2022 cyber security incentives and regulation review
Published 19 January 2022
1. Ministerial foreword

Julia Lopez MP, Minister for Media, Data and Digital Infrastructure
The digital age is making the world more interconnected than ever before, driving extraordinary opportunity, innovation and progress. UK businesses, organisations, and citizens increasingly operate online to deliver economic, social and other benefits. This government has committed to a pro-innovation approach to governing digital technologies, and has set out ambitions to drive use and implementation of the latest technology in infrastructure and boost cyber skills across the country.
Alongside the enormous opportunities offered by this transition comes an increased threat of cyber attack. As the digital economy is growing, so too is the opportunity for malicious actors to exploit vulnerabilities in IT systems. Recent high-profile cyber incidents where attackers have attacked organisations through vulnerabilities in their supply chains, such as SolarWinds and Microsoft Exchange, along with the notable increase in ransomware attacks on organisations and critical national infrastructure such as the Colonial Pipeline in the US, have demonstrated the disruptive potential of these threats and the real world impacts they can realise.
According to the Cyber Security Breaches Survey 2021, two in five businesses (39%) report having experienced cyber security breaches or attacks in the last 12 months. Among the businesses that identify breaches or attacks, over a quarter (27%) are experiencing these issues at least once a week. However, only half of organisations have taken any action to help identify cyber security risks in the last twelve months.
COVID-19 has increased our reliance on digital technologies and has changed the cyber security landscape. Around a quarter of the incidents the NCSC responded to in 2020 related to coronavirus.
Government, industry, academia and the public have an important role in building UK resilience to counter these risks. The challenge is to build a prosperous digital society that is both resilient to cyber threats, and equipped with the knowledge and capabilities required to maximise opportunities and manage risks. Making explicit the link between good cyber security and business resilience is crucial to our mission of keeping the UK safe and secure online.
Protecting the public, UK businesses, organisations, and critical infrastructure, will always be the highest priority of this government. This publication sets out our approach to meeting this challenge and ensuring the UK economy is resilient enough to meet the ongoing demands of a modern, digital world.
Julia Lopez MP
Minister of State for Media, Data, and Digital Infrastructure
Department for Digital, Culture, Media and Sport
2. Executive summary
The cyber threat is significant and growing, yet cyber attacks are not always sophisticated. Attacks frequently succeed as a result of poor cyber hygiene and the exploitation of known vulnerabilities. For every highly sophisticated hostile state attack such as SolarWinds, there are hundreds of low-level phishing, denial of service, and ransomware attacks. Raising cyber resilience across the economy and society, even if it is just the basics of ensuring good cyber security practices are implemented consistently, is the first line of defence against cyber attacks. The government recognises this is a complex challenge that needs the involvement of businesses, organisations and the public if the UK is to succeed in becoming more cyber resilient.
Since 2016, the government has made significant progress in tackling cyber threats and improving the resilience of the UK society and economy. Through the National Cyber Security Strategy (2016-2021), the government’s efforts have been focused on addressing cyber threats to the UK. Improvements to cyber risk management have been brought about through the provision of advice and guidance from the National Cyber Security Centre, and the implementation of the General Data Protection Regulation, the Data Protection Act 2018 and the Network and Information Systems Regulations 2018. Nevertheless, a broader set of business frameworks have not yet effectively stimulated the governance and accountability needed across business to significantly improve resilience and effectively manage current and future cyber risks.
There has been an increase, across the whole economy and society, in the usage and dependence on digital services, which are employed to provide key corporate needs such as information storage, shared communications, and security. This has brought considerable benefits to industry and the UK but has also increased the breadth of cyber risks to organisations and the wider economy.
It is clear to the government that its previous approach, set out in the 2016 Regulation and Incentives Review, is not delivering the requisite change at sufficient pace and scale. Government cannot leave cyber security solely to the marketplace to deliver widespread improvements in cyber resilience. In order to improve cyber resilience across the economy and society, the government needs to be more proactive and interventionist. This paper sets out the evidence for this change in approach, and explains the proposed direction of travel for future government interventions across four key policy areas:
-
Foundations - the provision of advice and guidance on cyber risk management and the promotion of trustworthy services.
-
Capabilities - supporting skilled professionals capable of implementing advice and guidance.
-
Market Incentives - engaging with market actors to create incentives for organisations to invest in cyber security measures.
-
Accountability - holding organisations accountable for effective management of their cyber risk.
The approach set out in this Review forms part of our plan to meet the outcomes of the recently-published National Cyber Strategy which include “Building a resilient and prosperous digital UK, reducing cyber risks and ensuring citizens feel safe online and confident that their data is protected.”
The strategic policy framework.
Through this approach, the government will also deliver on its vision for the UK’s foreign, defence, security and development policy as outlined in Integrated Review’s objective of ‘building the UK’s national resilience’:
To establish a ‘whole-of-society’ approach to resilience, so that individuals, businesses and organisations all play a part in building resilience across the UK. We will seek to develop an integrated approach, bringing together all levels of government, CNI operators, the wider private sector, civil society and the public.
3. Introduction
There has been a notable global increase in ransomware attacks which can cause severe disruption to critical national infrastructure and government services. In May 2021 a ransomware attack on the Colonial Pipeline Company shut down the largest fuel pipeline in the United States for several days and led to fuel shortages across the East Coast of the country. The National Cyber Security Centre (NCSC) reported a significant rise in ransomware attacks on the UK in 2020, including an attack against Redcar and Cleveland Borough Council which cost the Council an estimated £10.4 million.
The trend suggests that attempted ransomware attacks will increase globally and in the UK, with criminals developing new techniques to circumvent cyber defences. The NCSC also identified a shift in the way ransomware attacks are carried out: rather than preventing access to data, criminals are increasingly stealing sensitive data and threatening to leak it publicly - compromising the security not just of organisations, but of individuals.
As supply chains become increasingly interconnected, vulnerabilities in suppliers’ products and services correspondingly become more attractive targets for attackers seeking to gain access to organisations. Recent high-profile attacks include the Kaseya global supply chain compromise in July 2021. Kaseya, an information technology solutions developer for managed service providers, was compromised when malicious actors leveraged a software vulnerability to target multiple managed service providers and their customers. It is currently estimated that between 800 and 1500 organisations were compromised by the attack. The incident demonstrates how seemingly small players in an organisation’s supply chain can introduce disproportionately high levels of cyber risk into the wider economy.
It is clear that organisations dependent on digital technologies are at risk of being disrupted by unforeseen incidents, both malicious and accidental. This can have a devastating impact on an organisation’s ability to function. It is in this context that the government sees business resilience and cyber security as intrinsically linked.
Threats are adapting in a fast-paced cyber environment, and so cyber security plans must be designed with the ability to evolve through periods of change. ‘Cyber resilience’ - the ability for organisations to prepare for, respond to, and recover from cyber attacks and security breaches - is key to operational resilience and continuity, as well as the growth and flourishing of the whole UK economy as we adapt to the demands of operating online.
The government needs to look at all levels of the ‘digital stack’[footnote 1] when it comes to resilience. Cyber resilience cannot be seen simply as securing data or procuring the latest technology: it is about identifying critical services and infrastructure, assessing vulnerabilities, ensuring that the appropriate mitigations and systems are in place, and creating a supportive governance structure.
This publication provides an update of the policy areas outlined in the 2016 Cyber Security Regulation and Incentives Review as priority interventions. As we have reached the end of the 2016-2021 National Cyber Security Strategy and are starting to deliver the new 2022 National Cyber Strategy, this review lays out the current state of cyber resilience, assesses the impact of available support, and recognises the impact of existing regulation on building cyber resilience in the UK economy.
Evidence[footnote 2] suggests that government initiatives since 2016 have had a positive impact on cyber security, in particular, the implementation of the General Data Protection Regulation (GDPR) and the Security of Network and Information Systems (NIS) Directive, and the establishment of the UK’s world-leading National Cyber Security Centre (NCSC). Nevertheless, evidence gathered through our annual Cyber Security Breaches Survey and our 2019 Cyber security incentives & regulation review call for evidence indicate that these efforts have not been sufficient by themselves to drive the necessary improvement in organisational cyber risk management, and to ensure the economy as a whole is adequately protected.
The government is assessing which options most effectively support the economy and society to overcome the main barriers to cyber resilience, without placing unnecessary burdens on organisations. The government aims to encourage business and organisations to effectively manage cyber security as part of broader business continuity and operational resilience risk management. In order to improve cyber resilience across the economy and society, government interventions are offered across four key policy areas:
-
Foundations - the provision of foundational advice and guidance which articulates cyber risk management best practice.
-
Capabilities - investment into training skilled professionals capable of enacting advice and guidance.
-
Market Incentives - engaging with market actors to create incentives which stimulate market-driven demand for organisational cyber hygiene.
-
Accountability - holding organisations accountable for effective management of their cyber resilience measures.
4. Review of progress 2016 - 2021
The 2016 Regulation and Incentives Review recognised that, for many organisations, lack of information can be a major barrier to action. Therefore, ahead of new requirements under the (then) upcoming GDPR and NIS Directives, the first National Cyber Security Strategy focused on preparing organisations through increased provision of support and information, in order to improve organisations capability to embed the GDPR and NIS Directive. The establishment of the NCSC was intended as a vital portal in delivering this support and information. At this stage, less explicit focus was placed on providing commercial rationales for organisational investment in cyber security.
In relation to the right mix of regulation and incentives, the 2016 Review focused on how good cyber risk management could be better embedded into corporate governance processes. Whilst there were already several proposals for regulation under consideration, the 2016 Review concluded that cyber risk management would be more effective when pursued from a positive business engagement stance, rather than instituting a culture of compliance which may not lead to transformative behaviour change. The 2016 Review therefore proposed that the NCSC engage with Boards on understanding their cyber risk and how they can improve the risk management. In response to this, and to direct engagement with Boards, the NCSC produced the Cyber Security Toolkit for Boards of all sizes to assist them in asking the right questions of the leadership teams of their organisations.
The GDPR and the NIS Directive were considered positive interventions with the potential to drive significant improvement in cyber security behaviours. However, the 2016 Review recommended their impact would necessarily be subject to regular review, noting that this assessment may lead to consideration of further government action to achieve the improvement in cyber risk management required.
Since 2016, the government, through its Cyber Security Breaches Survey has tracked the experiences of organisations with regards to cyber security breaches and attacks on an annual basis. The Cyber Security Breaches Survey 2020 found that organisations were becoming more resilient to breaches and attacks over time and that they were less likely to report negative outcomes or impacts from breaches than they were in 2016, and more likely to make a faster recovery. The Cyber Security Breaches Survey 2021 showed that some of this progress has since levelled off or in some cases deteriorated, likely as a result of businesses finding it harder to administer cyber security measures during the COVID-19 pandemic. However, overall, organisations still remain more resilient than they were in 2016.
In 2020, DCMS published The Impact of GDPR on Cyber Security Outcomes. This research focused specifically on the impact of GDPR, and similarly to the Cyber Security Breaches Survey, indicated that there have been positive changes in cyber security prioritisation and practices since the introduction of the GDPR. Since the introduction of GDPR most organisations reported that they have:
- increased prioritisation of cyber security, including at Board level
- increased spend on cyber security
- introduced new or improved cyber security policies, processes and technical controls
However, these improvements were not realised equally across all aspects of cyber security. More improvements were reported in relation to governance, risk management, data security and systems security, while less change was evident in relation to procurement and supply chain risk management. DCMS is consulting more broadly on reforms to data protection and UK GDPR, to keep people’s data safe and secure, while supporting growth and innovation across the UK.
Despite these improvements in organisations’ cyber risk management, a sizeable number of organisations that identify cyber security breaches or attacks report a specific negative outcome or impact. The Cyber Security Breaches Survey 2021 showed that 39% of businesses and 26% of charities identified that they had experienced at least one breach or attack in the last 12 months. Among those that identified breaches or attacks, one in five (21% and 18% respectively) lost money, data or other assets. One third of businesses (35%) and four in ten charities (40%) reported being negatively impacted regardless of whether they experienced a material outcome, for example because they required new post-breach measures, had staff time diverted or suffered wider business disruption.
These figures have shifted over time, with the proportions experiencing negative outcomes or impacts in 2021 significantly lower than in 2019 and preceding years. This is not due to breaches or attacks becoming less frequent but may, in part, be due to more organisations implementing basic cyber security measures following the introduction of the GDPR in 2018.
Despite these improvements, for those that experience material outcomes, the financial costs are substantial. Where businesses have faced breaches with material outcomes, the average (mean) cost of all the cyber security breaches these businesses have experienced in the past 12 months is estimated to be £8,460. The mean cost rises to £13,400 for medium and large businesses.
In addition, organisations are identifying breaches and attacks with more frequency. Among those identifying any breaches or attacks in the Cyber Security Breaches Survey in 2021, half of businesses (49%) and almost half of charities (44%) say this happens once a month or more often and around a quarter (27% of businesses and 23% of charities) say they experience breaches or attacks at least once a week.
In 2019, DCMS launched the Cyber Security Incentives and Regulation Call for Evidence to seek feedback on the core barriers organisations face in managing their digital security risks. In particular, it called on industry to identify the information and assurances that would result in organisations better prioritising and investing in the mitigation of cyber risks as part of their broader organisational resilience and business continuity.
The call for evidence was a key first step in testing our understanding of the barriers that many organisations face in managing their risks. When the government published a summary of the evidence received these barriers were outlined as:
- a range of inabilities that organisations may have, from not knowing what to do, to not having the right skills and resources
- a lack of commercial rationale or business drivers that stimulate the prioritisation of and investment in cyber risk management
- a complex and insecure digital environment within which organisations base many business operations in this digital era
Over 70% of respondents agreed that each of these three barriers presented a barrier to organisations managing their risk effectively. Respondents also highlighted two further barriers of:
- a lack of incentives to support organisations to protect their organisation online;
- insufficient regulation to compel organisations to better manage cyber risks.
The findings highlight that a lack of commercial rationale is a significant barrier for organisations, and was identified to be an even more severe barrier for micro and small organisations. Overall, our evidence suggests that softer levers and positive business engagement are not sufficient in themselves to transform industry behaviour to meet the increasing threat landscape.
Government must help company boards understand that cyber security is an integral component of the resilience of their business and must be part of their risk management. Their customers expect it, as do their shareholders. To manage cyber risks effectively, organisations must align cyber risk management with broader enterprise and digital risk management. Cyber security therefore needs to be incorporated into strong corporate governance procedures and board-level representation, building on and developing the existing support in place from the NCSC, BEIS and DCMS.
The government’s future support to improve business’ cyber resilience will therefore focus on:
- enabling better decision making and governance practices within businesses, to improve organisations’ understanding of what is both appropriate and proportionate for their own operations, and take ownership of and responsibility for their risk management
- taking a more interventionist approach to utilising market incentives and regulations in order to quickly establish better practices that keep pace with the changing risk environment and ensure responsibility is taken for the impact cyber attacks can have for their own business, their customers, and the broader economy in which they do business
5. Our approach
Our approach is to:
- increase the speed at which effective behaviours are adopted, the government will set a clear strategic framework, within the context of the resilience pillar of the National Cyber Strategy, so that it can focus on helping organisations understand the commercial rationale to adopt cyber security practices as a core part of business resilience.
- ensure sustained improvement of cyber resilience outcomes for the UK, the government will provide support across all four policy areas: Foundations, Capabilities, Market Incentives, and Responsibility (P1 - P4).
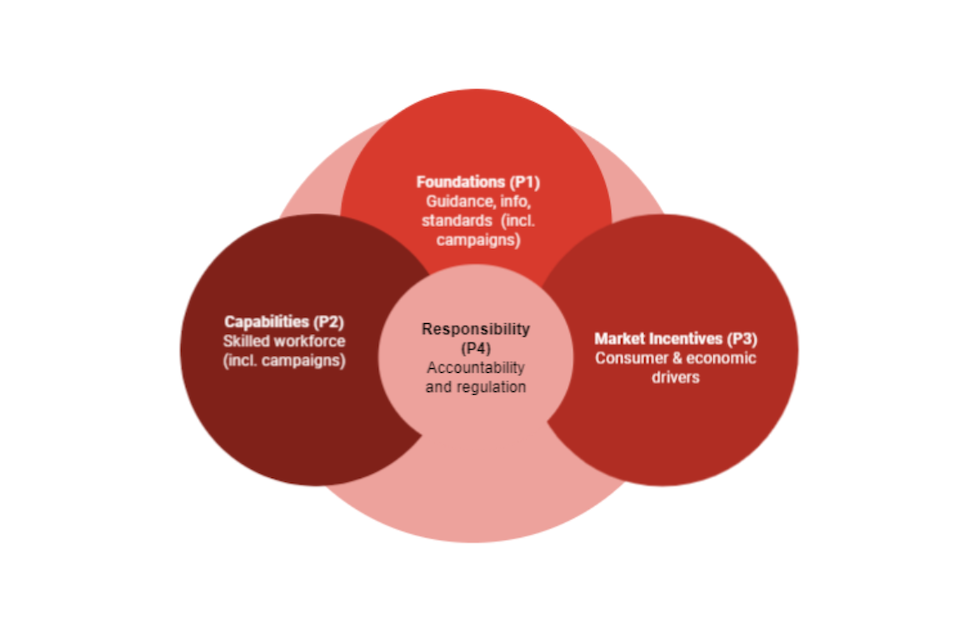
The four policy areas: a holistic approach
Foundations and Capabilities (P1 and P2), focus on how the government provides tools, support, and skills to businesses to help them understand how to implement cyber hygiene practices. The latter two areas, Market Incentives and Accountability (P3 and P4), concern the need to stimulate demand for uptake of these behaviours from either a market-driven or a regulatory perspective. Our holistic approach is consistent with the regulatory principles set out in the Plan for Digital Regulation, which commits the government to drawing on the full range of regulatory tools available, including industry-led or co-regulatory measures.
The inclusion of supply chain risk management as part of the Market Incentives workstream demonstrates that these pillars are designed to be mutually reinforcing. It is not appropriate to expect organisations to voluntarily change their behaviour, or for the government to pursue regulatory action, without supporting organisations with the provision of guidance and skills required to help organisations understand the incentives for behaviour change, and to effectively comply.
The following sections provide an outline of the existing and new priority policy initiatives in each of these four pillars. These sections will cover activity over the course of the next National Cyber Strategy, which is due to be published in late 2021.
6. Foundations: advice, guidance, and campaigns
When the National Cyber Security Strategy (NCSS) began in 2016, cyber security guidance and support was predominantly aimed at critical national infrastructure,[footnote 3] with limited support for the businesses in the wider economy.
Over the course of the NCSS there has been significant focus on creating accessible, tailored guidance and support for businesses to help address the barriers to taking action and protect against the most common cyber threats. To build the foundations of cyber resilience, the government has focused on three broad areas:
-
Raising awareness of the cyber threat.
-
Helping businesses know what to do (guidance, standards and frameworks).
-
Improving uptake of existing government support (engagement activity).
Raising awareness of the threat is an important step in the journey we want businesses to take towards action. Over the past five years, the government has run the Cyber Aware (formerly Cyber Streetwise) campaign to highlight the threat and show the public and small businesses how to protect themselves. In addition, the Police Service’s Protect programme brought dedicated cyber officers into all police forces, which has created the opportunity for local business engagement within regions.
As the government’s centre for technical expertise in cyber security, the NCSC has now created a wide range of tailored guidance for audiences across the economy and society, including the citizen. Entry-level guidance and schemes for small businesses help protect against the vast mass of low-sophistication, untargeted cyber attacks.[footnote 4] This includes the Cyber Essentials Readiness Toolkit and advice delivered via Cyber Aware.
For larger organisations, there is a wider suite of advice to support the required spectrum of cyber risk management activities. This includes comprehensive strategies and frameworks to help firms understand the range of action they need to take, such as the 10 Steps to Cyber Security, which go beyond technical measures to include governance processes and organisational culture. A board toolkit shows how senior managers can drive cyber resilience improvements, whilst online training and incident exercising are also freely available from the NCSC.
To build on awareness of the cyber threat, distribute guidance and drive adoption of cyber security measures, the government has undertaken a significant programme of industry engagement. This includes communications, campaigns and engagement by government departments such as BEIS and by the NCSC, campaigns and outreach by law enforcement, and partnership work with industry organisations and trade bodies, such as the Federation of Small Businesses and the British Retail Consortium. A key part of this has been aligning messages to NCSC technical advice and ensuring activities are informed by insights gathered via government research, and engagement with sectors across economy and society.
Many of the foundations required to drive better cyber resilience across the economy are now in place. Government guidance has been user-tested and is well-received by industry, with the vast majority of businesses that use it saying it is useful (83% in 2020 according to the Cyber Security Breaches Survey 2020). The annual {Cyber Security Breaches Survey 2021](https://www.gov.uk/government/statistics/cyber-security-breaches-survey-2021) shows improvement over time: 77% of businesses say cyber security is a high priority, up from 69% in 2016. Furthermore, awareness of the Cyber Aware campaign is up 13 percentage points from 21% in 2017 to 34% in 2021, with the campaign and associated engagement activities driving well over 100,000 businesses towards using the NCSC’s cyber security small business guide in the past year.
However, there is some way to go before we achieve the transformation in cyber resilience across the economy which was stated as an aim in the 2016 National Cyber Security Strategy. 1.4 million UK businesses employ staff[footnote 5] and many still do not take basic protective actions: only 15% of businesses have carried out an audit of their cyber security vulnerabilities, and only 14% train their staff on cyber security.[footnote 6] Only 8% of businesses have proactively sought information or guidance from government or public-sector bodies such as the NCSC.[footnote 7] Of those who recall government communications or guidance, just 37% report making changes to their cyber security as a direct result.[footnote 8]
COVID-19 has made cyber security a harder task, particularly for the smallest businesses. New threats have been presented by the rapid adoption of new technologies and the high number of staff connecting remotely. However, in 2021 only 83% of businesses report having up-to-date malware protection (down from 88% in 2020) and only 35% are using security monitoring tools (down from 40% in 2020).[footnote 9]
The challenge therefore is to increase the reach and adoption of existing activities and guidance. The key barrier to adoption for UK organisations is the lack of commercial rationale for investment and action. The UK Cyber Survey research suggests around a half of businesses (48%) do not see cyber security as a priority or think it unlikely they would be targeted.[footnote 10] Engaging more of these businesses in getting basic protections in place is a key priority, as is moving other more engaged firms further along the journey to cyber resilience maturity.
A more active approach is therefore needed to drive faster and wider adoption of cyber resilience measures. We are exploring what government interventions will broaden the reach of existing guidance and engagement in order to make cyber security become part of the standard set of good business practices. This will require greater market intervention, in particular by exploring mechanisms for increasing business accountability.
7. Foundations: standards
In addition to the provision of advice and guidance, the government has developed a range of risk management and trustworthy products and services to help organisations stay safe online by incentivising them to meet defined cyber hygiene measures. These products allow organisations to demonstrate their commitment to cyber security and provide confidence to customers, investors, insurers and other stakeholders that they have taken essential steps to manage their cyber risk.
Government currently provides a number of products that enable organisations to become confident that they are protected and insured against a range of common cyber attacks, most notably Cyber Essentials and Cyber Essentials Plus. We will continue to promote their take-up and, if necessary, measures to mandate their use where circumstances warrant it.
The Cyber Essentials scheme seeks to help organisations, regardless of size, improve their cyber resilience and protect themselves against the most common internet-based threats by setting out five basic technical controls, which can either be independently audited or tested through Cyber Essentials PLUS.
Since 2014 when the Cyber Essentials scheme was launched, over 80,000 certificates [as of the end of December 2021] have been awarded to businesses, charities and other organisations across the UK. The rate of adoption is accelerating, with 26,598 certificates awarded during 2021, compared to 19,357 certificates in 2020 and 15,945 in 2019. The findings from the Cyber Security Breaches Survey 2021 also highlight that, compared to 2016, business awareness of Cyber Essentials has grown by 8 points (14% compared to 6%) while medium and large organisations are also substantially more aware of the scheme (45% and 50% respectively).
Cyber Essentials has also been an effective product for the government to target particular communities requiring urgent support to ensure they are resilient to online threats. This was demonstrated in September 2020 when the government initiated delivery of a £500,000 Cyber Essentials Covid Funding Scheme to help small and medium-sized enterprises in the healthcare and social care sectors, and their critical suppliers, to improve their digital resilience. Over 50% of organisations that were supported through the funding scheme said they would engage further with cyber security as a result of the positive experience.
In June 2020, six years after its launch, an evaluation of Cyber Essentials was conducted by Britain Thinks to review the Scheme against its core objectives to provide a baseline for assessing the impact of it in the future. While the evaluation highlighted the positive impact of Cyber Essentials overall, it also provided certain recommendations on how it could be improved.
DCMS is currently working in partnership with the NCSC to scope a range of proposals for how Cyber Essentials could be improved. These proposals take account of key insights on barriers which organisations may experience in accessing the scheme; as well as of needs across the UK economy; the evolving threat landscape; and opportunities presented by the transition of Cyber Essentials to a singular delivery partner, the IASME consortium, in April 2020. In addition, the government will continue to evaluate the effectiveness of Cyber Essentials as a tool to help manage risks in the government supply chain in terms of coverage and depth.
The NCSC has also developed the Cyber Assessment Framework, a tool for assessing cyber resilience.
The Cyber Assessment Framework is predominantly aimed at organisations that play a vital role in the day-to-day life of the United Kingdom such as those that form part of the critical national infrastructure, or are subject to certain types of cyber regulation, including the Network and Information Systems Regulations. The Cyber Assessment Framework, and associated guidance, aims to provide a systematic comprehensive approach to assessing the extent to which cyber risks to specified essential functions are being managed by the organisation responsible.
The basis of the Cyber Assessment Framework is a set of 14 principles which collectively represent a robust level of cyber security and resilience. These principles describe important outcomes that an organisation needs to achieve in order to successfully manage the risk of disruption to that organisation’s essential functions caused by cyber attack. Since it is not a prescriptive checklist of cyber security controls, the Cyber Assessment Framework is usable by a wide range of organisations across multiple sectors. It is best suited to larger organisations that have an established level of cyber security capability.
The Cyber Assessment Framework has been widely adopted by UK cyber regulators and is the most commonly-used method by which the cyber resilience of organisations in the UK’s Critical National Infrastructure is judged. The NCSC will continue to work with Cyber Assessment Framework stakeholders to determine if sector-specific aspects of the Cyber Assessment Framework are required and, if so, to assist in introducing changes.
Although there is a wide range of existing cyber risk management certification, and assurance standards and frameworks offered by government and industry, the 2019 Cyber Security Incentives and Regulations Call for Evidence found that two thirds of respondents believed the lack of a standardised definition of effective cyber risk management was a moderate to severe barrier to organisations effectively managing their cyber risk.
In addition, insight from evidence, engagement and analysis indicates that there are a number of barriers to the take-up of existing government and industry standards and frameworks, which prevent organisations making full use of this support. These include issues of accessibility around the high cost of meeting the technical requirements of Cyber Essentials, the technical nature of the language and controls themselves, as well as concerns that existing standards are viewed as compliance exercises and therefore do not provide sufficient assurance to other interested parties that an organisation is effectively managing its cyber risk.
The call for evidence also highlighted that existing standards/frameworks are frequently viewed as unfit for purpose as they are too prescriptive and/or too basic, or at the other end of the spectrum, too vague or demanding. Respondents also noted that the complexity of the landscape caused by the multiplicity of cyber risk management standards and frameworks results in confusion as to which is most appropriate for their particular organisational risk posture. It is clear that the current standards and frameworks offer does not provide sufficient clarity in expectations around ‘how’ organisations should be thinking about their cyber risk in placing it as part of wider operational resilience and business continuity.
Over the last year, DCMS has explored whether further government intervention is required to help organisations position cyber risk as part of business risk, and outline a good practice approach for embedding cyber security throughout the organisation. Our evidence suggests that a focus on improving the governance of cyber security within an organisation can often lead to the quickest improvements in overall cyber resilience, while industry-led research also indicates that there is demand for better governance of cyber security within an organisation as a recognised aspect of improving overall organisational resilience.
We will continue to work closely with the NCSC, BEIS and other relevant Whitehall departments, industry partners and academia to further collate relevant evidence and test these findings through consideration of how an increased focus on governance could be addressed within the context of cyber risk management standards and frameworks to improve take-up, drawing on a wealth of pre-existing work including the NCSC’s refresh of existing risk management guidance and the industry-led Cyber Crossroads project and work on what makes a competent professional.
8. Capabilities
Over the course of the National Cyber Security Strategy, the government has built up an evidence base to better understand the cyber skills requirements of industry. This has included running the annual Cyber Skills in the UK Labour Market survey, the Cyber Security Sectoral Analysis, as well as a standalone research piece that focused on drawing out an understanding of the cyber security recruitment pool. This has provided a starting point from which to identify the needs of industry and the nuance of the issues faced, as well as an opportunity to benchmark progress against which to measure the impact of interventions over time.
The Labour Market survey reveals that 50% of all UK businesses (around 680,000 employers) have a basic technical skills gap within their organisation. This means they do not have the confidence to implement the basic security controls to keep their organisation safe in line with the requirements of Cyber Essentials. Basic security controls include the ability to carry out functions such as storing or transferring personal data securely, setting up configured firewalls, and detecting and removing malware. Further to this, 33% of all UK businesses (around 449,000 companies) are not confident in carrying out, and do not outsource, advanced technical cyber functions such as penetration testing, forensic analysis of breaches, and security architecture.
As well as highlighting the skills gap within the workforce, there is also a skills shortage and continuous demand for skilled candidates to be supplied to the workforce, in order to support organisations to carry out the range of tasks required. In particular, there were around 124,000 job postings for cyber security-related roles between September 2019 and December 2020.[footnote 11] This demand came from across the country, with specific hotspots in London, Leeds, Edinburgh, Belfast, as well as across the West Midlands and the South West. While this demand temporarily dipped at the start of the pandemic, it has broadly remained consistent throughout and indicates that cyber security is a high growth sector for the economy. There are an estimated 134,500 individuals working across the UK cyber security workforce, with around 7,500 new individuals joining each year.[footnote 12] However, this is insufficient to keep up with the increasing demand for skilled candidates: there is an estimated annual shortfall of around 10,000 individuals per year.
Further to the need for an increased supply of competent candidates, there is a clear diversity issue within the cyber sector. In particular:
- 16% of the workforce is female, compared to an average of 28% across digital sectors and 48% of the entire UK workforce.
- 17% of the workforce are from ethnic minority backgrounds. This is slightly higher than across digital sectors (15%) and the wider UK workforce (12%). However, this drops to 15% in senior roles within the cyber sector.
- 9% of the workforce have a disability, lower than the digital sector average (11%) and wider UK workforce (14%), and this drops to 3% in senior roles.
- 10% of the workforce are neurodivergent individuals, falling to 8% in senior roles.
In order to address this, there needs to be a consistent, quality supply of diverse talent into the field. In order to support this and stimulate an industry response to galvanise wider effort, DCMS and the NCSC have funded a number of interventions over the previous five years of the National Cyber Security Programme. This has included sustained activity aimed at inspiring the next generation of cyber security talent.
CyberFirst was launched in 2015 as a programme to identify and nurture talented students into jobs in cyber security. Initially established as a bursary scheme, the low levels of diversity among applicants meant the programme had to reach back into the education system, implementing a number of activities intended to encourage and inspire more students, especially female students, to consider a career in technology and cyber security. As well as the University bursary scheme, the programme now includes a degree apprenticeship scheme, a girls’ only competition, and thousands of free places on CyberFirst courses at UK Universities and Colleges.
Cyber Discovery was a gamified learning platform, running over four years and inspired over 23,000 young people every year aged between 13-18 years old to consider a career in cyber security, whilst identifying and nurturing promising talent from a young age.[footnote 13]
While this work has looked towards the future, the government has also supported the training market to develop and run ambitious programmes for adults with an interest in changing careers and bringing transferable skills to enrich the cyber talent pool now. This develops the profession, while also begins to address the skills shortage in the more immediate term. Activity in this space has included the funding of initiatives through the Cyber Skills Immediate Impact Fund, which focused on increasing opportunities across the UK for groups that are underrepresented in the cyber sector, as well as the recent Cyber LaunchPad initiative to support up to 200 individuals access cyber security learning and increase their job prospects during the pandemic. Activity to date has supported upwards of 1,000 individuals to obtain more basic level understanding in preparation for a potential career in cyber security.
However, for meaningful and sustainable change, there is a need to assure the range of degrees, certifications and qualifications in the cyber security landscape. Efforts to date have included the NCSC-led work to certify cyber security degrees across the UK to bring consistency to the higher education offerings and providing students with the confidence and understanding they need when making their study choices.
Government is therefore building on the academic excellence within the UK and looking to provide the appropriate structure to hone and encourage collaboration in this space that improves the offering across education more broadly. In December 2020, the first nine UK universities were recognised as Academic Centres of Excellence in Cyber Security Education (ACE-CSE). These institutions are recognised for delivering certified cyber security degrees, growing cyber security across the institution and engaging with their local community to promote cyber skills.
Further applicants will be considered to expand this cohort going forward. The institutions provide non-cyber security students with opportunities to learn about cyber security and interdisciplinary teams of educators that bring in other fields of study including politics, law and psychology, which is essential to expanding the consideration of cyber security beyond the sole focus of its profession alone.
Further to working with the academic institutions, the University of Bristol has developed the Cyber Security Body of Knowledge (CyBOK). This product defines and codifies the breadth of foundational knowledge needed by those working in or close to cyber security roles. It is intended that CyBOK will provide a foundation for consistency that can be mapped to all education and training offerings in cyber security, as part of bringing coherence and quality assurance to an active training market and learning landscape.
There has been, over the last five years, a huge amount of work across government, academia, industry and the professional landscape to develop the field and ensure its flexibility to adapt to the continually changing threat landscape, and with that what cyber security professionals need to know and be able to do. This has been illustrated by industry trailblazer groups coming together to draft, challenge and progress industry-designed apprenticeship standards at Levels 3, 4 and 6 that can be supported through the Apprenticeship Levy.
There is a need to go further. The 2018 public consultation on pDeveloping the UK cyber security profession indicated that the professional landscape remains complex and difficult to navigate. There is no universally-accepted, underpinning understanding of what it means to be a cyber security professional and how to develop within a field that is made up of different specialisms and functions that range across both technical and non-technical. As a result, DCMS have funded the creation of the new UK Cyber Security Council to bring structure, coherence and leadership to this space.
This body will set out a clear set of professional standards and ethical principles, bringing clarity to prospective new entrants, existing practitioners and employers alike. As this new body stands up over the coming years, DCMS, NCSC and wider government will increasingly work with the Council to quality assure skills interventions across the board, ensuring consistency and quality in the candidates undertaking learning, skills and development activity.
9. Market incentives: internal and external drivers
In order to establish long-lasting change in how businesses manage their cyber risk and improve their resilience levels, there remains a need to stimulate market incentives. Market drivers that could normalise investment in cyber security across the economy and lead companies to feel compelled to take up effective cyber risk management, such as strong consumer pressure and competitive advantage, have not yet formed in many sectors or across the economy. While harder forms of government intervention, including legislation, can be a useful tool to drive behavioural change from above, stimulating market incentives in parallel will ensure businesses themselves prioritise cyber resilience, and that practice continues to adapt to evolving threats.
The 2019 Cyber Security Incentives and Regulation Call for Evidence found that 71% of respondents agreed that a lack of strong commercial rationale was a barrier for effective cyber risk management. Responses from the Call revealed that there are a number of information failures preventing organisations from conducting robust cyber risk assessments, including on the threat (frequency and severity of attacks), impact or harm of cyber incidents, and the mitigation activities and associated costs that organisations need to have in place for their particular risk posture.
Given these information failures, organisations find it difficult to demonstrate a return on investment in cyber security as they are unable to quantify the level of cyber risk, and therefore cannot justify investment in cyber risk mitigations. The sensitive nature of information on the cost of a cyber incident exacerbates this issue, leading to very limited commercial offerings that support organisations to develop effective return on investment cases.
While the ‘impact or harm’ of a cyber incident can include a range of negative outcomes experienced by an organisation and its clients or customers, it is most often recognised and quantified as the costs associated with a cyber attack. For the purposes of this publication, we therefore refer to ‘impact information’ as the costs to an organisation incurred over the short and long term, including direct (such as share value) and indirect costs (such as loss of staff time).
The failure of the market to create impact information creates a case for government intervention:
- Organisations find it difficult to price impact as there is no common methodology. Organisations tend to overlook indirect, long term and intangible costs when thinking about the impact of a breach. It is likely that organisations are therefore underestimating the true cost of cyber breaches.[footnote 14] The lack of awareness, understanding and transparency of these costs represent a barrier to organisations’ ability to make appropriate, informed investment decisions and potentially results in an underinvestment in cyber security.
- Secondly, given the sensitive nature of information on the impact of cyber incidents, it has been difficult for industry to develop solutions that provide more robust information on their impact.
The government is working to develop, and make available, the impact information required by organisations to make a stronger case for prioritising and investing in cyber security.
DCMS will explore how this impact information can enable organisations to:
- Build a business case for increasing investment in cyber security, including additional cyber security insurance, or associated training;
- Position cyber security on an organisation’s risk register and;
- Provide additional evidence to support external reporting requirements, such as a cyber insurance claim.
As part of these efforts, DCMS commissioned Ipsos MORI to research the Full Cost of Cyber Security Breaches and produce a robust sector and size agnostic series of costs (and cost categories) that reflect a full assessment of total costs of a cyber attack to organisations. DCMS will explore how this methodology can be used to help organisations better estimate the full cost of breaches.
While organisations need to take action to improve their own cyber risk management, the government is also prioritising targeting those professionals who can influence and set market expectations, and are therefore able to stimulate demand for greater investment in cyber security across the UK economy. We have labelled these professionals as ‘market risk managers’ as they have the ability to normalise investment in cyber risk management across the broader economy, by driving organisations, clients and customers to prioritise cyber security as part of broader organisational resilience and business continuity.
Despite the potential that these market risk managers have to incentivise and determine how cyber security is integrated across all business operations, most are not yet operating as effectively as possible. Findings from our evidence base and engagement to date has identified three main challenges:
- Limited interest/awareness of cyber risk management. The Cyber Security Breaches Survey 2021 found that only 12% of organisations formally reviewed the cyber risks of immediate suppliers, suggesting that such risks are not widely considered by procurement professionals. Similarly, qualitative findings from the survey noted that investors and shareholders have little interest in how cyber risk is being managed by the organisations they invest in.
- The information failures relating to return on investment and likelihood of cyber attack. Even if market risk managers are aware of the cyber risk, they require information on the cyber risk posture and mitigations that organisations have implemented to manage the cyber threat.
- Limited influence. While some of the identified market risk managers are more aware and able to understand cyber risk (e.g. consultancies/ insurers), these market risk managers have less leverage over organisations as they generally provide advice and support rather than having accountability and purchasing power to incentivise organisations to improve their cyber resilience.
Over the next few years, cross-government efforts will focus on working to design interventions that enhance market risk managers’ awareness and prioritisation of cyber risk management, and enable them to most effectively utilise the leverage they have with businesses.
Looking forward, the government will focus on:
- Boards, and investors and shareholders: the NCSC will continue to iterate and evolve their support for Boards of Directors in organisations, including key guidance such as the NCSC Board Toolkit, and will lead government engagement with investors and shareholders, with guidance for increased understanding and awareness of national security threats and risk among emerging technology start-ups.
- Procurement professionals: DCMS will drive forward a policy workstream on how better to support procurers and those that manage supply chain cyber risk in organisations.
- Information technology, risk and management consultancies, and statutory audit: The Department for Business, Energy and Industrial Strategy will promote alignment and ongoing dialogue with Information Technology, Risk and Management consultants to share learning and insights on how to incentivise board uptake of, and investment in, cyber security measures. In addition, BEIS will look to build proportionate cyber security considerations into the audit and corporate reporting reform proposals on which the Government recently launched a public consultation.
- Cyber insurance: Her Majesty’s Treasury will continue to work closely with the cyber insurance sector, and explore how to make additional data available for use in modelling. DCMS’ policy focus on creating and sharing more robust cyber risk impact information will also contribute to this objective.
- UK Cyber Security Council: The UK Cyber Security Council will play a critical role in defining the skills required to perform cyber risk management in appropriate cases. This will improve the capability of professionals and through this inform how government and industry can choose training offers that have been specifically tailored to these market risk managers, in order to increase their cyber risk management understanding and capability.
By working in this way, the government aims to raise awareness of the cyber threat and potential impacts of cyber risk, encourage these market risk managers to prioritise cyber resilience and urge the organisation that they influence and advise to improve their cyber security, and enhance these market functions capability so they can better hold organisations to account or support them to become more secure online.
10. Market incentives: supply chains
Cyber threats are increasingly reaching organisations through vulnerabilities in their suppliers, or supplied products and services. Recent high-profile cyber incidents, where attackers have used vulnerabilities in the supply chain as a means to attack companies, are a stark reminder that seemingly small players in an organisation’s supply chain can introduce disproportionately high levels of cyber risk.
DCMS’ Cyber Security Breaches Survey 2021 found that just 12% of businesses have reviewed cyber security risks posed by their suppliers and 5% have done this for their wider supply chain.[footnote 15]
Evidence gathered through DCMS-commissioned research[footnote 16][footnote 17] and industry engagement found that organisations face several barriers that limit their ability to prioritise supplier cyber risk management, their understanding of what action to take, and their ability to act:
- Low recognition of supplier risk: Many organisations are often unclear of how the cyber security of their suppliers was linked to their own security. Cyber risk is often not considered in the procurement process at all, or is prioritised below other concerns.
- Limited visibility into supply chains: Supply chains can be incredibly complex, often involving many suppliers and their subcontractors. Organisations often find it difficult to acquire the necessary information from suppliers to manage risk, either through a lack of information availability or resistance to sharing critical information.
- Insufficient expertise to evaluate supplier cyber risk: Those managing supplier risk in organisations often do not have the capability to know what questions to ask their suppliers or how to seek assurance of effective cyber security.
- Insufficient tools to evaluate supplier cyber risk: Cyber security standards can help organisations understand their suppliers’ systems and risk posture. However, there are many standards on the market, with no overarching framework or outline for how organisations should use these standards to address their supplier risk.
- Limitations to taking action due to structural imbalances: Organisations may feel they lack sufficient leverage with larger or specialist suppliers to insist on certain security measures or standards, or may lack a choice of alternatives if these suppliers refuse to meet their requirements.
Existing government support goes some way in helping organisations to overcome the barriers outlined. NCSC’s Supply Chain Security Guidance provides organisations with an improved level of supply chain security awareness and baseline level of competence in managing supplier risk. This is supported by a set of Supplier Assurance Questions to improve organisations’ capability to gain confidence in their suppliers cyber risk management practices and specific guidance for procuring certain technologies, including cloud services and mobile devices.
The government has further sought to improve baseline supply chain risk management competence through the promotion of Cyber Essentials for all suppliers to the government that involve the handling of official government data and/ or the provision of certain information and communications technology products and services. However, the barriers detailed above are still inhibiting organisations from truly recognising the scale of the cyber threat posed by their supply chains and limiting their ability to prioritise and mitigate these threats.
Organisations must first be motivated to address cyber risk in their supply chains before they can benefit from guidance on how to do so or to invest in supplier assurance products, services and resources. As with the wider cyber risk management, even where organisations are aware of the threat there is often a lack of clear commercial rationale to put in place effective mitigations to attacks.
Those who manage supplier risk in organisations are uniquely positioned to protect their organisation from this threat by ensuring cyber risk does not spread throughout their organisation from vulnerabilities in its supply chain. They can improve the cyber risk management of suppliers by exhibiting market preference towards better-certified suppliers (i.e. they have a strong potential lever in the purchasing power they hold over suppliers), through contractual obligations to meet a cyber security standard, for example Cyber Essentials, and ensure continual monitoring of suppliers to ensure adherence to contractual security requirements.
DCMS is therefore developing networks and partnerships with those who manage supplier risk in organisations, including cyber and risk management professionals, as well as those involved in the procurement process, and relevant membership bodies to better understand current supplier risk management practices and explore ways to reduce the barriers to effective supplier risk management. DCMS is also considering ways in which baseline standards of cyber security throughout supply chains can be improved, by encouraging cyber risk managers to require Cyber Essentials as a minimum security requirement in contracts, where appropriate.
Through a Call for Views on Cyber Security in Supply Chains and Managed Service Providers (MSPs), published in May 2021, the government sought feedback on existing advice and guidance to further identify what works well, what good practice looks like across the economy, and what additional further action is needed to ensure organisations are incentivised to prioritise and invest in supplier risk management. The consultation further focused on MSPs, which often play a critical role in the UK supply chains as many organisations rely on Managed Services for their day-to-day operation, including government and critical national infrastructure. The response to the Call for Views will be published later this year. DCMS is working with NCSC to incorporate the findings, as well as insights from industry engagements, to develop policy interventions to enhance organisational capability to manage supply chain risks.
11. Responsibility: accountability and regulation
Organisations have a responsibility to assess and manage their cyber resilience to protect themselves and their customers from cyber attacks. Over the course of the National Cyber Security Strategy 2016 - 2021, the government has sought to put in place the right framework for cyber security to ensure that industry acts to protect itself from threats, is outcome focused and sufficiently agile, and delivers a competitive advantage for the UK.
In 2018, the government took significant steps in strengthening the regulatory framework for cyber through the implementation of the General Data Protection Regulation (GDPR), the Data Protection Act 2018 and the 2018 Network and Information Systems Regulations. These regulations have been reviewed since their implementation and have been assessed as having a positive impact on how cyber risk is managed. However, there are still further improvements needed to enhance the UK’s resilience commensurate to the cyber risks industry faces.
The 2016 Incentives and Regulations Review concluded that significant improvements in cyber risk management could be achieved through the implementation of the GDPR. This conclusion was tested in August 2020, which found that the GDPR has had an overall positive impact on organisations and how they manage their cyber risk. However, the research noted several areas where improvements within organisations were still needed, including application security, network security, supply chain risk management, and continuity planning. Given the interconnectivity that exists between organisations that are operating in a digital environment, and the rate at which technology is evolving, organisations must prioritise improvement in these areas.
UK organisations are subject to other non-cyber regulations which either explicitly or implicitly refer to cyber security and the security of information that should influence the way organisations manage their cyber risk. The business frameworks provided by the Companies Act, Corporate Governance Code, and Audit Regulations, shape business governance and accountability and are important levers in improving cyber resilience. It is clear that in today’s digitally-dependent economy, better corporate governance is key to enhancing the accountability of organisations in managing their cyber risk. Morgan Stanley noted in their 2020 CyberSecurity and Corporate Governance article that ‘cyber security is not just a technical problem - it also poses challenges to public companies’ corporate governance.’ The World Economic Forum’s 2017 report, Advancing Cyber Resilience: Principles and tools for boards, and Kroll’s 2021 article, Cyber Risk- why Corporate Governance matters, reached similar conclusions.
Organisations need to do more to manage their cyber resilience. While some organisations prioritise the management of their cyber risk and consider it part of their broader operational resilience, this is not the case across the economy. According to the Cyber Security Breaches Survey 2021, over a third of businesses (39%) report having experienced cyber security breaches or attacks in the last 12 months, but only 35% of organisations have taken action to help identify cyber security risks through security monitoring in the last twelve months. Notably, the Cyber Security Breaches Survey 2021 shows that only two fifths (37%) of businesses actually reported their most disruptive breaches externally (e.g. to the public or law enforcement).
The lack of transparency from organisations regarding their approach to cyber risk management was also noted in Wavestone’s 2019 analysis of FTSE 100 reporting. It was observed that 87% of the FTSE 100 companies acknowledged that they face cyber security risks, but a majority made only ‘simple’ references to cyber risk (48%) or did not mention cyber risk at all (13%). Organisations should provide more meaningful reporting on how they manage cyber risk, given that this underpins business continuity. This is supported by a World Economic Forum article in 2021, which noted that ‘cyber resilience reporting can increase transparency, enhance reputations and foster an organisational culture to combat cyber risk.’
Another contributing factor to the inadequate level of organisational cyber resilience is the lack of involvement from senior management and boards. The Cyber Security Breaches Survey 2021 tells us that only half of businesses (50%) update their senior managers on cyber security at least quarterly. This is supported by research undertaken by Grant Thornton in 2019, which stated that only 37% of boards formally review cyber security risks and management. The 2021 Captains of Industry survey also noted that where boards do review cyber information, only 51% are enabled to make decisions to adapt their cyber risk profile. This demonstrates that there is an information failure and disconnect between organisations and their leaders. As a result, senior managers and boards are ill-informed to make decisions about the organisation’s approach to managing its cyber risk.
Cyber is a top-tier strategic risk that all organisations need to manage. Where organisations do not take sufficient action or responsibility for effectively managing their cyber resilience, they should be more accountable. The use of new and existing technology will be underpinned by targeted effective regulation to ensure the implementation of appropriate cyber resilience measures by those who have the greatest responsibility to protect organisations, individuals and vital sectors from disruptive and harmful cyber attacks.
The collective cyber resilience of the largest UK companies is of greatest importance to the resilience of the UK economy and to individuals. We are therefore considering how to ensure that the largest UK companies meet their corporate governance responsibilities, including managing the cyber risks they face. As part of wider reforms of corporate governance and reporting, we aim to drive greater accountability for and transparency of organisations’ cyber resilience. This would support higher standards, provide greater protection to individuals and organisations and drive further investment in improving organisation’s cyber resilience. It will also encourage shareholders to hold their Boards and executives to account for cyber security.
The Network and Information Systems Regulations
An important part of the UK’s cyber regulatory landscape is the Network and Information Systems Regulations 2018 (“NIS Regulations”), which have been in force for more than three years. These require operators of essential services in the water, health, energy, transport and digital infrastructure sectors, along with select digital service providers, to take appropriate and proportionate measures to ensure the security of the networks that support their services. Through the implementation of these Regulations the government has been working to ensure that the UK’s essential services are more secure.
The first Post-Implementation Review of the NIS Regulations was published in May 2020, and found that the Regulations were having a positive impact and driving investment in cyber security for operators of essential services and relevant digital service providers that are in scope of the Regulations. The Regulations have improved our ability to understand the level of cyber security of those essential service entities at scale and helped provide evidence on where there is a need for improvement.
The Post-Implementation Review concluded that the NIS Regulations have increased the prioritisation of security at a senior management level. It is considered that this change has likely been driven by the monitoring and enforcement powers of the NIS Regulations, as well as its penalty regime and guidance published by Competent Authorities.
The Review suggested that although the NIS Regulations were leading to improvements to security, organisations needed to accelerate these improvements. The Review also recommended a number of other potential improvements that could be made, such as: addressing supply chain vulnerabilities, further development and refining of the enforcement regime, a new appeals mechanism, and improved support and guidance for Competent Authorities. As a result, in 2020 the government put forward legislative amendments to the NIS Regulations, in order to implement some of the recommendations of the Review.
Looking forward, it is critical that the NIS Regulations remain flexible and able to respond to evolving threats. A number of the recommendations in the Post-Implementation Review are still outstanding, as they require primary legislation to enact. The government is considering how it can ensure that appropriate cost mechanisms are in place to allow regulators to respond effectively to the cyber threat and provide adequate support to organisations.
The government is also looking at the incident reporting framework of the NIS Regulations in order to improve the visibility of threats and incidents for enforcement authorities. Supply chain security, a key concern of the Review, will also need to factor more in the NIS framework and the Regulations will need to be flexible and adaptable enough to tackle this complex issue.
The government continues to believe that the NIS Regulations are making a positive difference to the resilience of the UK’s essential services. The government will be looking, as outlined above, at ways in which we can strengthen the Regulations to make them more effective. The government is also considering whether the Regulations should be expanded to other sectors, especially those that do not already have an effective legislative framework for cyber resilience.
12. Conclusion
The internet, and the digital economy and communications that have been built on it, have helped deliver huge benefits to the UK and the UK’s economy. However, attempts to exploit its weaknesses continue to increase and evolve. Malicious actors, both criminal and state-run, continue to actively look to exploit vulnerabilities in the UK’s cyber defences. The risk of deliberate or accidental cyber incidents is heightened by the increasingly interconnected nature of networks, systems and devices in use by organisations and individuals and the increased use of digital services.
This threat cannot be eliminated completely since digital technology is necessarily open, and openness brings exposure to risk. However, the risk can be greatly reduced to a level that allows society to continue to prosper, and benefit from the huge opportunities that digital technology brings.
The government is clear that it needs to take a more interventionist approach to keep the UK safe from cyber attacks. Waiting for the market to incentivise better security practices is not leading to the pace and scale of change required to mitigate upcoming threats, and is leaving UK industry and services vulnerable.
This paper has set out the rationale for why the government needs to be more interventionist in order to improve UK cyber resilience. The key outcomes the government seeks to achieve, and how they fit into the National Cyber Strategy, are as follows:
Better awareness and understanding of why Government messaging is not having the impact it needs:
- Organisations should take steps to reduce their cyber risks. The Cyber Aware campaign, although successful, is not yet reaching enough organisations and people.
- The government needs to do more to understand why advice and guidance is not reaching a sufficient audience, and increase this reach.
- The government needs to do more to understand why advice and guidance is not being acted upon by certain audiences.
- The government will work with market influencers, including insurers and procurement professionals, to ensure that awareness of cyber risk, and awareness of relevant advice and guidance, is embedded across different sectors.
- The government will also work to increase the provision of trusted support to advise companies on how to implement technical guidance.
These actions support the following:
- National Cyber Strategy, Pillar 2: Cyber Resilience, Objective 1, Outcome - UK businesses and organisations have a better understanding of cyber risk and their responsibilities to manage them.
- National Cyber Strategy, Pillar 2: Cyber Resilience, Objective 2, Outcome - Technical advice, self-help tools and assured products and services to improve cyber resilience are easy to find and continually improving, with a particular emphasis on helping citizens, sole-traders and small organisations.
More resilient organisations in the UK through increased uptake of the Cyber Essentials scheme:
Cyber Essentials is a fundamental standard which helps companies improve their cyber security. Although the 80,000+ certifications granted so far should be seen as a positive step, in the context of the number of UK small and medium enterprises this is not enough.
- The government will look at ways in which we can increase the number of companies achieving Cyber Essentials certification.
- Recognising that Cyber Essentials provides a foundational technical standard of cyber security, the government is exploring what additional support it can provide to organisations seeking to move towards a more mature level of organisational cyber resilience such as the Cyber Assessment Framework.
These actions support the following:
- National Cyber Strategy, Pillar 2: Cyber Resilience, Objective 2, Outcome - A greater number of UK businesses and organisations are proactively managing their cyber risks and taking action to improve their cyber resilience.
Improved resilience within essential services and digital services:
There has been a notable recent increase in ransomware attacks causing disruption to essential services, and the exploitation of vulnerabilities in digital supply chains to target organisations.
- The government will seek to provide more specific guidance on supplier assurance for procurers, and to establish a cyber security baseline for critical providers of digital technology services such as managed service providers.
- The government will strengthen UK cyber legislation, in particular through the Network and Information Systems Regulations, to ensure that organisations are taking appropriate action to secure their services.
These actions support the following:
-
National Cyber Strategy, Pillar 2: Cyber Resilience, Objective 2, Outcome - Cyber risks to UK critical national infrastructure are more effectively managed.
-
National Cyber Strategy, Pillar 3: Technology Advantage,Objective 3, Outcome - Major providers of digital services, including cloud, software, managed services and app stores, are required to follow better standards of cyber security, helping to protect organisations and consumers from cyber threats
Greater accountability for cyber security in business:
Organisations must take responsibility for their own risk exposure. Among the 39 per cent of businesses and 26 per cent of charities that identify breaches or attacks, one in five (21% and 18% respectively) end up losing money, data or other assets.[footnote 18] Organisations need to take action and take ownership of protecting their assets and potentially their customers from cyber threats.
- The government is considering ways in which we can mandate large companies to appropriately assess and address the cyber risks they face.
These actions support the following:
- National Cyber Strategy, Pillar 2: Cyber Resilience, Objective 2, Outcome - A greater number of UK businesses and organisations are proactively managing their cyber risks and taking action to improve their cyber resilience.
- National Cyber Strategy, Pillar 2: Cyber Resilience, Objective 3, Outcome - UK businesses and organisations have a clearer understanding of what to do in the event of an incident, who to call, who can help and how to recover.
Clarity for the cyber security profession:
The government needs to support organisations to be more confident in the quality of skilled professionals they are hiring, and to support both prospective and existing practitioners in navigating the qualification and certification landscape more effectively.
- The government will look to lead by example to embed clear professional standards and pathways developed by the UK Cyber Security Council as the professional authority. This will ensure consistency in how we recognise competence throughout the UK’s cyber security profession.
These actions support the following:
- National Cyber Strategy, Pillar 1: UK Cyber Ecosystem, Objective 2, Outcome - A higher quality and more established, recognised and structured cyber security profession.
These outcomes will be delivered over the course of the new National Cyber Strategy, as we work to protect the public, UK businesses, and critical national infrastructure from emerging threats. Building a resilient and prosperous digital UK is a priority objective for the government, and we look forward to working with our partners to achieve this.
-
The ‘Digital stack’ refers to the concept of different layers within digital infrastructure, for example the hardware layer, the software layer, and the user layer. ↩
-
Critical national Infrastructure consists of those facilities, systems, sites, information, people, networks and processes necessary for the country to function and upon which daily life depends. It also includes some functions, sites and organisations which are not critical to the maintenance of essential services, but which need protection due to the potential dangers they could pose to the public in the event of an emergency (civil nuclear and chemicals sites for example). ↩
-
ibid - see above ↩
-
ibid - see above ↩
-
ibid - see above ↩
-
Ipsos/NCSC/DCMS UK Cyber Survey 2019 ↩
-
Cyber Discovery Evaluation 2021 ↩
