Competition document: the invisible battlespace phase 2
Updated 18 July 2019
1. Introduction
This Defence and Security Accelerator (DASA) Phase 2 competition is seeking proposals for novel and innovative technologies and approaches to enable UK Defence to effectively conduct electromagnetic (EM) operations across the air, land (urban and rural), sea, space and cyber domains.
The following broad question is posed: ‘How can UK Defence take a radically different approach to conducting operations effectively across or within an EM environment that is increasingly congested and contested?’
Please note this is the second phase of funding for a multi-phase competition. It is not compulsory to have been involved in previous phases to apply. You should however make yourself aware of the previous competition Invisible Battlespace Phase 1 and the proposals we funded. Work for this phase will need to reach higher maturity than work funded in Phase 1.
The scope and challenge for Phase 2 remains the same as for Phase 1. However, proposals will need to deliver a higher maturity innovation than phase 1. We expect the starting Technology Readiness Level (TRL) of the innovation at TRL 3. By the end of the project, we expect the innovation to be developed to TRL 5.
Phase 2 of this competition closes at midday (BST) on Monday 9 September 2019.
2. Competition Scope
2.1 Background
The EM spectrum is a critical resource used across the full range of UK defence and security operations. It is essential for communication, situational awareness, gaining information superiority, retaining full use of military and security capability and enabling joint effects in different defence and security domains. (In Defence, such resources are often referred to as ‘force multipliers’, reflecting their importance). New and innovative approaches are needed to ensure UK defence and security personnel can continue to use the EM spectrum to full advantage and are not disadvantaged when operating in the EM environment as it becomes increasingly congested and contested.
The challenge for UK Defence to use the EM spectrum most effectively arises primarily from spectrum congestion, poor spectrum management, the environment and the impact of intentional disruption, principally from adversary electronic warfare (EW) capabilities. EW is military action that exploits EM energy to provide situational awareness and achieve offensive and defensive effects.
With the ever increasing demands placed upon the EM environment there is, more than ever, a requirement for UK defence and security personnel to have capability to be able to dynamically sense, understand, obscure, communicate, manage and effectively conduct dynamic offensive and defensive EM operations.
Military capabilities operating in the future multi-domain battlespace will need to function in a coherent and coordinated manner within the EM environment. Solutions which enable this are of significant interest and the opportunity for integration across the domains (stated in the introduction above) should be highlighted where appropriate.
2.2 Scope
The image below illustrates the EM operating environment for Defence. The inner ring depicts friendly forces, the middle ring acknowledges civilian non-combatants (civilians who are not taking a direct part in hostilities) and infrastructure, and the outer elements represent the adversary domains. The whole of this operating environment is in scope for this competition.
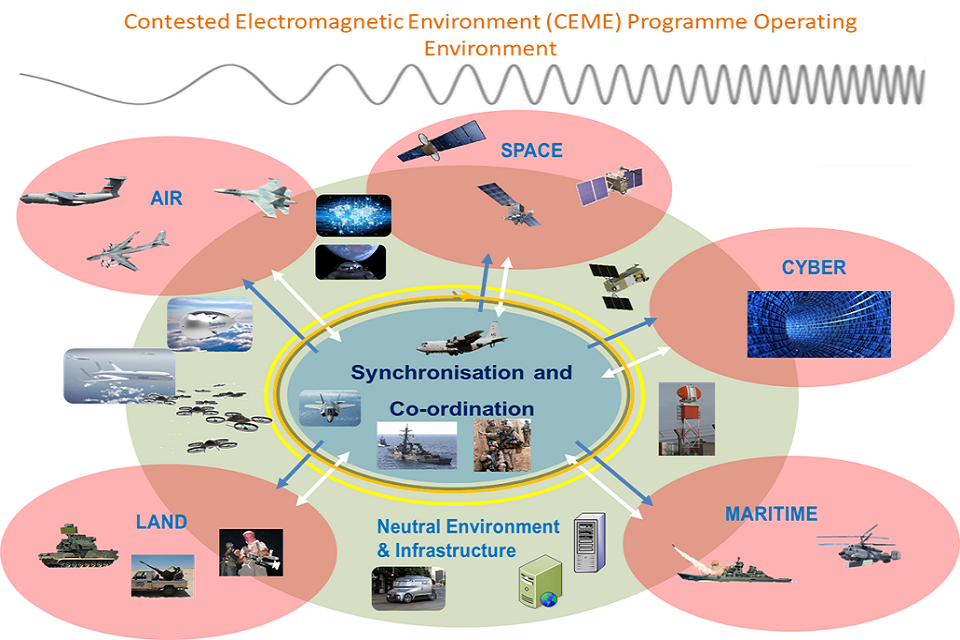
The EM spectrum covers all radio waves (for example, commercial radio and television, microwaves and radar), infrared radiation, visible light, ultraviolet radiation, X-rays and gamma rays. Factors influencing the EM spectrum include terrain, climate, solar activity and propagation media.
EM operations are all operations that enable, shape or exploit effective military activities within the EM environment (it is a force multiplier within the full spectrum of defence operations). EM operations include, or contribute to, (but are not limited to):
- EW (encompassing electronic attack, electronic defence and electronic surveillance)
- signals intelligence (SIGINT)
- electronic intelligence (ELINT)
- intelligence, surveillance, target acquisition and reconnaissance (ISTAR)
- navigation warfare (NAVWAR)
- battlespace spectrum management (BSM)
- communications, command and control (C2)
- cyber
3. Competition Challenges
This competition is divided into four challenges which are described in more detail in the Challenge section below.
Challenges 1 and 2 are broad and focused on understanding the EM environment, including how best to facilitate understanding, visualising, operating and conducting EW within a contested and congested EM environment.
Challenges 3 and 4 are more specific and focus on understanding how UK Defence could address the air defence systems of UK adversaries within the EM environment.
Whilst we are looking for ideas from across the EM spectrum (for example, electro-optical and infrared in the context of EW), the primary focus is within the radio and microwave bands. Concepts and ideas that look to utilise unconventional parts of the EM spectrum to address the challenges are also encouraged (for instance, an optical based solution to replace very high frequency (VHF) line-of-sight communication).
Whilst we invite proposals that address any aspect of the broad question presented in the introduction above, we would encourage suppliers to focus proposals on one of the following four specific challenges.
For all of these challenges we are interested in proposals that consider a systems approach, including the potential to integrate with other existing, planned or potential future EM capabilities. Whilst the whole solution is not expected within Phase 2, the proposal could offer part of, or be an important step towards, a greater integrated solution to the challenge further into the future.
3.1 Challenge 1: Find me a channel
We want to know what EM signals are out there, what equipment is generating them, what frequency bands they are using, how things are changing over time and how we make the best use of our equipment in the presence of all these signals.
This challenge seeks innovative proposals to improve how UK Defence can sense, manage, visualise and utilise the EM spectrum (in real-time). This should include an understanding of the impact on our systems and operations, our adversaries’ actions, and non-combatants’ use of the EM spectrum.
Ideas must contribute to EM spectrum management processes and be able to contribute to sensing, identifying and visualising the positions of a variety of EM emitters across the EM spectrum. This should include UK force emissions and EM signatures, as well as those of adversaries and civilians (including radars, radios, jammers, radio controlled improvised explosive devices and man-made noise). The operation of own force EM equipment and infrastructure should be able to be dynamically de-conflicted across the EM spectrum, geographical battlespace, time and cyberspace in order to reduce conflicts and enable freedom of action.
Proposals addressing any aspects of the challenge will be considered. Particular areas of interest include, but are not limited to:
- dynamic, real time, full spectrum situational awareness
- understanding and visualising our own, adversary and civilian electromagnetic emissions
- techniques for electronic surveillance (for example, detect, separate, identify, locate and track emissions)
- ability to enhance electronic surveillance by fusing with or utilising other sensor sources
- electronic surveillance capabilities with sufficient fidelity to cue and trigger electronic attack or cyber effects
- electronic systems with reduced reliance on position, navigation and timing (for example, relative referencing and opportunistic calibration)
- advanced EM operations battlespace management aids (for example, real-time models and simulation and analysis for situational awareness and decision making)
- automatic translation of user needs to dynamic sensor tasking cognisant of a wide range of live operational factors
- autonomous dynamic spectrum access systems for resilience, stealth and reducing spectrum conflicts
- solutions to understand, identify and auto-allocate EM spectrum
- solutions to permit coordinated and synchronised tasking of EM operations
3.2 Challenge 2: Stay in contact
We want to be able to communicate and share information with each other continuously when the EM environment is busy. We want to stop people interfering with our systems, interfere with their systems to make their life harder and disguise ourselves in the EM environment if we need to.
This challenge seeks innovative proposals to address how UK Defence can survive and conduct effective EW operations within an environment of multiple target/threat signals, multiple jammers and multiple radio systems, enabling us to operate and maintain capability effectively within the EM environment.
The key enablers to conducting effective EM operations are based primarily on combinations of:
The task (military requirement):
- sense
- intercept
- identify
- locate
- deceive
- jam
- inhibit
- neutralise
- stimulate
- protect
and the purpose (military objective):
- shared situational awareness
- indication and warning
- denial
- deception
- disruption
- degradation
- neutralisation
- destruction
- protection
For example, a combination of sensing, interception, identification and location are required to provide shared situational awareness.
Proposals addressing any aspects of the challenge will be considered. Particular areas of interest include, but are not limited to:
- unhindered, secure, reliable, capable command and control (from the highest echelons down to individuals)
- data management and efficient information dissemination
- networking across domains (joint force)
- electronic protection measures
- cognitive systems to access the spectrum, autonomously counter threats and allow rapid/continued operations against agile adversaries
- multi-function, multi-spectrum, agile, distributed, high dynamic range, wide/multi band, real-time EW systems
- technology transfer opportunities enabling operations within a congested EM environment
- EM stealth and camouflage to prevent adversaries finding, fixing, exploiting or understanding our emissions or true intent.
- EM signature management
- tools to visualise and develop courses of action using modelling and simulation
- tools to analyse and display success and impact on EW EM operations
3.3 Challenge 3: No use hiding from me
We want to find ways to overcome attempts by our enemy to avoid detection as we go about trying to find and target them.
This challenge seeks innovative proposals to help UK Defence to conduct effective operations against modern Integrated Air Defence Systems (IADS) that may be employed by potential adversaries. This includes the ability to conduct intelligence, surveillance and reconnaissance of enemy IADS in order to locate all potential targets and threats.
Such air defences are expected to make use of a number of approaches to frustrate our efforts to do this. In particular, efforts will be taken to counter our ability to target systems of interest and to hide key equipment. In order to be effective against IADS, UK Defence requires a detailed understanding of potential technologies or process-based counters to these evasive approaches which include, but are not limited to:
- use of ‘low probability of intercept’ radar signals
- use of passive detection means
- off-site cueing through shared data and networks
- ability for units to remain radar silent until very late in an engagement
- use of active missile sensors that reduce the amount of radio frequency emissions required for the support of weapons during an engagement
- emergent use of multi-spectral sensors on weapons (such as electro-optical and radar sensors combined)
Proposals addressing any aspect of the challenge will be considered. Particular areas of interest include, but are not limited to:
- methods to expose those IADS components that are hard to detect, such as radars, radio frequency communications networks, datalinks and unintentional emissions (approaches may include provoking the system to act in a way so as to be detectable by other equipment or assets)
- approaches to improve awareness of the location of IADS components and to map command and control chains though the use of the EM environment
- approaches to improve awareness of the adversary ‘Order of Battle’ (how and where the adversary capabilities are deployed) and command and control chains using the EM environments
- novel EM based concepts and effects that may disrupt, confuse or degrade IADS capabilities
3.4 Challenge 4: Taxi!
We want to know how best to transport our effect delivery options into areas where there will be many EM ‘bad guy’ sensors looking at us, to deliver our effect on target.
Novel delivery mechanisms are sought which are capable of supporting effects at long range (target is between 250 and 450 km from the launch site) and long endurance (application of effect for between 30 and 90 minutes). The speed at which the effect may be delivered is also a factor as militarily useful systems will need to be able to fit within standard planning cycles. They may also have to keep pace with other support assets such as tactical aircraft. In addition, delivery mechanisms may have to contend with adverse meteorological conditions, a contested EM environment and varying geographical and topographical factors.
Proposals should consider the benefits, technical issues and likely technical risks associated with the following:
- size, weight and power demands of the payload that the proposed solution is expected to support
- likely unit cost drivers and, where possible, how mitigating factors such as the scale of purchase may impact final unit costs
- for platform based solutions, the on board vehicle system requirements and the effects of inclusion or exclusion on the design capabilities (for example navigation, data links, provision of power to a payload)
- survivability of the delivery mechanism
- factors that affect the ‘shelf-life’ of a delivery mechanism, for example, technical and cost impacts from developing ‘containerised’ systems requiring limited if any maintenance as opposed to those that require routine servicing
- tactical implications of the proposed speed of delivery over the ranges discussed
3.5 Clarification of what we want
Proposals should address the following aspects:
- novel approaches or solutions to address the broad question or defined challenges stated
- potential for further development beyond this phase with a view to the eventual maturation into real-world technology-enabled solutions in the future
- utilisation and demonstration of a systems approach, with consideration of integration with other capabilities
- identification and demonstration of clear applicability within a joint military operating environment
- proof of technology validation in a relevant environment
- demonstration of verification and validation options for the proposed solution
- articulation of what enabling capabilities are required to support the proposed solution
- articulation of through life costs for the mature capability
- consideration of system level operational ‘measures of effectiveness’
At the end of Phase 2, we require a technical demonstration, in line with the required delivery level, of the proposed Science and Technology, which could take the form of working hardware, models, or simulation, within an application representative environment.
We want innovation, but that does not mean that proposals cannot use existing technology. Repurposing of current capabilities and commercial-off-the-shelf equipment into new, related applications may offer a potentially easy, swift path to capability development which may be highly desirable for military applications.
3.6 Clarification of what we don’t want
For this competition we are not interested in proposals that:
- constitute consultancy, paper-based studies or literature reviews which just summarise the existing literature without any view of future innovation
- are an identical resubmission of a previous bid to DASA or MOD without modification
- offer demonstrations of off-the-shelf products requiring no experimental development (unless applied in a novel way to the challenge)
- offer no real long-term prospect of integration into defence and security capabilities
- offer no real prospect of out-competing existing technological solutions
4. Exploitation
It is important that over the lifetime of DASA competitions, ideas are matured and accelerated towards appropriate end-users to enhance capability. How long this takes will be dependent on the nature and starting point of the innovation. Early identification and appropriate engagement with potential end-users during the competition and subsequent phases are essential in order to develop and implement an exploitation plan.
All proposals to DASA should articulate the expected development in technology maturity of the potential solution over the lifetime of the contract and how this relates to improved operational capability against the current known (or presumed) baseline. Your deliverables should be designed to evidence these aspects with the aim of making it as easy as possible for possible collaborators/stakeholders to identify the innovative elements of your proposal in order to consider routes for exploitation. DASA Innovation Partners are available to support you with defence and security context.
You may wish to include some of the following information, where known, to help the assessors understand your exploitation plans:
- the intended defence or security users of your final product and whether you have previously engaged with them, their procurement arm or their research and development arm
- the current TRL of the innovation and where you realistically think it will be by the end of this phase
- awareness of, and alignment to, any existing end-user procurement programmes
- the anticipated benefits (for example, in cost, time, improved capability) that your solution will provide to the user
- whether it is likely to be a standalone product or integrated with other technologies or platforms
- expected additional work required beyond the end of the contract to develop an operationally deployable commercial product (for example, ‘scaling up’ for manufacture, cyber security, integration with existing technologies, environmental operating conditions)
- additional future applications and markets for exploitation
- wider collaborations and networks you have already developed or any additional relationships you see as a requirement to support exploitation
- requirements for access to external assets, including GFA - for example, information, equipment, materials and facilities
- how you intend to demonstrate the outputs at the end of this phase, what form the demonstration would take and whether it will require any special facilities (for example, outdoor space, specific venue)
- how your product could be tested in a representative environment in later phases
- any specific legal, commercial or regulatory considerations for exploitation
5. How to apply
Phase 2 proposals for funding to meet these challenges must be submitted by midday on 9 September 2019 via the DASA submission service, for which you will be required to register.
Proposals where there is no collaboration with other organisations should be of no more than £330k cost to DASA but we welcome bids lower than this amount.
However, DASA would like to offer an additional option when submitting to this competition. If organisations are planning on collaborating and funding a joint venture then we would like to offer an upper limit of £650k, but there needs to remain a lead bidder. We would need to see clear evidence in the proposal of the benefit the collaboration brings, and a detailed breakdown of the finances across the two, or more, companies.
If successful, Phase 2 contracts will be awarded for a maximum duration of 12 months.
Additional funding for subsequent phases to increase TRL further towards exploitation may be available. Any further phases will be open to applications from all suppliers and not just those that submitted Phase 2 successful bids.
Further guidance on submitting a proposal is available on the DASA website.
5.1 What your proposal must include
When submitting a proposal, you must complete all sections of the online form, including an appropriate level of technical information to allow assessment of the bid and a completed finances section.
Your proposal must demonstrate how you will complete all research and development activities/services and provide all deliverables within the competition timescales (for this competition, the competition timescales are 12 months maximum duration). A project plan with clear milestones and deliverables must be provided. Deliverables must be well defined and designed to provide evidence of progress against the project plan and the end-point for this phase; they must include a final report. Proposals with any deliverables (including final report) outside the competition timeline will be rejected as non-compliant.
A resourcing plan must also be provided that identifies, where possible, the nationalities of those proposed Research Workers that you intend working on this phase. In the event of proposals being recommended for funding, the DASA reserves the right to undertake due diligence checks including the clearance of proposed Research Workers. Please note that this process will take as long as necessary and could take up to 6 weeks in some cases for non-UK nationals.
You must identify any ethical / legal / regulatory factors within your proposal and how the associated risks will be managed, including break points in the project if approvals are not received. MODREC approvals can take up to 3 months therefore you should plan your work programme accordingly. Further details are available in the DASA guidance. If you are unsure if your proposal will need to apply for MODREC approval, then please contact DASA for further guidance.
In addition, requirements for access to Government Furnished Assets (GFA) should be included in your proposal. DASA cannot guarantee that GFA will be available.
Your proposal must demonstrate how you will complete all R&D activities/services and provide all deliverables within the competition timescales (for this competition, the competition timescales are 12 months maximum duration). This includes the delivery of the final report. Proposals with any deliverables (including final report) outside the competition timeline will be rejected as non-compliant.
Completed Phase 2 proposals must comply with the financial rules set for this competition. The upper-limit for this competition is £330k, or £650k for collaborative bids. Proposals will be rejected if the financial cost exceeds this capped level.
Proposals must include costed participation at the following two DASA events:
- a collaboration event
- a demonstration event
Both events will be held in the UK.
Failure to provide any of the above listed will automatically render your proposal non-compliant.
6. Public facing information
When submitting your proposal, you will be required to include a proposal title and a short abstract. If your proposal is funded, the title and abstract you provide will be used by DASA, and other government departments as appropriate, to describe the project and its intended outcomes and benefits. It will be used for inclusion at DASA events in relation to this competition and included in documentation such as brochures for the event. This information (proposal title) will also be published in the DASA transparency data on gov.uk, along with your company name, the amount of funding, and the start and end dates of your contract.
6.1 How your proposal will be assessed
All proposals will be checked for compliance with the competition document and may be rejected before full assessment if they do not comply. Only those proposals who demonstrate their compliance against the competition scope and DASA criteria will be taken forward to full assessment. Failure to achieve full compliance against stage 1 will render your proposal non-compliant and will not be considered any further:
Mandatory Criteria:
| The proposal outlines how it meets the scope of the competition. | Within scope (Pass) / Out of scope (Fail) |
|---|---|
| The proposal fully explains in all three sections of the DASA submission service how it meets the DASA criteria | Pass / Fail |
| The proposal clearly details a financial plan, a project plan and a resourcing plan to complete the work proposed in Phase 2 | Pass / Fail |
| The proposal identifies the need (or not) for MODREC approval | Pass / Fail |
| The proposal identifies any GFA required for Phase 2 | Pass / Fail |
Proposals will then be assessed against the standard DASA assessment criteria by subject matter experts from the MOD (including Dstl), other government departments and front-line military commands. You will not have the opportunity to comment on assessors comments.
DASA reserves the right to disclose on a confidential basis any information it receives from bidders during the procurement process (including information identified by the bidder as Commercially Sensitive Information in accordance with the provisions of this competition) to any third party engaged by DASA for the specific purpose of evaluating or assisting DASA in the evaluation of the bidder’s proposal. In providing such information the bidder consents to such disclosure. Appropriate confidentiality agreements will be put in place.
Further guidance on how your proposal is assessed is available on the DASA website. After assessment, proposals will be discussed internally at a Decision Conference where, based on the assessments, budget and wider strategic considerations, a decision will be made on the proposals that are recommended for funding.
Proposals that are unsuccessful will receive brief feedback after the Decision Conference.
6.2 Things you should know about DASA contracts
Please read the DASA terms and conditions which contain important information for suppliers. For this competition we will be utilising the Standardised Contracting (SC) Innovation Contract, links to the contract here: Terms and Schedules. We will require unqualified acceptance of the terms and conditions. For the avoidance of any doubt, for this Themed Competition we are NOT using the DASA Short Form Contract (SFC).
Funded projects will be allocated a Technical Partner as a technical point of contact. In addition, the DASA team will work with you to support delivery and exploitation. We will use deliverables from DASA contracts in accordance with our rights detailed in the contract terms and conditions.
For this phase, £1m is currently available to fund proposals. There may be occasions where additional funding from other funding lines may subsequently become available to allow us to revisit those proposals deemed suitable for funding but where limitations on funding at the time prevented DASA from awarding a subsequent Contract. In such situations, DASA reserves the right to keep such proposals in reserve. In the event that additional funding subsequently becomes available, DASA may ask whether you would still be prepared to undertake the work outlined in your proposal under the same terms. Your official DASA feedback will indicate if your proposal was fundable or not.
7. Phase 2 Dates
| Event | Date |
|---|---|
| Phase 2 competition opens | 9 July 2019 |
| Dial-in | 15 July 2019 |
| Pre bookable 1-1 telecom sessions | 15 July 2019 |
| Competition closes | 09 Sep 2019 |
| Contracting | Aim to start in Dec for 1 year |
7.1 Supporting events
15 July 2019 – A dial-in session providing further detail on the problem space and a chance to ask questions in an open forum. If you would like to participate, please register on the Dial in Eventbrite page.
15 July 2019 – A series of 20 minute one-to-one teleconference sessions, giving you the opportunity to ask specific questions. If you would like to participate, please register on the 1-1s Eventbrite page.
8. Help
Competition queries including on process, application, technical, commercial and intellectual property aspects should be sent to accelerator@dstl.gov.uk, quoting the competition title. While all reasonable efforts will be made to answer queries, DASA reserves the right to impose management controls if volumes of queries restrict fair access of information to all potential suppliers.
