2024). ”Internet of Things - China” ↩
-
Shirer, M. (2023). “Worldwide Spending on the Internet of Things is Forecast to Surpass $1 Trillion in 2026, According to a New IDC Spending Guide” ↩
-
AMDEA. (2023). A Year in Review: 2023 report, p.15. ↩
-
(2023). Radio Equipment Directive (RED) Delegated Act for Cybersecurity Officially Postponed to 2025: What Does it Mean? Accessed on 22 March 2024. ↩
-
Also confirmed in: The Association of Manufacturers of Domestic Appliances (AMDEA) and techUK. (2024). Letter to the Government on the UK PSTI regime. Accessed on 22 March 2024. ↩
-
Rajnovic, G. (2024). Blogpost: UK PSTI Act 2022 – Examples. Accessed on 22 March 2024. ↩
-
Quocirca Insights. (2024). Blogpost: The UK PSTI Act and its implications for the print market. Accessed on 22 March 2024. ↩
-
Rajnovic, G. (2024). Blogpost: UK Product Security and Telecommunication Infrastructure Act 2022. Accessed on 22 March 2024. ↩
-
See Chapter 2 for a description of the evidence of compliance scale. ↩
-
See, for instance: Framing the Nature and Scale of Cyber Security Vulnerabilities within the Current Consumer IoT Landscape, 2020, Centre for Strategy & Evaluation Services (CSES); and Evidencing the cost of the UK Government’s Proposed Regulatory Interventions for Consumer IoT Products, 2020, RSM. ↩
