Evaluation of the LORCA programme
Published 4 August 2023
Executive summary and key findings
Background: Through the National Cyber Security Strategy (NCSS) (2016-2021) and National Cyber Security Programme, the Department for Digital, Culture, Media and Sport (DCMS) worked with partners across government and industry to develop an ambitious programme of interventions to help grow the UK’s cyber security sector and ecosystem. This included two cyber innovation centres in London and Cheltenham.
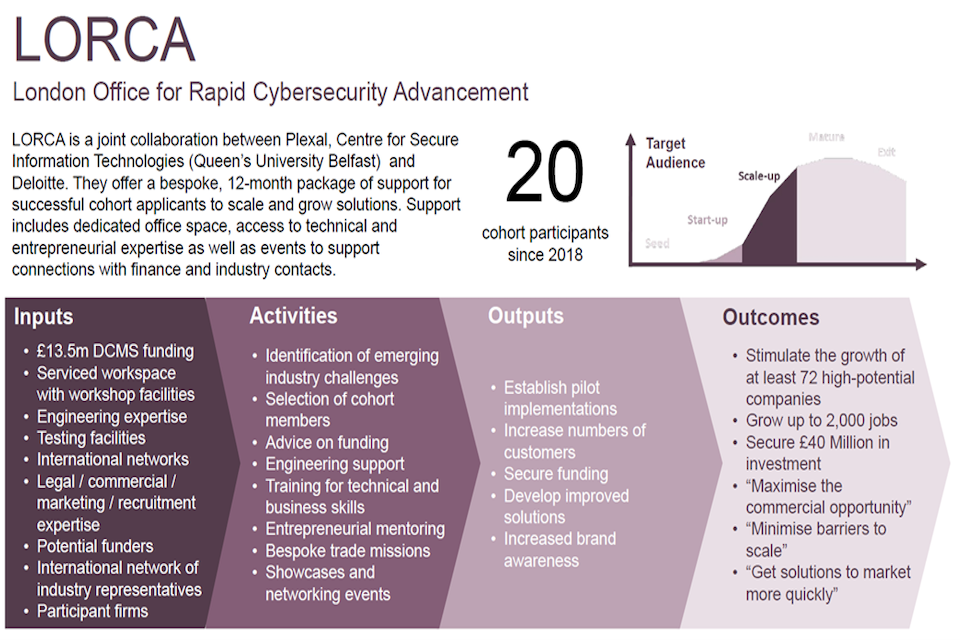
LORCA: The cyber innovation centre in London is called LORCA (London Office for Rapid Cybersecurity Advancement) and it is a joint collaboration between Plexal, the Centre for Secure Information Technologies at Queen’s University Belfast, and Deloitte. LORCA offered a bespoke package of support for successful cohort companies to scale and grow cyber solutions. Support included dedicated office space, access to technical and entrepreneurial expertise as well as events, such as LORCA Live and LORCA Challenges, to support connections with finance and industry experts. Over four years LORCA was tasked with stimulating the growth of at least 72 companies; growing up to 500 jobs; securing £40 million in investment and getting solutions to market more quickly
Scope of the Evaluation: RSM UK Consulting LLP was appointed by DCMS in March 2022 to undertake the evaluation of LORCA with the following aims.
- To determine how the LORCA Programme has performed over the last four years
- To clarify if the programme has produced benefits
- To help DCMS understand the impact of the programme and issues related to government intervention to help grow the cyber security ecosystem
- To explore whether the same benefits would have been achieved without government intervention
This evaluation addresses the complete timeline of the LORCA project, detailing the performance and impact of the project since its inception in 2018 through to March 2022, with a particular focus on:
- the bespoke support LORCA offered through providing space, arranging events, such as the annual LORCA Live conference and networking opportunities, and fostering collaboration
- the LORCA Ignite programme which ran between April 2021 and March 2022 and the extent to which it has supported the scaling growth of six of the most promising companies from within the LORCA graduate community
- the three challenge-led programmes and assessing the extent to which they have encouraged start-ups and industry to co-create new solutions that address these challenges
Methods: The evaluation methodology was agreed with DCMS and included the following:
- a rapid Evidence Assessment to inform the evaluation about the types of variables that should be considered in assessing the success of cyber accelerators;;
- a Theory of Change Workshop to get a sense of how LORCA fitted into the cyber ecosystem and what some of the wider outcomes and impacts were intended
- Mapping the Cyber Security Ecosystem;
- analysis of Programme Monitoring Information and Impact Data from direct beneficiaries of LORCA, including information about (a) growth of companies, (b) jobs secured and (c) investments, to assess the cohort companies’ growth relative to average UK cyber security market growth;
- interviews with 22 strategic stakeholders and an online workshop with programme beneficiaries in May 2022 to explore perceptions of how well LORCA met its core aims and objectives, and suggestions for improvement; and
- recommendations for the future given ongoing changes in the cyber security market.
RSM also completed three different online surveys with (a) all five cohorts of LORCA with a separate section for participants in LORCA Ignite; (b) participants from the three LORCA Challenges; and (c) a counterfactual group of companies matched to the successful LORCA cohort companies. We analysed the impact of LORCA by comparing participating companies to a matched group of similar firms based upon certain Key Performance Indicators (KPIs) such as equity transactions, number of employees, and turnover.
Key Findings: Plexal was awarded the contract from DCMS in 2018, with the initial contract intending this to spread between 2018 and 2021. However, the programme was extended by one year to 2022. LORCA delivered on budget for each of the four years the programme took place. The granting of the extension and the additional costs were due to the addition of several contract variations and an extension of the original programme. LORCA was designed to interact with, and counterbalance, the threats and challenges faced by the industry alongside other programmes within the national cyber security programme.
LORCA captured monitoring information on participants at the beginning of the programme, at a 3-month and a 6-month interval, and at the end of the programme at 12 months. Job growth, investment growth, revenue, number of new contracts and Proof of Concepts, have been collected across all 5 cohorts for the participating firms. The programme delivered on its key economic performance indicators, with the figures below representing the programme’s cumulative performance from the 5 cohorts delivered over 3 years. This includes:
- 72 businesses supported
- 865 jobs created
- £37m of revenue uplift
- £210m investment raised [footnote 1]
In general, the people we interviewed and surveyed in our analysis felt that the Executive Team had done a good job in terms of governance. This is particularly notable when discussing the LORCA management team, who were extremely well thought of by the majority of those interviewed. In terms of the cohorts our review of the criteria used by LORCA to evaluate firms applying to join LORCA concludes that the processes were fair and transparent, and our stakeholder interviews confirmed that the decision making processes were robust and transparent.
Our report describes what worked well and less well in LORCA and there were a variety of different themes that emerged. A dominant theme that emerged was the positive attitudes about the technical support provided during the programme. A key theme that also emerged on the topic of what worked less well was the fact that some aspects of the programme were too generic. This view was held by interviewees in larger companies or who had worked previously in start-ups.
All stakeholders felt that the bespoke elements of the programme and the opportunities for networking pre-COVID-19 were some of the key reasons for the programme’s success. This should be considered in any future iterations of accelerator programmes. As well as this, the success of the challenges should be noted as something to take into future delivery, allowing for an increased connection between government, participants and industry in a way that provides greater support to the sector through its problem-solving focus and attention paid to real-world cyber issues.
We analysed secondary data using the Beauhurst database, which tracks the performance of 82,463 growth firms in the UK, where 1,424 firms operate in the digital security sector. The KPI we used for our assessment was equity fundraising, which was selected as a precursor for business investment; as early-stage firms are more likely to show any potential impacts from the LORCA programme through this metric, given that finance is usually directed towards research and development (R&D) and business development. We found that post-LORCA participation, there has been an upswing in equity fundraisings for participating firms compared to non-participants. The increase in equity raised by participating companies is steeper than that of non-participants, which is an interesting observation; however, caution must be taken when attributing any difference to the LORCA programme given this is an early-stage evaluation and fuller data are still yet to be realised through KPIs such as revenue.
Limitations: Our evaluation had some challenges and hence there are key limitations which must be acknowledged. First of all, the engagement of LORCA firms with our surveys was lower than expected. The nature of the sector and the sensitive nature of some of the questions we were asking perhaps contributed to this low response rate. Secondly, it was difficult to establish a like-for-like counterfactual group of firms to undertake the Difference in Difference (DiD) analysis to evaluate the impact of the LORCA programme. Good data about impact is typically collected over a long period of time. For LORCA, quantifying impacts is difficult as very little time has passed since participants completed the programme, and COVID-19 may have impacted in ways that we are not yet aware of. Typically, realisations of impacts through increased investment in R&D and other broader business activities to generate sales revenue have a lagged element. A future consideration to estimating the impact of the LORCA programme would be through DiD econometric modelling.
Recommendations
- In terms of the future funding, we recommend that funding for the Challenges and some type of annual in-person event for the cyber sector should continue. LORCA has been successful in showcasing a model for future support; whilst DCMS continues to support the UK cyber security sector through programme such as Cyber Runway and CyberASAP, other organisations are also now active in the ecosystem and capable of delivering similar support.
- We recommend that the Challenges continue to be developed further. Several key stakeholders acknowledged the importance of the Challenges in developing closer relationships between participants, industry, and government. The Challenges’ potential for providing actionable solutions to cyber problems was also noted, with some of the findings from challenges already being used to inform government policy. If this potential is realised, it could also develop into a self-sustaining programme, with industry being more likely to fund activities that directly contribute to solving the real-world issues they are facing.
- The bespoke elements of the programme of support should be recognised as a key reason behind LORCA’s positive reviews and should be central in the development of future programmes. This element of the delivery process provided participants with a more well-rounded and useful support mechanism to contribute to future growth. A crucial element in the success of this element of delivery is ensuring a baseline needs analysis is undertaken for all participants when entering any programme to develop a precise understanding of their requirements and areas of interest. We recommend that this baseline needs analysis is undertaken in all future programmes of this nature.
- Transforming an entirely government-funded programme into a self-sustaining model over a relatively short period of time was arguably unrealistic and, therefore, we recommend DCMS consider alternative funding models in their Invitations to Tender for this type of work in the future. From our analysis, it would appear that a shift from this government-funded model to one focused on private funding was simply too great to achieve in the time period given.
- We recommend DCMS considers evaluating the LORCA Programme at a later stage. As with many evaluations of this nature it is too early to be able to draw out any meaningful impacts from the programme. We need more evidence about key performance indicators such as investment and revenue, so that econometric modelling can then be applied to better determine LORCA specific impacts.
Conclusion: Although the evidence we have is limited in some respects, on balance it is fair to conclude that LORCA was delivered on time, to budget and met or exceeded almost all of the original targets it had been set. Aspects of LORCA worked extremely well, such as facilitating networking, and a regular in-person event should continue as well as the challenge-led approach to solving real world problems. LORCA met a need in the cyber security ecosystem at a point in time. However, post-COVID-19, there is not enough evidence to suggest that the decision to cease funding of LORCA should be overturned.
1. Introduction
1.1 Background
The government is committed to making the UK the safest place in the world to be online and the best place in the world to start and grow a digital business. A key aspect of this commitment was the government’s National Cyber Security Strategy (NCSS) (2016-2021) which set out ambitious policies to protect the UK in cyberspace, supported by the National Cyber Security Programme which included £1.9 billion of transformative investment to provide the UK with the next generation of cyber security. [footnote 2]
The Department for Digital, Culture, Media and Sport (DCMS) was responsible for the ‘Develop’ strand in the National Cyber Security Strategy 2016-2021, and worked with partners across government and industry to develop policy for this pipeline. As part of the Strategy, DCMS undertook an ambitious programme of interventions to help grow the UK’s cyber security sector and ecosystem. This included two cyber innovation centres in London and Cheltenham; a programme to support cyber security clusters in spurring economic growth and prosperity across the regions and nations of the UK; a programme to support academics to convert their research into businesses; a series of bootcamps for cyber SMEs, and a scale-up programme to showcase and support the best of the UK’s cyber businesses.
The cyber innovation centre in London is called LORCA (London Office for Rapid Cybersecurity Advancement) and it is a joint collaboration between Plexal, the Centre for Secure Information Technologies at Queen’s University Belfast, and Deloitte.
LORCA offered a bespoke package of support for successful cohort companies to scale and grow cyber solutions. Support included dedicated office space, access to technical and entrepreneurial expertise as well as events, such as LORCA Live and LORCA Challenges, to support connections with finance and industry experts. Over four years LORCA was tasked with:
- Stimulating the growth of at least 72 companies
- Growing up to 500 jobs
- Securing £40 million in investment
- Getting solutions to market more quickly
1.2 Overview of evaluation objectives and methods
Evaluation objectives
The specification for this evaluation stated that DCMS required a comprehensive evaluation of LORCA from its inception in 2018 to March 2022 to measure the impact of the programme and to generate learning to help develop future interventions. [footnote 3]
RSM UK Consulting LLP was appointed by DCMS in March 2022 to undertake the evaluation of the LORCA Programme [footnote 4] and has conducted both an impact and process evaluation with the following aims.
-
To determine how the LORCA Programme has performed over the last four years, and if the programme has met its objectives and policy goals
-
To clarify if the programme has produced benefits other than those outlined in the original business case, including benefits in relation to diversity, reputation and socioeconomic benefits
-
To help DCMS understand the impact of the programme and issues related to government intervention to help grow the cyber security ecosystem and any policy considerations around this
-
To explore whether the same level of benefits would have been achieved without government intervention.
This evaluation addresses the complete timeline of the LORCA project, detailing the performance and impact of the project since its inception in 2018 when the Centre was established through to March 2022, with a particular focus on:
-
the bespoke support LORCA offered through providing space, arranging events, such as the annual LORCA Live conference and networking opportunities, and fostering collaboration
-
the LORCA Ignite programme which ran between April 2021 and March 2022 and the extent to which it has supported the scaling growth of six of the most promising companies from within the LORCA graduate community
-
the three challenge-led programmes organised by LORCA and assessing the extent to which the approach adopted has encouraged start-ups and industry to co-create new solutions that specifically address these challenges.
The full list of Evaluation Questions can be found in Appendix A.
Method
Our approach was based on three key elements:
- A theory-based evaluation using Theory of Change supported by Contribution Analysis
- Comparing KPIs for participants against a counterfactual group of firms. A preferred approach would have been a counterfactual based on DiD modelling to compare outcomes between non-participants and participants; however, due to the lack of data this approach was not statistically viable.
- A rigorous analytical framework to allow the evidence to be triangulated and systematised using a Realist Evaluation approach that identifies what worked, for whom, in what contexts and why.
The evaluation methodology was agreed with DCMS and included the following:
- Rapid Evidence Assessment: We conducted a rapid review of the literature on other cyber security accelerators to inform the evaluation about the types of variables that should be considered in assessing the success of such interventions. This Rapid Evidence Assessment can be found in Appendix B with references in Appendix C.
- Theory of Change Workshop: We conducted a workshop with DCMS staff involved in the design and management of the programme to refine the Theory of Change. The original Theory of Change was quite underdeveloped, so we used the workshop to get a better sense of how LORCA fitted into the cyber ecosystem and what some of the wider outcomes and impacts were intended.
- Mapping the Cyber Security Ecosystem: After reviewing the context in which LORCA was developed, and the business environment within which it operated, we explored how the current cyber ecosystem evolved. This was extremely useful in helping us make recommendations about which elements of LORCA should continue or not be given the establishment of other, newer programmes.
- Analysis of Programme Monitoring Information and Impact Data: We analysed data from direct beneficiaries of LORCA, including information about (a) growth of companies, (b) jobs secured, and (c) investments, to assess the cohort companies’ growth relative to average UK cyber security market growth.
- Stakeholder Interviews: We completed 22 interviews with strategic stakeholders and ran an online workshop with programme beneficiaries in May 2022 to explore perceptions of how well LORCA met its core aims and objectives; suggestions for improvement, and recommendations for the future given ongoing changes in the cyber security market.
- Online Surveys of Innovators: We completed three different online surveys with (a) all five cohorts of LORCA with a separate section for participants in LORCA Ignite; (b) participants from the three LORCA Challenges and (c) a counterfactual group of companies matched to the successful LORCA cohort companies. Response rates in all surveys were low, notwithstanding the challenges around asking businesses to take part in surveys generally. We have attributed the lower than usual response rate to the sensitive and confidential nature of the cyber security sector and the questions we were asking about growth and investment. Whilst we reassured respondents about the GDPR process we would use in collecting and using their data, disclosing financial information and information about equity or, more generally, investment raised by the surveyed companies might have been too sensitive for them to share.
- Counterfactual: We analysed the impact of LORCA by comparing participating companies to a matched group of similar firms based upon certain KPIs such as equity transactions, number of employees, and turnover. Moreover, further filtering was carried out in order to ensure that the counterfactual sample matched the treated firms that participated in LORCA and to obtain a like-for-like comparisons by restricting for geographic location, turnover, and investment Standard Industrial Classification (SIC) code, and other observable characteristics of the companies participating in LORCA. We used the Beauhurst business database in order to retrieve this sample of counterfactual firms.
2. Programme overview
2.1 Introduction
This section outlines the strategic context within which LORCA operates, the rationale for the LORCA programme, how it is delivered and funded, and the extent to which delivery has changed over time since 2018.
2.2 Strategic context
Cyber strategy
LORCA was set up in 2018 to act as a focal point for innovators and cyber security start-up companies in the early stage of their development, as they strove to develop ideas and concepts in collaboration with industry, leading ultimately to the creation of new products and solutions with potential end customers in mind.
The original intention was that LORCA would provide a unique environment where talent, creativity, entrepreneurship, and innovation could flourish. The centre in London would provide an environment in which cyber security start-ups and companies were supported to develop products and solutions in collaboration with industry partners. To support that endeavour, start-ups were provided with access to high-quality support relative to their needs through a holistic and tailored approach
To that end, LORCA was situated within a landscape of core and supporting strategies delivered by DCMS as part of the wider National Cyber Security Strategy 2016-2021. LORCA sits within the ‘Develop’ aim of this strategy in order to:
- improve the UK’s ability to defend and respond to cyber security incidents
- increase the UK’s ability to deter cyber criminals
- develop the pool of cyber security talent in the nation and increase innovation.
The National Cyber Security Strategy recognises that cyber security is also relevant to the following UK strategies:
- Net Zero Strategy: by promoting innovation in a space that has the potential to be low-carbon and build towards the 2050 net zero target issued by the government and delivered by the Department for Business, Energy, and Industrial Strategy. The importance of this transition is shown by the government’s commitment of £5.8 billion since the launch of the Ten Point Plan in November 2020 [footnote 5]
- National Data Strategy: ensuring the systems which are used are secure and allowing the four key pillars [footnote 6] of the strategy to be properly addressed. The cyber security industry is crucial to this, with it being able to contribute to the improvement of data quality and availability, data processing skills, and ensuring that the data is responsibly sourced. The programme, delivered by DCMS with support from key institutions including the University of Cambridge and government departments such as the Department for Business, Energy, and Industrial Strategy, will clearly be positively influenced by a strong UK cyber security sector
- Innovation Strategy: cyber security is key for economic development, and new technologies have an important role. Examples include the Digital Security by Design challenge fund and Security of Digital Technologies at the Periphery (SDTaP) programmes [footnote 7] that will act as key contributors to the UK’s target of becoming a global hub for innovation by 2035 [footnote 8]. Both seek to ensure that cyber spaces are safe, and problems are addressed through academia and industry.
All of the issues that form core parts of these strategies, whilst not directly linked to LORCA in terms of explicit KPIs, had a bearing on how LORCA delivered its programme.
Cyber security context
The UK cyber security industry is growing rapidly. DCMS recorded over 1,800 cyber security firms in the UK in their Cyber Security Sectoral Analysis Report (2022), [footnote 9] which reported double-digit growth in several key business performance indicators. An example of this is the sector’s revenue, which has increased to more than £10 billion for the first time (a 14% growth on the number identified in last year’s Sector Analysis Study [footnote 10]. In addition, the 2022 report highlighted that the sector has added over 6,000 jobs in the past year, with this representing a 13% growth to 52,700 full time equivalents working in cyber security related roles within the industry.
These numbers illustrate the considerable size of the industry and also its potential for further growth, highlighting the significant potential of the industry. The UK is also a global leader in cyber security research, with 19 academic Centres of Excellence in Cyber Security Research, four Engineering and Physical Sciences Research Council (EPSRC-NCSC) Research Institutes, four Centres for Doctoral Training, the Centre for Security Information Technologies (CSIT) and the PETRAS National Centre of Excellence for Internet of Things Systems Cybersecurity. [footnote 11]
Investments in cyber security start-ups are also increasing. Over £821 million was raised in 2020 by dedicated cyber security firms across 73 deals, more than twice what was raised in 2019. [footnote 12] The sector has a critical role in responding to emerging cyber threats and challenges, and in the rapid proliferation of connectable products. However, research in 2020 by the University of Bristol, Imperial College London and the University of Surrey, found that significant long-term investments in other nations, especially the USA, France and Germany, are leading to the development of large clusters of research excellence. [footnote 13] Consequently, based on 2012-2019 levels of investment, the UK is at risk of not only a brain drain, but also endangering its position as a leader in cyber security research and innovation.
According to this research, UK investment in cyber security research falls significantly behind major competitors in absolute terms, and particularly as a percentage of GDP [footnote 14]. Furthermore, said competitors are ahead of the UK regarding their ability to accelerate research commercialisation in order to support innovators to scale-up their businesses. This is done through the provision of a network of partners, investors and corporates providing contacts, information, and capital. Overseas cyber hubs in the US and Israel excel in this area and the UK is facing significant competition despite its strong cyber security industry.
The challenges within the sector and the innovation landscape in the UK include:
- investment being skewed towards larger companies, preventing start-ups and SMEs receiving necessary funding [footnote 15]
- commercialising academic research into cyber security is difficult and there are barriers related to funding, ability to dedicate time to market research and validation, and the need to balance teaching, research, and commercial activity [footnote 16]
- the regional divide in the cyber security sector (33% of registered firms are in London, with only 3% in Wales) [footnote 17]
- half of businesses reported cyber security skills gaps at a basic level in 2021 [footnote 18]
- a lack of diversity in the sector: 22% of the workforce is female (compared to 30% across the digital sectors as a whole). However, ethnic minorities make up 25% of the cyber security sector workforce, which is higher than the 15% of people from ethnic minorities represented across all digital sectors [footnote 19]
- due to Brexit, the UK no longer has access to EU cyber security funding introduced as a priority for the 2021-2027 spending cycle. These programmes include Digital Europe and Horizon Europe, with significant funding. [footnote 20]
Although many of these challenges are general in nature, it is important to recognise how LORCA specifically interacts with some of them. One example is the issue of skewed investment towards larger companies. As highlighted in the LORCA Report 2020, there is a growing issue with investment being heavily weighted in favour of more mature companies. [footnote 21] This could possibly pose a barrier to new cyber security SMEs and start-ups, preventing them from growing or even from forming.
LORCA sought to address this problem through its development of accelerator programmes, providing support for these smaller companies to develop their entrepreneurial skills, their connections within the industry, and their ability to capture funding from investors in order to ensure a higher number reach stability and maturity. LORCA also recognised the issue of a separation between academia, investors and industry support and made collaboration one of its primary goals. Key examples of LORCA activities are listed below:
- Included academics from key institutions within the cyber security space to act in a programme delivery, mentoring and support capacity for participants
- Promoted interaction between investors and participants, as well as other delivery partners, through workshops and networking events
- Included representatives from industry to aid in the delivery and support of the programme and its participants.
COVID-19, on the other hand, was not identified as a challenge to the cyber security industry, according to investors that contributed to the Cyber Security Sectoral Analysis 2022. Most investors believed the pandemic had little or no impact on the sector, and in fact could be said to present a new opportunity for the sector that otherwise would not have been available, by increasing demand for remote working and fostering public awareness of potential secure technology solutions.
2.3. Market context
Growing number of cyber security firms in the UK
As outlined above, the sector is growing with small-sized (24%) [footnote 22] and micro-sized firms (57%) [footnote 23] making up the majority of the registered companies within the cyber security sector. The remainder of the cyber security firms comprised either medium or large-sized firms (18%). [footnote 24] This compares to just about 4% of all businesses across the whole of the UK that were medium or large-sized firms, revealing that businesses in cyber security sectors had a relatively higher proportion of scaling operators. [footnote 25]
Although the total number of cyber security firms increased in 2021, around 6% of the firms were reported to have either dissolved, were under administration, liquidised, or were no longer active. [footnote 26] This is higher than the 5% that was reported the year before, potentially indicating the challenges that some cyber businesses faced over the last 12-months due to the pandemic. [footnote 27]
The number of cyber professionals continues to grow but falls short of demand
The number of Full-Time Equivalent employees (FTEs) also grew from 2020 to 2021, increasing by 13% from 46,673 to 52,727. [footnote 28]In the previous year, employment grew by 9%, showing the sector continued to attract new entrants. [footnote 29]
Despite the overall increase in the cyber security workforce, there exists a shortage of cyber security professionals in the sector overall. [footnote 30] A recent study [footnote 31], for instance, shows that approximately 697,000 businesses (around 51% of 947 surveyed business samples) incurred a basic cyber skill gap [footnote 32], representing the lack of qualified professionals who could carry out the basic level of tasks listed in the government-recognised Cyber Essentials scheme. [footnote 33]
Around 451,000 businesses (33%) have reported that they were affected by a more advanced skills gap, which commonly involved technical skills such as penetration testing, forensic analysis, and security architecture. [footnote 34]
Deal value continued to rise in 2021 despite pandemic pressures
In 2021, the cyber sector saw the number of investment deals decline to 108 from 139 the previous year. [footnote 35] The pandemic may have been a contributing factor to this fall with caution spreading throughout financial markets. However, qualitative investor responses in the Cyber Security Sectoral Analysis 2022 highlighted that investors were likely becoming more selective. [footnote 36] Maturity was becoming increasingly important to investors as firms that were more experienced were favoured in addition to teams underlying cyber expertise. The focus for investors also turned towards innovative and growth areas such as cloud computing, smart cities or internet-based firms. Some investors felt other areas in cyber were already crowded markets and required de-risking through government support. This is echoed through an increase in the total value of deals, from just over £0.8 billion in 2020 up to over £1.4 billion in 2021. The value per each investment deal was higher on average, with £9.4 million per deal in 2021 compared to £5.9 million in 2020. [footnote 37] The investment environment within the cyber security sector also showed signs of gradual maturity and upscaling as cyber firms were successfully enticing more investors who have higher capacity for funding. [footnote 38] Thirty-five investors stated they were able to offer more than £25 million worth of funding by 2021, compared to only twenty-four investors from the 2019 - 2020 period. [footnote 39]
2.4 Delivery context
Programme rationale
LORCA builds on the work of programmes such as Cyber ASAP, HutZero, and NCSC Accelerator. These programmes address the formative stages of start-up and SME development, supporting companies in the development of initial understanding of value propositions, proof of concept and the attraction of seed and pre-seed capital.
LORCA has also been used to inform programmes such as Cyber Runway Grow and Scale. LORCA differs from Cyber Runway Grow and Scale, with Cyber Runway Grow helping start-ups and SMEs to establish sound business foundations and commercialise their ideas and Cyber Runway Scale focusing on removing barriers to national and international growth once the company has developed. Therefore, LORCA overlaps and runs alongside both of these stages of development, with the programme rationale section below providing detail on how it does this and the results of this process thus far.
Figure 1: DCMS Growth and Innovation Ecosystem for Cyber Security
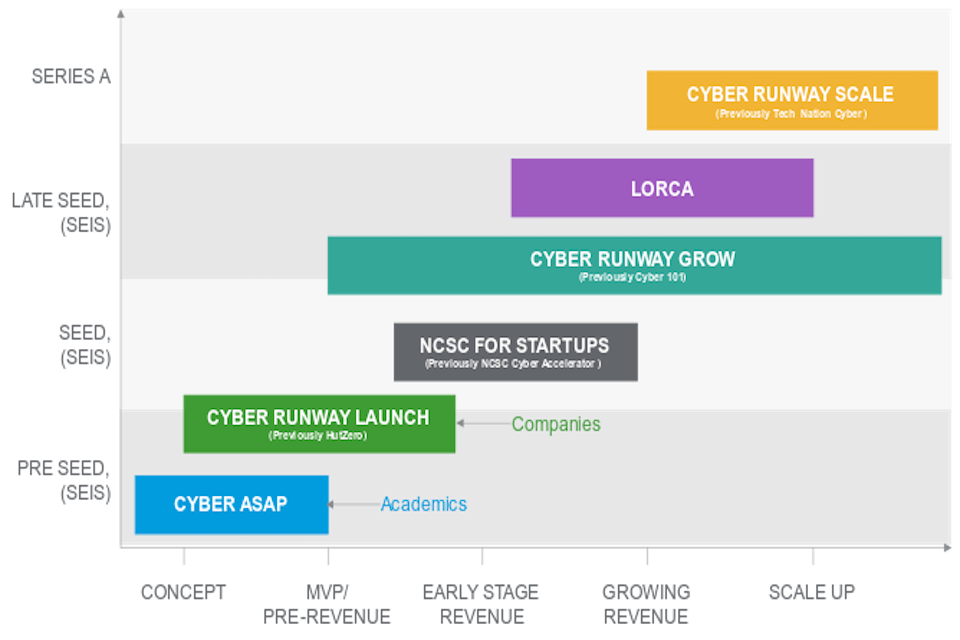
The rationale behind LORCA was to support collaborations between product developers and users by offering support and business mentoring to SMEs and start-ups in order to avoid common circumstances that can often lead to market failure within the cyber security industry. At the time LORCA was established, these market failure-inducing circumstances included:
- information asymmetries
- failures in financing, commercial and entrepreneurial expertise
- access to market, technical and legal advice
- the need for often unrealistic time and financial resources to develop a strong knowledge base.
Funded activities and contract variations
LORCA was awarded an initial contract to run between 2018 and 2021. However, the programme was extended by one year to March 2022. Plexal and the LORCA delivery team intended to use their DCMS funding across the timeline agreed in the initial contract, incorporating individual costs from these areas:
- Programme governance
- Rental/leasing costs
- Training and mentoring costs
- Business advisory support
- Marketing
- Programme outreach
- Monitoring
- Development of programme sustainability
- Cohort recruitment.
LORCA delivered on budget for each of the four years the programme took place. The granting of the extension and the additional costs were due to the addition of several contract variations and an extension of the original programme.
In the first variation in funding received from the original contract, Plexal was asked to carry out research to provide DCMS with evidence regarding the underlying data that drives the cyber security sector and internet-based SMEs, which was then fed into initiatives across the National Cyber Security Programme.
DCMS granted Plexal additional funds in the 2020-2021 Financial Year, due to the unprecedented circumstances of the COVID-19 pandemic. Plexal requested this extra funding to recover expenses incurred when organising the LORCA Live 2020 event, which was cancelled.
DCMS and Plexal extended their contract to 31st March 2022, a year longer than originally anticipated to allow for the engagement of six more companies in the programme LORCA Ignite.
During this extra year, Plexal also received additional funding to develop a third industry-led security challenge based on prior research exploring and documenting 5G security threats. This was carried out to:
- Explore and resolve critical gaps identified in the 5G Security Threat Landscape analysis
- Test the output in a real-world scenario, demonstrating to the UK 5G ecosystem that the output meets the objectives of supporting regionalisation and enabling resilience by tackling critical security challenges in 5G networks.
2.5 Summary
In summary, this section provides detail around the context within which the UK’s cyber security industry operates in order to enhance understanding around the key findings presented in this report. In order to do this, the UK’s position as a global leader in the cyber security space was discussed, and also the core challenges and barriers being faced by the industry as a whole. This facilitates understanding how LORCA was designed to interact with, and counterbalance, these threats and challenges faced by the industry alongside other programmes within the national cyber strategy. In addition, a closer assessment of the LORCA programme itself was carried out, describing programme funding in order to provide an overall context for both the wider cyber security space and LORCA itself.
3. Methodology
3.1. Approach
The Invitation to Tender for the LORCA evaluation required the production of a high-level Theory of Change mapping the inputs and activities that lead to programme goals [footnote 40]. At RSM, our general approach is to situate all evaluative thinking within a Theory of Change. This provides stakeholders with a clear, concise, communicable framework within which to frame the evaluation. Our model looked at:
- Context, Rationale and Assumptions: Why LORCA was needed at that time
- Objectives: What the programme intended to achieve in terms of outcomes
- Inputs and Activities: The ways and means by which the programme achieved its objectives
- Outputs, Outcomes and Impacts: Measurable changes that the programme achieved for those participating in terms of growth in relation to jobs and investment.
The rationale is that if the links between inputs, activities, outputs, outcomes, and impacts can be confirmed, and achievement measured by reference to agreed indicators for each link in the chain, then there is a basis for reaching conclusions on the performance delivered by the programme. Where it is found that there are weaknesses in some linkages within the Theory of Change, then this has an effect on the strength of the conclusions that can be reached. This approach also makes it easier to measure success.
This chapter sets out:
- our approach to producing the Theory of Change
- the research that was carried out to provide evidence for the specified outputs, outcomes and impacts using primary and secondary research.
The section on research methods covers both the process and impact evaluations, as these both drew heavily upon primary research for evidence.
3.2 LORCA Theory of Change
The original Theory of Change for LORCA, as provided by DCMS, is shown in Figure 2 below:
Figure 2: Original LORCA Theory of Change
Based on our review of the documentation and after discussion at a workshop with key DCMS stakeholders a revised Theory of Change was employed to guide the evaluation. There were two major classes of revision:
- The revised Theory of Change explicitly distinguishes between short-, medium-, and long-term effects of the programme
- The revised Theory of Change incorporates many more quantitative indicators drawn from management information on the programme and secondary sources such as the regularly updated DCMS Cyber Security Sectoral Analysis.
Figure 3 shows how the new Theory of Change encapsulates the way in which LORCA fits within the overall change being brought about in the cyber ecosystem. The outputs, outcomes, and impacts were built into our evaluation plan and, where information was not available from secondary sources, questions investigating these were built into our surveys and interviews. Whilst we are unable to report on every single outcome and impact due to the lack of available information, this Theory of Change lens informed all aspects of the evaluation.
Figure 3: Revised LORCA Theory of Change

3.3. Primary data collection
Interviews
We conducted 22 interviews with people from a variety of stakeholder groups related to LORCA and the cyber security ecosystem. The groups to which they belonged were as follows:
- DCMS Policy Staff
- LORCA Programme Staff
- Wider Stakeholders
- Industry/Enterprise Members
- Investors
- Challenge Cohort Problem Owners
During these interviews, a range of key topics were identified as being relevant to all discussions, and a list of questions were developed for each group including:
- Whether delivery of the programme was successful
- What elements of delivery worked, which worked well, and less well, for participants
- How suited the programme’s activities were to the priorities of participants
- What lessons there are to be learned from the delivery methods used
- How external factors influenced the programme
- How the programme could be improved to become more effective
- Whether the programme contributed or led to economic displacement
- The impact of LORCA on participants (investment, business wins, international development).
Surveys
As well as stakeholder interviews, we developed surveys to further our understanding of the LORCA cohort and LORCA challenge experience for the participants. The surveys were aimed at LORCA participants who successfully applied to the programme. They focused on identifying what has worked well and less well in the implementation and delivery of the programme, as well as trying to understand what has motivated firms to apply for the programme and what outcomes have been achieved. The surveys were developed on the SmartSurvey platform, and were categorised as follows:
- LORCA cohort participant survey
- LORCA challenge participant survey.
The LORCA cohort participant survey received a total of 24 complete responses out of the 72 LORCA cohort participants, with the challenge participant survey having 7 responses in total. Each survey ran from 12 April 2022 to 19 May 2022 and, though sent to all relevant parties, was naturally limited in number of responses by how many of those people were willing to complete them fully or to a meaningful degree. This is exemplified by the partial response numbers for our surveys, with the cohort participant survey receiving 13 partial responses, and the challenge survey receiving one partial response. We did not include partial responses as they contained very little relevant information. Response rates are always a challenge with a survey-based approach, but the insight we have gained from these surveys has developed our understanding of the LORCA programme and those who participated in it.
The LORCA cohort participant survey focused on a range of issues related to prior participants, so as to develop our understanding of who they are/what type of company they belong to, their company’s positions before and after LORCA, and their overall view of the programme and its activities. The LORCA challenge participant survey centred on assessing how impactful they have been, as well as what type of company was involved in the process and how their experience could have been improved.
Future Focus workshop
We also conducted a Future Focus workshop over Microsoft Teams with former LORCA cohort participants, in order to develop an understanding of what LORCA did well, and less well, from their perspective. These findings are used in both the process and impact evaluation. In addition to this, we sought to develop an understanding of how LORCA could develop in the future to improve the experience of participants and increase LORCA’s (and similar cyber security accelerators’) positive impact on the ecosystem as a whole. The workshop format was relatively informal in structure, providing the former participants with a platform for open discussion of the LORCA programme. The discussion guide for the workshop was adapted from the topic guides for participant interviews and covered both process and impact evaluation questions.
Analysis
There were several sources used to understand the LORCA programme and the impact it had, some of which included:
- Analysis of monitoring data for each cohort
- Analysis of secondary data: The source used was the Beauhurst database which tracks the performance of 82,463 [footnote 41] growth firms in the UK, where, according to the platform, 1,424 firms operate in the digital security sector. The KPI we used for our assessment was equity fundraising, which was selected as a precursor for business investment; as early-stage firms are more likely to show any potential impacts from the LORCA programme through this metric, given that finance is usually directed towards R&D and business development. The LORCA programme was due to end with the last cohort in July 2021, hence not enough time has passed for firms to incorporate learnings through to changes in revenue. Therefore, the lag in revenue realisations would likely distort any potential impacts. In subsequent evaluations, where a sufficient amount of time has passed following the completion of the LORCA programme, revenue would be the ideal KPI to establish potential impacts. See section 5.3 on secondary data analysis for further details.
- Qualitative framework analysis: Applying a thematic framework to the interview analysis; we coded each transcript with emerging themes to decide which are prevalent or only occur rarely; the combinations in which themes appear; the contexts in which they appear and the strength of perception about certain issues.
- Quantitative analysis: This included descriptive statistics to compare outcomes in a group of similar companies matched for key information such as the average size of firms, their revenue and investment growth. Beauhurst’s platform, which supports a filtering system that allowed us to produce a counterfactual group of firms similar to the treatment group of firms, enabled us to conduct a matching exercise and a like-for-like comparison. The detail of this exercise can be found in Section 5.
The analysis has been shared with DCMS throughout the evaluation, in accordance with the evaluation plan. This report summarises our analysis, conclusions, and recommendations about LORCA.
3.4 Evaluation challenges and limitations
The team at RSM were faced with a number of challenges during this evaluation. These have shaped, and to some degree limited, the evaluation process and its findings. These included:
- Willingness to cooperate and low response rates to surveys. The engagement of LORCA firms with our surveys was lower than expected. Despite two reminder emails issued on our behalf by Plexal, the response rates remained low.
- The nature of the sector and the sensitive nature of some of the questions we were asking perhaps contributed to the low survey response rate.
- One limitation we noted from our workshop was the lack of diversity in the ages of participants. This was remarked upon by some of the workshop participants, who suggested that younger LORCA cohort participants might have different views on key topics. However, we were once again limited by who was able and willing to attend.
- It was difficult to establish a like-for-like counterfactual group of firms to undertake the DiD analysis to evaluate the impact of the LORCA programme. Section 5.3 on secondary data analysis provides further detail
- Good data about impact is typically collected over a long period of time. For LORCA, quantifying impacts is difficult as very little time has passed since participants completed the programme, and COVID-19 may have impacted in ways that we are not yet aware of; therefore, being able to report on the causal relationships between DCMS funding and impacts is difficult.
- The data used to evaluate LORCA’s performance consisted primarily of the monitoring information provided through LORCA to DCMS.
4 Key findings: programme delivery and performance
4.1 Overview
This section assesses the performance of LORCA and how it was delivered from 2018 until the programme ceased in March 2022. It addresses the following evaluation questions:
- Was the programme delivered as intended?
- What worked well, or less well, for whom and why?
- Were there any unexpected or unintended issues in the delivery of the intervention?
- What can be learned from the delivery methods used?
- How did external factors influence the delivery and functioning of the programme?
- How can the existing programme be improved to become more effective?
- To what extent were the activities suited to the priorities of the participants?
We summarise what LORCA has achieved to date and present findings in relation to the above questions.
4.2 Programme delivery
LORCA represented a shift towards the introduction of regional cyber security hubs that would aid in the acceleration and growth of cyber security companies, whilst also providing space for increased innovation and collaboration. The programme was delivered by Plexal (offering a common workspace and support network containing commercial and technology validation clinics, access to investors, mentoring opportunities and national as well as international support and events), in collaboration with Deloitte (access to virtual validation testing) and the Centre for Secure Information Technologies (academic and engineering support), as well as other partners (AHL Connect, Outfly, Informed Funding and InfoSec People among others to provide ongoing support), with members also benefiting from international trade delegations, mentoring and workshops on several key aspects of the industry.
Key outcomes expected
Over the period of 2018 to 2021 LORCA was expected to support 72 companies in the scaling process in order to create up to 500 jobs and secure £40 million investment. By January 2022, it had supported five cohorts, provided a platform for further investment, introduction to new markets, and increased talent retention.
Each cohort focused on specific issues identified by a panel of industry leaders, addressing topics such as supply chain security. This allowed for different problems to be addressed by each cohort, with programme partners such as Dell Technologies referencing the importance of these cohorts in developing the UK’s ability to adapt to the array of cyber threats currently present [footnote 42].
New elements of the programme were introduced in response to changing industry needs. For example, the Challenges were introduced to the programme to act as a problem-focused initiative aimed at developing real-world solutions to cyber issues and strengthening ties between LORCA participants and the wider industry. To date, three challenges have been completed and have assessed issues related to three key industry areas:
- Telecoms Diversification
- Connected and Autonomous Vehicles
- Network Vulnerabilities.
In addition, LORCA Ignite was introduced in 2021, inducting six of LORCA’s most successful scaleups into an intensive six-month programme. LORCA Ignite aimed to build on the accelerators provided within the central LORCA programme, offering an increased level of support to those selected in the form of commercial and technology validation clinics; access to investors and mentoring services, and access to national and global networks.
Please note that just because these impacts occurred since the start of the LORCA support, it does not necessarily follow that they arose because of the LORCA support, or that the companies would not have found a different way to achieve these impacts to some extent in the absence of LORCA. Section 4.9 on “economic indicators” and “additionality” at the end of this chapter discusses this further.
4.3 Roles and responsibilities
The information below provides further detail on roles and responsibilities of the main organisations involved with LORCA:
Table 3: Roles and responsibilities of LORCA organisations
| Stakeholder | Role |
| DCMS | Funder and management oversight of the LORCA programme |
| Core delivery team | |
| Plexal | • Programme management • Provide core programme team • Space and facilities provision • Marketing and start-up recruitment • Industry engagement • Government engagement • Provision of start-up professional services • International outreach • Annual cyber summit (LORCA LIVE) and Challenges |
| Deloitte | • Programme management • Industry engagement • Government engagement • Cyber SME and technical advice • Business mentoring • International outreach • Annual cyber summit • Remote lab access |
| Centre for Secure Information Technologies | • Academic engagement • Government engagement • Cyber SME and technical advice • International outreach • Annual cyber summit • Remote lab access |
| Partnerships with established bodies | |
| Industry partners | Included Lloyds Banking Group, Kudelski Security, Global Cyber Alliance, KX, Amazon Web Services, SOSA, Splunk, and DELL Technologies |
4.4 LORCA governance
The governance structure for the LORCA programme centred around an Executive Board at Plexal responsible for delivery. However, they were also assisted by an Advisory Board made up of industry stakeholders.
Executive board
The purpose of the Executive Board was to review management of the programme, oversee performance ensuring that LORCA goals, objectives and targets were met, and provide strategic guidance to LORCA. The Executive Board met each calendar month, ensuring that insights from key stakeholders, e.g. the Industrial Advisory Board (IAB), Finance Forum and Innovation Forums, informed the ongoing delivery and strategy for LORCA.
In general, the people we interviewed and surveyed in our analysis felt that the Executive Team had done a good job in terms of governance. This is particularly notable when discussing the LORCA management team, who were extremely well thought of by the majority of those interviewed and the efforts of the LORCA delivery team were also recognised in the survey responses.
We have greatly benefited from our involvement with LORCA over an extended period, and we also value the relationships we’ve built with the LORCA delivery team (including the delivery partners) over that time. Great to see Plexal and LORCA going from strength to strength over the past 3 years.
LORCA Cohort Survey Participant
DCMS had the vision early on, and the Director at Plexal was brilliant. What’s worked well in the delivery partnership has been the relationship and understanding that we are all in this together.
LORCA Programme Staff
LORCA Industrial Advisory Board
Plexal recognised it was essential to bring a degree of independence to the leadership and governance arrangements of LORCA and so they set up an Industrial Advisory Board (IAB). From the programme documentation reviewed, we established that the IAB met three times a year to advise on the direction and delivery of the Centre.
Other functions of the IAB included:
- receiving briefings on upcoming and existing cohorts
- identifying research results that are appropriate for rapid commercialisation
- highlighting shifts in technology, market demand or new business models
- advising on the content and emphasis of the Centre’s training activities
The small number of participants we interviewed on the issue positively spoke about the LORCA Advisory Board, saying the IAB provided the programme with an outlet to focus on where the ecosystem as a whole was moving, and how LORCA could best maintain relevance in an ever-changing environment. This fits with the recognised purpose of the advisory board, with its role being to focus more on the industry and LORCA’s direction of travel than the specific design and delivery elements of the programme.
The advisory board’s original purpose was not to micro-manage or act as an executive board, but rather to act as a sounding board and discuss the direction of the industry.
Wider Stakeholder
DCMS
The final element of governance that is important to recognise is the relationship between programme management and DCMS. As noted by a DCMS staff member, the maintenance of consistent contact between the two organisations was important. This allowed for feedback to be delivered effectively and ensured that the delivery teams were aware of what DCMS were expecting from the programme. Those who took part in stakeholder interviews believed that this relationship was managed successfully, with DCMS and programme staff members both recognising the consistency of meetings surrounding risk, programme management and KPI delivery. The quote below illustrates how a DCMS staff member made it clear from the outset what their expectations were:
“We engaged a lot with start-ups, using monthly meetings with LORCA management to develop information and feedback. Having these discussions meant that they knew we were expecting to see that there was value being created for participants.” – DCMS Staff
Application process
Demand for the first cohort was low, with 9 participants selected out of a total of 10 applications. However, as the LORCA programme became better known the number of applications for subsequent cohorts increased, and the percentage of companies that were selected fell accordingly.
| Cohort | Cohort Participants | Total Applications per Cohort | % Companies Selected |
| Cohort 1 | 9 | 10 | 90 |
| Cohort 2 | 11 | 23 | 48 |
| Cohort 3 | 15 | 43 | 35 |
| Cohort 4 | 20 | 79 | 25 |
| Cohort 5 | 17 | 55 | 31 |
For LORCA there were some eligibility requirements and applicants needed to be:
- A fast growth company with technology that matched the programme’s innovation themes
- Have generated revenue and/or raised capital
- Have a business relevant to cyber security
- Be a UK registered company.
Moreover, companies were also considered for LORCA based on their active market development strategies and desire for growth. Businesses that had already generated revenue were preferred over those that had just started looking for customers, as were businesses that were developing products to meet user-centric market requirements. Similarly, companies that promoted commercial opportunities with a clear plan for engaging customers were more likely to be accepted onto the programme than those that did not.
The application process consisted of the following steps:
- Application form
- Scoring and Shortlisting
- Evaluation Day (Live pitching to a panel of evaluators)
- Final Scoring and Selection.
Our review of the criteria used by LORCA to evaluate firms applying to join LORCA concludes that the processes were fair and transparent, and our stakeholder interviews confirmed that the decision-making processes were robust and transparent. Some of the criteria used to make decisions included impact, innovation, sustainability, capacity, and programme need and fit. We do not have sufficient information to draw any conclusions about the efficiency or effectiveness of the application process, for example, how quickly applications were reviewed, but it may be something that DCMS might want to consider monitoring in the future.
4.5 Support provided
As part of the LORCA programme, there was an intensive six-month support period, followed by a less intensive six-month period. During the first six months, the programme generally consisted of the following components, which were tailored to meet the specific needs of each cohort company:
- One to one weekly support on cyber commercial and cyber technical support, marketing support, legal advice, investment-readiness and sales support
- Academic masterclasses
- Professional services masterclasses
- Access to the finance community (via a quarterly finance forum)
- Access to inward and one outward bound trade delegation
- One to one and group engagement with corporates and buyers
- A mentor, where demand and supply align
- Exhibiting space at LORCA Live and other LORCA-supported external conferences.
In the second six months of the programme there was a significant reduction in one-to-one support for cohort members, but free attendance to group sessions, as well as the use of the Plexal environment and desks, continued during that period. Given the approach that LORCA took to facilitating meetings and networks, and expecting that initial introductions could snowball into a whole range of other contacts, and coupled with a lack of mandatory reporting to capture every activity, there is not sufficient information to be able to report adequately of the extent of take-up of each individual aspect of support by company.
4.6. LORCA participants
Plexal captured monitoring information on participants at the beginning of the programme, at a 3-month and a 6-month interval, and at the end of the programme at 12 months. Job growth, investment growth, revenue, number of new contracts and Proof of Concepts, have been collected across all 5 cohorts for the 72 participating firms. The data was usually self-reported by participant companies, and independently cross-checked and validated by Plexal’s team by researching public datasets and desk-based research.
Table 4 below outlines the companies in each cohort that took part in the LORCA programme.
Table 4: LORCA cohorts
Cohort 1: 07/2018-07/2019 (9 companies): Aves Netsec, B-Secur Ltd, CyberOwl, Cybershield (Aquilai), Ioetec, ThinkCyber, Surevine, Trust Elevate, Zonefox
Cohort 2: 01/2019-01/2020 (11 companies): Ampliphae, Bob’s Business, Crypto Quantique, CyberSmart, CyNation, Distributed Management Systems, ObjectTech Group, OutThink, Privitar, RazorSecure, Xanadata
Cohort 3: 06/2019-06/2020 (15 companies): CounterCraft, CTO Technologies, D-RisQ, Elemendar, Hack the Box, Human Firewall, Messagenius, Panaseer, Quant Network, Salt DNA (Salt Communications), Security Alliance, Storage Made Easy, SwIDch, Threat Status, Uleska
Cohort 4: 01/2020-01/2021 (20 companies): Acreto, Anzen Technology Systems, Avnos, Contingent, Continuum Security (Irius Risk), Darkbeam, Heimdal Security, Kinnami, Keyless Technologies, L7 Defense, Orpheus, Osirium, Risk Ledger, ShieldIOT, SureCert, ThreatAware, ThunderCipher (Licel), Variti, VIVIDA, Westgate Cyber Security (Enclave Networks)
Cohort 5: 07/2020-07/2021 (17 companies): AdvSTAR, BlockAPT, BreachLock, CapsLock, ContextSpace, CyberHive (100 Percent IT), InsurTechnix, ITsMine, MIRACL, Nanotego, RedHunt Labs, The CyberFish Company, Truststamp, VerifiedVisitors (GleveVentures), VU Security, Zamna, ZeroGuard
LORCA IGNITE (6 companies): Ampliphae, Crypto Quantique, CyberOwl, CyberSmart, Risk Ledger, Salt Communications,
A fuller description of all companies that took part in LORCA is given in Appendix H.
LORCA participant background information
The information shared from Plexal about LORCA participating companies did not include information on the companies’ leadership structure or geographic location. So, in the absence of these data, we used Beauhurst to gather information about the characteristics of the participating companies in the programme. Beauhurst did not track data for all 72 participating companies in the programme since some of them are not based in the UK. Therefore, this analysis is based on a sample of 55 out of the total of 72 firms. [footnote 43] A separate analysis of the available information on the 17 international firms is provided at the end of section 5.3.
We analysed the following characteristics for each company:
- Directors and founders gender identity
- Company location
- Sector in which they operate
- Type of company and corporate structure.
Directors’ and founders’ gender identity
Monitoring information about the gender of the directors and founders of the sample of LORCA companies shows a significant weighting towards males. In our sample of 55 LORCA companies, 52% of the firms do not have any female directors and 69% do not have any female founder. Among 55 companies, only five (9%) have all of their directors identifying as female. There are three companies in which more than 50% of the founders are female, two of which have all female founders.
Company location
In our LORCA sample, more than half of companies (53%) are based in London. The second largest group of companies is based in the South East of England (16%), and the least represented regions are the East and South West of England, as well as Wales, each with one company (2%).
Sector code
Standard Industrial Classification (SIC) Code 2007 identifies the industry in which Beauhurst’s sample of LORCA participants operates. SIC codes are used to classify business activities. The sample we are analysing falls into the following categories:
Table 5: SIC codes
| SIC Codes 2007 - Group | Sample of LORCA participating firms -frequency | % |
| NA | 1 | 2% |
| C - Manufacturing | 1 | 2% |
| J - Information and communication | 45 | 82% |
| K - Financial and insurance activities | 1 | 2% |
| M - Professional, scientific, and technical activities | 1 | 2% |
| N - Administrative and support service activities | 4 | 7% |
| P - Education | 2 | 4% |
It is evident from the table above that the bulk of our sample (82%) comes under the ‘information and communication’ category. This includes activities such as business and domestic software development as well as information technology consulting.
Type of company
In our sample from Beauhurst, almost all of the LORCA programme firms are private companies (98%), with one datapoint missing. In addition, 89% of companies in the sample, regardless of whether they are part of a wider group of companies or not, are the ultimate parent company and are not owned by mother companies.
4.7 Performance
The source used to evaluate LORCA’s performance consisted primarily of the monitoring information provided through LORCA to DCMS.
Performance against key performance indicators
The evaluation of LORCA against its KPIs for the period is based on data collected from the log frames provided by DCMS and LORCA and is presented in the form of tables, with each table analysing the relevant indicators, measurements, targets, and status of each of the five KPIs. These KPIs are:
-
LORCA delivers growth and support for high potential business up to 31 March 2022
-
LORCA addresses unmet real-world cyber security challenges
- LORCA supports the increased adoption of innovative cyber security technology across private and public sectors
- LORCA contributes to the overall UK cyber ecosystem supporting growth and diversity in the sector and is a convening force across cyber security community
- LORCA is sustained beyond March 2022.
Table 6: LORCA delivers growth and support for high potential business up to 31 March 2022
| Indicators | Indicative Measures | Targets | Evidence | Status |
| Project delivery milestones are being delivered on time, in budget and to the satisfaction of DCMS | Percentage of milestones delivered on time. Percentage of milestones delivered within budget forecast | 100% milestones delivered to time and budget agreed | Log frame reports | Delivered |
| The centre provisions are relevant to the needs of cohort participants | Qualitative and quantitative data is collected by a confidential cohort questionnaire | Average quantitative feedback score is greater than or equal to 7 (as decided by DCMS) and qualitative feedback is shared with DCMS as required | Monitored by DCMS. | Delivered |
| Cohort companies’ growth relative to average global and UK cyber security market growth | Revenue growth. Funding raised. Jobs increased. | Tracking of ongoing growth relative to average global cyber security market growth as measured by % growth increase | Log frame reports | Average revenue increase - 49%; Investment raised £2.1m (25% increase); 16 jobs created (9% increase)* |
Note: * These figures are reported verbatim from the log frame reports. The overall investment and jobs growth targets were exceeded (see paragraph under Table 10).
Source: LORCA Log Frame, March 2022
Table 7: LORCA addresses unmet real-world cyber security challenges
| Indicators | Indicative Measures | Target/s | Evidence | Status |
| Number of corporates participating in the Innovation Forum and /or providing mentors to programme and Centre activities | Number of different companies involved in mentoring and / or innovation forum / challenge-led activities / convened events | 10 Companies | Log frame reports | Delivered |
| Proportion of industry challenge list contributors working directly with the LORCA ecosystem to address specific challenges and needs | Number of problem-owners / challenge sponsors per challenge-led project | Minimum of 2 per challenge-led project | Challenge Reports | Delivered |
| Proportion of LORCA cohort and alumni members working on solutions directly aligned to unmet real-world security challenges. | Percentage of members selected who align with identified challenge areas | 90% | Monitored by DCMS. | Delivered |
Source: LORCA Log Frame, March 2022
Table 8: LORCA supports the increased adoption of innovative cyber security technology across private and public sectors
| Indicators | Indicative Measures | Target/s | Evidence | Status |
| Number of industry trials/proofs of concept secured through participation in LORCA | Percentage of members who develop / secure new PoC/ trials as a result of / or through the cohort programme;Number of new PoC/ trials in place as a result of / through cohort programme | 50% of members 5 new PoCs/trials | Monitored by DCMS. | Delivered |
| Number of business introductions secured during time as a LORCA member, or as a result of membership | Percentage of members who develop/secure new business contacts as a result of /or through the programme. Number of new business introductions made per company, per quarter | 80% of members 3 new business introductions | Monitored by DCMS. Evidence received. | Delivered |
| Number of introductions to government-related projects or opportunities as a result of being a LORCA cohort or alumni member | Percentage of members who are proactively introduced to cross-government initiatives such as NCSC, MoD, ACE etc.Number of introductions to major government suppliers/ primes as a result of being a LORCA member, per company | 30% of members 2 Introductions | Monitored by DCMS. Evidence received. | Delivered |
Source: LORCA Log Frame, March 2022
Table 9: LORCA contributes to the overall UK cyber ecosystem supporting growth and diversity in the sector and is a convening force across the cyber security community.
| Indicators | Indicative Measures | Target/s | Evidence | Status |
| Consistent engagement with the LORCA Cohort, Alumni and Ecosystem network | Huddles with the Cohort members; Number of targeted broadcast emails to Cohort and Alumni network per quarter; Number of monthly LORCA update emails to Ecosystem mailing list per quarter | 6 Huddles 9 targeted broadcast emails 3 monthly LORCA update emails | Log frame reports | Delivered |
| Numbers of non-Cohort members utilising the Centre or joining the LORCA ecosystem | Percentage of non-cohort members joining the Centre or LORCA ecosystem | 20% of total LORCA cohort and alumni number | Log frame reports | Delivered against a target of 14 members |
| Increasing gender and ethnic diversity across the LORCA network | Percentage of female-founders / female senior leaders within LORCA alumni and cohort community;Percentage of BAME founders / BAME senior leaders within LORCA alumni and cohort community;Number of virtual or physical events/ roundtables/ meetups delivered or supported with a focus on engaging underrepresented entrepreneurs within cyber security e.g., Women in Cyber, CyberFirst support etc | Ongoing measurement and reporting. Proactive encouragement for LORCA Cohort and Alumni members to embed increasing diversity into their company’s core values and talent strategy. 2 Events | No evidence received. | Verbal feedback that some progress was being made. An ongoing issue for the sector |
| Number of cluster, academic and international ecosystem partnerships | Number of partnerships through MoU in place | 10 Partnerships | Monitored by DCMS. | Delivered |
Source: LORCA Log Frame, March 2022
Table 10: LORCA is sustained beyond March 2022
| Indicators | Indicative Measures | Target/s | Evidence | Status |
| Lead generation activities to support future private-sector funding for LORCA | Number of meetings per month; Number of partnership leads generated; Number of convening events with private sector stakeholders | 5 meetings 2 partnerships1 convening event per quarter | No evidence received. | Delivered activities but no funding forthcoming |
| Partnership renewals | Percentage of LORCA partnerships renewed during 2021/22 | 90% | Monitored by DCMS. | Delivered |
| Volume of private funding for LORCA related activities | Income amounts from private sector sources | >300k by 6 months>500k by 12 months | Monitored by DCMS. | Delivered |
Source: LORCA Log Frame, March 2022
This analysis, drawn from the log frame report dated 28th March 2022 indicates how LORCA met most of its key performance indicators. The success of LORCA is showcased by the fact that the majority of KPI indicators were delivered or exceeded. In summary, a cumulative assessment of the LORCA programme (from 5 cohorts delivered over 3 years) finds that LORCA has surpassed its investment and job creation targets, with £210 million in investment raised (original target of £40 million) and 865 jobs created (original target of 500). [footnote 44]
Was the programme delivered as intended?
In order to answer this question, we utilised a range of sources, including interviews with stakeholders, workshops with former LORCA participants, and participant survey data so that we could provide a detailed and unbiased view of how the programme was delivered.
In interviews, we found that the LORCA programme staff spoke very positively around the issue of programme delivery, feeling that LORCA did meet all its objectives. Evidence of this has been present in this report, highlighted by the programme’s success in either meeting or surpassing job creation and revenue targets. However, it is important to note that analysis of both the delivery staff / those involved in the process and the views of participants is required to present an unbiased and balanced view of the programme. The quotes provided below demonstrate the survey participants’ positive view of programme delivery, with a clear focus being placed on the importance of bespoke training sessions and workshops that contributed to a general improvement of skills within the participant base. This is highlighted in participant and staff quotes provided, with these one-to-one mentoring sessions and workshops being regarded as the element of delivery that separated LORCA from other relevant cyber accelerators.
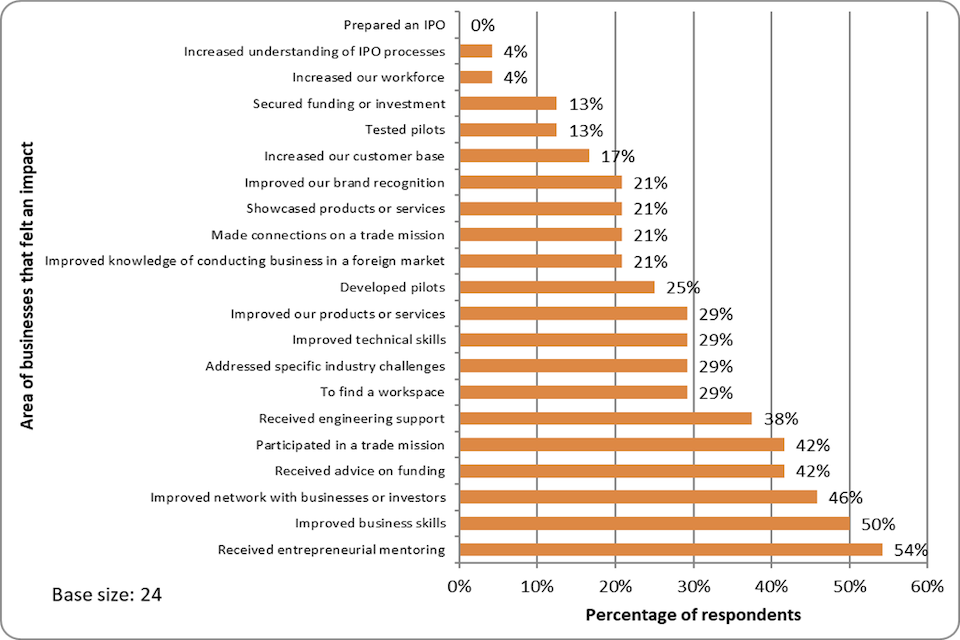
Figure 4 illustrates that 50% of those surveyed (i.e.,12 respondents) felt they had experienced business skill development as a result of LORCA. This is particularly notable when considering that, according to the percentages presented, only one other aspect of the programme received a higher proportion of the vote. This highlights the crucial role that business skills support played in a programme that both staff members and participants felt had been delivered successfully.
The mentoring sessions were extremely helpful because they helped us prepare for discussions with potential customers.
LORCA Cohort Survey Participant
The one-to-one support to LORCA participants from corporate partners, this was the best out of the couple accelerators we took part in.
LORCA Cohort Survey Participant
Figure 4: How participation in LORCA has impacted the cohorts
(percentage reporting an impact, multiple answers permitted)
In addition, it can be seen that the LORCA programme has supported the growth of the participant companies through the provision of a strong and active governance structure within the programme. Though Plexal was relatively new to the cyber security accelerator space, stakeholders consistently pointed to the importance of LORCA and DCMS leadership in the programme’s success. LORCA leadership was referenced multiple times when discussing the positive elements of the programme’s delivery, as highlighted both by quotes from programme staff below, but also by LORCA participants, with one participant highlighting their support for the level of organisation and the quality of key programme delivery teams.
I suppose what has worked well is the governance and the leadership. We have a good advisory board and brought together a good executive team.
LORCA Programme Staff
The organisation and the quality of the executive and support team. Excellent engagement, excellent mentors. Excellent introductions and opportunities.
LORCA Cohort Survey Participant
One important aspect of the delivery process that was less successful, however, was LORCA’s evolution into a self-sustaining cyber security accelerator. Despite DCMS making this central to the aims of the programme in its initial development phase, this goal is yet to be achieved. Several interviewees noted the lack of interest or action from industry in replacing DCMS as the central financers for LORCA. One DCMS staff member even suggested that this aim may have been unrealistic in nature, but the fact remains that LORCA was unsuccessful in delivering this objective.
It was probably unrealistic for LORCA to continue in the way we set up sustainably
DCMS Staff
No one has been willing to step into our shoes.
DCMS Staff
What worked well and less well?
In terms of what worked well and less well, there were a variety of different (and sometimes contradicting) themes that emerged. Starting with what went well, a dominant theme that emerged from interviews and the free-text survey responses was positive reviews of the technical support provided during the programme. Primarily stemming from the Centre for Secure Information Technologies (CSIT) involvement in the programme as delivery partners, this view was supported by both LORCA programme staff and DCMS staff. This was the result of CSIT’s ability to provide a testing and support service for participants on the LORCA programme.
The technical piece on the engineering side. That was something that was quite unique and quite different
LORCA Programme Staff
When I joined, I felt that the feedback I was getting and the sense was that one of the stronger partners in the LORCA consortium was having CSIT on board
DCMS Staff
Very well organised for technical workshop and the quality of speakers and mentors.
LORCA Cohort Survey Participant
However, a key aspect of the programme that was not perceived as working quite as well was Plexal’s location in the former Olympic Park in East London. Though this issue was lessened by the impact of COVID-19 and the development of a virtual delivery model, it is important to note that this was repeatedly referenced by participants and wider stakeholders as an issue. This largely stemmed from issues surrounding the time required to travel there from Central London and further afield. One stakeholder interviewed for our analysis argued that it could have made the process of attracting key technical experts more difficult. This suggests that the location could have a negative impact both on participant experience and the development of collaborative engagements with experts. Whilst it is important to note that this theme is specifically centred on the issue of travel to Plexal’s location rather than the resources/facilities provided once there, these facilities will not be properly utilised if the travel is too inconvenient or costly for stakeholders and participants. This could also be seen as further evidence of the need for a more regionally diversified presence in the cyber accelerator space, in order to avoid any exclusion for regionally dispersed participants.
It was a long way to travel for single one hour sessions. Multiple events on the same day made the amount of travel time more worthwhile
LORCA Cohort Survey Participant
Location in Stratford is awkward, making it difficult to get technical experts to interact there.
Wider Stakeholder
Travel to LORCA from Northern Ireland was always a bit more difficult, and in particular added significant cost to our participation
LORCA Cohort Survey Participant
A key theme that also emerged on the topic of what worked less well was the fact that some aspects of the programme were too generic. This view was held by interviewees in larger companies or interviewees who had worked previously in start-ups. As a result of their increased experience, the less tailored elements of the programme had a greater chance of covering areas these companies no longer needed help with. This became an issue as the programme needed to successfully cater to as much of the participant base as possible in order to succeed. Whilst development in this area over time was noted, and the issue became less relevant as the programme became more mature, it is important to note this theme as it was raised by several stakeholders.
Broadly Speaking, the bigger the company the less need for the generic piece
LORCA Programme Staff
Some of the support was quite academic, generic and basic.
LORCA Cohort Survey Participant
What can be learned from the delivery methods used, and how can the programme be improved?
As has been made clear throughout the analysis so far, the key lesson learned from delivery was the importance of the bespoke elements of the programme. All reviews of this element of delivery during the interviews were positive, with many highlighting it as a key reason for the programme’s success. This is showcased in several quotes already provided from interviews and should, therefore, be considered as a focal point for any future iterations of the programme or those similar to it. In addition, the success of the challenges should be noted as a lesson learned and something to take into future delivery, allowing for an increased connection between government, participants, and industry in a way that provides greater support to the sector through its problem-solving focus and attention paid to real-world cyber issues.
The outputs and outcomes from the challenges are generally positive, with this specifically emphasised by the use of findings in informing government policy.
LORCA Programme Staff
The success of the challenges did not mean that they were perfect, however, and there are still more critical lessons to be learned from them. Specifically, a challenge cohort problem owner noted that improvements could be made in exploiting the results of the challenges in order to ensure maximum impact from the process. Though it was noted that this is difficult to achieve, the theme of ensuring maximum impact from challenges was a repeated one. Another interviewee noted that, despite feeling the challenge was successful, it perhaps raised more questions than it answered. These themes would suggest that, going forward, those running the challenges must ensure that the work translates to the development of real-world solutions in order to properly deliver on the challenges’ aims and objectives.
For other stakeholders, it probably just raised more questions
Challenge Cohort Problem Owner
I would look to focus on how we can exploit the results of the challenges
Challenge Cohort Problem Owner
Participant feedback on the challenges, as shown in Figure 5, provides support for the themes presented above. The vast majority (86%) of those surveyed described the experience as ‘excellent’. This is furthered by the fact that none of the survey participants rated their experience any lower than ‘good’. Despite this, the survey analysis also mirrored the view that more could be done to ensure the outcomes of the challenges are properly utilised. 71% of participants felt there were still gaps in the challenges, with multiple participants indicating the need for more concrete outcomes and a clearer understanding of what happens after the challenge as the reason for this. However, it is important to note that the base size is relatively small, and that the data must be interpreted cautiously.
Figure 5: Participant feedback on Challenges: rating of experience of taking part
This may not be a gap as such, but we received the final report but do not know the next steps. I don’t know whether we can share the details or report itself, or when we may be able to discuss something akin to a proof of concept. It hasn’t been long since the report was published, so this is not a criticism as I expect to have these answers in the coming weeks!
LORCA Challenge Survey Participant
More concrete outcomes please
LORCA Challenge Survey Participant
In addition to this lesson learned from the challenges, one of the Future Focus workshop participants noted that they had not been approached for, nor been made aware of, a specific challenge that would have been particularly useful to their company. This is clearly a gap in delivery, and something that should be developed in the future, in order to ensure maximum participation and engagement from key participants and stakeholders.
No, the challenges passed us by. Autonomous vehicles would have been interesting to us.
Future Focus Workshop Participant
How did external factors influence the design or delivery of the programme?
Survey participants agreed with the view that COVID-19 had an impact on the programme, but the majority did not feel that this impact was overly sizeable. This is shown by almost half (48%) agreeing that LORCA was moderately impacted by the pandemic.
Figure 6: How COVID-19 Impacted Delivery: extent to which COVID-19 affected the outcomes achieved because of LORCA
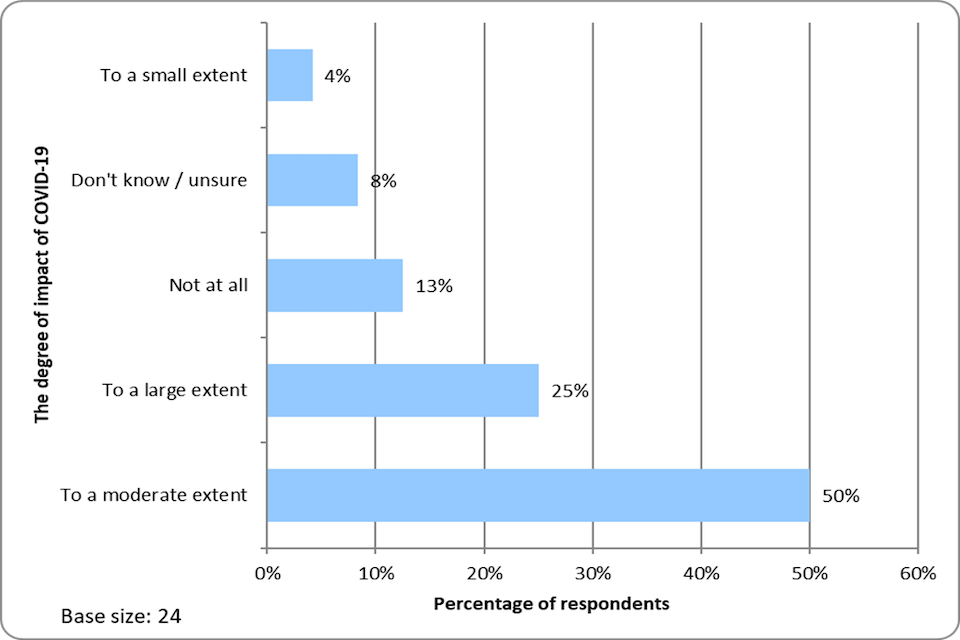
The majority of free text answers to the question of how this impacted the programme were focused on networking concerns, mirroring previous analysis in this section where opportunities for networking was highlighted as a key element of the LORCA programme. As shown in the quotes below, survey respondents felt that they would have been able to develop personal relationships with other participants if there were a higher number of opportunities to meet face-to-face.
We could have participated in more networking / business mentoring events where relationships are much easier to build in-person, rather than purely on-line
LORCA Cohort Survey Participant
We found it very difficult to network, develop business relationships, engage with LORCA partners in an online manner during the program.
LORCA Cohort Survey Participant
From a more policy-focused perspective, it was noted that the levelling-up agenda that had grown to become a central part of mainstream political dialogue in 2020-2021 did have an impact on the programme. Specifically, key members of the executive/governance structure noted the negative impact this shift towards levelling-up had on the programme’s perception. Despite the bid process emphasising the programme’s position as a London-based accelerator, programme staff found that they were having to adopt a defensive position surrounding the issue of LORCA’s location as levelling-up became a more prominent issue. Whilst this external influence did not lead to a direct and substantial change in programme delivery or design, it did impact the programme’s reputation and perception and is likely to impact the design of similar future cyber accelerators and therefore should be noted here.
Levelling-up definitely influenced us. LORCA was procured as the London cyber innovation centre, but by the time we actually got around to starting it, levelling-up had become a key part of the policy agenda and we became quite apologetic
LORCA Programme Staff
We were concerned about the connotations of having a London-based accelerator
LORCA Programme Staff
To what extent were all activities suited to the priorities of the participants?
In interviews, programme staff highlighted the difficulty of delivering a programme that is suited to all participants. However, as a result of the evolution away from the previously referenced generic elements of the programme that were not being well-received, they felt that the programme had developed in a manner that provided something for each of the participants. Though the success in providing the bespoke element of the programme has been discussed, it is important to recognise that it did not always carry over into tangible results. This is most notable when considering the technical support provided in the programme. Though many surveyed felt the technical support had a positive impact on them, Figure 7 shows that it was lowest out of all activities in terms of engagement. This would suggest that, though the quality of the technical support was strong, there were issues with encouraging engagement.
As noted in the programme delivery section of this analysis, it can be seen that business skills development is strong amongst the surveyed participants. This is highlighted by the fact that it performed best in terms of engagement, with a very low proportion of those surveyed feeling that they wanted more or less of the support. This indicates that the delivery team provided impactful, and well-balanced business skills support that suited the needs of those involved. The quotes from survey respondents and stakeholders provided below support this view, recognising the importance of (and challenges related to) the provision of bespoke support in providing a relevant programme that supported the priorities of its participants.
One area that was clearly suited to the needs of the participants but was seemingly not provided often enough during the delivery process was networking events. This was highly ranked in terms of engagement, but also an aspect of delivery that respondents felt was not provided often enough (as shown in Figure 7). This is something to note for future accelerators, as it is clear that this is high up in the participants’ priorities list. This is further highlighted by the fact that none of the participants surveyed for this analysis felt they needed the level of networking being provided to be lessened, strengthening its position as a key area for participants and suggesting that the programme fell short in providing opportunities for networking to occur. It is, however, important to recognise that this may have been impacted by the COVID-19 pandemic which created barriers for several of the cohorts in providing meaningful and impactful networking events.
Figure 7: The aspects of LORCA participants were involved in, and thoughts on whether more or fewer of these activities should be organised.
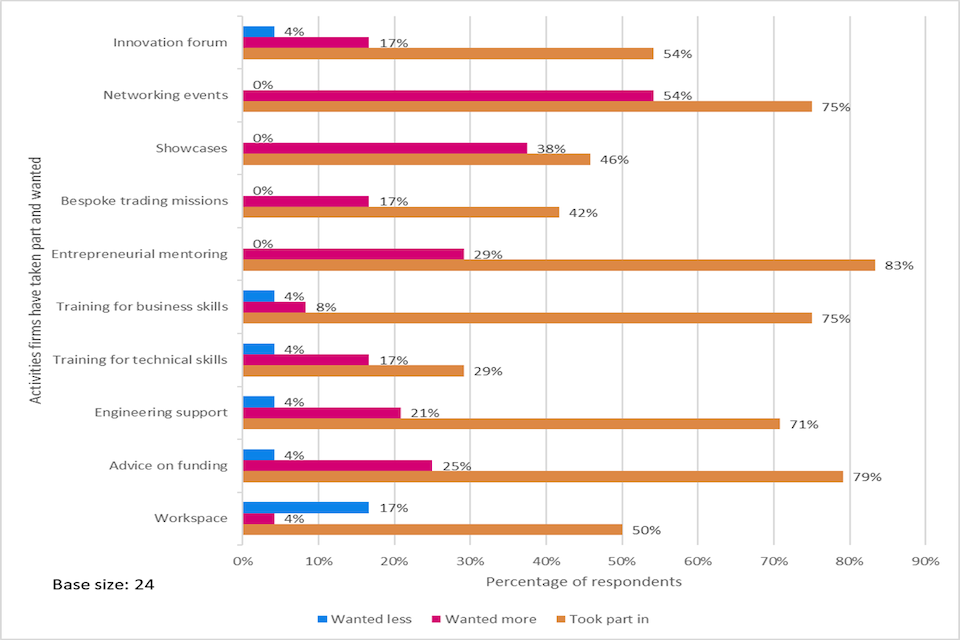
The participant quotes provided below not only highlight the support for the bespoke and one-to-one elements of the programme both from delivery staff and participants, but also the challenge of providing this from a programme delivery perspective.
The one-to-one support to LORCA participants from corporate partners, this was the best out of the couple accelerators we took part in.
LORCA Cohort Survey Participant
The challenge from a delivery point of view was that we wanted to make it customised
LORCA Programme Staff
Entrepreneurs really value the one-to-one support
DCMS Staff
Were there any unexpected or unintended issues that emerged?
It was generally agreed by the majority of survey participants that there were a low number of unexpected issues related to the delivery process. This is particularly notable for negative unexpected consequences, with 0% of respondents noting any negative consequences in this regard. However, a minority of respondents (18%) did note some more positive unexpected impacts, with the most common being an increased connection to other accelerators as a result of LORCA (namely, the NCSC accelerators).
Hub8 membership in Cheltenham as part of the programme
LORCA Cohort Survey Participant
Connection to NCSC programmes.
LORCA Cohort Survey Participant
However, an additional theme did emerge from the stakeholder interviews. The issue of economic displacement and the impact of DCMS-funded cyber accelerators entering this space was a common issue discussed during interviews, with different groups of interviewees presenting contradicting views on this issue. LORCA programme staff generally disagreed with the view of LORCA leading to economic displacement in the sector, instead suggesting that LORCA actually suffered from the existence of other accelerators that were already in this space. This stemmed from the fact that these accelerators were not designed to be complementary, and therefore LORCA staff felt constrained with the type of company with which they worked at times. DCMS policy staff tended to agree with the view that it did not displace other accelerator programmes, suggesting that the market is still thriving (the West Midlands Cyber Centre, for example) and that there may have been similar approaches in the past, but these were slower and less effective.
We felt constrained in our ability to work with genuinely innovative businesses, as the reality was that we had to fit in with other programmes that were not necessarily designed to be complimentary
LORCA Programme Staff
I think there are actually other parties in the environment. The West Midlands Cyber Centre opened its doors recently in partnership with Wolverhampton University and other industry partners
DCMS Staff
However, views from other interviewees were mixed. Wider stakeholders held a variety of different beliefs on this issue, but the prevailing view was that a certain level of economic displacement had taken place. Opinions on the extent of this displacement and whether it was a positive development varied, but one of the more critical perspectives was that LORCA’s closeness with government provided it with an unfair competitive advantage in the space. According to wider stakeholders, this manifested in different ways. One suggested that this would make investment into private accelerators from industry less likely as they would now be used to the fee-free model LORCA provided as a result of its position as a government-funded programme. Another argued that there was a distrust towards companies attached to LORCA as their position as partners or contributors on a government-funded programme gave them an advantage over competitors. However, some wider stakeholders disagreed, instead arguing that a certain level of economic consolidation in the industry was necessary in order to propel the cyber security industry forward.
I feel that the nature of corporate partners means they will be far less likely to fund private programmes after witnessing companies being able to get the same outcomes while reducing budget
Wider Stakeholder
The companies I’ve worked with have been critical of having commercial relationships with LORCA, as companies see it as a commercial advantage for LORCA’s partners over them
Wider Stakeholder
In order to make an impact at a broader scale, economic consolidation was necessary
Wider Stakeholder
This mixed perspective continued in interviews with industry partners, investors, and challenge cohort problem owners. As a whole, industry partners did not offer an overly detailed perspective on the issue of displacement. However, an industry member did highlight the fact that Plexal had not been present in the cyber security sector prior to winning the DCMS bid. Investors also pointed towards a certain level of displacement taking place but did not suggest that this had prevented anyone else from operating in the sector. Whilst there was general agreement from investors that there is now a level of saturation in the space, they did not argue that government-funded accelerators were now the only relevant actors. This is supported by the previously noted recognition of the West Midlands Cyber Centre, which was not delivered through government funding. Challenge cohort problem owners also generally agreed that there were similar programmes present in the sector prior to LORCA, but once again did not feel as though this has had a negative impact. This highlights that, from the majority of those interviewed outside the DCMS and LORCA staff umbrella, it was agreed that LORCA has contributed to some level of economic displacement. However, the extent to which this has occurred, as well as whether it has had a negative impact, are clearly debatable topics.
Plexal didn’t have a history in cyber prior to running the programme
Industry Member
There has maybe been a slight saturation, but I don’t think the government is owning the market. There is a very strong private sector that is leading to growth in the cyber security market
Investor
Similar approaches I have worked in have been slower and less effective, but there might be clashes with other programmes. I saw it as a very effective approach
Challenge Cohort Problem Owner
There is no specific survey data to contribute to discourse around this topic, but Future Focus workshop participants were asked about LORCA’s displacing impact on the wider ecosystem. Participants generally disagreed with this view, from both a sectoral and personal perspective. All agreed that government intervention in the space was necessary, as the market alone cannot be relied upon to provide these services. From a personal perspective, they did not feel that LORCA participation caused any displacement within their businesses, instead joining LORCA was a way of adding to the services they already provided.
The government are not trying to own the space. They were trying to get things started
Future Focus Workshop Participant
To a degree, the government is pump-priming this and I think that’s a good idea generally
Future Focus Workshop Participant
I think the market probably won’t do this, unless there’s a bit of pump-priming
Future Focus Workshop Participant
This didn’t displace anything we were doing
Future Focus Workshop Participant
4.8 Comparable programme accelerators
As part of our analysis, we undertook an assessment of the cyber accelerator ecosystem and how it relates to the LORCA programme through an analysis of publicly available information from a selection of relevant comparators. The information analysed included:
- Programme aims and key features
- Number of businesses supported
- Investment into the programme from key stakeholders
- Job creation goals
- Revenue generated
- Investment raised by companies through the accelerators.
Whilst it is the case that information about each comparator may not be provided publicly in sufficient detail, the analysis can aid in understanding how LORCA’s programme structure and impacts interact with the broader cyber accelerator global ecosystem.
Comparator analysis table
Three comparators were selected for this analysis, with two existing within the national cyber accelerator framework (NCSC Cyber Accelerator/NCSC for Start-ups and the Tech Nation Cyber Programme) and one operating in the USA (Cyber NYC). Table 11 provides an overview of the information found on each of the comparators analysed. Please note that the time period over which aspects are being compared differs so it is not possible to say that one is more successful than another; however, the table does give a useful overview of this area.
Table 11: Analysis of LORCA and its comparators
| Programme Metrics | LORCA [footnote 45] | (NCSC) Cheltenham Cyber Accelerator/ NCSC for Startups [footnote 46], [footnote 47] | Cyber NYC [footnote 48] | Tech Nation Cyber Programme [footnote 49] |
| Programme Aims and Key Features | - Aid later-stage start-ups and SMEs in the attraction of late seed capital, revenue growth and the scaling-up process. This is done through the provision of workspace, a support network (containing commercial and technology validation clinics, access to investors, mentoring opportunities and national as well as international support) | - Drive innovation in the cyber security sector.- Improve commercialisation of potential solution products leading to increase in trials and proof of concept solutions.- Improve skills and knowledge amongst participants leading to investment in their companies. The programme works with start-ups to:- Develop and communicate their core product or service- Facilitate introductions to companies and investors. Create commercial growth opportunities | - Developing the cyber workforce of the future - Catalysing the next billion-dollar company - Establishing NYC as the capital of the global cyber security industry | - Masterclasses, meet ups, cohort trips and networking opportunities provided to companies who meet these criteria:1. UK HQ 2. 10+ employees 3. Seed funding or £500,000 in revenue if bootstrapped. Goal is to boost UK cyber sector, accelerate growth of its top companies, and build a robust cross-industry network [footnote 50] |
| Number of Businesses Supported | 72 Businesses | 40 Tech Companies | 42 Companies | |
| Job Creation Goals | 500 Jobs (865 achieved) | 10,000 cyber security jobs | ||
| Revenue | £37 million | 334% increase of revenue (just under £1 million) [footnote 50] | Cohort 1 found a 258% increase in revenue. | |
| Investment raised | £210 million over 5 accelerators in 3 years | Over £100 million across the four years [footnote 51] | Cohort 2 attracted £35 million in venture capital and grant funding |
As we can see from the table above, the data available on comparators for LORCA is not of a consistently detailed level, particularly compared to the publicly available data from LORCA itself. However, the data that was sourced for each comparator largely stemmed from either government analysis reports and other relevant government documents (particularly in the case of the UK-based cyber companies), the relevant websites of each cyber accelerator (which was the central source for Cyber NYC) and client documents (relevant to LORCA specifically).
As would be expected from a comparative analysis of cyber accelerators, the core theme present in the aims and objectives of each programme was the provision of tools and resources to aid in the growth of the start-ups and SMEs involved. This support typically included:
- Mentoring opportunities (LORCA)
- Facilitating introductions to companies (NCSC cyber programmes)
- Providing trips for cohort companies to aid with international and national networking (Tech Nation cyber programme)
In relation to the numbers of businesses that have been successfully supported in each programme, with the exception of Cyber NYC, all accelerators have published data on this topic. From said data, we can see that LORCA has the potential of supporting a high number of businesses, with 72 successfully completing the process. Though this is higher than both the NCSC and Tech Nation cyber programmes (42 and 40 respectively), the differences in type of company selected may play a part in this. Though it is not possible to identify a single objective cause for this, it should be noted that the NCSC start-up programmes have a more tailored focus than other accelerators, meaning that they select companies from a more limited pool. It is also important to note that this can simply be the result of accelerators being designed in different ways. Though LORCA has technically outperformed the other accelerators in terms of number of participants, this does not necessarily mean that the other programmes are not doing what they intended. For example, NCSC accelerators and the Tech Nation accelerator were designed to have a lower number of participants per cohort, causing this difference in overall participant numbers.
This feature of limited data availability continues into job creation. The two available data points on this topic (job creation targets for LORCA and Cyber NYC) are vastly different. This is highlighted by Cyber NYC’s higher job creation goal of 10,000 [footnote 52]. On the Cyber NYC website, the reason for this high number is given as a need to “develop the cyber workforce of tomorrow”. This high job creation goal separates the accelerator slightly from LORCA as the programmes’ aims are clearly different. Whilst this could be the result of the talent pool within the USA being larger (not least because of a far larger population), Cyber NYC’s programme aim of developing the next billion-dollar cyber company represents a consistent theme of high-level target setting from the New York-based cyber accelerator programme. Once again, this comparison is unfortunately limited to two of the four companies due to a lack of publicly available data on the subject.
One of the best-represented data points within the comparative analysis table is the measuring of revenue generated through the programme. Three of the four relevant accelerators have published data on this topic, with Tech Nation and the NCSC Cyber accelerators presenting this data in the form of revenue growth for participants. This differs from LORCA, with revenue data being represented as an overall revenue figure instead. This makes comparative analysis of the three against each other difficult (as has been the trend throughout this comparator analysis).
4.9 Economic indicators
The LORCA programme delivered on its key economic performance indicators, with the figures below representing the programme’s cumulative performance from 5 cohorts delivered over 3 years. This includes:
- 72 businesses supported
- 865 jobs created (original target: 500)
- £37m of revenue uplift
- £210m investment raised (original target: £40m) [footnote 53]
These were measured using monitoring information on participants from the beginning and end of the programme (12 months) and are therefore relative to the baseline at the beginning of the programme. However, just because these impacts occurred since the start of the LORCA support, it does not necessarily follow that they arose because of the LORCA support, or that the companies would not have found a different way to achieve these impacts to some extent in the absence of LORCA (see section on “additionality” below).
We investigated the available data to see if an estimate of Gross Value Added could be made from uplift of wages and profits, but it was not suitable for this. A rough estimate of the GVA impact can be made by applying the GVA/turnover and GVA/job ratios from the whole cyber security sector that can be derived from the most recent Cyber Security Sector Analysis:
- GVA/turnover = 52%, which would imply GVA increase of £19.4m due to LORCA revenue uplift
- GVA/FTE job = £101k, which would imply GVA increase of £87m due to LORCA job creation
This is a very large range. The discrepancy may be due to recruitment and investment in IP in LORCA companies which have not yet resulted in a turnover impact. LORCA companies are, relative to the cyber economy as a whole, small and growing [footnote 54]; the wider cyber economy includes mature companies that are consistently generating sales from their products and services. The implications would be that the “job creation” estimate of GVA is an overestimate at this stage of company development, but that there are turnover and GVA impacts yet to be realised from the LORCA cohort if they can continue to make progress with commercialisation of their innovative ideas.
As the programme delivered multiple quantifiable benefits, it is difficult to produce a single indicator of value for money in terms of the benefit realised per unit output. The assumption could be made that employment uplift is the primary benefit, which leads in turn to increased revenue and investment. In this case, the most appropriate key business performance indicator would be the level of job creation. However, we suggest that investment was a key benefit of the LORCA programme and that it was, for the companies that sought it, a primary goal and a generator of future growth. An alternative assumption, then, would be that increased sales and investment are the catalysts for recruitment and employment growth. For these reasons, it is difficult to identify a single indicator of value for money for this programme, and focusing on a single indicator would underestimate the overall benefit.
Additionality – share of impacts strictly due to LORCA
The impacts set out here are gross impacts. A full assessment of value for money would require an assessment of the net additional impact. This would take into account the deadweight impact (the level of benefit which would have occurred in the absence of the support) and other effects such as displacement of beneficial activity in the economy towards LORCA-supported firms, for example at the expense of their competitors). It is likely that there was some displacement of economic activity as a result of LORCA. For example, businesses that are supported may have gained an advantage over other businesses in a way that distorts competition, and the investment that they raised may have been diverted from other cyber projects. The counterfactual analysis was designed to explore these factors but as detailed elsewhere, finding truly comparable data was challenging. Intuitively, as the cohort of supported companies were innovative firms seeking growth, it is likely that they would have achieved some of the growth impacts in the absence of LORCA.
Additionality benchmarks for this sort of evaluation are highly variable. Evidence from the UK government Additionality Guide [footnote 55] suggests that business support has a deadweight of 26-46%, and furthermore that generic business support displaces an average of 49% of its employment impact from other firms, and targeted support 42%. Overall, it would be expected that roughly half of the gross benefits might be lost when assessing the net benefit, due to the challenge of directing support to provide activity that is genuinely innovative and additional, and which grows the economy rather than reallocating activity and resources from elsewhere.
However, value for money can also be assessed in more qualitative terms. The National Audit Office (NAO) uses three criteria to assess the value for money of government spending, in terms of the optimal use of resources to achieve the intended outcomes:
- Economy: minimising the cost of resources used or required (inputs) – spending less
- Efficiency: the relationship between the output from goods or services and the resources to produce them – spending well
- Effectiveness: the relationship between the intended and actual results of public spending (outcomes) – spending wisely
As the analysis of KPIs and other key monitoring data set out above in the section on performance shows (summarised in Table 11), the LORCA Programme was delivered successfully. It exceeded expectations in both investment attraction and job creation, and by consistently delivering on its KPIs as presented in the log frame reports. It was also well-thought of by its participants and regarded as well-managed by the stakeholders that were interviewed. In this sense, it has delivered value for money in that it has been effective – the required outcomes have been provided and they are seen to be of value.
There is some evidence of efficiency in delivery from the process evaluation. The programme appears to have spent its full allocation each year. As the programme exceeded its targets and met its budget requirements, it is delivering efficiently by definition (it has produced the outcomes that it was required to do, and more, for the agreed cost). It is not clear from our research if economy (minimisation of costs) could have been better.
Given the timing of this evaluation, we were unable to investigate the impact of COVID-19 on LORCA’s expenditure profile, that is, whether the switch to virtual delivery had any unforeseen costs associated with it, and if it perhaps would have resulted in an overall reduction in expenditure once fully in place.
4.10 Summary
Although the evidence we have is limited in some respects, on balance it is fair to conclude that LORCA was delivered on time, to budget and met or exceeded almost all of the original targets it had been set. Aspects of LORCA worked extremely well, such as facilitating networking, though there was not enough time to instigate change given COVID-19 and the fact that programme funding ceased in March 2022. However, there are observations made in this section which are useful for similar DCMS initiatives, such as closer monitoring of programme management information.
5 Key findings: impact evaluation
5.1. Overview
This chapter deals with the evaluation questions from the ITT that are related to impact.
- What was the direct result of the LORCA programme for the direct beneficiaries of the programme?
- To what extent has the programme been successful in supporting cyber security start-ups to grow and scale at a rapid pace?
- To what extent has the programme produced new ideas, leading to bold and inventive cyber security solutions?
- To what extent have participants from different geographical areas been impacted in different ways and why?
- To what extent have participants from different types of business been impacted in different ways and why?
- To what extent can the outcomes be attributed to the intervention?
- To what extent have external factors impacted programme outcomes?
- What are the additional or unintended benefits of the programme?
5.2 Impact of LORCA on participants
Survey data used to assess the impact of LORCA on participants was drawn from the LORCA Participant survey. Of the 37 responses we had from this survey, 24 were fully completed and 13 were partially completed. Of these partial completions, we did not utilise any as they did not consist of a sufficient amount of relevant information.
Companies were asked in our survey to assess the areas in which LORCA had had an impact on their company. Some of the most common responses relate directly to LORCA’s objectives and the issues raised in our review of policy and market context: these include “received entrepreneurial mentoring” (54%), “improved business skills” (50%), “improved network with businesses or investors” (46%), and “received advice on funding” (42%). The full results are shown in Figure 4 above.
It is important to explore the data from the surveys in greater detail in order to present a more complete appraisal of this key area.
Beginning with investment rates, some of the key findings from survey analysis are listed below:
- A lower proportion of those surveyed received between £0-100,000 in investment following LORCA (30%) compared to the year prior to taking part in LORCA (50%). However, it is important to note both that these are self-reported figures, and that one company did not report their investment figures following LORCA, resulting in one missing value.
- Before LORCA, the highest investment received had been £1-2.5 million investment, achieved by 13% of companies. After LORCA, 17% had received over £1 million, including 9% which had achieved over £2.5 million. [footnote 56] However, it once again must be acknowledged that this is a self-reported figure from the survey and therefore it cannot be guaranteed that these figures are accurate.
As only 13% felt that LORCA had impacted their level of investment it is possible that the slight increase in investment was down to normal company growth and market trends. When considering any trends in this area however, one must also recognise the small sample size from which we draw this data and therefore accept the associated limits to this data. However, looking outside the survey results, we can see strong performance from companies involved in the LORCA programme. A particularly notable example of this is Privitar, which raised £66 million in Series C funding following participation in LORCA. [footnote 57] However, when considering case studies such as Privitar, it is important to recognise that participation in LORCA does not automatically mean that Privitar’s subsequent success can be fully attributed to the programme [footnote 58].
Case Study: Privitar
Founded in 2014, co-founders Jason du Preez and John Taysom united to combine John’s academic work on privacy with Jason’s experience of big data and enterprise software. Together, they launched Privitar, with a passion for building a centre of excellence around their idea that technology and privacy together can thrive.
Privitar organisations mine datasets containing sensitive information while preserving privacy or confidentiality. Whether it is customer data, banking transactions, or patient records, it opens the data for secondary use without endangering privacy or confidentiality. It works with major companies across industries, including HSBC, Citibank, and NHS Digital.
Privatar took part in the second cohort of the LORCA programme in 2019.
To date, Privitar has raised more than $150 million in funding, led by Warburg Pincus, Accel, Partech, IQ Capital, Salesforce Ventures, ABN AMRO Ventures and HSBC.
Privitar has been ranked as one of the UKs fastest growing companies. Venture Radar had them in their top 10 list for RegTech companies globally in 2019. Deloitte ranked them 9th in their rankings of all companies globally after an increase of 3,431% in 2019, while ranking them second in the software sector. In 2020, Privitar ranked 18th in Deloitte’s 2020 list, after an increase of growth of 2,178%. [footnote 59]
Investment
Being mindful of the fact that different companies joined LORCA at different times, Figure 8 below shows the amount of investment that companies received in the financial year leading up to LORCA, and since joining LORCA. Before LORCA, no firm received more than £2.5 million, but afterwards, about 9% did. There was also an increase in amount of investments for the £251k to £500k and £501k to £1 million investment brackets, indicating that LORCA, as an accelerator, might have played a role in making investors more confident in investing more in firms, which might otherwise have remained unknown to them. However, it remains possible that these investments might have been planned in advance and taken place regardless of LORCA. We must once again acknowledge that these are self-reported figures and are therefore not entirely reliable. [footnote 60]
Figure 8: The value of investments LORCA participants received in the Financial Year before the start of their participation in LORCA and since their involvement with LORCA.
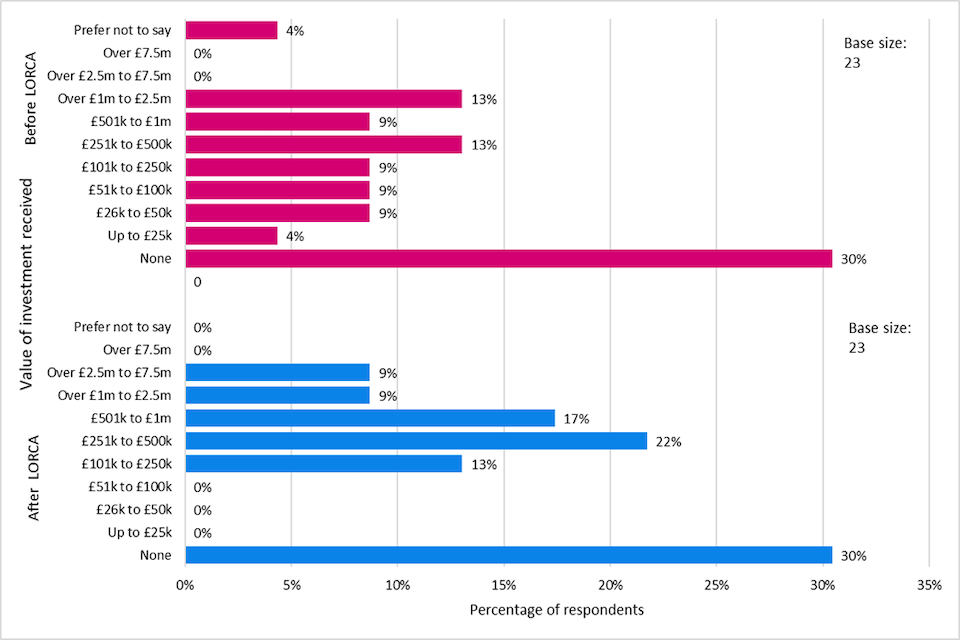
Looking further into the survey data on investment, we can see that there is no clearly dominant origin of investment for LORCA companies. However, the main investment streams seem to come from:
- Business Angels
- Other Individuals
- Government Grants
This even spread of investment should be seen in a positive light, as it means that LORCA cohort participants were not overly reliant on one specific type of investor. This positivity continues when looking into whether the participants feel this investment will be long term, with the majority feeling that this is either likely or very likely. Figure 9 below sets out the full range of responses on the types of investors used, with Figure 10 assessing the likelihood of continued investment. As shown in Figure 9, the most common type of investor was business angels, with 44% of those surveyed receiving investment from someone / a company within this group. It must also be acknowledged that Figure 10 highlights a positive assessment of the potential for continued investment from the perspective of those surveyed, with 95% of respondents feeling that it was either likely or very likely that this investment would continue. However, as stated previously in this report, all survey data figures are self-reported which must be considered.
Figure 9: Types of investors who have invested in the businesses of LORCA participants (post-LORCA) [footnote 61]
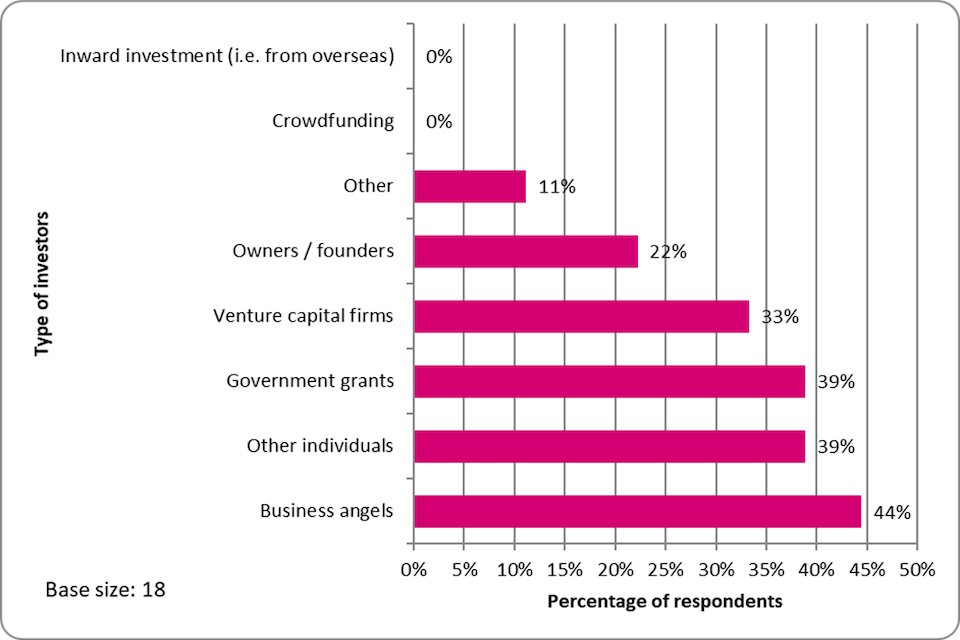
Figure 10: Likelihood of investors wanting to continue investing in the longer term.
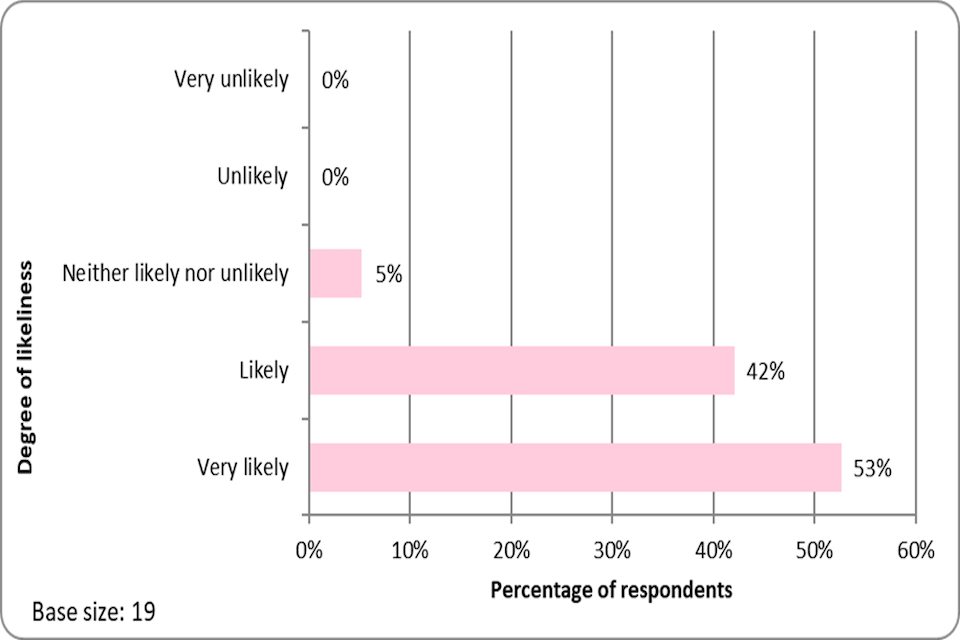
The final factors to consider when assessing survey data on LORCA’s impact are business wins and overseas connections successfully developed following LORCA. [footnote 62] Looking at the data, there is no clear answer on whether this has been a success or not. One thing to note on each of these categories, however, is the high number of participants stating that they have not experienced these developments following LORCA (32% of survey respondents are yet to achieve any overseas business wins, for example). Whilst it is natural that some would not experience development in all areas, increasing the number of business wins and developing overseas business links are key elements of LORCA’s objectives and we would therefore expect to see a higher number of participants succeeding in these areas.
However, we can see the development of some positive trends:
- 23% of those surveyed have achieved domestic business wins totalling between £201k – £300k, with 18% totalling over £500k
- 14% of those surveyed have developed more than 5 overseas connections [footnote 63]
Despite this, it is clear that more development in these areas is required, with a particular emphasis on improving the number of overseas business wins. [footnote 64]
Figure 11: The approximate value of new business wins that LORCA participants achieved in the UK since taking part in LORCA.
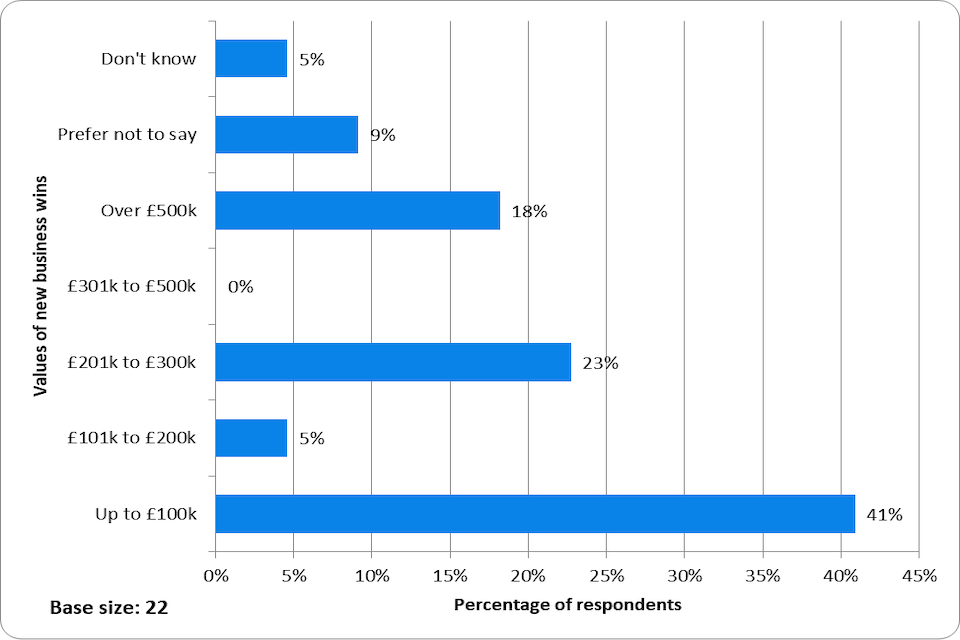
Figure 12 : Number of businesses wins abroad for those in a trade mission

Figure 13: Overseas connections since LORCA for those in a trade mission
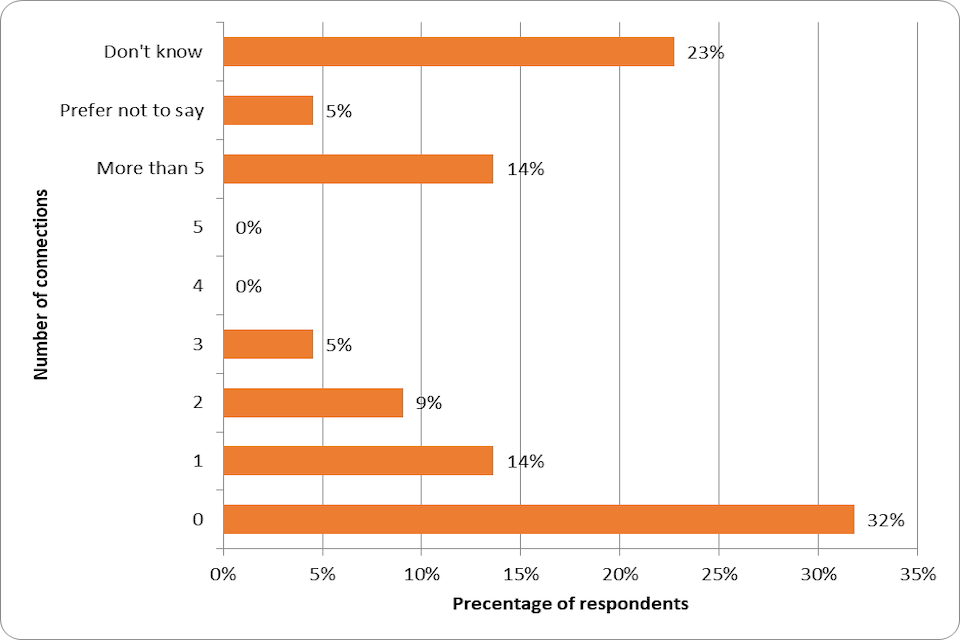
5.3 Secondary data analysis
LORCA Secondary data analysis: The purpose of this section is to begin exploring the impact of the LORCA programme. Data has been collected via the Beauhurst Database [footnote 65] and analysed on the observed outcomes (KPIs) of the group of firms that participated in the programme and a comparable group who did not participate.
According to the Magenta Book [footnote 66], when the two groups mentioned above are effectively identical, evaluators can attribute any measured changes in data to the intervention. To find out how much of the observed outcomes in the data could be attributed to LORCA, we considered a quasi-experimental method, the Difference-in-Differences estimation. This method, by definition, requires us to construct a counterfactual group of firms in the cyber-security industry that are representative of the LORCA participating firms.
The rest of this section details the challenges encountered when creating the counterfactual sample, the limitations of the small sample, and how, at this early-stage evaluation, it was not possible to conduct the modelling. This was partly due to not enough time periods having passed post LORCA, to realise any impact the programme had. Secondary data analysis has provided an indicative trend as a result of LORCA participation which has been detailed below.
Data challenges: There were several data challenges that arose when approaching the impact analysis of the LORCA programme. These were:
- Sample size
- Time horizon
- Lack of time series data
- Outturns not realised
Data availability: One of the challenges we faced as part of the early-stage evaluation was availability of data. In order to perform robust modelling to assess the impacts from the programme, data completeness is crucial. The more information we can base the statistical result on, the greater the level of accuracy in determining the impact of the LORCA programme on participating firms, and the broader market/ economic impacts.
LORCA participants are usually selected according to several criteria. These are scored on the impact they are aiming to create in the cyber industry, their innovation and sustainability, their capacity to put their ideas into practice and being well placed to benefit from the technical, academic and specialist support the programme had to offer.
The application processes’ eligibility criteria were aimed at businesses that are being regarded as innovating and high growth within the cyber sector. Firms that were already revenue generating were more likely to be selected compared to those firms in earlier stages of the business cycle according to the application scoring system.
Businesses at this stage are likely to be pre- or early-stage revenue and are usually focussing efforts on investing in research and development activities. From a data perspective, this poses a challenge in that data on KPIs are likely not available for these ventures. There are also potential issues with data timeliness, given that getting reliable secondary data on operational KPIs may require a lag of at least two years, combined with the problem that policy impacts themselves may take time to be fully reflected in measurable operational performance.
So, while revenue growth would be an ideal indicator in identifying the potential impact from the programme, it is unlikely to show any impact in the early stage of an evaluation. There is however some research to support the idea that accelerator programmes participation often increases participating companies’ revenue (Roberts et al., 2016) [footnote 67].
Our focus turned towards equity fundraisings by firms as the indicator to use in order to draw out any potential impact from the programme within the early phases. In their research, Roberts et al. (2016) noted that accelerators may influence funds raised by participating companies, which could be attributable to the fact that accelerators can be appealing to investors since high quality candidates are screened in and will benefit from participation. Fundraisings can be considered proxies for expectations of future growth, especially for early-stage firms who seek finance to develop products or services they believe there is demand for. Sufficient data availability on equity fundraisings was also key, as this can capture potential impacts from the programme, at least over the short term.
Beauhurst Database: Our sample was developed from Beauhurst [footnote 68] data, a platform that features information on high growth companies, accelerators, and funds and tracks companies’ fundraisings - including ones that are unannounced, which make up the majority of the deals for private companies in the UK.
A key feature of the platform is its robust and granulated filtering system, which was used to produce a counterfactual group of firms - companies with broadly similar characteristics to LORCA participants but those who did not participate in the programme. The selection was based upon the management information from LORCA participating companies obtained directly from Plexal [footnote 69] and the Beauhurst database.
The dependent variable extracted from Beauhurst was equity funds raised in GBP. The additional variables extracted included in the main, Companies House ID, region, SIC sectoral code, the fundraising date, turnover and FTE employee counts for each of the treated and counterfactual group companies.
Treatment firm selection: The Beauhurst database tracks firms within accelerator programs such as LORCA. This allowed for a direct download of a majority of participating firms. 55 firms were drawn down from the database of the 72 firms who participated. 17 firms were registered at Companies House but their headquarters were outside of the UK. They were registered to a foreign address and hence were not picked up by the Beauhurst database which only collects data from UK founded firms. This reduced the number of treated firms from 72 to 55, adding to sample size concerns. Another consideration is the actual duration of the programme for each cohort differs. The five LORCA cohorts as a whole cover a period from 07/2018 to 07/2021. However, companies participating in Cohort 1 for example have their baseline data framed correctly during the start of the LORCA programme (July 2018), yet the fundraising data we have used for their post-treatment is given in 2021, despite having finished the twelve-month programme in July 2019. The post treatment fundraisings data is reported a few years after Cohort 1’s participation. This is problematic as there might be other external impacts that influenced the change in investment for a company that was not due to their involvement in LORCA. These factors could come from other accelerators or similar programmes in which the company participated or are simply unobservable. This data structure would have been improved if we had the opportunity to assess impact on a cohort basis, but the sample size was too small to draw out any impacts. The number of participants per cohort ranged from 10 to 20 companies.
Counterfactual firm selection: Filtering firms based on KPIs was guided through descriptive statistics conducted on LORCA participants at baseline. Our counterfactual group was selected based on characteristics such as:
- Standard Industrial Classification (SIC) 2007 code
- Geographical location
- Turnover
- Employees count
- Equity being the form of funding received
- Company stage of evolution at the time of fundraising being seed, venture or growth
- LORCA – Only firms that did not participate in the programme
- “Buzzword” assigned by Beauhurst platform - Digital Security – which, by definition means companies operating in the cyber industry formed around the need for the protection of digitally sensitive information
The SIC codes (2007) used for the filtering are as follow:
- Information technology consultancy activities (62020)
- Other information technology service activities (62090)
- Business and domestic software development (62012)
- Other business support service activities n.e.c. (82990)
- Security systems service activities (80200)
- Other software publishing (58290)
- Data processing, hosting and related activities (63110)
- Other service activities n.e.c (96090)
- Other information service activities n.e.c (63990)
- Manufacture of computers and peripheral equipment (26200)
- Other education n.e.c. (85590)
- Other research and experimental development on natural sciences and engineering (72190)
Turnover and employee counts were filtered for a range of up to £5 million for turnover and at most 80 employees, respectively.
Our dependent variable, fundraisings, was filtered to capture only equity raisings and the company status of “Seed”, “Venture”, or “Growth” type companies at the time of funding. The reasons for this are that LORCA’s eligibility criteria applies to early-stage revenue generating companies with high growth prospects. These criteria allowed us to construct a sample of counterfactual firms which had similar characteristics to the treatment group (companies that participated in the programme) and to avoid selection bias [footnote 70].
It is important to note that the counterfactual sample did not pick up the fact that some of the participant firms were headquartered abroad. This is because LORCA was a programme intended to have a focus on the UK economy and in the developing of UK’s cyber security firms and industry. Moreover, Beauhurst database only contains UK-based firms. The counterfactual firm sample selection was more extensive as the baseline management information provided by Plexal was comprehensive and the Beauhurst database currently covers a population of 79,000+ firms in the UK. Our final sample of counterfactual firms following the filtering exercise was 335 firms.
Longitudinal element: The period between 2016 to July 2018, just before the start of the LORCA programme, corresponds to the pre-treatment period, and July 2021 onwards to the overall post-treatment period. The unbalanced time period between the pre- and post-treatment periods was drawn as cohorts started at different dates throughout the period between pre and post treatment. The closest data point for equity raised was chosen to the pre- and post-treatment cut-off dates for each company. Summing the fundraisings during each period would potentially bias the results as this variable is not periodic in that firms will choose the optimum moment for fundraisings. This is compared to turnover for example which is reported and generated over set intervals.
In selecting the closest equity transaction by firm, either before or after the programme, an important limitation should be considered for the rest of the analysis. The results of our study would then be interpreted differently because the impact we are observing would not refer to the impact on equity created by the LORCA programme, but rather a per-round impact on equity funding.
Data validation: As part of our analysis, we undertook a data validation exercise whereby we cross-referenced data provided by Plexal [footnote 71] on LORCA participating companies with secondary sources, and participant surveys. The indicators we focussed on were revenue, investment, and full-time equivalent employee counts.
Plexal was required to collect data on participating companies at the baseline, after three months, six months, and at graduation (12 months), as per DCMS requirements for the programme. To ensure the accuracy of their data, they also checked the self-reported data from the companies against external sources.
In order to validate Plexal’s data, we analysed data about LORCA’s participating firms from two secondary sources and from our survey (primary research), listed below:
- Beauhurst database, which tracks funds raised by high-growth, innovative firms in the UK [footnote 72]
- Orbis from Bureau Van Dijk [footnote 73], which is a database that has information on around 400 million companies worldwide and is used to obtain detailed financial information
- We have also cross-checked the validity of the data with some of the data extracted from the participant surveys sent out as part of our primary research.
The cross-validation of the companies’ outputs at baseline - before the programme began - and at graduation was difficult to obtain in general as data on private companies and financial statements are not always publicly available. In addition, using other platforms to compare certain KPIs such as Beauhurst for investment has been difficult since we cannot analyse the time series component and compare data at the same time as Plexal is collecting the data.
Despite the limitations above, we noticed that for most cases, even when comparing data over a different month as a result of the date of publication of financial statements, there were no significant differences in the data provided.
Responses from surveys strengthened the validity as they were broadly aligned with the data shared by Plexal, and what was collected from secondary sources.
Recommendations based on data validation:
- Reporting should be made a mandatory requirement for participating firms. This would allow for a robust assessment of whether the scheme is meeting its objectives.
- Definitions of key performance indicators need to be set to ensure data provided is equivalent across all participants.
- Data provided at baseline needs to be defined over a fixed time period. For example, over the last year what has been the cumulative revenue generated. Firms that participate in the programme will likely have been joining at different stages with some newly formed and others having operated for a few years perhaps. A defined time period will help to assess firms at the start of the programme and subsequent impacts more accurately.
Data filtering and cleaning: Our initial raw data sample was 510 observations before we began the data cleaning process. The first step we took was to remove missing observations for equity after filtering the data according to the selected period of time, as described previously. The sample size was then lowered to 450 observations.
Although the equity funds entries in the sample were never equal to zero, we discovered there was a significant clustering near zero. This is likely because most of the firms are early-stage and might not have attracted many investors yet. Consequently, the distribution of firms was skewed to the right, with only a small percentage having raised a large amount of equity.
To address this problem, we then carried out a data filtering exercise, which involved several steps, and are described as follows:
Removal of the outliers: We have removed outliers from the sample using the interquartile range (IQR) method. This method, the difference between the 75th percentile (3rd quartile) and the 25th percentile (1st quartile) of the equity raised distribution, measures the spread of the middle 50% of values of the sample. Outliers are observations whose interquartile ranges are 1.5 times larger than the third quartile (Q3) or 1.5 times smaller than the first quartile (Q1) [footnote 74].
By removing the defined outliers, we were then able to draw a sub-sample. It’s crucial to identify and remove outliers in a sample as their presence could yield erroneous results in the model calculations.
Removal of firms that were not present in both time periods: The firms that were observed to have raised funds only in either one of the pre- or post- treatment period, were removed from the sample. They were removed as we could not observe the change in funds between the two periods. This reduced the sample size drastically.
We selected the observation closest to both the pre-treatment and post-treatment cut-off dates for each company. This was done because there has been little time since the end of the programme and these relatively early-stage companies typically receive equity funding sporadically and in an unstructured manner.
Therefore, selecting the closest equity observation to the cut-off dates would result in a drastically smaller sample size, and as explained earlier, the impact derived from our model would be calculated on a per-fundraising basis instead of an absolute basis.
Outturns not realised: Our examination of the final, cleaned sample (74 observations) showed that both the residual and dependent variable of the sample, equity fundraisings, was not normally distributed. [footnote 75] The above implied that we were unable to carry out a Difference-in-Differences estimation [footnote 76] for our sample as per the following reasons:
- The sample size of the dataset, after carrying out the data filtering and cleaning process, was too small, n = 74 observations, with only 12 firms remaining in the treatment group. [footnote 77]
- To obtain a meaningful result when performing an estimation of the model, the residuals distribution should be normal or at least quasi-normal, this is not the case in our sample. The particular shape of the double-peaked residual distribution is likely due to small sample size and might yield some estimation biases. In the case of large sample size, this issue would be relegated due to the asymptotic property of the estimators, justifying the use of statistical inference despite the case of residuals distribution not necessarily normal. [footnote 78]
- The parallel trends assumption is necessary. The assumption states that the treatment group, without the intervention from LORCA, would have followed the same time trend as the control group. This does not seem to be the case for our sample – or it might hold weakly as depicted later - as observed from the trend in equity for both the treatment and control group.
Other methods such as synthetic control are not considered in this setting because the treatment group also suffers from the issue of a small sample size.
As depicted from the bar chart below, which shows the frequency of the equity fundraisings variable in the sample, the variable distribution has two separate peaks. This could be due to the fact that:
- The sample size is very small. Since there are not many observations, each one greatly affects the shape of the distribution
- Potentially, extreme outcomes in the distribution are created by a positive feedback loop. This might be a situation where a company that has already received funding - i.e., a successful start-up - may be sending positive signals to investors. Signals to potential investors can be caused, for example, by a firm’s ability to strategically use funds received from previous investors. This might explain the difference between firms that are more successful in receiving funds from investors than others, as depicted in the graph below.
Figure 14: Histogram showing distribution of the amount of equity raised for both the control and treatment group firms combined [footnote 79]
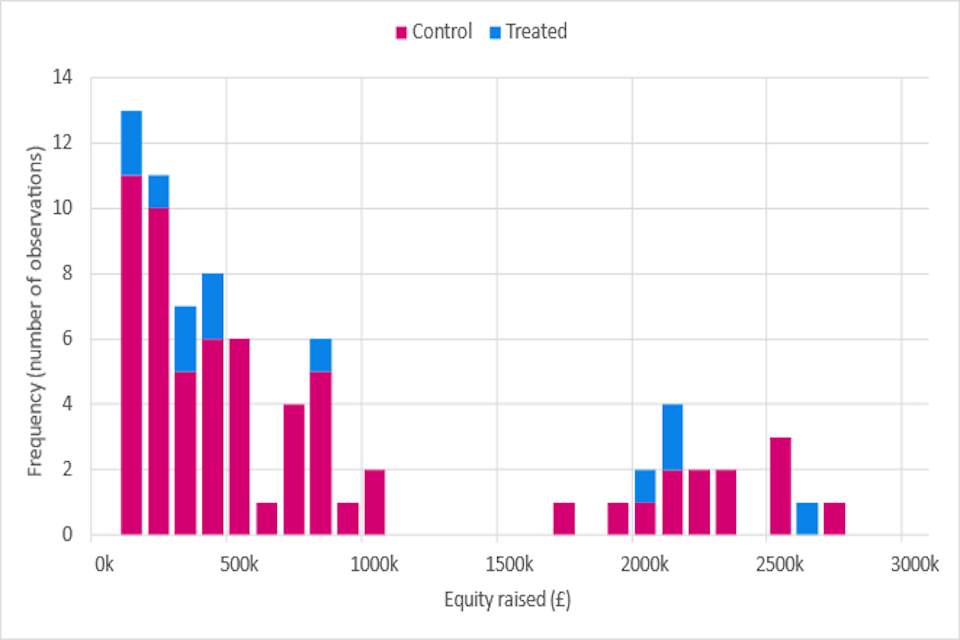
In the two graphs depicting the treated and control group distributions below, it can be seen that the same issues as those described above arise in both the treated and control groups’ distributions. These are more evident for the treated group, where the small sample size issue is even more pronounced as it only contains 12 observations.
It is important to note that in both the control and treatment variable cases, there appears to be a gap between the £1 million - £1.5 million equity range. It appears that, despite the limited sample size, this is a range firms need to somehow breakthrough in order to be more likely to receive funding from investors. It could suggest that investors consider firms within this sector who seek > £1.5 million in equity funding as more viable ventures and are more likely to consider investing in these firms.
Figure 15: Histogram showing distribution of the amount of equity raised for treatment group firms
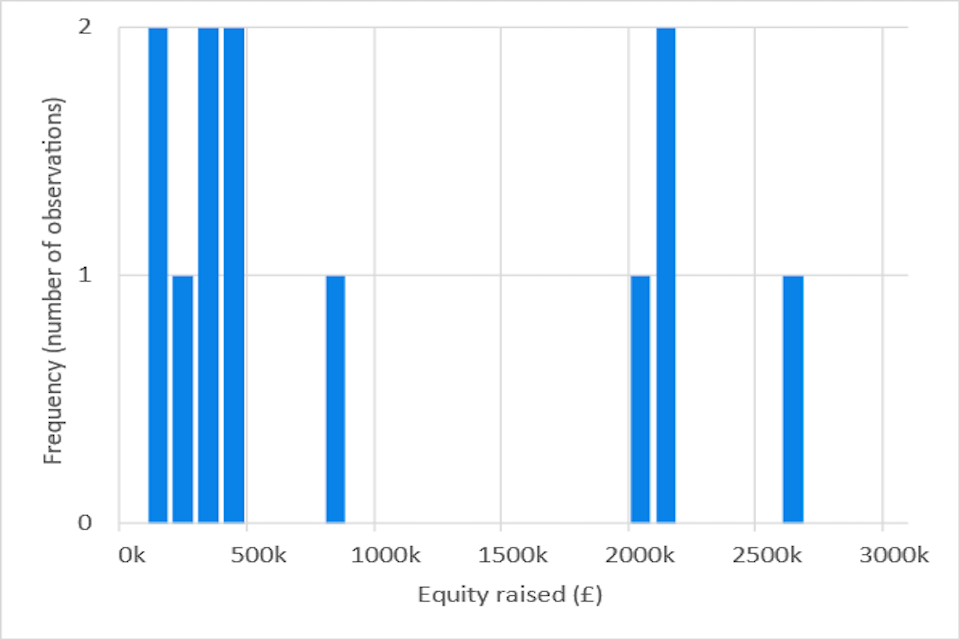
Figure 16: Histogram showing distribution of the amount of equity raised for control group firms
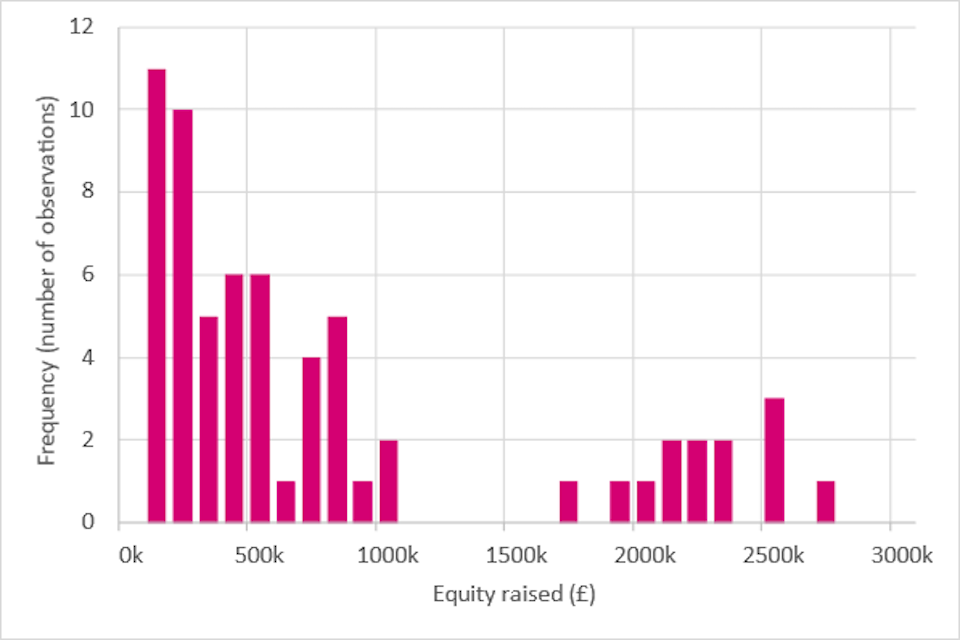
Descriptive statistics: Our analysis has therefore been restricted to descriptive statistics, focusing on the change in equity funds raised before and after LORCA, both by treated and counterfactual groups, because of the limitations highlighted in the previous sections.
The following graphs depict the trends in equity funds raised before and after the programme, both for the treated group and the control group.
Figure 17: Average equity raised per year for both control and treatment group before LORCA
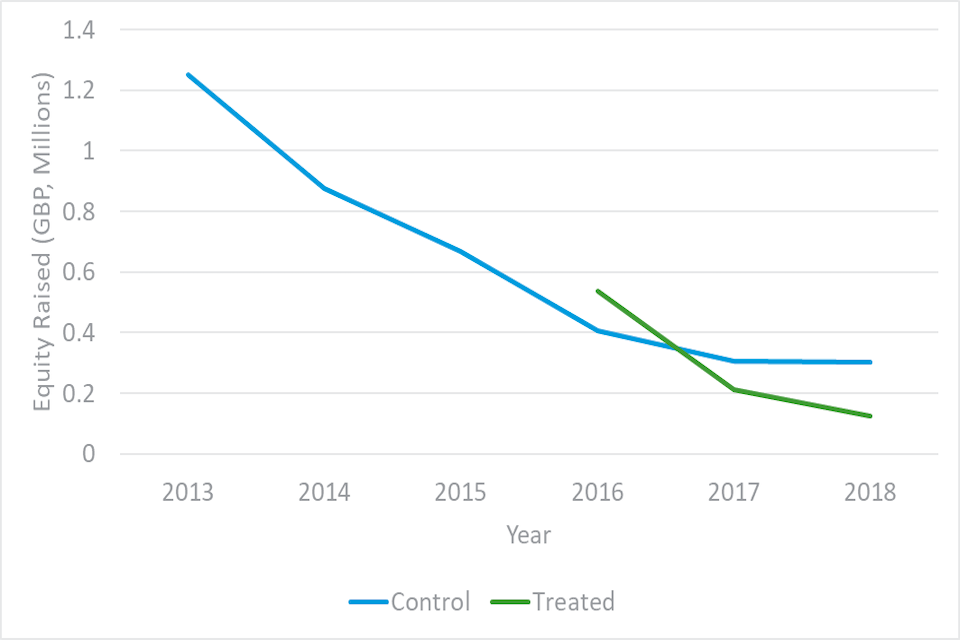
The trend of equity fundraisings by both LORCA participants and the counterfactual group is declining in the years leading up to the start of the programme. This decline could be explained by several factors:
- Equity raised might decline as these companies may have similar financing cycles. Business cycles are likely to result in periods of ups and downs in operations. For example, early-stage ventures that raised equity funds in 2013 and subsequent years would be less likely to require the same level of funding in later years, i.e., closer to the start of the LORCA programme. Therefore, the trend may have partially been influenced by finance demands.
- Brexit may have been a key driver in the decline as the uncertainty surrounding London’s status as a technology-driven innovation hub, attracting intellectual capital from areas in Europe such as Southern and Eastern Europe. This could have been a contributing factor towards increasing investor risk aversion and subsequent decline in equity funds raised by cyber-security companies.
- The small sample of firms analysed does not allow us to see a complete picture of the declining investment trend since the data on equity raised from LORCA’s treated firms does not go back to earlier than 2016.
The graph below shows the change in equity raised by treated and counterfactual companies after the LORCA programme completion. The increase in equity raised by participating companies is steeper than that of non-participants – which is an interesting observation; however, caution must be taken when attributing any difference to the LORCA programme given this is an early-stage evaluation and fuller data are still yet to be realised through KPIs such as revenue.
Figure 18: Average equity raised per year for both control and treatment group after LORCA
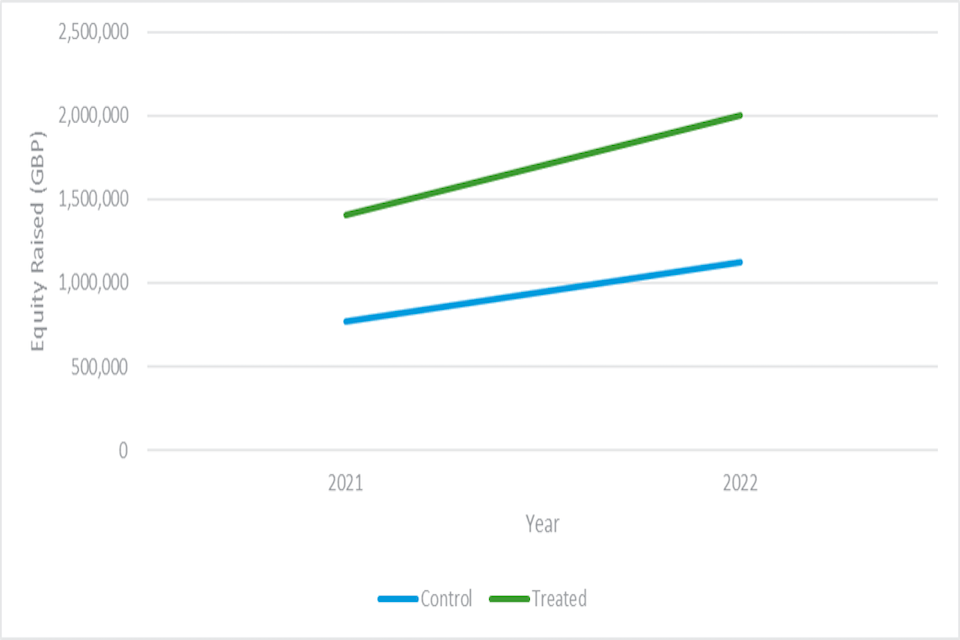
A third graph below shows the trends before and after the implementation of LORCA to provide a clearer picture. The shaded area represents the LORCA scheme – applied to different cohorts over the course of three years. We can see that post-LORCA participation, there has been an upswing in equity fundraisings for participating firms compared to non-participants. This could imply an increase in investments on cyber-security firms, especially those that participated in LORCA. This could be indicative that firms are internalising learnings from the programme and becoming more successful in pitching to investors. A consideration to note is that participation in the programme may simply act as a signalling function to investors who will understand the higher skills obtained through participation.
Note that for the period between July 2018 and July 2021, data has been filtered and excluded to an extent which it is not recommended to draw conclusions regarding the effectiveness of the programme. Cohort 1, for instance, started in July 2018 and completed LORCA in July 2019, whereas Cohort 5 started in July 2020 and ended in July 2021. There is a gap of two years between one cohort completing the programme and another cohort participating and completing the programme, distorting the equity fundraising data in a before-and-after analysis. Hence, we opted to assess the period when all cohorts were not participating in LORCA (i.e., before July 2018), and after the point at which all firms had completed LORCA. (i.e., after July 2021) As a result, the data generated during the course of treatment (i.e., when the LORCA programme was happening) is not used for analysis. We understand the limitations of this approach as there is some overlap between some cohorts beginning to experience benefits during the period of (July 2018 to July 2021), however it was the most sensible given the data. An alternative approach considered was to assess the impact on a per cohort basis, however, the sample sizes were too low (around 10-20 companies per cohort).
Another cautionary note is that, unlike figures such as revenues that are periodically reported, firms strategically choose an optimum point in time for the amount of equity fund raised. Although LORCA enables firms to raise a higher level of funds, some might choose to delay or move forward with their funding plans. While some were capable, they might not raise the maximum amount of funds due to strategic reason. In interpreting the data, it will be necessary to consider the irregularity of fund-raising schedules and the amounts raised by different firms. This was another reason we chose to select equity fundraisings pre-LORCA (certain there was no impact from the programme for participants raising funds), and post-LORCA, (certain that LORCA impacts would have been internalised).
Figure 19: Trends of equity raised from 2013-2022
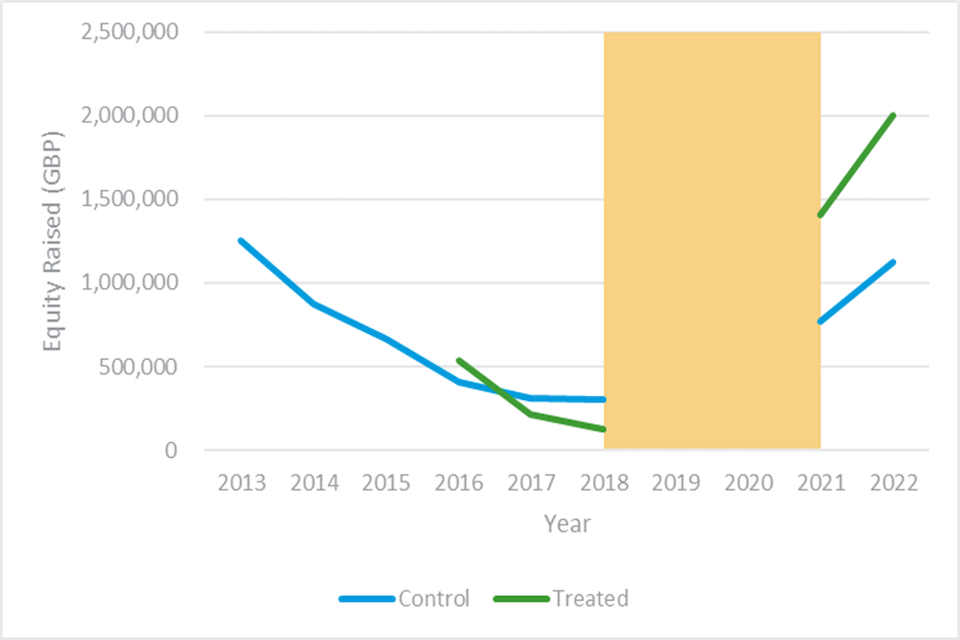
Table 12: Average and percentage change in the equity raised by firms (2017-2022)
| (£) Average equity raised by group | (%) Change in average equity raised | (£) Absolute change in average equity raised | ||||
| Year | Control | Participants | Control | Participants | Control | Participants |
| 2017 | £306,869 | £212,245 | -24.5% | -60.5% | -£99,757 | -£325,221 |
| 2018 | £301,556 | £123,257 | -1.7% | -41.9% | -£5,313 | -£88,989 |
| LORCA Programme (Cohorts 1 to 5) (July 2018 to July 2021) | ||||||
| 2021 | £772,690 | £1,406,727 | 156% | 1041% | £471,134 | £1,283,471 |
| 2022 | £1,124,752 | £2,000,027 | 45.6% | 42.2% | £352,063 | £593,300 |
In addition, as illustrated by the table above, the average equity raised by both the control and treatment groups rose sharply by 156% and 1041%, respectively. This jump continued in 2022 but at a slower rate.
This was likely driven by a bounce back from a low base in the last year of LORCA which coincided with the initial emergence from the global economic downturn caused by COVID-19, and equity raised by firms could have been influenced by various support measures that firms received as a result of the pandemic.
At the same time the government had introduced the National Cyber Security Strategy (NCSS) (2016-2021) [footnote 80], which sets out ambition policies to make the UK a leader in the cyber-security sector. This might have attracted interest and investment in cyber-security companies in recent years.
These differences in the funds raised by companies participating in LORCA, compared to the counterfactual group of cyber-security firms, may be partially explained by participation in the programme. However, this needs to be considered critically since, as described below, there are some very important limitations to be considered:
- The impact of the programme has not been formally and robustly estimated. As such, caution should be exercised when using this conclusion since there is a high risk that an increase in equity raised by LORCA participating companies might not be causally related to LORCA because of other confounding factors, such as the economy or the market, might have affected the observed increase instead.
- There have been different treatment times for different firms participating in the programme. LORCA’s cohorts began at different times, at this point, and as explained by the data limitations in earlier sections, it is not possible to analyse the impact of the programme for each cohort individually. This may not be a true representation of the impact of the programme, which could be lower, given some time has passed for firms from the early cohorts since the end of the programme, and their increase in equity raised could be due to other unobserved factors.
Counterfactual Survey: The counterfactual survey was conducted in order to gain insights into the reasons for the non-participations of LORCA programme for companies with similar characteristics to LORCA participants, while other methods of exploring the counterfactual sample is not available. The Beauhurst database was used to draw down a sample for the counterfactual group of firms. [footnote 81] The platform holds a variety of company information on 79,000 firms in the UK. Built into the database is an extensive filtering system that allowed us to narrow our search criteria based on a descriptive data analysis exercise on participating firms.
The filters we applied to the search are:
- Buzzword (digital security)
- Company status – selecting only SMEs and more specifically: seed, venture and early-stage
- Turnover [footnote 82]
- Employee counts [footnote 83]
- Fundraisings – Equity only
- SIC codes (2007) – Details the economic sectoral group the firms belong to
- LORCA – Only firms that did not participate in the programme.
- Geographical location
After applying the filters above we were able to draw down 335 firms from the database. Contact information was also drawn down (names and emails) for these firms and we received sign-off from the Beauhurst team to use these details. One-hundred-and-eighteen firms from the sample did not have emails, contact information, or we received a bounce back email with no other contact information. These were removed from the list of firms we wanted to contact to complete the online counterfactual survey.
A total of 217 firms were sent the survey to complete which was open for response from 6th May to 16th May 2022, which is 10 days. Only 4 firms responded fully to the survey during that period with 9 firms partially responding. This response rate of fully completed surveys stood at 1.8%. It is expected that for counterfactual firms you are likely to receive a lower response rate as these firms are not engaged with the programme, unlike participants and have limited incentives to respond. Robust data analysis is not feasible with only 4 responses and is a major limitation to producing any results on this group of firms.
Considerations for future impact evaluation modelling approach: A future evaluation of the impact of the LORCA programme, could consider, in full, the Difference-in-Differences approach as described below.
In quasi-experimental econometric design, difference-in-differences leverages longitudinal data sets to determine what is the causal effect of an intervention. This method calculates the difference in outcome before and after an intervention, comparing a set of firms that joined the intervention – the treated group – with similar firms that did not participate in the programme – the control group.
An early impact assessment of LORCA may use this technique, which is commonly used within policy impact evaluations. An appropriate design should include data before and after the intervention on a control group and a treatment group. The following equation represents the equation in general terms:
The coefficient of interest is which estimates the average treatment effect. The coefficient on the interaction term is derived from the differences in conditional expectations.
Following several years post LORCA, an evaluator may consider, in addition to filtering for firms that are similar to the participating companies as we did for our analysis, further refining the construction of a counterfactual group by using the Propensity Score Matching method (PSM).
In the PSM method, an artificial control group is constructed using statistical techniques. PSM matches one treated observation to one (or more) untreated observations with similar characteristics in the dataset. Therefore, by matching observations, the joint distribution of observables would be more aligned to individual participants of the treated group, allowing the estimation of an unbiased and robust model.
Conclusions: The realised benefits from the LORCA programme are likely still being experienced by participating firms. Key performance indicators such as revenue usually take a few years to have any signs of impact due to the lag in experiencing the programme, building in teachings and learnings, and developing products and services to generate sales.
At this early stage however, there are possible initial signs of a positive impact from the programme. Using the Beauhurst data set on fundraisings for SMEs in the cyber sector we can see that the trend pre-programme for both treatment and control firms was declining. This could have been driven by Brexit uncertainty and company’s financing cycles. Post-LORCA we see a positive trend in fundraisings for both groups of firms, but LORCA participants experienced a stronger positive trend in equity fundraisings. This trend has not been disseminated from external impacts such as market size or economic risks for example.
There are data limitations to the analysis which have been described above such as small sample sizes, both total participants and per cohort. Realisations of impacts through increased investment in R&D and other broader business activities to generate sales revenue have a lagged element. This is partially shown within the market context section where broadly, on a per cohort basis, revenue and investment start trending upwards towards the end of the programme.
A future consideration to estimating the impact of the LORCA programme would be through DiD econometric modelling as theoretically described above. A more appropriate KPI to use would be revenue but takes time for potential benefits to be realised. Inputting programme learnings into the production process will take time and the subsequent increase in sales as a result of potential improved service offerings. Given the LORCA programme has recently come to an end (July 2021), the full impact through increased sales will take time to realise. At this early stage we can say the trends show a likely positive impact from the LORCA programme.
Characteristics of international firms
The analysis of the LORCA 72 participating companies revealed that 17 of them had their headquarters outside of the UK, in countries such as the USA, Argentina, Israel, as well as countries around Europe. The Beauhurst database, which only collects data on UK-based companies, did not collect information about these 17 firms, so we could not use it to observe equity funds raised by these firms for our secondary data analysis.
16 of the 17 foreign-based firms were registered at Companies House, a requirement to participate in the programme, and we were able to establish that most were incorporated in the UK shortly before joining LORCA. It appears that, despite not having either a physical presence, nor employees in the UK, the majority are still operating in the country, as evidenced by their active accounts on Companies House. This might indicate that LORCA has been successful in attracting innovative cyber security firms from abroad, which further expand their presence and provide the UK with more elaborate solutions and services in cyber security.
About 8 of the 17 participants with headquarters outside of the UK dissolved or went dormant in the UK after participating in LORCA. Although difficult to infer due to the lack of information, these firms may have been active in the UK only during the period of the programme, possibly indicating they registered a company in order to participate in the programme but without generating any knock-on benefits for the UK economy.
The self-reported data on these firms received from Plexal indicates, during LORCA, an increasing trend in terms of revenue, investment received, FTE employees, proof-of-concepts developed, and clients’ contracts secured, suggesting the programme may have been, to some extent, contributing to the growth of these firms. It is however difficult to infer the effect of their growth on the UK economy, since this self-reported data may include revenue earned abroad, as well as growth in the number of employees and contracts overseas.
The findings may suggest that, while participation in these sorts of government interventions from innovative firms from abroad might bring talent and fresh perspectives to the industry, and could have a positive impact on the economy, delivery partners such as Plexal may need to do more to work with overseas firms to commit to building a presence in the UK and creating a positive impact. Additionally, firms that are headquartered overseas should be required, where possible, to report their metrics separately for UK and foreign operations so that it is easier to establish how much benefit is created for the UK economy.
We suggest that eligibility criteria and selection processes for future programmes should be reviewed to consider whether existing processes sufficiently ensure that when funding is allocated to UK companies that are foreign controlled, the funding will catalyse sustainable benefits for the UK cyber sector. Encouraging foreign direct investment into the digital economy is a valid growth policy, and restricting internationally founded businesses from participating in programmes like LORCA could dissuade them from participating and investing in the UK economy at other stages of company development. For this reason, applying the existing criteria more rigorously is a suggestion for review rather than a recommendation of this report, as there are economic trade-offs involved in this approach.
5.4 Case studies
We have included a selection of companies that were LORCA participants, shedding some light on the potential impacts as well as providing insights into the extent of LORCA’s success. A selection of case studies is included here to illustrate the range of companies that participated in LORCA at various stages of the programme. A full list of companies is included in Appendix D.
| Risk Ledger | |
| LORCA Involvement | Risk Ledger took part in the fourth LORCA cohort and were also selected for the LORCA Ignite programme, suggesting that they are recognised as one of the most successful British start-ups of the last three years in scaling up their operation. |
| How did Risk Ledger begin? | Risk Ledger was founded in 2018 by Haydn Brooks and Daniel Saul, aiming to connect clients and suppliers such that clients can better understand the cyber security measures that their suppliers have taken to prevent cyber-attacks. At the beginning, Risk Ledger neither had a product to sell to the market nor the cash to create a product. To generate investment they sold two pilot programmes to two separate companies. Once they proved to clients that there was a market, they grew exponentially. |
| What does Risk Ledger do? | Risk Ledger is aware that businesses and organisations encounter many difficulties monitoring and mitigating security risks associated with their suppliers. A large part of this is due to the lack of a network platform that would allow clients and their suppliers to exchange information regarding the measures taken to control cyber security risks. Therefore, companies either face a high risk of cyber-attack on their supply chain providers, or bear a significant cost in mitigating such risks. Risk Ledger seeks to address the asymmetry of information in the market by offering a third-party platform that allows both clients and suppliers to stay informed regarding the level of risk they face. The businesses that enrol with Risk Ledger will submit a list of their suppliers to Risk Ledger, who will in turn invite suppliers to join the platform for free and share information about how their organisations have taken steps to protect themselves from cyber-attacks and data breaches. A supplier’s profile account will only have to be established once. Upon successful registration, all of their company’s clients will receive real-time updates on the cyber risks they face. Suppliers can simply update their account profile with Risk Ledger without having to communicate separately with their clients. |
| Risk Ledger Clients | Risk Ledger worked with the NHS during COVID-19 in monitoring cyber risk of their suppliers in the UK. Currently their platform is used by close to 40 organisations with complex supply chains. These includes BAE Systems Applied Intelligence, City of London Police, Schroders Personal Wealth, and online retailer ASOS. |
| Cyber Smart | |
| LORCA Involvement | Since graduating from their first accelerator programme with the second LORCA cohort they have experienced explosive growth and have quickly become one of the UK’s leading automated cyber security companies for SMEs. This resulted in CyberSmart joining LORCA Ignite to continue their rapid growth. |
| How did CyberSmart begin? | CyberSmart was founded by Jamie Akhtar and Mariella Thanner in December 2016. Cyber security regulations are constantly changing and for SMEs it can be very costly to keep updating their security systems and changing their security often can lead to gaps. CyberSmart saw this and decided to automate this process and sell it to their clients. CyberSmart take security standards and use smart technology to create an automated and user-friendly platform. CyberSmart emphasises they can help businesses quickly reach the government-required level of standard in security measures, which can be completed within 24 hours. |
| What does CyberSmart do? | CyberSmart is a cyber security company that focuses on empowering small to medium enterprises to better protect themselves in a digital way. CyberSmart is a digital security and compliance platform. Before CyberSmart, every device had to be checked manually which was very costly, inefficient, and time-consuming. Now, with the help of CyberSmart technology anyone can fix, check, and maintain their device with just a few clicks. CyberSmart continuously work in the background to ensure all devices are secure. CyberSmart also provide their clients with cyber security standard certificates to prove that their clients’ systems are guaranteed to be secure. |
| CyberSmart’s future | Cybersmart intend to grow by 300% year-on-year as they want to expand their team and they want to continue protecting more SMEs. They claim that SMEs have the biggest gap in the market regarding cyber security and therefore their focus is on protecting them and their market. With the help of LORCA Ignite CyberSmart intend to tap into the international market in 2022. |
| What parts of LORCA did you avail of? | Mentoring, workshops, third party support (Outfly) |
| What did you find most useful? | From LORCA cohort 2 it was the trip to RSA for connecting with the ecosystem. From LORCA Ignite, the VIP dinner was fantastic, as was the away day. |
| What did you find least useful? | None, although would prefer more in person sessions as they bring additional depth and discussion. |
| To what extent do you attribute your subsequent success to participation in LORCA? | “A journey of a thousand steps is just that. LORCA was several of the steps that moved us closer to our overall mission of protecting and empowering SMEs”. |
| Bob’s Business | |
| LORCA Involvement | Bob’s Business graduated from the LORCA programme as part of the second cohort. They attended LORCA Needs Accelerator programme targeted at the media industry, identifying the challenges and risks faced by media organisations, challenges such as theft of intellectual property, state-sponsored attacks, and unsecured devices used by remote teams. |
| How did Bob’s Business begin? | Bob’s business was founded by Melanie Oldham in 2007. |
| What does Bob’s Business do? | Bob’s Business provides award-winning cyber security awareness training and phishing campaigns. Bob’s business places a huge emphasis on human behaviour and how they react to cyber security threats like phishing. Bob’s Business provides training to companies with the focus on eliminating human error in cyber security in the workplace. Humans are often considered the weakest link in cyber security with over 90% of cyber-attacks aimed at humans. Bob’s Business recognised this and acted upon it to minimise error. Their training programmes are entertaining, engaging, and memorable for clients which helps to increase their impact. The focus of the training is to achieve industry standards, create behavioural change and develop a security conscious workforce for their clients. |
| Examples of Bob’s Business customers | Qualco, Liberata, Merthyr Tydfil County Borough Council, Simplyhealth, The City of Cardiff Council, The Law Society, Altodigital Networks Ltd, The Scout Association, vXtream Managed Services, UK government |
| Example of Bob’s Business working with UK government | UK government approached Bob’s Business to develop an innovative cyber security training initiative to educate over 70,000 members of staff and third-party IT service providers about the threat of phishing. Bob’s Business developed Think Before You Click, an innovative simulated phishing programme, which incorporated three key elements: Education, Awareness & Testing. As a result of Think Before You Click, UK government staff now routinely and quickly refer suspicious emails for specialist analysis, which has improved intelligence with their Cyber Security Command Centre, allowing them to deal with threats in a prompt manner. Bob’s Business’ simulation enabled UK government to target education to where staff need it most. This approach allowed users to receive training at the most important time – directly after a mistake. |
| Trust Elevate | |
| LORCA Involvement | Trust Elevate was one of 10 companies that took part in the first LORCA cohort. |
| How did Trust Elevate begin? | Trust Elevate was founded in January 2017 when Dr Rachel O’Connell decided to make the internet a safer place for children and young people. Trust Elevate also promotes the importance of adding extra security online. |
| What does Trust Elevate do? | Trust Elevate is a child age verification and parental consent provider which enables social media, edtech, and gaming platforms to reliably know their users’ ages and to create safer spaces for children. It is the world’s first privacy, security and trust technology platform for handling children and young people’s data, which enables companies to comply with the CCPA, GDPR, AVMSD, PSD2, AML and hundreds of the world’s privacy and security laws. |
| How does it work? | Trust Elevate’s cyber security tool adds an extra layer of security to a website. They use a ‘plug and play’ system while verifying details in areas like online video gaming, social media platforms and banks. The product of Trust Elevate enables companies to create the link between parents and their children, redirecting the page of consent to parents when the users are too young to give one, minimising the risk of companies offering age-unappreciated content to underage users. Furthermore, Trust Elevate stresses that they do not retain clients’ data and that they only use their user’s data when the computer system is connected. |
| Capslock | |
| LORCA Involvement | Capslock took part in the fifth LORCA cohort and also took part in a LORCA Challenge. |
| Who founded Capslock? | Capslock was founded in September 2019 by Dr Andrea Cullen, who is now a lead tutor in Capslock, Lorna Armitage, who is also a lead tutor in Capslock, and Jonathan Slater who is now the Head of Learner Success with Capslock. |
| What do Capslock do? | Capslock offers training programmes to fully re-skill their clients in cyber security. Capslock is a revolutionary educational organisation. They re-skill adults into cyber professionals in as little as four months. They provide cyber re-training education, delivered online by industry professionals. They base their courses on employer wants and popular cyber certifications. |
| What makes Capslock special? | Capslock use Income Share Agreements: unique and accessible methods of tuition finance which allow their clients to pay for the course in small instalments only after they have graduated, been hired, and are earning a good wage, which is a good incentive to boost the attractiveness of your company. Only 10% of UK cyber professionals are women, so Capslock are on a mission to increase gender diversity by supporting women to re-train in cyber security. [footnote 84] Capslock saw this gap in the market and now provide a woman only initiative to try and promote more women in cyber security. In an interview with Plexal, the founders of Capslock expressed their gratitude for being selected as part of the LORCA programme that helped them to stay connected with investors, eventually securing pre-seed funding which enables them to expand and design the programme needed for new talents interested in entering the UK cyber security industry. |
| Threat Status | |
| LORCA Involvement | Threat Status graduated as part of the third LORCA cohort and also took part in a LORCA Challenge. |
| How did Threat Status begin? | Threat Status was established in 2017 by Jon Inns and Ian Nice who have both spent most of their careers in the information security industry. After the large Yahoo data breach of approximately three billion user accounts in 2013, they began observing a steady increase in compromised and leaked user data and recognised very quickly that the release of this information had the potential to do a lot more harm than many imagined possible. In the summer of 2017, they acted upon their findings and founded Threat Status. Their headquarters are based in Fareham. |
| What does Threat Status do? | Threat Status provides the solution to Dark Web Monitoring, assisting companies suffering from the breach to locate the leaked data that are circulated on dark web pages used by malicious attackers. They develop Arc-Credential Stuffing Protection programme to help e-commerce companies identify their customers. Should the identity of the log-in detail be found on dark web, paste sites, hacker forums, or deep web, Threat Status will alert these companies about the potential breach of their client data, advising on further preventive measures to take place. Another programme developed by Threat Status is Trillion™, which is a Breached Accounting Mining platform on which signed-up companies can track and trace the usernames and passwords that are stolen, recovering the identity of their clients that are leaked to the dark webs. “Trillion gobbles up that data like a hungry goat, extracts useful artefacts, compares them with everything we’ve ever seen before, decides how dangerous the data is to our clients and delivers its results. Easy. From the outset we designed our service to be affordable for all, as data breaches affect everyone, so no matter how large or small your organisation is.” |
Table 13: Employment, Turnover, and Investment of Case Studies
| No. of Employees* | 2016 | 2017 | 2018 | 2019 | 2020 | 2021 | |
| Risk Ledger | 2 | 3 | 8 | 12 | |||
| Cyber Smart | 2 | 4 | 10 | 43 | |||
| Bobs Business | 11 | 14 | 24 | 29 | 24 | 22 | |
| Trust Elevate | 1 | 1 | 1 | 1 | 2 | ||
| Capslock | 5 | ||||||
| Threat Status | 1 | 5 | 4 | 4 | |||
| Turnover** | 2016 | 2017 | 2018 | 2019 | 2020 | 2021 | |
| Risk Ledger | £106,910.00 | £237,040.00 | |||||
| Cyber Smart | £250,000.00 | £350,000 | |||||
| Bobs Business | £1,173,220 | £275,220.00 | |||||
| Trust Elevate | |||||||
| Capslock | |||||||
| Threat Status | £145,000.00 | ||||||
| Investment* | 2016 | 2017 | 2018 | 2019 | 2020 | 2021 | |
| Risk Ledger | £138,256.50 | £1,264,450.06 | £0 | £2,100,000.00 | |||
| Cyber Smart | £230,764.50 | £155,000.20 | £1,300,000 | £5,500,000.00 | £2,563,637.01 | ||
| Bobs Business | £0 | £0 | £0 | ||||
| Trust Elevate | £50,000.00 | £0 | £0 | £279,999.65 | |||
| Capslock | £137,000 | £900,000.00 | |||||
| Threat Status | £399,999.60 | £0 |
*Source: Beauhurst
**Source: Plexal and Beauhurst
Empty cells in the table indicate that no data is available. Data indicates that Cyber Smart’s number of employees increased fourfold between 2019 and 2020, consistent with a rising level of investment over the same period, which may suggest that between 2019 and 2020 was a period of expansion for the company as funds were raised, which was reflected in the company’s growth in size. During the same period, the firm also experienced an increase in turnover. This further suggests Cyber Smart, a cyber infrastructure service provider, capitalised on the surge in demand for digital security services as work-from-home working policies were in place for most companies during the pandemic.
Unlike Cyber Smart, Bob’s Business’s turnover fell between 2019 and 2020 during the outbreak of the pandemic. Since Bob’s Business has an average of 21 employees over the years 2016 – 2021, which makes them the biggest firm among all the seven start-ups, it was possible that its relative scale led to a high cost of keeping the businesses afloat compared to the rest of the start-ups in the case study. As a result, this could potentially reflect a drop in turnover and reduction in employee numbers.
The period 2019-2021 also shows that Bob’s Business was not as popular among investors with zero investment across the three consecutive years. This indicates that investors did not prioritise Bob’s Business as a cyber security course provider despite an increasing trend of working-from-home policies that potentially raised the demand for cyber security awareness among remote employees. Since Bob’s Business was relatively scaled compared to other early-stage companies, this might reflect the law of diminishing marginal returns, which suggests that investors would expect a lower potential return from investing in a larger firm.
On the other hand, another start-up that has seen rapid growth is Risk Ledger, with its employees rising from 2 to 12 from 2018 to 2021. Due to a lack of data, we do not have information regarding Turnover and Investment for Risk Ledger before 2017. Nevertheless, from 2018 through 2021 Risk Ledger continued to attract investors, with 2021 registering the highest investment so far. Risk Ledger appears to have benefited from the pandemic as NHS Test & Trace selected the start-up as the gatekeeper for the national healthcare provider’s supply chain. This could potentially reflect the rise in turnover between 2020 and 2021.
On the basis of the information available, the majority of the start-ups appear to be doing well, with four out of six firms receiving investments in 2021. From 2020 to 2021, Trust Elevate saw a significant increase in investment raising close to £300,000. In 2021, Capslock secured investment of just under £1m. There is, however, a lack of usable data, which makes it difficult to interpret the full picture of the growth and future prospects of these start-ups.
5.5 Summary
The realised benefits from the LORCA programme are likely still being experienced by participating firms. Key performance indicators such as revenue usually take a few years to have any signs of impact due to the lag in experiencing the programme, building in teaching and learning, and developing products and services to generate sales.
At this early stage however, there are initial signs of a potential positive impact from the programme. Using the Beauhurst data set on fundraisings for SMEs in the cyber sector we can see that the trend pre-programme for both treatment and control firms was declining. This could have been driven by Brexit uncertainty and company’s financial cycles. Post-LORCA we see a positive trend in fundraisings for both groups of firms, but LORCA participants experienced a stronger positive trend in equity fundraisings. This trend has not been disseminated from external impacts such as market size or economic risks for example.
There are data limitations to the analysis which have been described above such as small sample sizes, both total participants and per cohort. Realisations of impacts through increased investment in R&D and other broader business activities to generate sales revenue have a lagged element. A future consideration to estimating the impact of the LORCA programme would be through DiD econometric modelling as theoretically described above. By applying statistical inference on fuller datasets allows for the estimation of an average treatment effect. This corresponds to the LORCA specific impact on participating firms compared to the counterfactual group. At this stage, due to insufficient sample size and lack of post LORCA participation data, the results are indicative.
6 Conclusions and recommendations
6.1 Conclusions
The overarching questions for this evaluation were as follows.
- To determine how the LORCA Programme has performed over the last four years, and if the programme has met its objectives and policy goals (performance against objectives). (Evaluation Question (EQ)1: Performance)
- To clarify if the programme has produced benefits other than those outlined in the original business case, including benefits in relation to diversity, reputation and socioeconomic benefits. (EQ2: Spillovers)
- To help DCMS understand the impact of the programme and issues related to government intervention to help grow the cyber security ecosystem and any policy considerations around this. (EQ3: Ecosystem)
- To explore whether the same level of benefits would have been achieved without government intervention. (EQ4: Additionality)
These were to be explored through process and impact evaluation, with the following sub-questions:
Process evaluation:
- P1: Was the programme delivered as intended?
- P2: What worked well, or less well, for whom and why?
- P3: Were there any unexpected or unintended issues in the delivery of the intervention?
- P4: What can be learned from the delivery methods used?
- P5: How did external factors influence the delivery and functioning of the programme?
- P6: How can the existing programme be improved to become more effective?
- P7: To what extent were the activities suited to the priorities of the participants?
- P8: What was the direct result of the LORCA programme for the direct beneficiaries of the programme?
Impact evaluation:
- I1: To what extent has the programme been successful in supporting cyber security start-ups to grow and scale at a rapid pace?
- I2: To what extent has the programme produced new ideas, leading to bold and inventive cyber security solutions?
- I3: To what extent have participants from different geographical areas been impacted in different ways and why?
- I4: To what extent have participants from different types of business been impacted in different ways and why?
- I5: To what extent can the outcomes be attributed to the intervention?
- I6: To what extent have external factors impacted programme outcomes?
- I7: What are the additional or unintended benefits of the programme?
These questions are addressed in the conclusions and recommendations that follow.
Although there is very little literature relating to cyber accelerator programmes and the measurement of their success, we found that most accelerator programmes tend to offer a similar range of activities and support, including mentorship, training events, and physical space. Those programmes that enable businesses to access a network of peers are seen to produce positive impacts for participants. This was definitely the case with LORCA (EQ1, P1).
Participants valued the technical support provided during the programme in particular, and the programme delivery staff also felt that this was impactful. However, the location of the programme in the former Olympic Park was not perceived as working so well (P2, P7).
The key lesson on delivery was the importance of the bespoke elements of the programme (P7). One-to-one support and access to networks were seen as crucial. The success of the challenges provides lessons for sustainable future delivery, allowing for an increase in connection between government, participants and industry in a way that provides greater support to the sector through its problem-solving focus and attention paid to real-world cyber issues (P4).
The major external factor affecting delivery was COVID-19. This was handled well by LORCA programme staff, who succeeded in shifting the programme from in-person to virtual delivery. (P3, P5). However, the importance of networking and face-to-face relationship development would make an entirely virtual delivery in the future less impactful. The combination of the relative ease of transition to virtual delivery and the noted importance of in-person aspects of the programme led key LORCA programme staff members to suggest that any future iteration of the programme would be delivered on a hybrid basis (P4).
The success of accelerator programmes is typically assessed using metrics such as growth in revenue and sales following programme participation. Some studies have focused on an increase in the number of workers to indicate firm growth and also the qualifications of the workforce, as a performance indicator. LORCA was tasked with growth, investment and creating jobs, and succeeded in delivering on all aspects, exceeding its targets in most cases (P1, P8, I1). The programme has delivered on its key economic performance indicators over the course of the 5 cohorts delivered in 3 years, with gross impacts of:
- 72 businesses supported
- 865 jobs created (against a target of 500)
- £37m of revenue uplift
- £210m investment raised (against a target of £40m) [footnote 85].
These indicators were recorded by the programme monitoring information and represent an increase over the period of the support from a baseline when the companies first joined the programme. However, it is not possible to attribute all this growth directly to LORCA, as the companies would be likely to have achieved at least some growth through other means. The data available for our counterfactual analysis was not sufficient to be able to robustly discern a difference between LORCA companies and a control group; benchmark information from other initiatives, though highly variable, suggests that very roughly half of the observed benefits would have occurred in the absence of LORCA.
The full impacts of LORCA on the supported companies will take time to materialise, as the companies use the knowledge they have gained to develop new products and services and generate sales. At this early stage however, there are possible initial signs of a positive impact which is attributable to LORCA (I5) due to the performance of LORCA firms relative to the control group. Even though there is apparent better performance for the treatment group, the impact cannot be robustly / causally attributed to LORCA and there might be other factors involved.
LORCA firms are typically from ICT sectors and are even more concentrated in London than the wider sector (with 53% of the companies in our survey sample coming from London, as against 33% in the latest Cyber Security Sectoral Analysis). As such, it is difficult to conclude on any regional or sectoral differences in support (I3, I4).
Overall, our survey, though limited in size, would suggest that the processes for participants were conducted in a fair and transparent manner, though given the lack of management information on some aspects of the programme, it shows that taking a light touch approach to monitoring and not enforcing mandatory reporting requirements – which is very difficult to do in the absence of direct funding for programme beneficiaries – can often result in incomplete information when conducting a process evaluation. However, other measures of the success of an accelerator can include the perceptions of programme alumni and wider stakeholders and much of the information sought in this area was used to formulate our recommendations.
The most significant external factor influencing the delivery of the programme (P5, I6) was COVID-19. LORCA were able to pivot mid-cohort and turned much of their face-to-face support into online activity. For many programme participants this was an unexpected benefit, given the concerns expressed about the geographical location of the Plexal site (I7).
6.2 Recommendations
- In terms of the future funding of LORCA we recommend that funding for the Challenges and some sort of annual in-person event for the cyber sector should continue (P2, P4, EQ3). LORCA has been successful in showcasing a model for future support; whilst DCMS continues to support the UK cyber security sector through programme such as Cyber Runway and CyberASAP, other organisations are also now active in the ecosystem and capable of delivering similar support. (EQ3).
- We recommend that the Challenges should continue to be developed further. This element of LORCA was consistently praised in our stakeholder interviews, with several key stakeholders recognising the importance of the Challenges in developing closer relationships between participants, industry, and government (EQ2, EQ3). The Challenges’ potential for providing actionable solutions to real-world cyber problems was also noted, with some of the findings from challenges already being used to inform government policy. If this potential is realised, it could also develop into a self-sustaining programme, with industry being more likely to fund activities that directly contribute to solving the real-world issues they are facing.
- The bespoke elements of the programme of support should be recognised as a key reason behind LORCA’s positive reviews and should therefore be made central to the development of future programmes (P2, P4, P6, P7). Like the challenges, the provision of bespoke mentoring and business support was positively reviewed by almost all stakeholders and participants. This element of the delivery process, when done correctly, provided participants with a more well-rounded and useful support mechanism to contribute to future growth. This bespoke approach should, therefore, continue to be implemented and developed further to increase positive impact on programme participants. A crucial element in the success of this element of delivery is ensuring a baseline needs analysis is undertaken for all participants when entering the programme to develop a precise understanding of their requirements and areas of interest. We recommend that this baseline needs analysis is undertaken in all future programmes of this nature.
- Transforming an entirely government-funded programme into a self-sustaining model over a relatively short period of time was arguably unrealistic and, therefore, we recommend DCMS consider alternative funding models in their Invitations to Tender for this work in the future (EQ3). From our analysis, it would appear that a shift from this government-funded model to one focused on private funding was simply too great to achieve in the time period given. In future, therefore, a hybrid funding model could be considered, in order to limit a programme’s reliance on government funding. In addition, this proposed model could aid in limiting economic displacement in the industry, as it provides private enterprise (e.g., privately funded accelerators) with an opportunity to partner with government in that space in order to ensure private and public interest can coexist more easily in the cyber security industry. This could also further strengthen ties between participants, government, and industry (EQ3, EQ4).
- We recommend DCMS considers evaluating the LORCA Programme at a later stage, perhaps two years post cohort 5 (July 2023). As with many evaluations of this nature it is too early to be able to draw out any meaningful impacts from the programme. We need more evidence about key performance indicators such as investment and revenue, so that econometric modelling can then be applied to better determine LORCA specific impacts (EQ3, EQ4).
Acronyms and glossary
| Accelerator | Provides early-stage companies that already have a minimum viable product with the education, resources and mentorship needed to promote what might otherwise be several slow years of growth into a few short months. |
| BEIS | Department for Business, Energy and Industrial Strategy |
| CSIT | Centre for Security Information Technologies |
| Cyber ASAP | Cyber Security Academic Start-up Accelerator Programme: a pre-seed accelerator programme to support cyber security innovation and commercialisation |
| Cyber Runway | A programme of cyber accelerators and bootcamps with three workstreams: ‘Launch’, developing proposals and establishing new businesses; ‘Grow’, providing business skills to help start-ups survive and grow; and ‘Scale’, building skills and networks to address barriers to growth nationally and abroad. |
| DCMS | Department for Digital, Culture Media and Sport |
| DiD | Difference in Differences |
| EPSRC | Engineering and Physical Science Research Council |
| FTE | Full Time Equivalent |
| GCHQ | Government Communications Headquarters |
| IAB | Industrial Advisory Board |
| LORCA | London Office for Rapid Cyber Security Advancement |
| Incubator | Helps entrepreneurs refine business ideas and build their company from the ground up. |
| ITT | Invitation to Tender |
| MVP | Minimum Viable Product |
| NCSC* | The National Cyber Security Centre |
| NCSS | National Cyber Security Strategy |
| PETRAS | Privacy, Ethics, Trust, Reliability, Acceptability, and Security |
| PoC | Proof of Concept |
| R&D | Research and Development |
| SME | Small and Medium Enterprises |
| UKRI | UK Research and Innovation |
Appendix A: evaluation questions
| Programme | Evaluation Questions |
| LORCA | Process Evaluation: |
| 1. Was the programme delivered as intended? | |
| 2. What worked well, or less well, for whom and why? | |
| 3. Were there any unexpected or unintended issues in the delivery of the intervention? | |
| 4. What can be learned from the delivery methods used? | |
| 5. How did external factors influence the delivery and functioning of the programme? | |
| 6. How can the existing programme be improved to become more effective? | |
| 7. To what extent were the activities suited to the priorities of the participants? | |
| Impact Evaluation: | |
| 1. What was the direct result of the LORCA programme for the direct beneficiaries of the programme? | |
| 2. To what extent has the programme been successful in supporting cyber security start-ups to grow and scale at a rapid pace? | |
| 3. To what extent has the programme produced new ideas, leading to bold and inventive cyber security solutions? | |
| 4. To what extent have participants from different geographical areas been impacted in different ways and why? | |
| 5. To what extent have participants from different types of business been impacted in different ways and why? | |
| 6. To what extent can the outcomes be attributed to the intervention? | |
| 7. To what extent have external factors impacted programme outcomes? | |
| 8. What are the additional or unintended benefits of the programme? |
Appendix B: rapid evidence assessment
Introduction
Although the focus of the evaluation of the LORCA Programme is quite narrow, we undertook a rapid evidence assessment of some of literature around cyber accelerators to further aid our understanding of the context in which LORCA is operating, to see how other programmes have been delivered and to explore evidence about what they have achieved.
Methodological approach
Our approach to identifying evidence involved a purposive approach to searching key terms (‘accelerators,’ ‘incubators’, ‘cyber security KPIs’ and ‘innovation hubs’) in journals and across research papers, international government papers, policy papers, and corporate documentation; and mining publisher repositories for information, such as Elsevier’s ScienceDirect, Emerald Insight, Springer Link, and Wiley Online Library, and SSRN Online Library.
We reviewed literature covering the last 16 years. Duplicate records were then removed, and the remaining studies prioritised for relevance and robustness. In reviewing studies, team members extracted descriptive information, such as the KPIs used to assess the success of accelerator programmes and their spillover effects. Information about the work of existing cyber accelerators was also extracted. Findings were summarised thematically and include:
- Types of cyber security accelerators;
- Accelerator programmes and the impact that these have on programme participants;
- Characteristics of high-performance accelerator programmes;
- Variables used to assess the success of accelerator programmes; and
- Spillover effects of accelerator programmes.
Existing cyber security accelerators
In recent years the growth in the global cyber ecosystem has led to the establishment of various cyber accelerator programmes and hubs. There is a dearth of publicly available information on cyber accelerator programmes, such annual reports, and a particular lack of evaluation evidence. However, the websites of cyber accelerator programmes tend to contain detail on the offer and the support available to companies which we have also drawn upon to provide additional context and insights about the market within which LORCA sits. The impacts of accelerator programmes are also supported with testimonies from previous programme participants for various accelerators.
Cyber accelerators with global objectives
Cyber security accelerators tend to be of two types. On the one hand, some cyber accelerator programmes aim to have a global impact, such as the FinSec Innovation Lab in Tel Aviv, which was established to test and develop products and solutions in financial cyber security for the payments and energy ecosystem globally [footnote 86]. Additionally, a Melbourne based accelerator, CyRise, is open to founders from anywhere in the Asia-Pacific region and focuses on supercharging the growth of early-stage cyber security start-ups [footnote 87].
Cyber accelerators with local hubs
Other cyber accelerators have slightly different objectives aimed at their local cyber security industry. There is a focus among many cyber accelerators to catalyse innovation by bringing the local ‘cyber security community together’ as quoted by Cyber NYC [footnote 88]. Both the New York’s ‘Cyber NYC’ and Cheltenham’s ‘Cynam’ programmes aim to make their regions a cyber hub by establishing a platform for collaboration and a cyber eco-system that enables entrepreneurs and companies to thrive. Other accelerators also focus on their geographical area including ICE71, a cyber security start-up hub that aims to strengthen Singapore’s growing cyber security ecosystem to mitigate the rapidly increasing cyber security risks in the region [footnote 89]. Boosting innovation and employment in an area has its benefits, but the geographically focused accelerator has also been found to create logistical issues for participating companies who have to relocate to where the accelerator is (Christiansen 2014).
Cyber accelerator programmes
Research by Bone, Allen and Haley (2017) defines accelerators by a set of characteristics pertaining to a fixed duration programme (usually between three and twelve months) that is growth based and typically provides seed funding, physical space and start-up services including mentorship and entrepreneurial training. They also state that these programmes are typically designed to have admission in cohorts and are highly selective.
In reviewing existing Cyber accelerator hubs, it is apparent that they offer an array of services with an overarching objective to create a cyber ecosystem that encourages innovation among industry stakeholders. Across the accelerator programmes this is most often facilitated through workshop-style events, mentoring and funding.
Mentoring would appear to be the most common form of business support reportedly offered by accelerators (Bone, Allen and Haley, 2017) with Christiansen (2014) claiming it to be one of the most consistently cited benefits of an accelerator programme for start-ups despite evidence of companies finding mentors ineffective and unqualified in very specialist areas. Other accelerator activities and support includes access to peers, help with team formation, direct funding, and press or media exposure, all of which are found to have positive impacts on participants (Bone et al., 2019). Such social relationships may facilitate vicarious learning from the experiences of others, providing essential information including insights about the failures of others (Hallen, Bingham and Cohen, 2017). However, the same study also discusses time compression diseconomies, suggesting that ventures participating in an accelerator may fail to absorb the knowledge provided by the accelerator, possibly learning less than they would have had they not participated in the accelerator.
Basic services and co-working spaces are typical characteristics of accelerator programmes but the evidence suggests that they have little effect on company performance if provided alone. If, however, coupled with entrepreneurship training or coaching, these programmes can lead to a significant increase in new venture performance (González-Uribe and Leatherbee, 2017). This theme is echoed across the literature highlighting that while finance is important, it is not the primary motivation or reason for going through an accelerator (Christiansen 2014) and that venture growth is still prominent despite no cash provision especially among companies with high-growth potential (González-Uribe and Reyes, 2019).
Assessing the success of accelerators
There are a number of ways by which successful outcomes can be analysed for companies participating in accelerator programmes:
Revenue growth and sales
Some research has looked specifically at the increased revenue growth experienced by participating companies (Roberts et al 2016) finding up to a 157% revenue increase relative to the baseline, even in cases where no funding was provided by the accelerator. This is thought to reflect the added-value sources of training in business accelerators beyond business instruction, including advice from mentors and staff, access to a network of like-minded individuals, and certification and self-validation effects from selection (González-Uribe and Reyes, 2019).
Some research uses data on sales to assess the success of accelerator programmes, as a way to gain insight on the economic output of participating firm in a particular year (Lasrado et al., 2015). Sales are included in the work of González -Uribe and Leatherbee (2017) with ‘The What Works Centre for Local Economic Growth: Incubator Toolkit’ finding some evidence that incubator programmes may increase participating sales (Bone et al., 2019). This is further supported by the work of Hallen, Bingham and Cohen (2017) that finds that accelerator programmes tend to raise customer traction for participating companies. There is also potential for firm’s performance to continually improve beyond the incubation period, having long term positive effects on both sales and employment (Lasrado et al., 2015).
Employment
Other literature looks at factors pertaining to employment within participating companies including changes to the number of employees since attending the accelerator programme, as this provides an insight to the firm’s rate of growth (Lasrado et al. 2015). This metric also features in literature focusing on university incubation programmes and finds evidence that programmes have a positive impact on employment (Bone et al., 2019). However, the incubation of business ideas may not always result in positive enterprise growth as the emphasis on job creation can contradict investors’ advice putting significant pressure on the demand for minimising wage bill expenditure by the investing firms, reducing the recruitment process (Newton, no date).
Furthermore, the potential for employment growth is reliant upon business survival and success with Bone et al. (2019) finding that accelerator programmes have positive effects on both survival and revenue. Although it must be noted that this positive effect on start-up survival is open to interpretation with some literature finding that the support offered by accelerator programmes can promote start-up survival (Lasrado et al., 2015) while others conclude that it can decrease survival by helping firms quickly gauge the quality of business and encouraging them to drop bad ideas sooner (Bone et al., 2019).
The characteristics of the workforce are also of interest, including the change in proportion of employees that hold a degree. One study analysed an incubator environment for the transformation of research into production in the technology-based sector, using the employment of qualified personnel as a performance indicator (Dettwiler, Lindelöf and Löfsten, 2006). More research in this area is needed particularly in relation to diversity and inclusion.
Investment
Many researchers have assessed the impact that accelerator programmes have had on companies’ investment and capital raising abilities, for example the increase in funds raised is considered in research carried out by Roberts et al. (2016) and variables such as R&D expenditure and investment raised also feature in analysis conducted by Bone et al. (2019). Similar variables have been considered by González-Uribe and Leatherbee (2017) including the company’s ability to secure capital after participation in the accelerator and capital raised since inception, excluding the seed capital provided by the programme to participants. Evidence has been found by Hallen, Bingham and Cohen (2017) that ventures backed by top accelerators (TechStars or Y Combinator) are faster in raising venture capital than non-accelerator comparison ventures. Although the findings also imply that acceleration is difficult and not achieved by all accelerators, and in one case, slower capital raising was evident among ventures involved with an accelerator (LaunchBox Digital) when compared to businesses not involved with the programme.
Perceptions of programme alumni
Research by Bone et al. (2019) also considers the view of direct programme beneficiaries, including their views on the impact of programme participation and any subsequent change in innovativeness. The views of companies are seen to be a key source of data to measure the success of accelerator programmes, many of which advertise these as case studies on their website by way of promotion. Alongside this, most programmes improve their attractiveness to start-ups through developing and communicating an enhanced understanding of the needs of their clients, and improved market reach (Clarysse, Wright and Hove, 2015).
Success stories of accelerators outline the benefits felt by participants of the programmes (Dee et al. 2015). One example is the Cheltenham GCHQ Cyber Accelerator that saw nine companies develop cutting-edge products and services to enhance the UK’s cyber defences (GCHQ 2018). According to their website [footnote 90],CyRise, a Melbourne based cyber accelerator saw the survival rate of participating companies rise from 75% to 100% for cohort 1 in 2017 and cohort 2 in 2018. Miller and Bound (2011) capture the successes of other accelerators, such as the IT accelerator, Y combinator, based in California, whereby the 21 best companies that had been funded by YC, were valued at around $4.7 billion in total.
Characteristics of high performance accelerators
The work of Roberts et al. (2016) discusses the characteristics of high-performing accelerators which have been described by participants as programmes with collegial and supportive entrepreneurs, with emphasis on action, shared opportunity, partnerships and peer-to-peer involvement. This is also reflected in the work of Christiansen (2014) who found the frequently cited benefits of programme participation to include the combination of the network built during the programme, the alumni connections available, and the enhanced future networking opportunities that are the result of the prestige of the accelerator.
Other characteristics, such as the average amount of money spent on high-performing programmes, are also found to be substantially higher than among low-performing programmes. Furthermore, evidence suggests that high-performing programmes spend more time on developing soft skills, including networking, organisation structure and design, and presentation and communication skills. Meanwhile low-performing programmes spend more time on accounting, business plan development and finance (Roberts et al. 2016).
There is also a geographical aspect to high performance accelerators according to research conducted by Clarysse, Wright and Hove at Nesta (2015) which found that cities such as London, Paris and Berlin are good environments for accelerators to operate in due to their dense population of entrepreneurial ventures and a dense seed stage funding supply. This results in better circumstances for start-ups and start-up programmes to make an impact and is consistent with the findings of Steer Economic Development (2021) which demonstrate that growth is particularly strong in larger cities, which benefit from agglomeration economies and cluster effects.
Hochberg (2016) highlights the need for further research to assess which types and elements of programmes are most important for the success of an accelerator, both from the perspective of the entrepreneurs and local policymakers or businesspeople. Here, too, multiple measures of success must be considered, as “success” itself may differ based on the goals of the programme founders.
Spillover effects of accelerators
Increased investment
The reviewed literature also points to the spillover effects of accelerators on the wider regional business ecosystem. For example, there is evidence of a significant increase in both the number and value of investments made by venture capitalists into non-accelerated seed and high-tech companies in areas where accelerators have recently been launched (Bone et al., 2019). According to Hochberg (2016), this is because accelerators serve as deal sorters and deal aggregators for venture capitalists. By aggregating high potential candidates in a single location, it attracts investors who might otherwise find the costs of searching for opportunities in smaller regions too high to justify. There are similar findings in Fehder and Hochberg (2014) who found that Metropolitan statistical areas where an accelerator is established, exhibit more seed and early-stage entrepreneurial financing activity. It is highlighted that this additional activity is not restricted to accelerated start-ups, but also spills over to non-accelerated companies. It seems that attracting venture capitalists to accelerator activities through mentorship roles and events may lead to increased exposure of non-accelerator companies in the area to investors. Although, this research points to the possibility of this increase in activity to be at the detriment of other regions (Fehder and Hochberg 2014). The heavy geographical skew of the UK’s digital ecosystems may influence the spillover effects of accelerator programmes with many venture capitalists reluctant to make digital sector investments beyond London (Steer Economic Development, 2021).
Economic growth and employment
There is a consensus in the literature that accelerators and incubators play a role in helping young businesses save time, money and increase survival rates. This, in turn, has consequences for job creation, regional development, innovation and economic growth. Further to this, if non-UK companies which participate in UK accelerator programmes remain in the UK post-programme, this is likely to attract potential high-growth businesses into the country (Bone, Allen and Haley, 2017). Other research has yielded similar conclusions with one study on accelerator programmes within enterprise zones finding that accelerators have a positive effect on the local labour market in their geographical area (Ham et al 2011) and that the high survival rates of graduated companies often result in the increased employment rate in a country.
Digital ecosystems differ across the UK, with larger cities seeing more growth than other areas due to their wide range of job opportunities, large addressable labour market, and strong networks of industry contacts. For example, London appears as one of the top regions in metrics such as digital sector share of employees, digital sector services balance of trade as a proportion of GVA and venture capital investment per capita in digital sector firms. However, it also has the worst metrics for the affordability of housing and business floorspace and does not feature in the top quartile for the recent growth in digital sector employees and digital occupations (Steer Economic Development, 2021). This all suggests that the impact of any accelerator will differ depending on the geographical area and the characteristics of its digital ecosystem.
Appendix C: references
Bone, J., Allen, O. and Haley, C. (2017). Business incubators and accelerators: The national picture. [online] Available at: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/955469/business-incubators-accelerators-uk-report.pdf [Accessed 5 Apr. 2022].
Bone, J., Gonzalez-Uribe, J., Haley, C. and Lahr, H. (2019). THE IMPACT OF BUSINESS ACCELERATORS AND INCUBATORS IN THE UK. [online] Available at: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/839755/The_impact_of_business_accelerators_and_incubators_in_the_UK.pdf [Accessed 5 Apr. 2022].
Christiansen, J. (2014). Startups’ view: What do founders get from attending an accelerator programme? [online] EU Accelerator assembly. Available at: http://files.basekit.com/live229668_euacceleratorsassembly-startups-bestpracticesusecasesstudy.pdf [Accessed 5 Apr. 2022].
Clarysse, B., Wright, M. and Hove, J.V. (2015). A LOOK INSIDE ACCELERATORS - Building businesses. [online] Available at: https://media.nesta.org.uk/documents/a_look_inside_accelerators.pdf [Accessed 5 Apr. 2022].
| Cyber Security Agency. (n.d.). CSA | Innovation Cybersecurity Ecosystem @ Block71. [online] Available at: https://www.csa.gov.sg/programmes/ice71 [Accessed 6 Apr. 2022]. |
| Cyber-nyc.com. (n.d.). Cyber NYC | CyberNYC. [online] Available at: https://cyber-nyc.com/ [Accessed 6 Apr. 2022]. |
Dee, N., Gill, D., Weinberg, C. and Mctavish, S. (2015). WHAT’S THE DIFFERENCE? Startup Support Programmes ACKNOWLEDGEMENTS. [online] Available at: https://media.nesta.org.uk/documents/whats_the_diff_wv.pdf [Accessed 5 Apr. 2022].
Dettwiler, P., Lindelöf, P. and Löfsten, H. (2006). Utility of location: A comparative survey between small new technology-based firms located on and off Science Parks—Implications for facilities management. Technovation, [online] 26(4), pp.506–517. Available at: [https://www.researchgate.net/publication/228316337Utility_of_Location_A_Comparative_Survey_between_Small_New_Technology-Based_Firms_Located_on_and_Off_Science_Parks-Implications_for_Facilities_Management/link/5eb9c2eb4585152169c82945/download](https://www.researchgate.net/publication/228316337_Utility_of_Location_A_Comparative_Survey_between_Small_New_Technology-Based_Firms_Located_on_and_Off_Science_Parks-_Implications_for_Facilities_Management/link/5eb9c2eb4585152169c82945/download) [Accessed 6 Apr. 2022].
Fehder, D.C. and Hochberg, Y.V. (2014). Accelerators and the Regional Supply of Venture Capital Investment. SSRN Electronic Journal. [online] Available at: https://quebeccityconference.com/wp-content/themes/qcciir-v2.5/uploads/2014/ppf/papers/Fehder_Hochberg_Accelerators.pdf [Accessed 5 Apr. 2022].
Gonzalez-Uribe, J. and Leatherbee, M. (2017). The Effects of Business Accelerators on Venture Performance: Evidence from Start-Up Chile. The Review of Financial Studies, [online] 31(4), pp.1566–1603. Available at: https://academic.oup.com/rfs/article/31/4/1566/4104437?login=true#112927969 [Accessed 5 Apr. 2022].
González-Uribe, J. and Reyes, S. (2019). Identifying and Impacting ‘Gazelles’: Evidence from Business Accelerators. [online] Available at: http://juanitagonzalez-uribe.net/wp-content/uploads/2019/03/Gazelles_022019.pdf [Accessed 5 Apr. 2022].
GCHQ (2018). Start-ups graduate from the GCHQ Cyber Accelerator. [online] www.gchq.gov.uk. Available at: https://www.gchq.gov.uk/news/start-ups-graduate-gchq-cyber-accelerator [Accessed 5 Apr. 2022].
Hallen, B.L., Bingham, C.B. and Cohen, S. (2017). Do Accelerators Accelerate? A Study of Venture Accelerators as a Path to Success? Academy of Management Proceedings, [online] 2014(1). Available at: https://journals.aom.org/doi/pdf/10.5465/ambpp.2014.185?download=true [Accessed 5 Apr. 2022].
Ham, J.C., Swenson, C., İmrohoroğlu, A. and Song, H. (2011). Government programs can improve local labor markets: Evidence from State Enterprise Zones, Federal Empowerment Zones and Federal Enterprise Community. Journal of Public Economics, [online] 95(7-8), pp.779–797. Available at: https://www.sciencedirect.com/science/article/pii/S0047272710001878 [Accessed 5 Apr. 2022].
Hochberg, Y.V. (2016). Accelerating Entrepreneurs and Ecosystems: The Seed Accelerator Model. Innovation Policy and the Economy, 16, pp.25–51 [Accessed 5 Apr. 2022].
Lasrado, V., Sivo, S., Ford, C., O’Neal, T. and Garibay, I. (2015). Do graduated university incubator firms benefit from their relationship with university incubators? The Journal of Technology Transfer, [online] 41(2), pp.205–219. Available at: https://link.springer.com/article/10.1007/s10961-015-9412-0 [Accessed 5 Apr. 2022].
Miller, P. and Bound, K. (2011). The Startup Factories. [online] Available at: https://media.nesta.org.uk/documents/the_startup_factories_0.pdf [Accessed 12 Apr. 2022].
Newton, E. (n.d.). Startup Incubators Benefits. www.academia.edu. [online] Available at: https://www.academia.edu/34702230/Startup_Incubators_Benefits [Accessed 6 Apr. 2022].
Roberts, P.W., Lall, S., Baird, R., Eastman, E., Davidson, A. and Jacobson, A. (2016). What’s Working in Startup Acceleration Insights from Fifteen Village Capital Programs. [online] Available at: https://www.lemelson.org/wp-content/uploads/Whats_Working_in_Startup_Acceleration.pdf [Accessed 20 Mar. 2022].
Steer Economic development (2021). Department for Digital, Culture, Media & Sport: Assessing the UK’s Regional Digital Ecosystems. [Accessed 26 Apr. 2022].
www.cyrise.co. (n.d.). CyRise Alumni. [online] Available at: https://www.cyrise.co/alumni.html [Accessed 5 Apr. 2022].
www.cyrise.co. (n.d.). CyRise Cyber Security Accelerator. [online] Available at: https://www.cyrise.co/ [Accessed 6 Apr. 2022].
www.finseclab.com. (n.d.). FinSec Innovation Lab - Startup Accelerator by Mastercard & Enel X. [online] Available at: https://www.finseclab.com/en.html [Accessed 6 Apr. 2022].
Appendix D: LORCA cohort companies
Cohort 1
Ioetec
Iotech preserve the integrity, confidentiality, and accessibility of data as well as safeguard against the dangers of devices being exploited to launch cyber-attacks. As well as providing the communications and cloud infrastructure, the Ioetec solution uses encryption and authentication technology to ensure that data is secured from the sensor to the user.
B-Secur
B-Secur specialises in biometric heartbeat solutions for use in authentication solutions, as well as in other applications including health and wellbeing. B-Secur’s services include Hardware design and characterisation, Electrode and Hardware Validation, System Validation, Human Factors and Clinical Investigations, Regulatory and Quality System Support, Dry Electrode Design and Characterisation
Aquilai
Aquilai stops targeted phishing attacks and alerts employees before they mistakenly act on deceptive emails.
CyberOwl
CyberOwl builds on cutting-edge research that started its life at the Defence Academy of the United Kingdom and completed at Coventry University. CyberOwl is cutting through ever-increasing volumes of data and alerts with a platform that clearly prioritises your cyber risks informing security professionals which fires to put out first.
Think Cyber Security
Think Cyber Security are transforming security awareness with their RedFlags software product, which draws on behavioural science to deliver context-sensitive just-in-time guidance. Think Cyber Security deliver secure behaviour change for their customers. Their software product RedFlags is a highly innovative security awareness subscription solution: uniquely delivering ongoing, context-aware, and real-time security awareness to help people make secure decisions day in, day out.
Aves Netsec
Aves NetSec massively reduces exploit opportunities for attackers through vulnerability containment, detection and prioritisation. Their mission is to deliver security teams innovative solutions to increase their unit economics.
Trust Elevate
Trust Elevate pioneers, technical solutions that solve verified parental consent and age-checking challenges, for businesses that serve children and young people.
Surevine
Surevine builds secure, scalable collaboration solutions for the most security-conscious organisations. It joins people up and enables them to collaborate even when there is highly sensitive information involved. Surevine develop and integrate a software into your companies’ system to share confidential information with other organisations like customers or suppliers.
Zone Fox
Whether employees are purposely exfiltrating data, or intentionally breaching data security policies, ZoneFox locks down the insider Threat. ZoneFox, a Fortinet company, is a unique UEBA cyber security solution that delivers Insider Threat protection through valuable, actionable insights.
Cohort 2
Xanadata
Xanadata can analyse massive amounts of unstructured data at incredible speeds bringing insights to multiple applications and business sectors. They provide business to business (B2B) consultancy in the areas of cyber security and fraud. They develop and build custom hardware and software to allow organisations to rapidly identify vulnerabilities, threats and risks caused by systems connecting to the internet.
OutThink
It’s able to scale and automate the processes required to identify, understand, measure and change human behaviour in the context of cyber security. OutThink is a revolutionary Human Risk Management Platform (SaaS) empowering CISOs by targeting the source of 90% of all data breaches: human behaviour.
CyNation
Using machine learning and data analytics, its CyDesk product provides a continuous, unified view of an organisation’s security position and threats across departments. CyNation offer training programme, both online and in person on the following topics: Writing an Information Security Policy, GDPR, Cyber Risk Awareness, Crisis Management, and Incident Response Planning and Various other GDPR modules from general to function and industry focus.
CASQUE SNR Technology
CASQUE SNR is a mutual, multi-factor authentication methodology that includes key distribution and key management. CASQUE handheld Tokens are active devices that resist cloning. Fundamental in the design of CASQUE SNR is the capability to dynamically change keys so there is nothing for a Hacker to discover or for a complicit insider to disclose, delivering powerful deterrent again Insider Attacks.
ObjectTech
ObjectTech is transforming how people travel. It has created a global distributed identity ecosystem for consumers, businesses, governments, and not-for-profit organisations across several sectors. Its digital passports are designed to allow travellers to go from plane to taxi without having to stop at a gate.
Crypto Quantique
Crypto Quantique’s Quantum Driven Secure Clip uses quantum processes in semiconductors. Combined with new, quantum-safe cryptographic algorithms, it’s crated a security platform that makes end-to-end security seamless and easy to implement for today and tomorrow’s connected devices.
Razor Secure
RazorSecure provides intrusion and anomaly detection software for securing systems that operate in challenging rail, aviation, maritime, and automotive environments. Its software can actively detect, report and protect a system from attacks in real time, whether the mode of transport is connected or not, and it’s already detected and stopped both known and unknown attacks against critical infrastructure in the aviation and rail industries.
Cyber Smart
Cyber Smart is a cyber security company that focuses on empowering small – medium enterprises to better protect themselves in a digital way. Cyber Smart is a digital compliance platform.
Ampliphae
Ampliphae allows enterprises to discover, understand, and manage all the cloud services and SaaS applications that are in use across the organisation.
Privitar
Privitar is a company that helps organisations mine datasets containing sensitive information while preserving privacy or confidentiality. Whether it’s customer data, banking transactions, or patient records, it opens the data for secondary use without endangering privacy or confidentiality.
Bobs Business
Bob’s Business delivers award-winning cyber security awareness training and simulated phishing campaigns. By focusing on the human side of cyber security and understanding how people behave, it can help make employees an asset (rather than the weakest link).
Cohort 3
CounterCraft
CounterCraft The Service™ combines the best deception technology in the marketplace with an elite team of experts that perform continuous analysis to deliver impactful intelligence. Everything you need to detect attacks quickly and easily collect relevant, actionable threat intel powered by deception technology— without training, ramp-up time, and recruitment of key personnel.
CTO Technologies
The company’s CyberCentral platform enables the public and private sectors to better manage their security risks by automating manual processes – and alleviating the strain on IT teams.
D-Risq
D-Risq develops and uses automatic, high-integrity software verification tools that are focussed on embedded systems and cyber security. The tool has been used in a range of sectors, including autonomous vehicles, aerospace and maritime.
Elemendar
Elemendar has developed an Artificial Intelligence (AI) analyst for Cyber Threat Intelligence (CTI) that tells cyber defence tools what threats to defend against. The company’s AI makes CTI machine-readable and shares it with existing tools using open data standards. This means the customer can act on all the CTI they buy and stop threats in time – whether they have human analysts or not.
Hack the Box
Hack the box is a massive hacking playground and infosec community of over 1 million platform members who learn, hack, play, exchange ideas and methodologies. It is an online cyber security training platform that allows individuals, businesses, universities, and all kinds of organisations all around the world to level up their offensive and defensive security skills through a fully gamified and engaging learning environment.
HumanFirewall
HumanFirewall transforms employees into an organisation’s strongest line of defence. And as well as being a security awareness and training platform, it also works when real attacks strike. The company gamifies learning through training and phishing simulations, builds individual risk-profiles, rewards real-time reporting and remediates incidents instantly.
Messagenius
Messagenius is the enterprise messaging tool for secure, smart, and integrated communications among colleagues. It looks and works just like the company’s everyday messenger while protecting sensitive information.
Panaseer
Panaseer’s continuous controls monitoring platform gives CISOs visibility of all assets, and the confidence that security controls are working effectively. It provides a trusted, unified view across business lines, regions, and technology platforms.
Quant Network
Quant Network is committed to building an internet people can trust. It’s recognised for having solved interoperability through the creation of Overledger, the world’s first blockchain operating system, and is leading the way for innovation and blockchain adoption.
SaltDNA
SaltDNA are a multi-award-winning cyber security company based in Belfast, Northern Ireland, that builds secure enterprise mobile communications solutions. Its product provides secure voice, messaging, conference calling, broadcasting, and image or file transfers for busy executives.
Security Alliance
Security Alliance delivers cyber intelligence services across the globe and has government, healthcare, financial services, energy critical national infrastructure clients. Its cyber threat intelligence platform ThreatMatch helps security analysts, operations teams, and security managers focus on cyber threats that will have the biggest impact on the organisation.
Storage Made Easy
Storage Made Easy provides a software solution, the Enterprise File Fabric™, which unites on-cloud and on-premises file and object storage infrastructure indexing file and object metadata and content.
SwIDch
swIDch’s OTAC technology combines elements of the three most common authentication systems – user ID/password, RSA hardware/software for generating authentication codes a tokenisation. It’s based on the world’s first 1-way dynamic authentication technology, OTAC sets a new standard for authentication in cyber security beyond the limitations of existing authentication methods.
Threat Status
The company’s Trillion service collects, analyses, and provides alerts on the billions of breached credentials from the deep web, closed forums, paste sites and the dark web, looking for the ones that belong to its clients. Its actionable intelligence can mitigate the effect of third-party breaches on organisations.
Uleska
Uleska is a scalable platform that provides continuous software security testing within DevOps software or IT projects. It automates business risk reporting and communicates security strategy value without the need for more personnel.
Cohort 4
Acreto
Acreto delivers a Security-as-a-Utility capability that protects distributed and mobile platforms. It can help you protect any technology, operating on any type of network, from anywhere.
Anzen Technology Systems
The company’s patented technology allows organisations to securely move highly sensitive or classified data from on-premises storage to the public cloud, while retaining their data sovereignty.
Avnos
Avnos is an AI powered engine to automate workload discoveries and mappings across all your environments. Leverage Avnos Discovery to close the visibility gaps that are widening with a growing remote workforce.
Contingent
Contingent is an AI-powered enterprise platform that quickly reduces the enormous burden of collecting, verifying and monitoring supply chain risk data.
IriusRisk
IriusRisk helps companies build secure software by embedding security in the design of their systems. By using IriusRisk you can: Generate a threat model within minutes, Identify threats to your product and countermeasures, Avoid delays to your deployment and speed up time-to-production, Save time, cost and development rework, Ditch the PDFs and instantly identify areas for compliance, Create a culture of collaboration between security and development teams.
Darkbeam
Darkbeam’s non-invasive threat reconnaissance platform gives you digital risk insights in seconds. Darkbeam Labs aims to: Provide a voice for our customers and partners to suggest new ideas for the product roadmap, incubate new ideas and assess their value to our users, Research relevant industry initiatives and implement appropriate developments, Create industry leading technical capabilities, Accelerate the utility of key technologies and practices, Rapidly deliver constant and consistent value to our customers and partners.
Heimdal Security
Heimdal™ combines threat prevention, vulnerability management, access management, and antivirus and e-mail security into a single platform that simplifies IT operations and helps companies stop any cyberattack, keeping critical assets, information, and intellectual property safe.
Keyless
Keyless is a deeptech cyber security company that’s building the world’s first privacy-preserving biometric authentication and personal identity management platform which eliminates the need for businesses to centrally store and manage biometric data, passwords, and any other sensitive information without compromising on convenience or privacy
Kinnami
Kinnami provides a resilient data fabric simplifying data availability, protection, and security for complex distributed networks essential to making our connected future possible and an autonomous future a reality.
L7 Defense
L7 Defense helps organisations to protect their infrastructure, applications, customers, employees, and partners against the growing risk of API-borne attacks. APIs have become critical for data sharing and applications integration and are therefore an attractive path for malicious attacks that expose organisations to new, continuously evolving threats.
Orpheus
Their powerful and award-winning technologies collect huge volumes of cyber risk data, which we analyse deploying Machine Learning and predictive analysis and our highly skilled team to enable you to stop cyber risks before they happen.
Osirium
Specialising in privileged access security, Osirium’s software allows customers to securely and cost-effectively manage all privileged access and automate complex business and IT processes.
Risk Ledger
Risk Ledger provides a service aimed particularly at the supply chain of businesses and implements strategies and training to minimize the risk of a cyber-attack to their customers supply chain. They provide a unique social network collaborative platform to help companies understand the risk in their supply chain.
ShieldIOT
Shield-IoT is an IoT cyber security and analytics software solution provider, enabling IoT service and solution providers to monitor and secure mass-scale B2B IoT/IIoT networks, reduce operational costs and generate new revenue streams.
Surecert
SureCert’s digital identity platform makes background checking for recruitment and ID verification quicker and more efficient. Like a credit check, it turns personal information into a score, making sure that sensitive personal information is kept securely.
Threat Aware
ThreatAware is a transformational Cyber Security platform that provides continuous actionable data that represents a paradigm shift in how teams manage and secure their organisations.
Licel
Their products use sophisticated protection techniques and robust cryptographic algorithms that build an in-app chain of trust. Interconnected layers of protection secure apps and SDKs against static and dynamic analysis, tampering, and network attacks.
Variti
Variti specialises in malicious bot detection and associated shielding technologies, especially for the verticals most at risk such as ecommerce, media, entertainment and financial sectors. It protects websites, apps and APIs from fraud and attacks without affecting the end user.
Vivida
VIVIDA combines storytelling, gamification, high production video and immersive content to create experiences with the power to change minds. We give your users a deep understanding of their subject areas through immersion and direct participation, helping them engage, remember and learn.
Westgate Cyber Security
They help organisations darken their networks and prevent cyber-attacks with invisible network access gates which only materialise when certain trust standards are met. Its technology makes connectivity within enterprises (and their supply chains) easier to arrange and safer to operate by ensuring connecting systems are completely invisible to third parties.
Cohort 5
Advstar
AdvStar provide external threat monitoring, threat intelligence, automation and services. Its customers span across multiple industries including banking, finance, payment cards, government, stock exchange, domain registrars, universities, hospitality, real estate developers, retail and entertainment.
Blockapt
BlockAPT helps SMEs and large enterprises protect their digital assets by unifying operational technologies and automating digital security ecosystems to protect and prevent against advanced persistent threats.
Breachlock
BreachLock™ offers a SaaS platform that enables clients to request and receive a comprehensive penetration test with a few clicks. Their unique approach makes use of manual as well as automated vulnerability discovery methods aligned with industry best practices.
Capslock
Capslock offer training programmes to fully re-skill their clients in cyber security. Capslock is a revolutionary educational organisation. They re-skill adults into cyber professionals in as little as 4 months. They provide cyber re-training education, delivered online by industry professionals.
Contextspace
ContextSpace has developed a comprehensive privacy information management system platform that enables highly effective data protection, enforcement of regulatory compliance and the fulfilment of data subject rights.
Cyberhive
CyberHive’s patented technology CyberHive Trusted Cloud was co-developed with the University of Oxford and is a real-time intrusion detection technology for protecting critical infrastructure. Cyberhive Connect is a Direct Peer-to-Peer [Mesh] network that implements novel cryptography superior to existing standards ensuring resistance to attack by Quantum Computer.
Insurtechnix
InsurTechnix combines AI, analytics and automation to help cyber insurers to properly price policy risks and constantly measure their portfolio exposure. Its C-suite reporting tools help businesses manage their cyber security risks. It also develops secure IoT platforms.
Itsmine
ITsMine enables corporations to stay protected from internal and external data threats. Its mission is to protect organisational data proactively, seamlessly and automatically while helping organisations stay compliant.
Miracl
MIRACL provides the world’s only single step multi-factor authentication that can replace insecure passwords, complex 2FA and expensive SMS texts on 100% of mobiles, desktops or smart TVs.
Nanotego
Nanotego delivers a technology agnostic cyber security solution that give any computing device the ability to self-govern and autonomously launch defensive countermeasures. Nanotego is a pro-active fluid platform that organically modulates it’s security posture in real-time regardless of geographic location, technology or number of nodes.
Redhunt Labs
RedHunt Labs provides attack surface management solutions and has created NVADR to solve the perimeter security problem.
Cyberfish
CyberFish blends technical guidance and behavioural analysis to deliver cyberpsychology research, learning and assessment services to organisations worldwide. Its training focuses on human collaboration and leadership – two factors identified as important predictors of cyber resilience and defence performance.
Trust Stamp
Trust Stamp is a privacy and AI company focused on the use case of identity. It’s developed a privacy-enhancing technique that can be used over any data, even highly sensitive data like biometric data, to create an Irreversible Transformed Identity Token.
Verified Visitors
VerifiedVisitors provides a unique, zero latency, multi-factor authenticated protection service for managing bot traffic, at scale. Our next-generation SaaS API protects network providers, hosting services and websites by managing bots before they reach the web estate while ensuring no good bots are blocked.
VU Security
VU Security is a cyber security company that specialises in fraud prevention and identity protection. Its mission is to provide secure digital experiences without friction, both for citizens and businesses, during the digital transformation process.
Zamna
Zamna verified health marks an industry-first in travel. Zamna empowers airlines to verify a passenger’s identity before arriving at an airport. Recognised by airlines, technology experts and investors as playing an integral part in the future of identity management within airlines, Zamna addresses the conflicting challenges posed by increasing numbers of airline passengers, growing privacy regulations, demand for better customer experience and increased security.
Zero Guard
ZeroGuard is the singular platform for combating digital threats, designed by engineers for engineers. They are a data company which combines traditional techniques with the latest in machine learning technology and adversarial simulation.
Appendix E: stakeholders consulted
| Name | Organisation |
| Deputy Director | DCMS |
| Programme Manager | DCMS |
| Head of Policy (Cyber) | DCMS |
| Managing Director | Plexal |
| Director | Plexal |
| Innovation Ecosystem Lead | Plexal |
| Innovation Strategy Director | Plexal |
| Partner (Risk) | Deloitte |
| Executive Director | CSIT |
| Director of Strategy, innovation & Testing | Lloyds Banking Group |
| Chief Innovation Officer | Digital Shadows |
| Investor | Evolution Equity |
| Managing Partner | NSSIF |
| Head of Programme | TechUK |
| CEO | Cylon |
| Deputy Director | NCSC |
| Chair person | LORCA Advisory Board |
| CEO | MemCrypt |
| Founder | Transatlantic Cyber Security Business Network |
| Head of Policy | DCMS |
| Head of Innovation | CCAV |
| Policy Lead | DCMS |
| CEO | Enclave Networks Ltd. |
| Chairman | D-RisQ Ltd. |
| CFO | InsurTechnix Ltd. |
Appendix F: sample topic guide for LORCA/Plexal staff
| Background information: role of the interviewee |
- Please tell me about your role in the LORCA programme.
- Role in relation to LORCA design
- Role in relation to LORCA delivery
- Interaction with DCMS
- Interaction with delivery partners
- Clarity of role
- Changes to role
- Time commitment of role
- In particular, please tell me about your role in LORCA Ignite.
- Role in relation to LORCA Ignite design
- Role in relation to LORCA Ignite delivery
- Interaction with DCMS
- Interaction with delivery partners
- Clarity of role
- Changes to role
- Time commitment of role
- In particular, please tell me about your role in the LORCA Challenges.
- Role in relation to LORCA design
- Role in relation to LORCA delivery
- Interaction with DCMS
- Interaction with delivery partners
- Clarity of role
- Changes to role
- Time commitment of role
| LORCA delivery |
- What LORCA activities have you delivered or been involved in?
- Workspace provision
- Advice and support
- Training provision
- Mentoring provision
- Event planning and delivery
- Trade missions
- Others
- And what LORCA Ignite specific activities have you delivered or been involved in?
- Events
- Training or other support
- Others
- And what LORCA Challenge specific activities have you delivered or been involved in?
- Events
- Interest generation
- Recruiting Challenge participants
- Others
- In your view, how well have these activities suited the needs of participants?
- Participant priorities
- Examples of activities that suited well
- Examples of activities that didn’t suit well
- Why activities suit participants’ priorities
- Actions needed to improve activities
- To what extent do activities suit all participants or any particular group of participants?
- Examples of activities that suit all participants
- Examples of activities that suit certain groups
- How do LORCA Ignite and other LORCA activities compare?
- Similarities
- Differences
- Target group
- Intensity of support
- Activities
- Examples
- Reasons for differences and similarities
- What are the things that you think work well in the delivery of the programme?
- Examples for Lorca Live, Ignite, or Challenges
- Reason for mentioning the examples
- Factors contributing to them working well
- Any unexpected benefits
- Any unexpected negative outcomes
- And what are the things you think work less well in the delivery of the programme?
- Examples for Lorca Live, Ignite, or Challenges
- Reason for mentioning the examples
- Factors contributing to them not working well
- In particular, external factors (e.g. Brexit or COVID-19)
- Any unexpected issues
- Any unexpected benefits
- Any unexpected negative outcomes
- Actions needed to improve them
- What resources do you use in the delivery of the programme?
- Advice material for Lorca Live, Ignite, or Challenges
- Industry expert time
- Research and academia
- Other
- Reasons for use of the resource
- What external factors influence the design or the delivery of the programme?
- Examples for Lorca Live, Ignite, or Challenges
- COVID-19
- Brexit
- Supply chain issues
- Training or onboarding delivery staff
- Others
- What changes have you made to the design or delivery of the programme?
- Activities for Lorca Live, Ignite, or Challenges
- Delivery methods
- Resources used
- Target groups
- Ignite-specific changes
- Reporting arrangements
- Why did you make these changes?
- Changes in demand from participants
- Changed DCMS or other priorities
- External factors
- What lessons have you learned from the delivery methods?
- Targeting participants
- Identifying needs
- Meeting needs
- What further changes, based on the lessons you’ve learned, could be made to the design or delivery of the programme to make it more effective?
- Activities for Lorca Live, Ignite, or Challenges
- Delivery methods
- Resources used
- Target groups
- Ignite-specific changes
- Reporting arrangements
| LORCA Challenges |
- What is your view of the Challenges?
- Purpose
- Design
- Participation
- In your view, have the Challenges met their objectives?
- Examples
- Reaching target groups
- Meeting target group needs
- Improving commercialisation of cyber security products
- Improving collaboration within the sector
- Other objectives
- Reasons why they have met their objectives
- Reasons why objectives have not been met
| Closing the interview |
- Are there any final comments or thoughts you would like to share?
Thank the participant and reassure them regarding the anonymity of their responses
Contacts
Jenny Irwin
Partner
2nd Floor, North Wing East,
City House,
Hills Road,
Cambridge,
CB2 1AB
T 028 9023 4343
M 07436 268728
jenny.irwin@rsmuk.com
Matt Rooke
Associate Director
2nd Floor, North Wing East,
City House,
Hills Road,
Cambridge,
CB2 1AB
T 01223 455721
M 07436 268348
matt.rooke@rsmuk.com
Acknowledgements
This study was carried out by RSM UK Consulting LLP, with support from RSM Ireland. The RSM Project Team comprised Jenny Irwin (Partner), Dr Rachel Iredale (Director and Project Manager), Matt Rooke (Associate Director), June Graham (Senior Consultant), and Leandro Baldelli, Gregory Choi, Liam Fitzgerald, Owen Morris, Ravi Talwar, and Keala Troy from the wider Economics Consulting Team at RSM UK, and Cormac O’Flynn from RSM Ireland.
Our academic project advisors were Professor Martin Sadler from the University of Bristol and Professor Vladlena Benson from Cambridge Research Park.
We are grateful to the Project Steering Group at DCMS; the team from Plexal, particularly Diane Gilbert; LORCA participants, and all the wider stakeholders who took part in interviews or workshops with us or who completed our online surveys.
-
LORCA Impact Report (2022) ↩
-
Policy Paper: National Cyber Security Strategy 2016 to 2021 Please note an updated version of the strategy from 2022 can be found in National Cyber Strategy 2022 ↩
-
DCMS. Invitation to Tender (ITT): Evaluation of the London Cyber Innovation Centre (LORCA), 2nd February 2022. ↩
-
Department for Business, Energy, and Industrial Strategy (2021) Net Zero Strategy: Build Back Greener ↩
-
GOV.UK (2020), National Data Strategy ↩
-
The DSbD Fund and SDTaP programme are both currently being evaluated by RSM UK Consulting LLP ↩
-
Department for Business, Energy and Industrial Strategy (2021), UK Innovation Strategy: Leading the Future by Creating it ↩
-
Ipsos MORI (2022), Cyber Security Sectoral Analysis 2022 ↩
-
Ipsos MORI (2021),Cyber Security Sectoral Analysis 2021 ↩
-
PETRAS is a combination of initials of privacy, ethics, trust, reliability, acceptability, and security. See PETRAS, Launch of The PETRAS National Centre of Excellence for IoT Systems Cybersecurity ↩
-
Department for Digital, Culture, Media and Sport (2021). Record year for UK’s £8.9bn cyber security sector ↩
-
Rashid, A., Hankin, C., Schneider, S. (2020). The Future of the UK’s Cyber Security Research Position in the World. ↩
-
Ibid. As a proportion of GDP, Germany’s investment was 1.07x greater, France 1.34x greater, the USA 1.62x greater, Israel 2.3x greater and Singapore 6.5x greater. ↩
-
Ipsos MORI (2022), Cyber Security Sectoral Analysis 2022 stated that most SMEs must first prove to investors their product to be validated given the sheer range and variety of the products/services available in the market. Most investors have confidence to invest in larger firms with sophisticated buyers, but find it challenging to be convinced on the product/services provided by SMEs. ↩
-
LORCA Report 2020: Making of an Ecosystem (2020) ↩
-
Department for Digital, Culture, Media and Sport (2022), Cyber Security Sectoral Analysis 2022 ↩
-
Ipsos MORI (2022). Cyber security skills in the UK labour market 2022 Findings report ↩
-
Cybersecurity in the EU: A strategic priority for 2021-2027 (2021) ↩
-
LORCA Report 2020: Making of an Ecosystem (2020) ↩
-
Drawn from Ipsos MORI (2022), UK Cyber Security Sectoral Analysis 2022. The definition of small-sized firms refers to firms with numbers of employers between 10 and 50 and with turnover less than €10 million or with balance sheet total less than €43 million. ↩
-
ibid, the definition of micro-sized firms refers to firms with numbers of employers less than 10 and with Turnover less than €2 million or with balance sheet total less than €2 million. ↩
-
Ipsos (2022), ibid, the definition for Large: Employees >=250 and Turnover > €50 million or Balance sheet total > €43 million; for Medium: Employees >50 and < 250 And Turnover <= €50 million or Balance sheet total <= €43 million ↩
-
ibid. ↩
-
ibid. Note 6.0% is a result of 87 firms out of the total number of 1,483 identified cyber security firms in 2021. (i.e., 87 / 1,483 = 5.9%) ↩
-
ibid. Note 5.0% is a result of 56 firms out of the total number of 1,221 identified cyber security firms in 2020. (i.e., 56 / 1,221) = 4.6%) ↩
-
ibid ↩
-
ibid ↩
-
Ipsos MORI. (2021). Understanding the Cyber Security Recruitment Pool suggests that the cyber sector had an annual shortfall in 2021 of 10,000 people, with the prospect of the widening of the shortfall since demand could potentially increase in future. ↩
-
Ipsos MORI (2022), Cyber security skills in the UK labour market 2022 Findings report Estimates look across both technical and non-technical roles in cyber and non-cyber companies ↩
-
In Ipsos (2022) study, around 51% of 947 businesses that were surveyed responded that they incurred a basic cyber skill gap. By applying the figure 50% to the number of total business population data available on BEIS, it can be extrapolated that around 697,000 businesses in the UK were affected by the basic skill gap. ↩
-
An organisation can achieve Cyber Essentials certification by undergoing annual assessments to prove they have a minimum level of cyber security protection. For detail, please see the NCSC website. ↩
-
Ipsos MORI (2022), Cyber security skills in the UK labour market 2022: findings report ↩
-
The definitions of investment are sourced from Beauhurst’s Glossary of Terms. See: Beauhurst. (2022). How We Classify Company Stages of Evolution ↩
-
Cyber security sectoral analysis 2022, page 41 ↩
-
Ipsos (2022) UK Cyber Security Sectoral Analysis 2022 ↩
-
Type of investors are discussed in Beauhurst, see ibid. ↩
-
ibid. ↩
-
DCMS. Invitation to Tender (ITT) for: Evaluation of the London Cyber Innovation Centre (LORCA), 2nd February 2022. ↩
-
As of 27/06/2022 ↩
-
Dell.com, Making Progress with LORCA (2020) ↩
-
Of the 55 LORCA companies in the Beauhurst sample, three were acquired by overseas companies during or after their participation in the LORCA programme. Beauhurst has ceased tracking them in this case. The data used from Beauhurst corresponds to the point in time when these firms were UK-based (prior to their acquisition by overseas companies), so our analysis of this LORCA background information does not change. ↩
-
LORCA Impact Report (2022) ↩
-
LORCA Impact Report (February 2022) ↩
-
DCMS Evaluation of G&I Programmes – client document ↩
-
https://cyber-nyc.com/ https://technation.io/news/tech-nation-cyber-the-uks-first-cyber-security-growth-programme/ ↩
-
Tech Nation Cyber- the UK’s first national cyber security scaleup programme (2019), ↩
-
NCSC Annual Review (2021)- ↩
-
LORCA Impact Report (2022) ↩
-
From Beauhurst. As later explained in section 5.3 Secondary data analysis, management information on LORCA participating companies refer to companies raising equity at the status of “Seed”, “Venture”, or “Growth” at the time of funding, meaning they were early-stage revenue generating companies with high growth prospects. ↩
-
Most recent version archived at GOV.UK. (2014). Additionality Guide ↩
-
The base size of the survey question on investment prior to LORCA was 24, whereas the base size for the question on investment following LORCA was 23 ↩
-
£66 was converted from USD using the foreign exchange rate on 23rd June 2022. See Plexal. (2020). LORCA member Privitar has closed an $80m Series C funding round. [online] Available at: www.plexal.com/lorca-member-privitar-has-closed-an-80m-series-c-funding-round/ ↩
-
As set out in section 4.9 on economic indicators above: just because these impacts occurred since the start of the LORCA support, it does not necessarily follow that they arose because of the LORCA support, or that the companies would not have found a different way to achieve these impacts to some extent in the absence of LORCA. ↩
-
UK Technology Fast 50. 2019 winners Privitar Privitar Ranked as One of UK’s Fastest Growing Companies for Second Consecutive Year by Deloitte’s 2020 Deloitte Technology Fast 50 ↩
-
This would suggest that investors did not risk investing in firms they didn’t invest in before. But it could also be possible that investors stopped investing in some firms, and started to invest in new firms, resulting in a change in composition, despite the percentage of firms who received no investment remaining at 30%. Either way, it would be premature at this stage to attribute changes to LORCA, as discussed in section 4.9 on “economic indicators” and “additionality”. ↩
-
Base size 18 with 6 respondents skipping the question. ↩
-
Business wins means any new tasks or projects the businesses do for clients. These projects or tasks may, for instance, be commissioned as a result of a tender bidding process or commissioned directly by clients. ↩
-
22 participants responded to this survey question, with 14% representing 3 of those respondents. ↩
-
As the previous footnoted, Business wins refer to any new tasks or projects obtained by the businesses to do for clients. ↩
-
Magenta Book Central Government guidance on evaluation (2020) ↩
-
Roberts, P.W., Lall, S., Baird, R., Eastman, E., Davidson, A. and Jacobson, A. (2016). What’s Working in Startup Acceleration Insights from Fifteen Village Capital Programs. ↩
-
Delivery partner for the LORCA programme ↩
-
A common problem in quasi-experimental econometric techniques such as Difference-in-Difference estimation. This refers to the fact that the validity of the study is compromised as it is not directly comparing “like-for-like” firms. ↩
-
Delivery partner for the LORCA programme. They asked participants to report on key performance indicators at four intervals. Baseline (before the start of the programme), 3 months, 6 months, and 12 months (end of programme). ↩
-
Orbis - comparable company data, Bureau van Dijk. bvd. Available at: www.bvdinfo.com/en-gb/our-products/data/international/orbis ↩
-
Whitley, E. and Ball, J., 2001. Statistics review 1: presenting and summarising data. Critical Care, 6(1), pp.1-6. ↩
-
The classical linear regression model requires normality assumptions such that Ordinary Least Square (OLS) estimators are suitable for statistical inference (i.e., using t and F test for hypothesis testing procedure with the assumption that the estimators are also random variables following a distribution of a particular functional form used in the hypothesis testing procedure). This assumption can be relaxed in a large finite sample case on the condition that the population has finite variances and the mean value, such that the estimator would be asymptotically normal (i.e., asymptotic normality property of the estimator in light of central limit theorem), in which case, we can continue to use t and F tests. However, we decided n = 74 observations was not a sufficiently ‘large’ sample size to justify the asymptotic theory invoked. Thus, we fall back on the normality assumption that plays an essential part in the case of a small sample size. With a small sample size and the double-peaked shaped distribution shown in the residual plot, we decide the point estimate in the difference-in-difference linear regression model is not usable and likely biased. See Gujarati, D.N., Porter, D.C. and Gunasekar, S., (2012) Basic econometrics https://cbpbu.ac.in/userfiles/file/2020/STUDY_MAT/ECO/1.pdf ↩
-
Fredriksson, A. and Oliveira, G.M.D., 2019. Impact evaluation using Difference-in-Differences. RAUSP Management Journal, 54, pp.519-532 ↩
-
The small sample size that remained is the direct result of our filtering and cleaning practice described above, which discusses the rationale and procedure that were taken to remove the observations that either only exist in one period or that are considered as outliers; both of which are undesirable observations for our analysis due to the bias they likely generate. ↩
-
The central limit theorem (CLT) dictates that with a large sample of independent and identically distributed random variables, the distribution of its sum would tend to normal regardless of the population distribution. See Gujarati et al (2012) Basic Econometrics. ↩
-
Please refer to Figure 15 and Figure 16 for the respective histogram of control and treatment group distributions. ↩
-
National Cyber Security Strategy (NCSS) (2016 - 2021). Note the updated version currently is National Cyber Strategy 2022. However, in this instance, we are referring to the analysis of the trend leading up to LORCA and the strategy that preceded it. It is for this reason that the previous version of the Cyber Strategy is cited here. ↩
-
Range was 0 to £5 million (Based on treatment group descriptive statistics) ↩
-
Range was up to 80 employees (Based on treatment group descriptive statistics) ↩
-
Figures coming from Slater, J. (2020). Cyber security needs more women, Capslock ↩
-
LORCA Impact Report (2022) ↩
-
FinSec Innovation Lab - Startup Accelerator by Mastercard & Enel X (finseclab.com) [Accessed 6 April. 2022] ↩
-
CyRise Cyber Security Accelerator[Accessed 6 April. 2022] ↩
-
Cyber NYC, CyberNYC (cyber-nyc.com) [Accessed 6 April. 2022] ↩
-
ICE71 (csa.gov.sg) [Accessed 6 April. 2022] ↩
